Zombie projects - merge user data even after his death
I’m talking about leakage of personal data again, but this time I’ll tell you a little about the afterlife of IT projects using two recent finds.
In the process of auditing database security, it often happens that you discover servers ( how to search for databases , I wrote in a blog) that belong to projects that have long (or not so long ago) left our world. Such projects even continue to imitate life (work), resembling zombies (collecting personal data of users after their death).
Дисклеймер: вся информация ниже публикуется исключительно в образовательных целях. Автор не получал доступа к персональным данным третьих лиц и компаний. Информация взята либо из открытых источников, либо была предоставлена автору анонимными доброжелателями.Let's start with the project with the loud name “Putin Team” (putinteam.ru).
A server with open MongoDB was discovered on 04/19/2019.

As you can see, the ransomware was the first to get to this base:
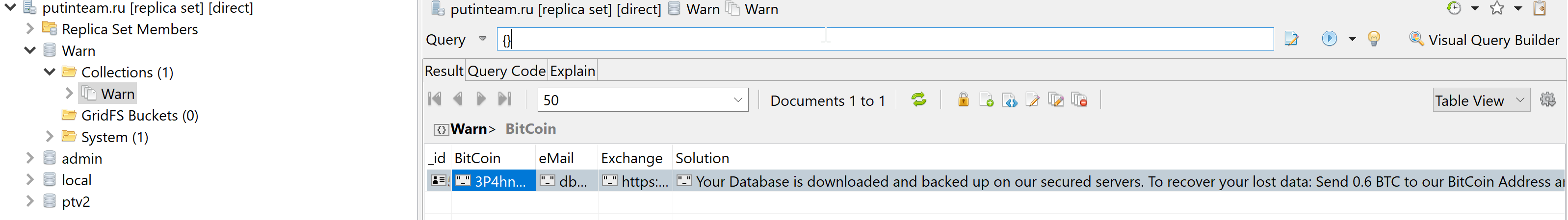
The database does not have particularly valuable personal data, but there are email addresses (less than 1000), first names, hashed passwords, GPS coordinates (apparently when registering from smartphones), cities of residence and photos of users of the site who created their personal account on it.
{
"_id" : ObjectId("5c99c5d08000ec500c21d7e1"),
"role" : "USER",
"avatar" : "https://fs.putinteam.ru/******sLnzZokZK75V45-1553581654386.jpeg",
"firstName" : "Вадим",
"lastName" : "",
"city" : "Санкт-Петербург",
"about" : "",
"mapMessage" : "",
"isMapMessageVerify" : "0",
"pushIds" : [
],
"username" : "5c99c5d08000ec500c21d7e1",
"__v" : NumberInt(0),
"coordinates" : {
"lng" : 30.315868,
"lat" : 59.939095
}
}
{
"_id" : ObjectId("5cb64b361f82ec4fdc7b7e9f"),
"type" : "BASE",
"email" : "***@yandex.ru",
"password" : "c62e11464d1f5fbd54485f120ef1bd2206c2e426",
"user" : ObjectId("5cb64b361f82ec4fdc7b7e9e"),
"__v" : NumberInt(0)
}A lot of garbage information and empty records. For example, the newsletter subscription code does not verify that the email address is entered, so instead of the address, you can write anything you want.
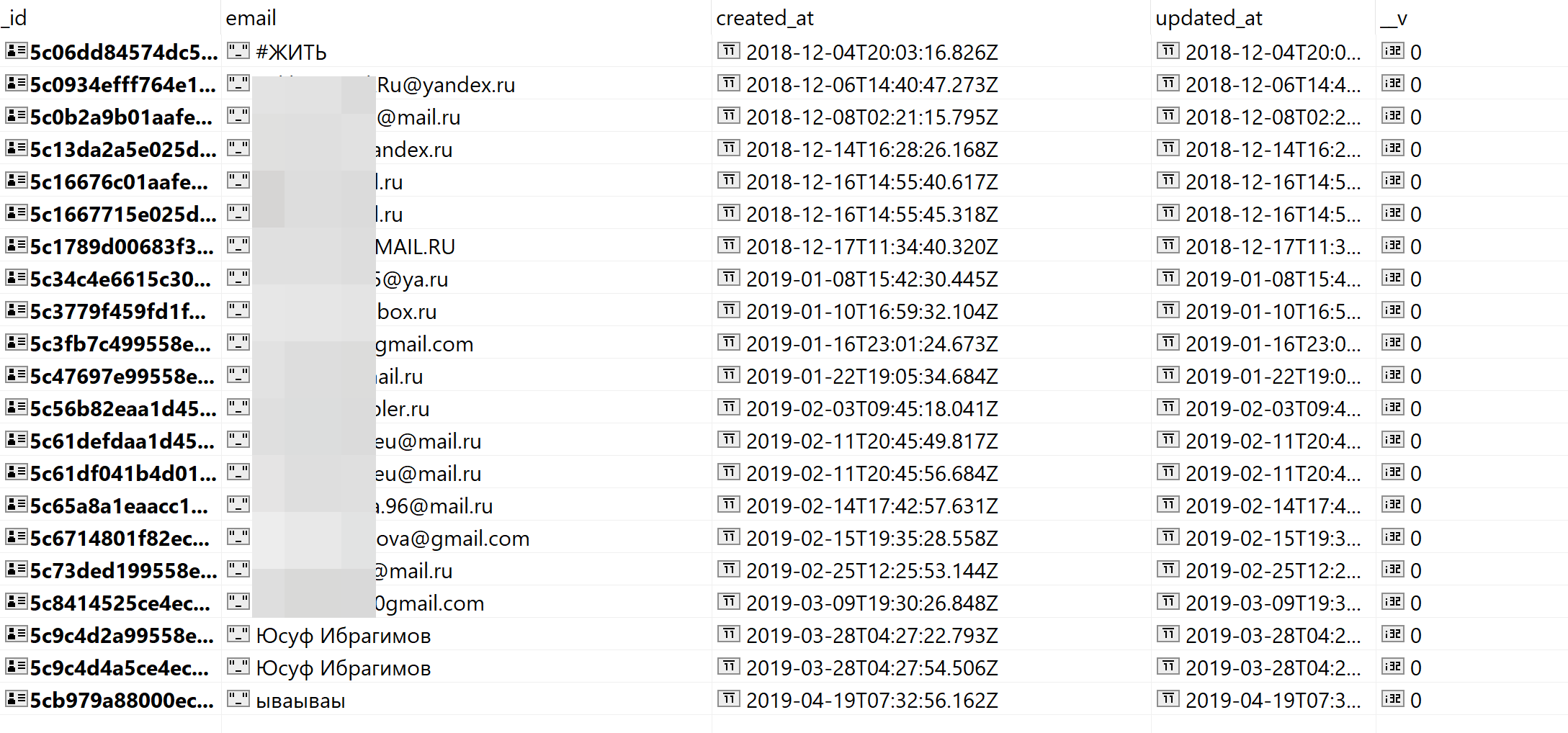
Judging by the copyright on the site, the project was abandoned in 2018. All attempts to contact the project were unsuccessful. However, rare registrations on the site are on - there is an imitation of life.
The second zombie project in my analysis today is the Latvian startup Roamer (roamerapp.com/ru).
04/21/2019 an open MongoDB database of the Roamer mobile application was discovered on a server in Germany.

The base, the size of 207 MB, is in the public domain from 11/24/2018 (according to Shodan)!
By all external signs (a non-working technical support email address, broken links to the Google Play store, copyright on the website of 2016, etc.) - the application has long been abandoned.
At one time, almost all thematic media wrote about this startup:
- VC: “ Latvian startup Roamer - roaming killer ”
- the-village: “ Roamer: An application that reduces the cost of calls from abroad ”
- lifehacker: “ How to reduce communication costs in roaming by 10 times: Roamer ”
The "killer" seems to have killed himself, but even continues to divulge the dead personal data of his users ...
Judging by the analysis of information in the database, many users continue to use this mobile application. Within a few hours of observation, 94 new entries appeared. And for the period from 03/27/2019 to 04/10/2019, 66 new users registered in the application.
In the public domain are logs (more than 100 thousand entries) of the application with such information as:
- user phone
- tokens of access to call history (available via links of the form: api3.roamerapp.com/call/history/1553XXXXXX )
- call history (numbers, incoming or outgoing call, call cost, duration, call time)
- mobile operator
- User IPs
- user’s phone model and mobile OS version on it (for example, iPhone 7 12.1.4 )
- user email address
- user account balance and currency
- user country
- current location (country) of the user
- promotional codes
- and much more.
{
"_id" : ObjectId("5c9a49b2a1f7da01398b4569"),
"url" : "api3.roamerapp.com/call/history/*******5049",
"ip" : "67.80.1.6",
"method" : NumberLong(1),
"response" : {
"calls" : [
{
"start_time" : NumberLong(1553615276),
"number" : "7495*******",
"accepted" : false,
"incoming" : false,
"internet" : true,
"duration" : NumberLong(0),
"cost" : 0.0,
"call_id" : NumberLong(18869601)
},
{
"start_time" : NumberLong(1553615172),
"number" : "7499*******",
"accepted" : true,
"incoming" : false,
"internet" : true,
"duration" : NumberLong(63),
"cost" : 0.03,
"call_id" : NumberLong(18869600)
},
{
"start_time" : NumberLong(1553615050),
"number" : "7985*******",
"accepted" : false,
"incoming" : false,
"internet" : true,
"duration" : NumberLong(0),
"cost" : 0.0,
"call_id" : NumberLong(18869599)
}
]
},
"response_code" : NumberLong(200),
"post" : [
],
"headers" : {
"Host" : "api3.roamerapp.com",
"X-App-Id" : "a9ee0beb8a2f6e6ef3ab77501e54fb7e",
"Accept" : "application/json",
"X-Sim-Operator" : "311480",
"X-Wsse" : "UsernameToken Username=\"/******S19a2RzV9cqY7b/RXPA=\", PasswordDigest=\"******NTA4MDhkYzQ5YTVlZWI5NWJkODc5NjQyMzU2MjRjZmIzOWNjYzY3MzViMTY1ODY4NDBjMWRkYjdiZTQxOGI4ZDcwNWJmOThlMTA1N2ExZjI=\", Nonce=\"******c1MzE1NTM2MTUyODIuNDk2NDEz\", Created=\"Tue, 26 Mar 2019 15:48:01 GMT\"",
"Accept-Encoding" : "gzip, deflate",
"Accept-Language" : "en-us",
"Content-Type" : "application/json",
"X-Request-Id" : "FB103646-1B56-4030-BF3A-82A40E0828CC",
"User-Agent" : "Roamer;iOS;511;en;iPhone 7;12.1.4",
"Connection" : "keep-alive",
"X-App-Build" : "511",
"X-Lang" : "EN",
"X-Connection" : "WiFi"
},
"created_at" : ISODate("2019-03-26T15:48:02.583+0000"),
"user_id" : "888689"
}Of course, it was not possible to contact the owners of the base. Contacts on the site do not work, on messages in the social. networks nobody reacts.
The app is still available on the Apple App Store (itunes.apple.com/app/roamer-roaming-killer/id646368973).
News about information leaks and insiders can always be found on my Telegram channel “ Information leaks ”: https://t.me/dataleak .
