Parsing a critical error in the KIB SEARCHINFORM encryption algorithm
Monitoring all the information circulating in the organization is one of the main tasks in the practical implementation of organizational and administrative documents (information security policy and other internal documents of the lower levels) of the organization.
Systems for preventing leakage of confidential information from an information system (Data Leak Prevention, DLP) are mostly able to solve this problem.
In today's market there are enough varieties of these systems, for example, such as: SearchInform DLP, Infowatch Traffic Monitor DLP, Zecurion DLP, Symantec DLP and others. But today, this article will be about the product of the company SearchInform.
SearchInform Information Security Circuit (CIB Searchinform) is a serious and highly customizable software package that, by its functionality and extensive analytical tools, creates serious competition to other companies in this field. But like all products, CIB Searchinform has one of the drawbacks, which we will discuss now.

Figure 1 - Logo CIB Searchinform
In CIB Searchinform, one of the sources of information collection is an agent (Windows / Linux). Agent for Windows, as well as for Linux, has a modular system for collecting information, if necessary, they are turned on or off. We will consider the Device module (control of external devices, network devices, processes, etc.). A demo version of this product can be obtained officially through the developer's website (with full functionality). Further actions will be implemented using the obtained license key - EndPointController version 5.51.0.9 (agent version 5.51.0.9).
The main problem in the operation of this module is the information encryption algorithm on external removable devices. Consider the principle of operation of the encryption algorithm in CIB Searchinform.
We install the agent on the workstation and set the external devices (Device module) to work under control in the Network Environment section of EndPointController 5.51.0.9
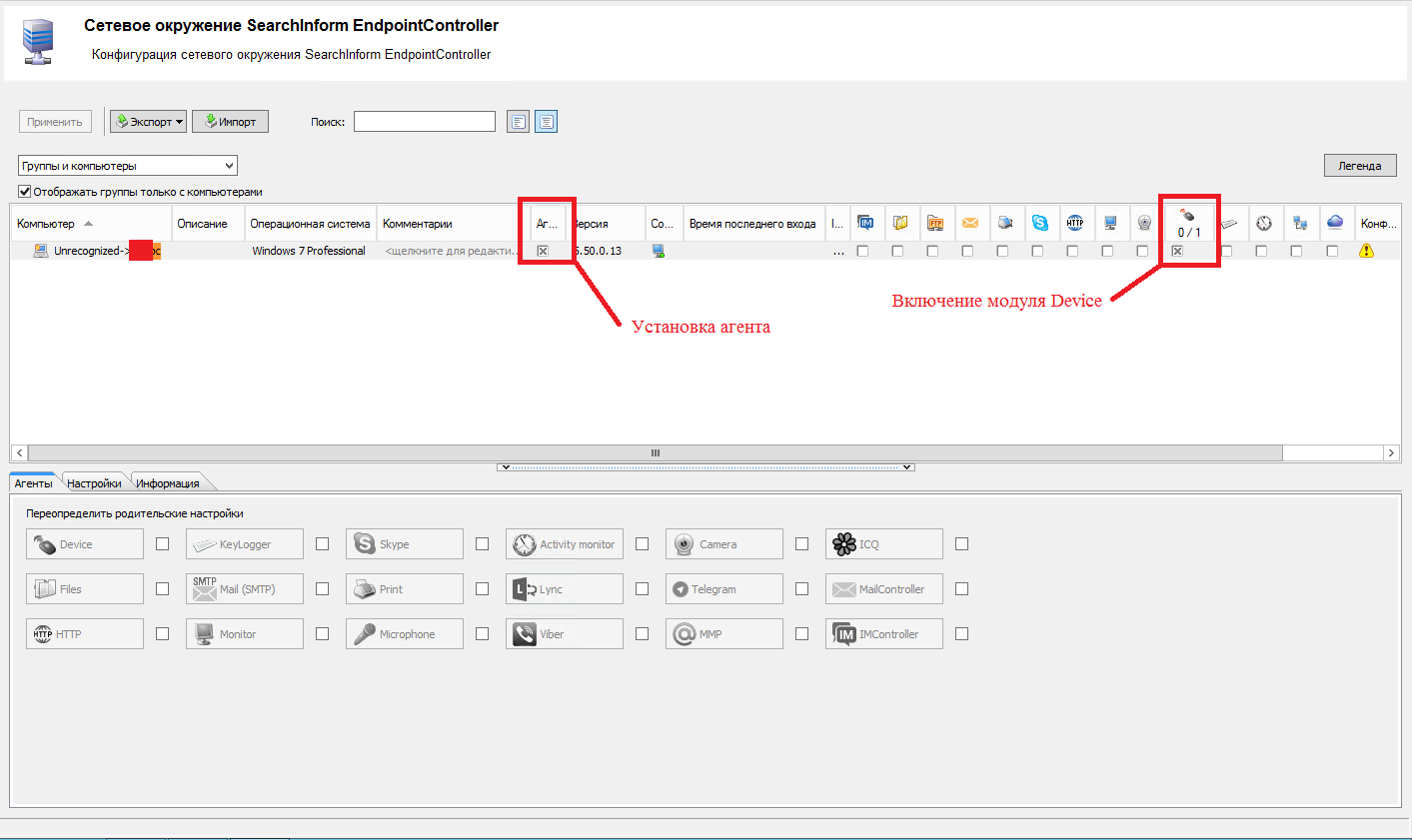
Figure 2 - Installing and enabling the module
Encryption configuration in the Device module settings of the Encryption tab: generate a key and enable encryption for all storage media (encryption can be enabled only for certain storage media).
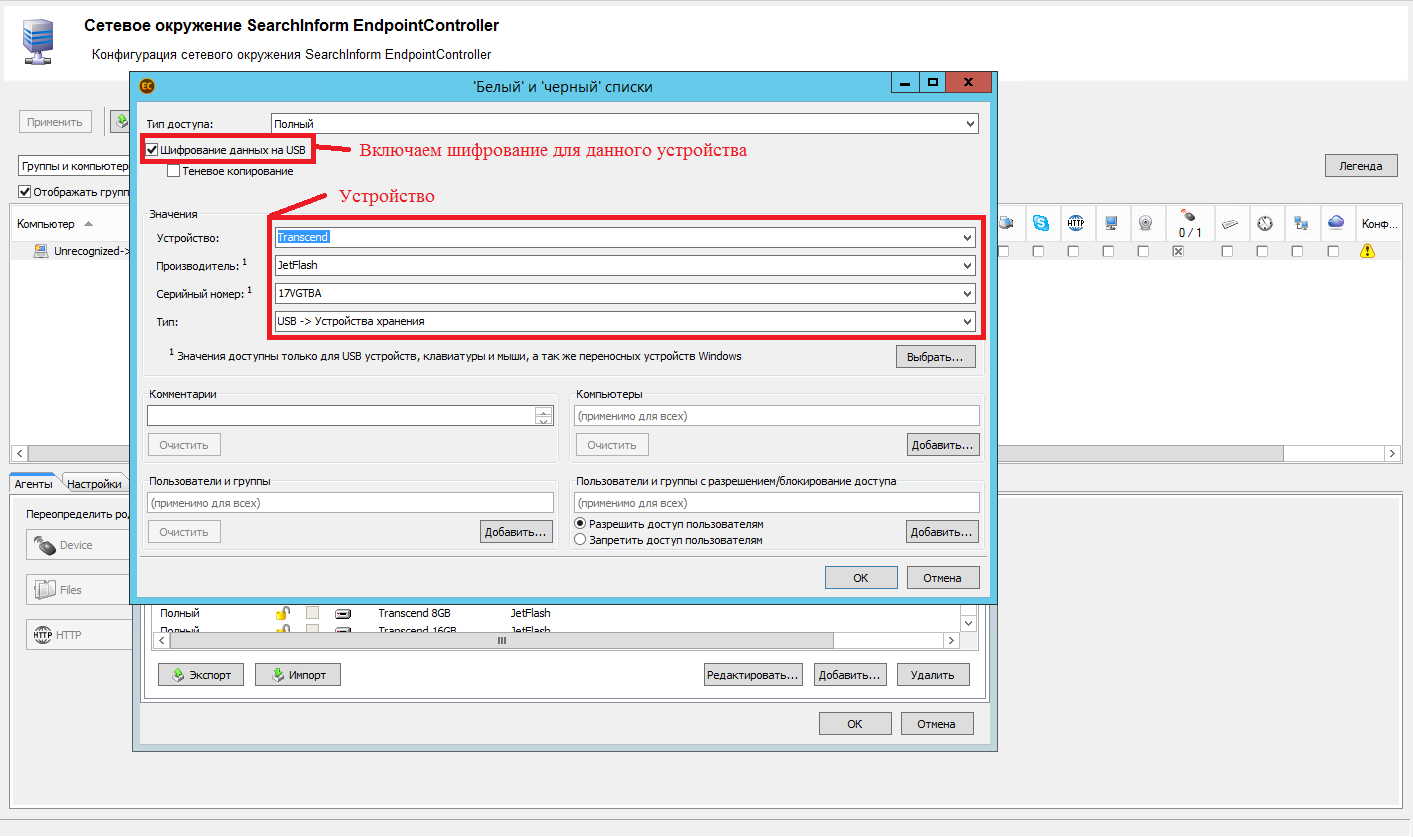
Figure 3 - Configuring the whitelist
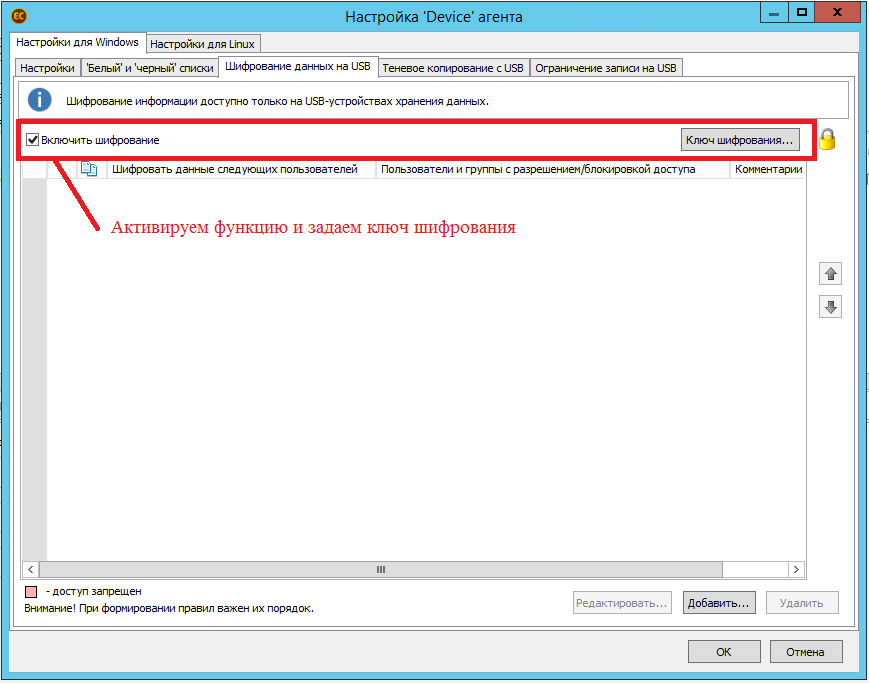
Figure 4 - Configuring encryption
Now we begin to analyze the file encryption algorithm for this product. Copy the files “Install.exe” and “Fundamentals of Rights.rtf” from the controlled workstation “WINOC” to the external removable media “Removable Disk (E :)”. As you can see in Figure 5, the “Install.exe” and “Fundamentals of Rights.rtf” objects were created in the hidden folder “System Volume Information”. Thus, we can conclude that the “System Volume Information” folder contains a list of encrypted objects on removable media.
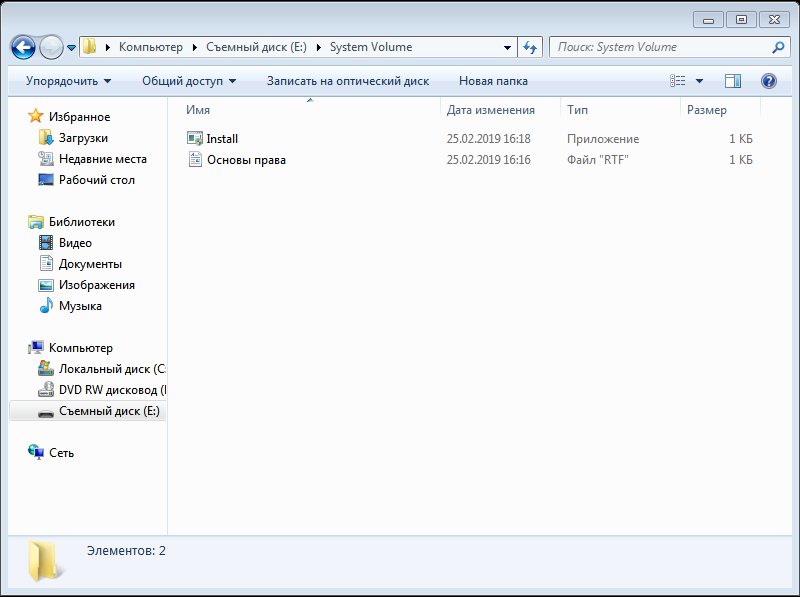
Figure 5 - System Volume Information
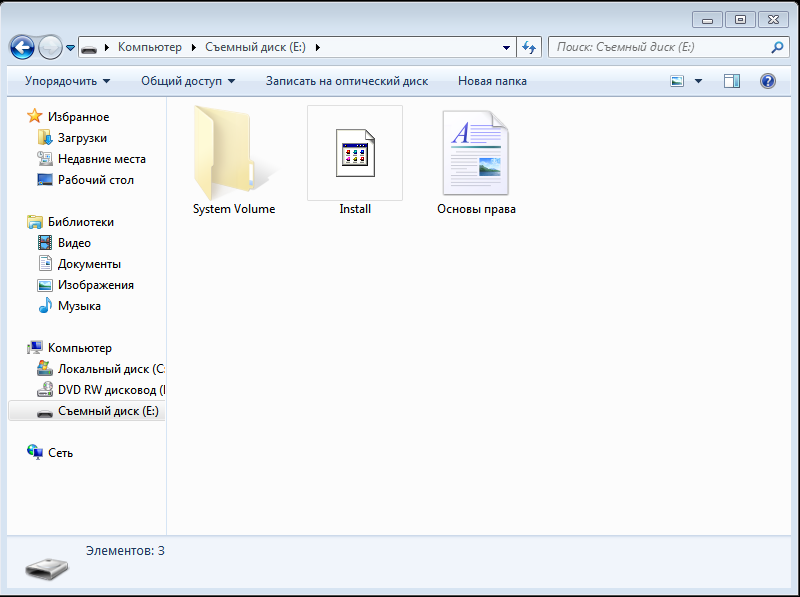
folder Figure 6 - The root folder of the removable storage medium
As you know, there are three aspects on which information security is built - these are integrity, accessibility and confidentiality. These aspects are violated using this encryption approach, since the system information about whether the object is encrypted or not should be in the object header itself.
In the current construction of the algorithm, variants of random modification / deletion of objects of the “System Volume Information” folder on removable media with further loss of the original encrypted objects, as well as modification of the objects themselves on uncontrolled stations (for example, renaming the “Install.exe” object with the network path “E : \ Install.exe "on a computer without an agent, while the information file for the CIB Searchinform software product in the" System Volume Information "" Install.exe "folder by the network path" E: \ System Volume Information \ Install.exe "remains unchanged, since missing agent which of ENITA service information, and the opening of the file has become impossible).
Let's hope that the developer will take into account this shortcoming in the function of encrypting removable storage media in the product of CIB Searchinform and change its algorithm.
Systems for preventing leakage of confidential information from an information system (Data Leak Prevention, DLP) are mostly able to solve this problem.
In today's market there are enough varieties of these systems, for example, such as: SearchInform DLP, Infowatch Traffic Monitor DLP, Zecurion DLP, Symantec DLP and others. But today, this article will be about the product of the company SearchInform.
SearchInform Information Security Circuit (CIB Searchinform) is a serious and highly customizable software package that, by its functionality and extensive analytical tools, creates serious competition to other companies in this field. But like all products, CIB Searchinform has one of the drawbacks, which we will discuss now.

Figure 1 - Logo CIB Searchinform
In CIB Searchinform, one of the sources of information collection is an agent (Windows / Linux). Agent for Windows, as well as for Linux, has a modular system for collecting information, if necessary, they are turned on or off. We will consider the Device module (control of external devices, network devices, processes, etc.). A demo version of this product can be obtained officially through the developer's website (with full functionality). Further actions will be implemented using the obtained license key - EndPointController version 5.51.0.9 (agent version 5.51.0.9).
The main problem in the operation of this module is the information encryption algorithm on external removable devices. Consider the principle of operation of the encryption algorithm in CIB Searchinform.
We install the agent on the workstation and set the external devices (Device module) to work under control in the Network Environment section of EndPointController 5.51.0.9

Figure 2 - Installing and enabling the module
Encryption configuration in the Device module settings of the Encryption tab: generate a key and enable encryption for all storage media (encryption can be enabled only for certain storage media).

Figure 3 - Configuring the whitelist

Figure 4 - Configuring encryption
Now we begin to analyze the file encryption algorithm for this product. Copy the files “Install.exe” and “Fundamentals of Rights.rtf” from the controlled workstation “WINOC” to the external removable media “Removable Disk (E :)”. As you can see in Figure 5, the “Install.exe” and “Fundamentals of Rights.rtf” objects were created in the hidden folder “System Volume Information”. Thus, we can conclude that the “System Volume Information” folder contains a list of encrypted objects on removable media.

Figure 5 - System Volume Information

folder Figure 6 - The root folder of the removable storage medium
As you know, there are three aspects on which information security is built - these are integrity, accessibility and confidentiality. These aspects are violated using this encryption approach, since the system information about whether the object is encrypted or not should be in the object header itself.
In the current construction of the algorithm, variants of random modification / deletion of objects of the “System Volume Information” folder on removable media with further loss of the original encrypted objects, as well as modification of the objects themselves on uncontrolled stations (for example, renaming the “Install.exe” object with the network path “E : \ Install.exe "on a computer without an agent, while the information file for the CIB Searchinform software product in the" System Volume Information "" Install.exe "folder by the network path" E: \ System Volume Information \ Install.exe "remains unchanged, since missing agent which of ENITA service information, and the opening of the file has become impossible).
Let's hope that the developer will take into account this shortcoming in the function of encrypting removable storage media in the product of CIB Searchinform and change its algorithm.
