Retrieving a Master Password from a SafeInCloud Locked Password Manager
After reading this article, I wanted to research another password manager for similar vulnerabilities.
In comments to the article, Dark_Angel asked a question:

The study was conducted on the free Windows version of SafeInCloud v.19.0.2.
When I first met the product, it made a very good impression on me.
However, further research revealed exactly the same vulnerability.
Unlike 1Password, SafeInCloud stores all your passwords in clear text even in a locked state (after the first unlock).
To get the password from the database, just read the application memory. Data obfuscation is completely absent! Master password (and all other passwords and records) is not overwritten never after the first successful unlock the database, even if the user will block it.
Your passwords may leak in the following cases:
+ Sending a bug report in any software. Very often, developers dump the memory of all applications for debugging purposes.
+ If you use a computer, not only you.
+ When gaining physical access to an attacker’s computer.
+ When starting malware.
+ It is possible that memory contents get into swap.
+ Something else ...
The Windows application is written in .net, which greatly simplifies the analysis of the source code.

The application is written in .net
After the successful decryption of the database (XDatabase), the decrypted database and master password are saved as class fields in the Singleton instanc of the DatabaseModel class.
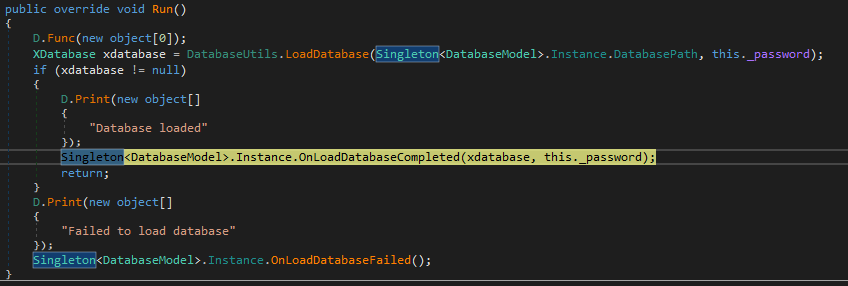
Setting fields with a database and a master password from it
All entries and passwords are stored in memory in clear form even after the user locks the application. The master password lies in the clear next to it.
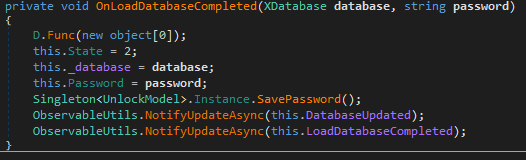
The password is stored in the Password property, _database is a field of the XDatabase class that contains the decrypted database.
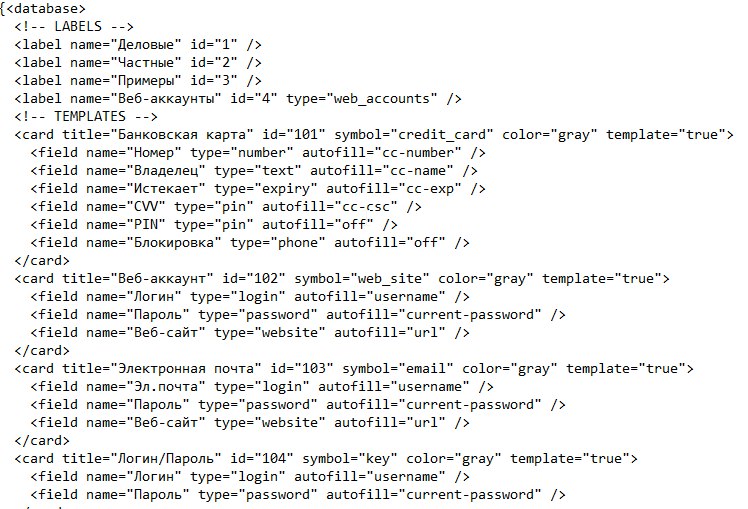
Database in XML format.
When re-unlocking, the application performs an elementary check:
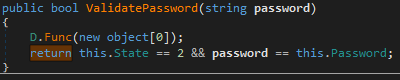
If the password entered by the user matches the one stored in the memory, the unlock is completed.
A simple SafeInCloudExtractor utility was written to automate the extraction of the master password .
The utility extracts the master password and the local path to the database file.
What password manager do you use? Write in the comments!
UPDATE After reporting a problem, the author of SiC took criticism very negatively (up to insults). Under pressure from users, a beta version was released with "protection against hackers." That is, with protection from the SafeInCloudExtractor utility. It would seem that the problem is solved! Passwords are cleared from memory. However, this is not the case and this is why: An
updated version of SiC also stores all passwords in memory. To complicate the analysis of the code, an obfuscator was applied + an IsDebuggerPresent check was added. Passwords are stored in clear text in memory, and are stored. It seems that the author does not understand what to defend against. Instead of fixing the problem, PoC was disabled. Most likely, the author does not have the necessary qualifications and knowledge to develop security-related software. Be carefull!
In comments to the article, Dark_Angel asked a question:
What about SafeInCloud?

The study was conducted on the free Windows version of SafeInCloud v.19.0.2.
When I first met the product, it made a very good impression on me.
However, further research revealed exactly the same vulnerability.
Unlike 1Password, SafeInCloud stores all your passwords in clear text even in a locked state (after the first unlock).
To get the password from the database, just read the application memory. Data obfuscation is completely absent! Master password (and all other passwords and records) is not overwritten never after the first successful unlock the database, even if the user will block it.
Your passwords may leak in the following cases:
+ Sending a bug report in any software. Very often, developers dump the memory of all applications for debugging purposes.
+ If you use a computer, not only you.
+ When gaining physical access to an attacker’s computer.
+ When starting malware.
+ It is possible that memory contents get into swap.
+ Something else ...
The Windows application is written in .net, which greatly simplifies the analysis of the source code.

The application is written in .net
After the successful decryption of the database (XDatabase), the decrypted database and master password are saved as class fields in the Singleton instanc of the DatabaseModel class.

Setting fields with a database and a master password from it
All entries and passwords are stored in memory in clear form even after the user locks the application. The master password lies in the clear next to it.

The password is stored in the Password property, _database is a field of the XDatabase class that contains the decrypted database.

Database in XML format.
When re-unlocking, the application performs an elementary check:

If the password entered by the user matches the one stored in the memory, the unlock is completed.
A simple SafeInCloudExtractor utility was written to automate the extraction of the master password .
The utility extracts the master password and the local path to the database file.
What password manager do you use? Write in the comments!
UPDATE After reporting a problem, the author of SiC took criticism very negatively (up to insults). Under pressure from users, a beta version was released with "protection against hackers." That is, with protection from the SafeInCloudExtractor utility. It would seem that the problem is solved! Passwords are cleared from memory. However, this is not the case and this is why: An
updated version of SiC also stores all passwords in memory. To complicate the analysis of the code, an obfuscator was applied + an IsDebuggerPresent check was added. Passwords are stored in clear text in memory, and are stored. It seems that the author does not understand what to defend against. Instead of fixing the problem, PoC was disabled. Most likely, the author does not have the necessary qualifications and knowledge to develop security-related software. Be carefull!
