How to get Security Log with non-administrative user
Hi Habr! Read under cat how to access the Windows security log without administrator privileges. This will not be the first article on Habr connected with Windows logs and probably not the most original one, but in my opinion I spent too much time searching for a simple solution for reading logs as an ordinary user, so I decided to share the “success story”.
I also had to compare the performance of Powershell cmdlets with the Get-WinEvent and Get-EventLog cmdlets .
Everything that is under the cut is relevant for Windows Server 2008R2 / 2012R2, Windows 10 Pro (1809), I have not tested it on other versions, I think that the situation is similar with the products of 2016 and 2019.
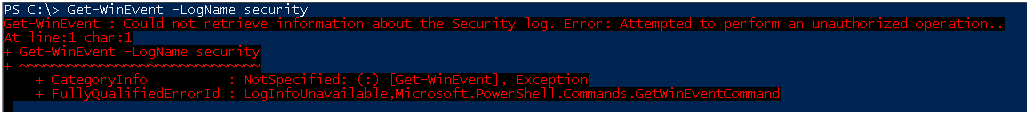
And so, by default, the average user does not have permission to read security logs.
When you try to get the logs, you get an error.
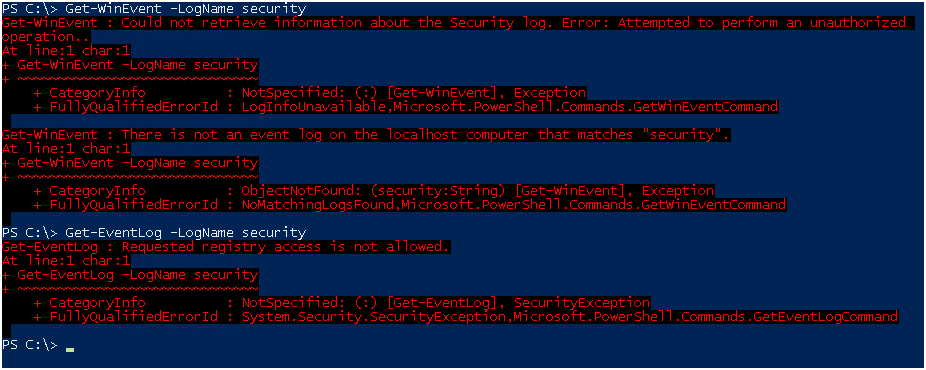
And through Event Viewer access will also be denied.

SHOWTIME
Add the user to the local Event Log Readers group .

Next, we grant read permissions to the MACHINE \ System \ CurrentControlSet \ Services \ Eventlog \ Security registry branch .
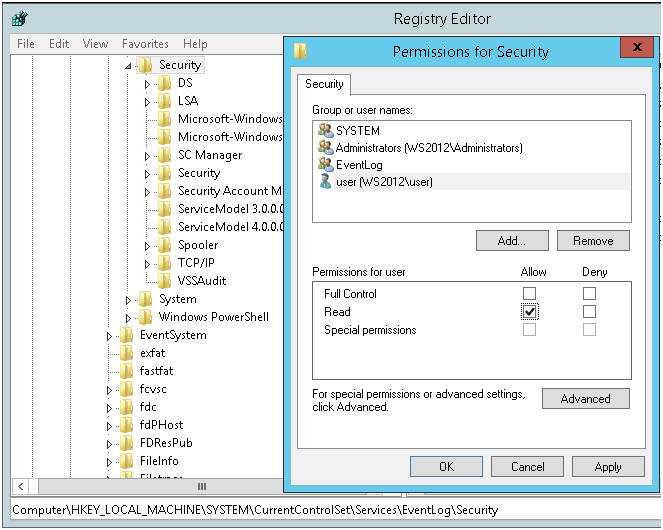
Without changing the rights to this registry branch, you won’t be able to read the parameters of the security log; accordingly, you won’t be able to find out the location and name of the log file. Security , this is the only section of the Eventlog service that does not inherit access rights from the root.
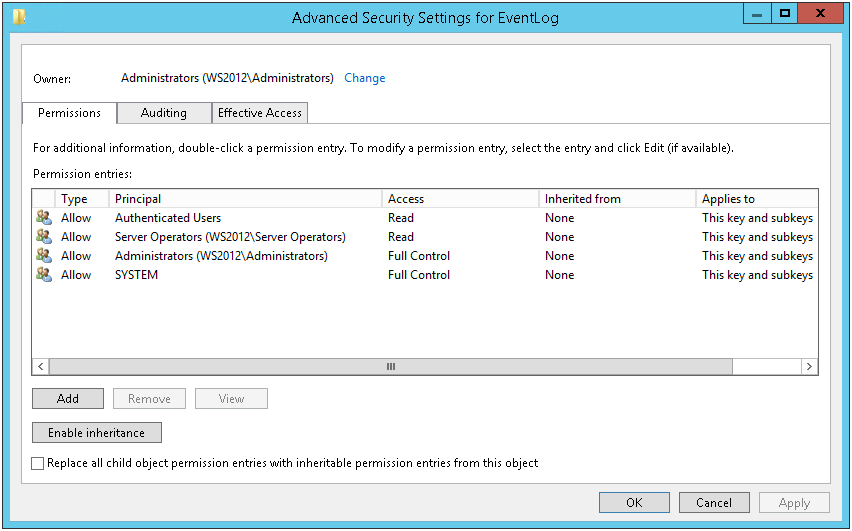
This is what the permissions for MACHINE \ System \ CurrentControlSet \ Services \ Eventlog look like .
Check that both Get-WinEvent and Get-EventLog cmdlets work!
Later, back to comparing these cmdlets ...

Manage auditing and security log
If the user needs to be granted rights to clear the log, you will have to edit the group policy. A user or group of users needs to add Manage auditing and security log permissions .
This group is located here Computer Configuration \ Windows Settings \ Security Settings \ Local Policies \ User Rights Assignment .

You can read more about Manage auditing and security log here.
This policy setting determines which users can specify object access audit options for individual resources such as files, Active Directory objects, and registry keys. These objects specify their system access control lists (SACL). A user who is assigned this user right can also view and clear the Security log in Event Viewer. For more info about the Object Access audit policy, see Audit object access.
We check that everything works as promised, the logs have been cleaned ... There are no
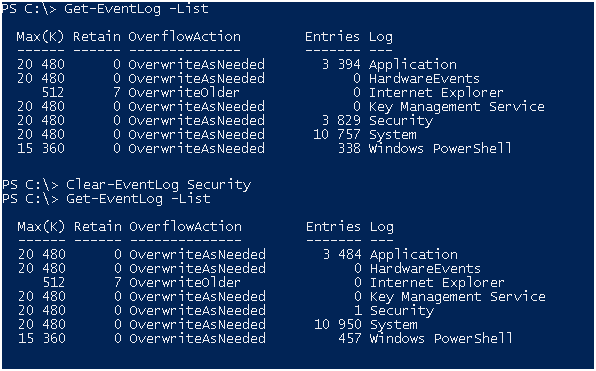
other logics to clear the logs.
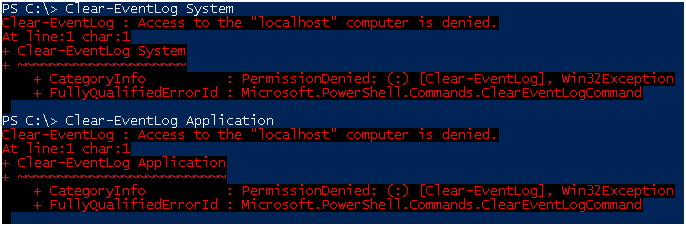
Honestly, I can’t come up with a scenario where the user needs to be given the right to clean up the security logs, but there is such an opportunity.
Get-WinEvent VS Get-EventLog
It's time to compare these two Get-EventLog cmdlets
Description:
The Get-EventLog cmdlet gets events and event logs on the local and remote computers.
You can use the cmdlet's parameters and property values to search for events. This cmdlet gets events that match the specified property values.
The cmdlets that contain the EventLog noun work only on classic event logs. To get events from logs that use the Windows Event Log technology in Windows Vista and later Windows versions, use Get-WinEvent.
Get-WinEvent
Description:
The Get-WinEvent cmdlet gets events from event logs, including classic logs, such as the System and Application logs, and the event logs that are generated by the Windows Event Log technology introduced in Windows Vista. It also gets events in log files generated by Event Tracing for Windows (ETW).
Without parameters, a Get-WinEvent command gets all the events from all the event logs on the computer. To interrupt the command, press CTRL + C.
Get-WinEvent also lists event logs and event log providers. You can get events from selected logs or from logs generated by selected event providers. And, you can combine events from multiple sources in a single command. This cmdlet allows you to filter events by using XPath queries, structured XML queries, and simplified hash-table queries
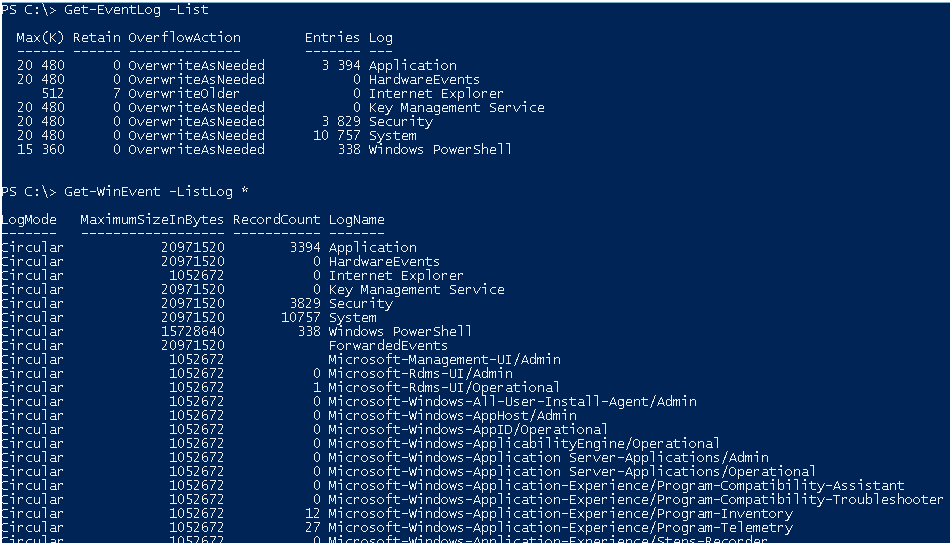
According to the description, Get-WinEvent can work with a large number of magazines that appeared in WIndows Vista .
For clarity, here are the lists these cmdlets work with ; I stopped the output for Get-WinEvent .
But there is one thing, performance matters, compare query execution time.
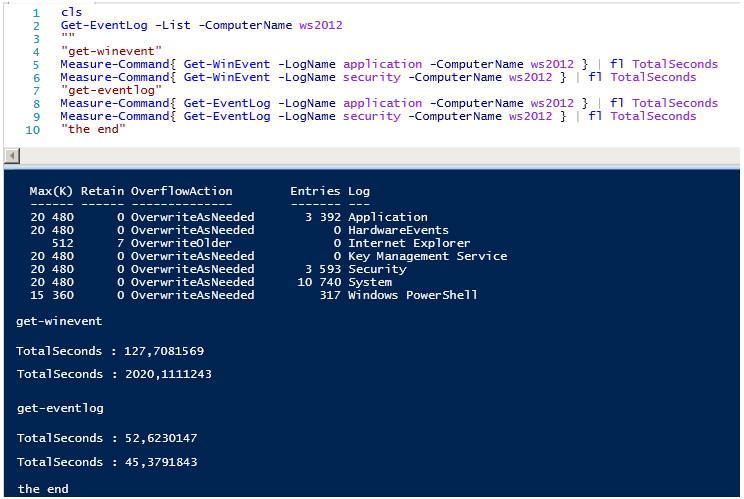
Working hours Get-WinEvent simply amazing, pay attention to the number of entries in the logs Applocation and Security , the number of events 3400-3600 about the same, but the difference in execution time is almost 20 times ...
Get-WinEvent spend 127 seconds to 52 seconds Get-EventLogto read Application events .
And checkmate, Get-WinEvent spends 2020 seconds versus 45 seconds Get-EventLog to read Security events .
If you execute the same commands locally, everything doesn’t look so bad, but even locally Get-EventLog works with security logs 50 times faster than Get-WinEvent .

And another example, already a little more meaningful, of receiving events with code 4624 An account was successfully logged on .
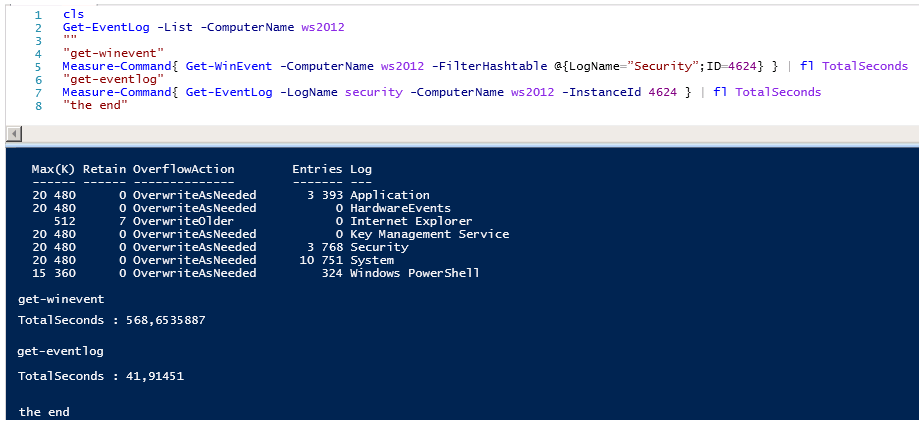
What can I say, the numbers do not lie ...
Non-administrator access to DC Event logs
And in conclusion, I left the topic of gaining access to security logs on the domain controller.
All of the above is also relevant for the domain controller with some amendments.
1 - You will find the Event Log Readers group in the Built-in security principals objects .
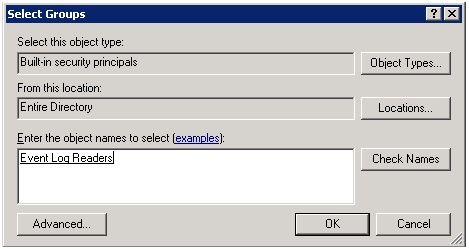
By adding a user to this group you only give read permissions to the domain controllers.
And do not forget that on each of the domain controllers you must give permission to read the registry branch MACHINE \ System \ CurrentControlSet \ Services \ Eventlog \ Security .
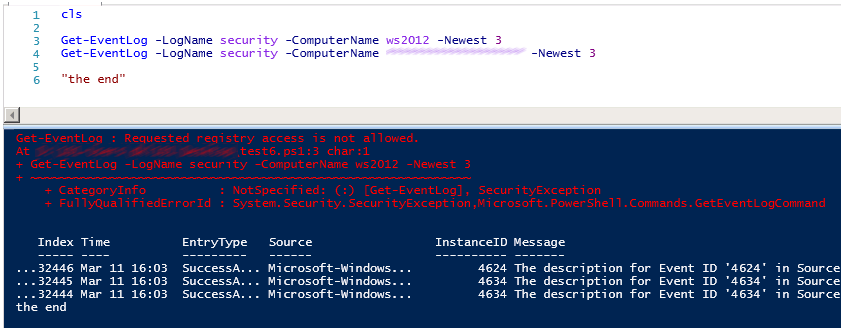
Here is an example, there is no permission to read the log of a member server, if you need to read logs from other machines in the domain, use group policies to add users or user groups to the local Event Log Readers groups .
2 - To add rights to clear logs, you must edit the Default Domain Controllers Policy .
3 - To allow the launch of tasks on behalf of the user on the domain controller, you must also edit the Default Domain Controllers Policy and give the user Log on as a batch job permissions .
4 - Be extremely careful when editing default domain policies!
PS
A short list of resources that helped me:- Giving Non Administrators permission to read Event Logs Windows 2003 and Windows 2008
- How to set event log security locally or by using Group Policy
- DC Security - Read Security Event Log
- Get-WinEvent with non-administrative user
- Domain Controller Security Logs - how to get at them * without * being a Domain Admin
In my opinion, useful publications on Habr, whose topics relate to Windows logs:
- Powershell audits Active Directory with change alerts. Part 1
- Finding the source of user locks in Active Ditectory
- Monitoring and Alerting Events in Windows Logs: E-mailing in Windows Server 2012 R2
- Security audit on the server. Search Security Journal. Power powershell
