3CX Technical Support Responds - 5 IP PBX Security Rules
- Tutorial
Hacks of 3CX automatic telephone exchanges, which lead to serious consequences, are quite rare. However, our customers sometimes become victims of scams. As practice has shown, this is mainly due to incorrect system settings, or using the outdated version of 3CX. In this article we will look at the most common errors that can lead to hacking your PBX, and explain how to avoid them.
Telephony fraud is pretty commonplace - outsiders or a robot diver make calls through your PBX at your expense. This usually happens late at night or on non-working days. Calls last as long as possible, with high frequency and to the most expensive international destinations. And at the end of the month you receive an invoice from the telecom operator for a huge amount, which you must pay, or dispute in court.
Calls to the most expensive international destinations were the main goal of hackers in the early period of the development of software exchanges. You might think that this type of fraud is a thing of the past, especially given the cost of international negotiations. However, this is currently being done by well-organized international groups that plunder customers and operators on an industrial scale.
Now PBXs are being hacked in order to make thousands of calls to “expensive” numbers of various paid automatic services that are controlled by the same scammers. In this case, the attacker makes a profit in the form of a commission from the operator for every minute of a paid call. This fraud is also called the International Revenue Sharing Fraud (IRSF).
Another way to make illegal money is to sell stolen SIP client credentials on "clandestine" online exchanges. Further, such access is used in different ways - either for competition with legal telecom operators, due to which it is possible to sell minutes much cheaper than the market price, or for some personal needs of the buyer.
3CX has several security levels whose default settings prevent most known attack types. However, some system administrators change or disable these settings without even realizing what the consequences are.
Let's look at the most common security settings that 3CX administrators make.
The first mistake is the “weak” account credentials used by 3CX applications, IP phones and users.
When you create a user (extension) in 3CX, secure credentials are automatically generated for him at all access levels. These are complex SIP and web client logins, randomly generated passwords for accessing the web interface of IP phones, random voicemail PINs, etc. Be sure to use only these secure credentials because random long passwords guarantee protection against attacks password guessing (also called brute force attacks).
Starting with 3CX v15.5, the system will not allow you to set the extension password weaker than required by modern security rules. However, often weak account passwords are inherited from backups of previous versions of 3CX. Therefore, now 3CX warns the administrator if extension numbers with weak passwords are present in the system - a warning appears near such numbers. If you hover over it, additional information appears.

By the way, we strongly do not recommend setting weak passwords for testing purposes. As a rule, people forget to change them and leave the PBX “full of holes”.
The second mistake is to disable the option “Deny connection from the public network” and not turn it back on when the user no longer needs it.

This option is included in 3CX by default and prevents registration of any users outside of your local network. Please note that you can use applications or the 3CX web client without enabling remote access, since they use tunneling technology to connect to the PBX. This option should be disabled only if someone needs a direct SIP connection for a hardware IP phone.
Try to avoid direct SIP connections to your PBX or allow them only from certain IP addresses specified in the firewall.
When installing 3CX, the Initial Setup Wizard asks which countries you want to allow outgoing calls to. The same list of countries can be seen (and changed) in the Settings - Security - Allowed international country codes section. Only those countries (prefixes) where your users really call should be allowed. By default, 3CX only allows calls to the country that was specified as the location for the exchange.
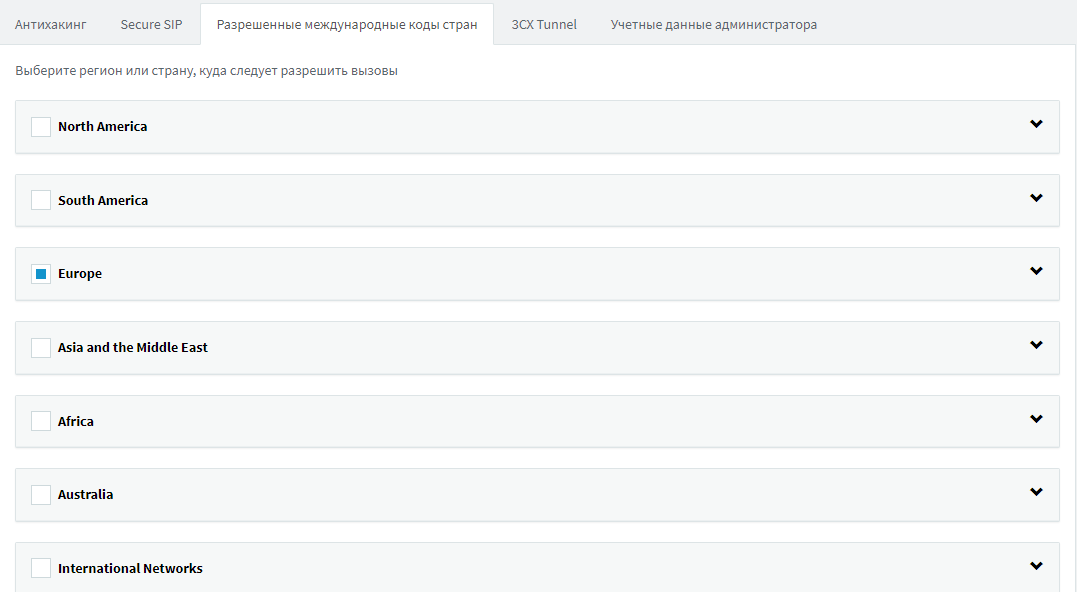
A very dangerous practice is to allow all countries to install automatic telephone exchanges, and to limit them later. Usually they forget about this, allowing the attacker to call in all directions as soon as he received the credentials of the PBX user.
Another bad practice is to use too general outgoing rules that allow any user (3CX Default organizational group) to call in any allowed direction. Some administrators, in order not to complicate their lives, create one universal rule for this.
In fact, you should create outgoing rules with the minimum necessary permissions, according to the same principle by which they are created, for example, in a firewall. Specifically list the prefixes, specify the minimum and maximum length of the number, clearly indicate the groups of extension numbers that are allowed to call in this direction.
In the Parameters - Numbers section E164, the processing of numbers is defined, in which the "+" symbol at the beginning of the number is replaced by the international dialing code. Substitution rules are defined for the country that is indicated as the place of installation of the telephone exchange. In most countries, “+” is replaced by 00, and for America, by 011. The substitution is in accordance with ITU standards.
The E164 parameters are important because it is used to determine the forbidden directions (prefixes) that we discussed above. For example, if a blocked country is Albania, 3CX will analyze and block numbers starting with 00355xxx and + 355xxx.

If you incorrectly entered the international dialing code for your country, this will lead not only to the erroneous substitution "+", but also to the malfunctioning of the country blocking function.
In 3CX v16 two interesting security features have been added.
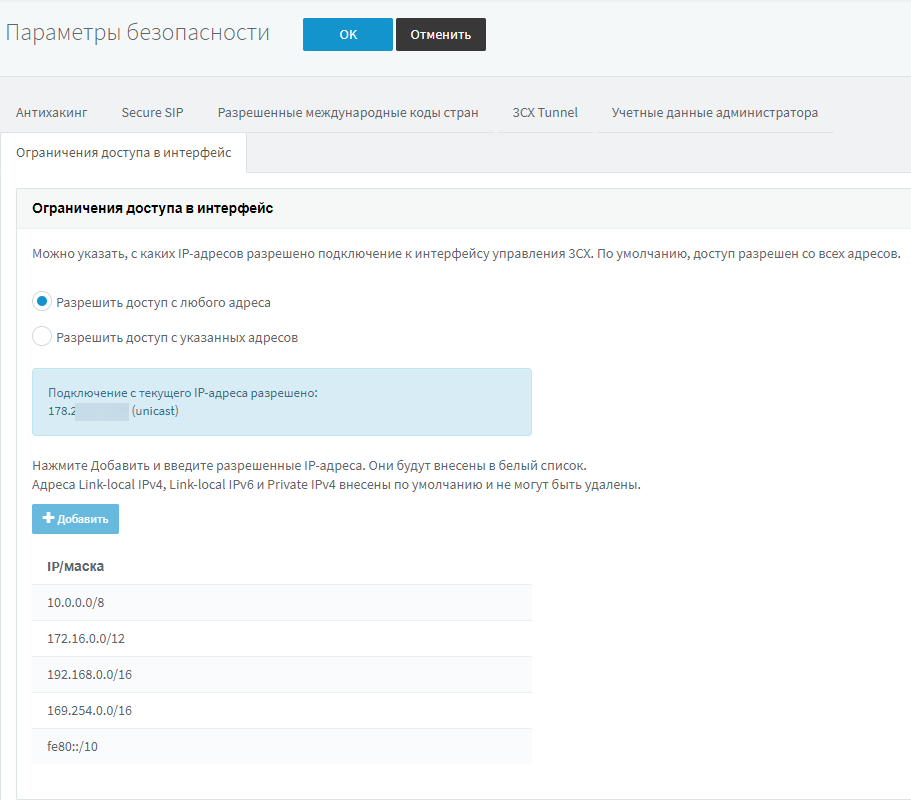
The first is restricting access by IP address to the 3CX management interface. It is configured in the Settings - Security - Restrict access to the interface section. By default, all IP addresses are allowed, but if IP protection is enabled, access will be allowed only from the local network and explicitly specified external IP addresses. Please note that this restriction does not affect the operation of other 3CX web services, such as auto-tuning phones, web client, etc.
The second security feature is the self-learning global IP blacklist maintained by 3CX. It is included in the Settings - Security Settings - Antihacking section. If this option is enabled, the PBX will automatically transmit information about suspicious activity, including the source IP address, to our central server. After analyzing the event, information about this IP address will be automatically transmitted to all 3CX systems in the world that also have this feature enabled. Thus, suspicious traffic will be blocked due to the “collective intelligence”. Today, our global list already contains more than 1000 IPv4 IP addresses from which attempts to scan or crack have been consistently repeated. We highly recommend enabling this feature on your PBX!

We noticed that hacking the system is immediately preceded by several errors taken together. We practically did not observe situations when serious consequences arose only due to one mistake.
Well, if you’ve been hacked, don’t panic! It is very important to collect server logs before taking radical actions. Subsequently, this will help to conduct a quality investigation of the incident. To collect logs, go to the Support - Create a file for technical support section. A zip archive will be generated, a link to which will be sent to you by e-mail. Attach this file and incident description to 3CX Technical Support.

You should contact technical support if you have any reasonable questions about 3CX security or want to report a hack that has already taken place. To understand the situation and get the necessary recommendations, open an appeal in the Security - Fraud category. These requests are considered with the highest priority. You can also get 3CX security advice on our user forum .
How do telephone scammers work?
Telephony fraud is pretty commonplace - outsiders or a robot diver make calls through your PBX at your expense. This usually happens late at night or on non-working days. Calls last as long as possible, with high frequency and to the most expensive international destinations. And at the end of the month you receive an invoice from the telecom operator for a huge amount, which you must pay, or dispute in court.
Calls to the most expensive international destinations were the main goal of hackers in the early period of the development of software exchanges. You might think that this type of fraud is a thing of the past, especially given the cost of international negotiations. However, this is currently being done by well-organized international groups that plunder customers and operators on an industrial scale.
Now PBXs are being hacked in order to make thousands of calls to “expensive” numbers of various paid automatic services that are controlled by the same scammers. In this case, the attacker makes a profit in the form of a commission from the operator for every minute of a paid call. This fraud is also called the International Revenue Sharing Fraud (IRSF).
Another way to make illegal money is to sell stolen SIP client credentials on "clandestine" online exchanges. Further, such access is used in different ways - either for competition with legal telecom operators, due to which it is possible to sell minutes much cheaper than the market price, or for some personal needs of the buyer.
3CX has several security levels whose default settings prevent most known attack types. However, some system administrators change or disable these settings without even realizing what the consequences are.
Let's look at the most common security settings that 3CX administrators make.
Weak user credentials
The first mistake is the “weak” account credentials used by 3CX applications, IP phones and users.
When you create a user (extension) in 3CX, secure credentials are automatically generated for him at all access levels. These are complex SIP and web client logins, randomly generated passwords for accessing the web interface of IP phones, random voicemail PINs, etc. Be sure to use only these secure credentials because random long passwords guarantee protection against attacks password guessing (also called brute force attacks).
Starting with 3CX v15.5, the system will not allow you to set the extension password weaker than required by modern security rules. However, often weak account passwords are inherited from backups of previous versions of 3CX. Therefore, now 3CX warns the administrator if extension numbers with weak passwords are present in the system - a warning appears near such numbers. If you hover over it, additional information appears.

By the way, we strongly do not recommend setting weak passwords for testing purposes. As a rule, people forget to change them and leave the PBX “full of holes”.
Enabled SIP Remote Access to Extension
The second mistake is to disable the option “Deny connection from the public network” and not turn it back on when the user no longer needs it.

This option is included in 3CX by default and prevents registration of any users outside of your local network. Please note that you can use applications or the 3CX web client without enabling remote access, since they use tunneling technology to connect to the PBX. This option should be disabled only if someone needs a direct SIP connection for a hardware IP phone.
Try to avoid direct SIP connections to your PBX or allow them only from certain IP addresses specified in the firewall.
Lots of allowed calls
When installing 3CX, the Initial Setup Wizard asks which countries you want to allow outgoing calls to. The same list of countries can be seen (and changed) in the Settings - Security - Allowed international country codes section. Only those countries (prefixes) where your users really call should be allowed. By default, 3CX only allows calls to the country that was specified as the location for the exchange.

A very dangerous practice is to allow all countries to install automatic telephone exchanges, and to limit them later. Usually they forget about this, allowing the attacker to call in all directions as soon as he received the credentials of the PBX user.
Outbound rules too loose
Another bad practice is to use too general outgoing rules that allow any user (3CX Default organizational group) to call in any allowed direction. Some administrators, in order not to complicate their lives, create one universal rule for this.
In fact, you should create outgoing rules with the minimum necessary permissions, according to the same principle by which they are created, for example, in a firewall. Specifically list the prefixes, specify the minimum and maximum length of the number, clearly indicate the groups of extension numbers that are allowed to call in this direction.
Invalid processing parameters E164
In the Parameters - Numbers section E164, the processing of numbers is defined, in which the "+" symbol at the beginning of the number is replaced by the international dialing code. Substitution rules are defined for the country that is indicated as the place of installation of the telephone exchange. In most countries, “+” is replaced by 00, and for America, by 011. The substitution is in accordance with ITU standards.
The E164 parameters are important because it is used to determine the forbidden directions (prefixes) that we discussed above. For example, if a blocked country is Albania, 3CX will analyze and block numbers starting with 00355xxx and + 355xxx.

If you incorrectly entered the international dialing code for your country, this will lead not only to the erroneous substitution "+", but also to the malfunctioning of the country blocking function.
New security features in 3CX v16
In 3CX v16 two interesting security features have been added.
The first is restricting access by IP address to the 3CX management interface. It is configured in the Settings - Security - Restrict access to the interface section. By default, all IP addresses are allowed, but if IP protection is enabled, access will be allowed only from the local network and explicitly specified external IP addresses. Please note that this restriction does not affect the operation of other 3CX web services, such as auto-tuning phones, web client, etc.

The second security feature is the self-learning global IP blacklist maintained by 3CX. It is included in the Settings - Security Settings - Antihacking section. If this option is enabled, the PBX will automatically transmit information about suspicious activity, including the source IP address, to our central server. After analyzing the event, information about this IP address will be automatically transmitted to all 3CX systems in the world that also have this feature enabled. Thus, suspicious traffic will be blocked due to the “collective intelligence”. Today, our global list already contains more than 1000 IPv4 IP addresses from which attempts to scan or crack have been consistently repeated. We highly recommend enabling this feature on your PBX!

Conclusion
We noticed that hacking the system is immediately preceded by several errors taken together. We practically did not observe situations when serious consequences arose only due to one mistake.
Well, if you’ve been hacked, don’t panic! It is very important to collect server logs before taking radical actions. Subsequently, this will help to conduct a quality investigation of the incident. To collect logs, go to the Support - Create a file for technical support section. A zip archive will be generated, a link to which will be sent to you by e-mail. Attach this file and incident description to 3CX Technical Support.

You should contact technical support if you have any reasonable questions about 3CX security or want to report a hack that has already taken place. To understand the situation and get the necessary recommendations, open an appeal in the Security - Fraud category. These requests are considered with the highest priority. You can also get 3CX security advice on our user forum .
