How to increase security in personal identification and access control systems

We already wrote about how to use the video surveillance system to control the perimeter and the situation inside the warehouse, store, parking lot and other facilities. But any security system gives the maximum effect only if it uses several technologies at the same time. And we will consider just such a synergy further.
We must say right away that we did not set as our goal to cover all technologies of video surveillance systems and access control in a short article. Our goal is to show how, by combining various technologies, to increase the level of security of the protected object.
He sees an eye ...

No modern store is complete without cameras. They help the director not only stop various illegal actions, but also quickly resolve conflict situations.
We have already talked about how, with the help of our system, you can control the cash register area and fight queues. And now we’ll dwell in more detail on the issues of combating theft in the trading floor and controlling access to office premises.
The head of the security service (SB) of a large store revealed to us professional secrets.
The trading floor of the store occupies two floors, plus there are warehouses in the basement, and a parking lot on the street. The company also has several remote warehouses. Naturally, when developing a security system, the task arose to gain full control over all protected objects. According to our interlocutor, it is not difficult to block the entire territory of the trading floor with cameras, which was done.
In the halls and at the box office, about 30 cameras are now installed that carry a constant “watch” and help the security guard monitor emergency situations. To monitor the parking lot, cameras are also installed, and in places with zero lighting at night, infrared spotlights are used.
On monitoring the footage coming from the trading floor, three women-operators work. According to the head of the Security Council, women are better at doing the routine work of monitoring monitors.
But that is not all. It is clear that not a single camera provides absolute protection against theft. Video surveillance is great, but after all, attackers often go into the store, who carefully study the installation locations of the cameras before committing the theft. And to combat such intruders, face recognition technology is ideal, because once in the field of vision of the camera once, the intruder is blacklisted. When it appears, the camera operator immediately receives a signal about the presence of an unwanted guest in the hall.
In addition to technical means of control in the trading premises there are full-time operational staff. Operatives monitor the order and receive information from the operators.
Sim-Sim, open up
When installing the security system, the store management immediately had a question of controlling access of personnel to the storehouse and to remote stores. After analyzing the various solutions that are on the market, the management settled on a combination of two technologies for protecting doors and turnstiles, namely Smart cards and face recognition.
The first method has long been used as part of access control and management systems. Ivideon is integrated into GuardSaas and RusGuard access control and management systems (ACS) , which allows you to configure reactions in the system (video recording of any ACS events) with the possibility of their associated viewing directly from the logs.
The choice of a combination of smart access cards and face recognition for ACS is explained very simply.
Smart card readers and the cards themselves are highly reliable, relatively inexpensive, easy to set up and resistant to mechanical stress.
We were told that one employee carried a card on a cord and, bending over, accidentally lowered it into an office shredder. Apparently, his cutters did not damage the antenna, and the card did not fail. Well, and from the stories about trampled in the mud, drowned in water and continuing to work maps, you can collect a whole collection.

When trying to establish control over the working hours of employees, especially those located in remote warehouses, using the Smart-card system, the management quickly found out that the system was easily fooled. After all, this is a regular store, and if an employee hands over his card to a colleague and asks him to fix the departure on time, and leaves early, then on an electronic time sheet he will be at work full time, but actually less.
And that is why it was decided to combine the technology of Smart-cards and face recognition. The combination of these two methods gave an excellent result: even if a dishonest employee tries to leave work earlier and does not fix it with a card, the camera will automatically track his departure.
Biometric control

©
On a real-life example of a store, one can clearly see how important it is for a business not only to obtain visual information about the operation of an object, but also to differentiate access levels for various employees in office premises.
Using smart card technologies today is the easiest way to control access to office space. Instead of cards, various key fobs can be used, both contact and non-contact.
These devices have one significant drawback: they are in no way associated with the specific employee to whom they were issued. Therefore, in order to gain access to a secure room, just take hold of a card or key fob.
Of course, protecting the card with a PIN code improves the situation a little, but this only works with self-discipline, because most people like to write a PIN on the card itself “so that it is always at hand.”
Therefore, in cases where it is necessary to provide increased protection of the premises against unauthorized entry, biometric access control systems come to the rescue.
We want to say right away that there is no system that will provide you with complete protection against penetration into the security zone. But when an attacker tries to penetrate, he will lose valuable time and will inevitably make mistakes, and this will give a good chance for the security service to quickly respond to the incident.
Put your finger
©
Everyone knows that the imprint of papillary lines on the fingers is unique to each person and provides almost unmistakable identification. And most importantly, the figure is almost independent of the state of human health, in contrast, say, to the voice. Therefore, fingerprint scanners were the first to enter the market for access control systems.
In the scanner sensor, the matrix of LEDs illuminates the finger, and the digital camera at this moment takes a photo of the fingerprint. Next, the image is processed by mathematical algorithms that evaluate its quality and generate information about the owner, which will be entered into the database.
As in forensics, all the main patterns of papillary lines are divided into three types by the program: arc, loop and curlicue. The task of the algorithm is to first determine the type of pattern, and then search for the minute, as professionals call the place where the pattern ends. It is the minutes and their locations that determine the uniqueness of the prints. The scanner recognizes their relative position and the pattern formed by them, which is divided by the program into small zones, including a fixed number of minutes.
Note that not one, even the most complex, scanner checks all the lines of patterns. He searches only certain patterns in the blocks and compares them with the values in the database. If they match, then the print belongs to one person.
Now the variety of models of fingerprint readers on the market in the hundreds. There are various types of scanners at your service, from the simplest ones, from the “finger and enter” series, to complex combined devices that may, for example, require the introduction of a special code, pronounce a passphrase or confirm authority using a Smart-card.
Any modern scanner is capable of storing in its memory information about hundreds of thousands of fingerprints of employees, and can easily be integrated into both access control systems and the staff time tracking program.
For lovers of detective stories and spy movies, let's say that tricking modern devices is quite difficult. Forget your favorite fingerprint transfer toner from a laser printer to tape! You just get dirty, and scanners have stopped responding to this “fool” already 15 years ago. So leave this trick to action scriptwriters and actors.
A serious scanner, also loved by filmmakers, with an amputated finger is not fooled. Powerful expensive scanners can distinguish living tissue from dead tissue. And what can happen with an inexpensive scanner built into a smartphone, a serious device will ignore or raise an alarm.
Of course, on the Internet you can still find quite a few ways to “deceive” the fingerprint scanner, in addition to those described by us, but you should not think that the developers of these devices are idle. If the hacking technology is published, then it can be argued that with a high degree of probability the creators of these devices have already found a way to deal with it. Or just about to find.
By the way, fingerprint scanners are used not only in special services or banks. We quite often came across these devices in ordinary offices. So, this technology has long passed from the category of exotic to everyday life for business.
Show your hand
©
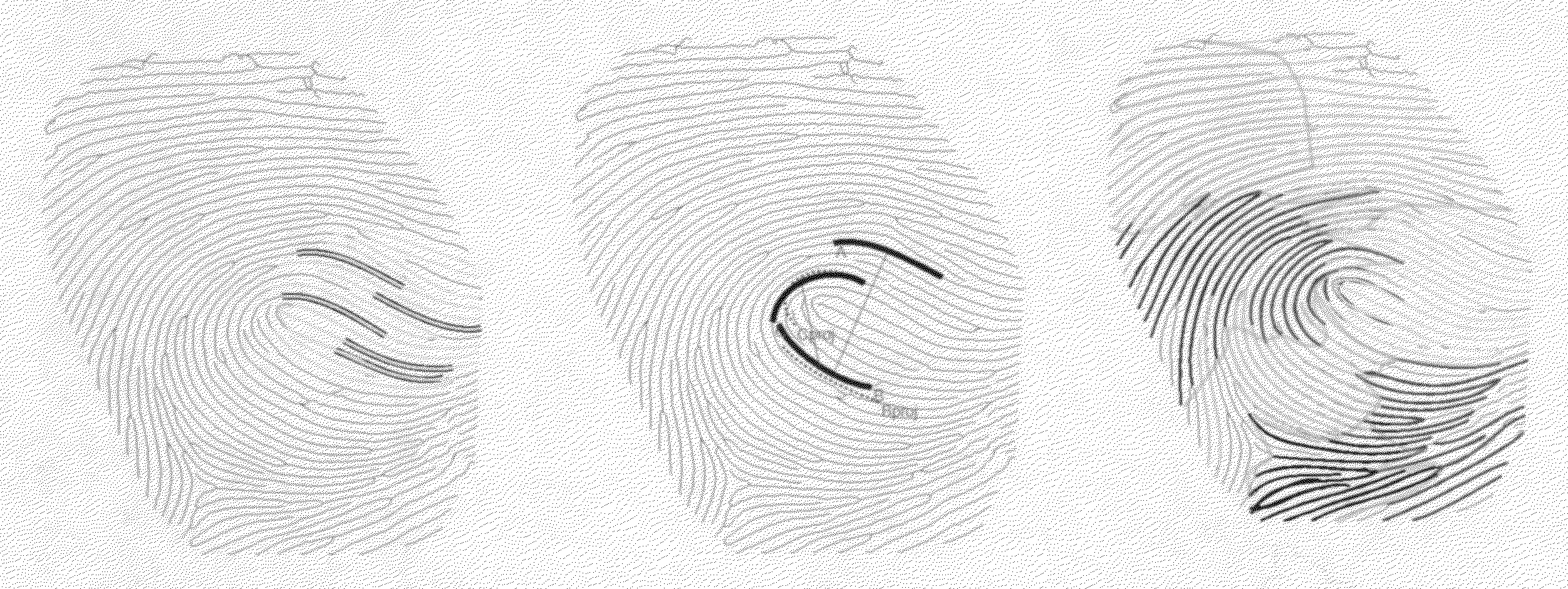
The next most popular authentication method is scanning the veins in the palm of your hand. There are quite a few devices of this type on the market.
As in the case of using a fingerprint scanner, control “prints” of all persons allowed into the room are recorded in the device’s memory or on the server. And if it is necessary to strengthen protection, you can purchase a combined reader, which requires, for example, additional confirmation of incoming credentials using a personal code or a smart card.
At the time of this writing, we were able to find only one way to deceive this system.
Engineers Jan Krissler and Julian Albrecht of Berlin Technical University have proposed a very simple and effective way to “inflate” a scanner. They transferred the drawing of the veins of the palm onto the paper and covered it with a layer of red wax; The scanner could not recognize the fake print. More details in the video:
This method is suitable for the laboratory, but not very useful in real life, since it requires serious preparation.
Your eye is your pass
©
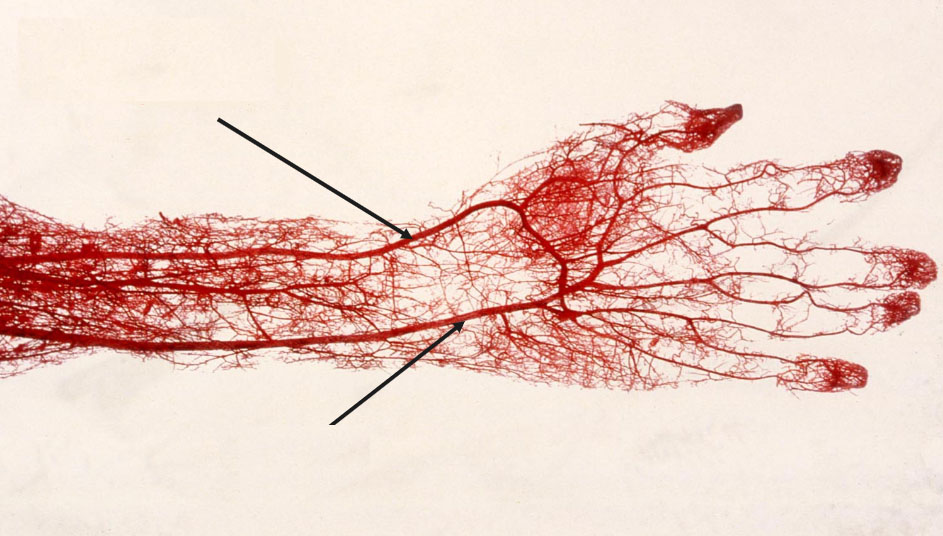
So, we got to the "protagonist" of most spy and adventure films: an iris scanner. Like fingerprints, each person’s iris pattern is unique. That is why it is also an important factor in biometric identification. Unlike fingerprints, faking an iris pattern is almost impossible, plus, according to studies, it is not subject to age-related changes.
When scanning the iris, the eye is irradiated with near-infrared radiation, and the integrated digital camera captures the pattern of the iris. Then, mathematical algorithms come into play that analyze and process the photo.
Note that the use of infrared rays during scanning allows devices to work in complete darkness. Ordinary glasses and contact lenses will not become an obstacle for the scanner.
From the description of the principle of operation of the device, we can make the erroneous conclusion that we are faced with an absolutely hacking-resistant system. If we leave fingerprints or palm prints almost everywhere, and you can easily get them and try to use to break into the biometric authentication system, then we certainly do not “spot” the iris pattern anywhere. According to experts, any protection system can be hacked, the only question is the time and resources that are needed for this.
And since the iris scanners began to be embedded in ordinary smartphones, the number of people wishing to experience such protection for strength has increased significantly.
In particular, we managed to find a description of the way in which the specialists at Chaos Computer Club managed to trick the iris scanner installed in the Samsung Galaxy S8 smartphone. Using a conventional camera, printer and contact lens, they broke into biometric protection and gained access to data on the smartphone. For details, follow the link .
Say "aaaaa"
©
Now let's talk about voice recognition systems. Attempts to recognize a person by voice have been made for a very long time. Paradoxical as it sounds, the more serious the technical and software methods for processing sound become, the less reliable this method of recognition becomes. However, judge for yourself.
Any voice recognition system is a combination of a sensitive microphone with an amplifier and a digital signal processor ( DSP ), “sharpened” for processing and analysis of information received from the microphone. And it is the built-in DSP algorithms that provide reliable user identification and protect the system from hacking.
Yes, the timbre of the voice, its spectral composition, manner of speech, the methods of pronunciation of phrases each of us has his own. But if fingerprints remain on any subject that we touch, then the situation with the voice is even worse. His sample can be obtained without much straining.
Even if you need to say a certain phrase to access the room, no one bothers the attacker to compose it from separate words in any audio editor, and then play it into the reader’s microphone, using, for example, your smartphone.
Another disadvantage of voice recognition systems is the exposure of the voice to age-related changes, various injuries to the face and larynx, and its distortion during illness. Given all of the above, human voice authentication systems are rarely used separately. They are most effective when working in dual identification systems, where they can complement, for example, a fingerprint scanner or palm.
Hardware face control

© Vasya Lozhkin
Due to the massive use in smartphones, the technology of user authentication using three-dimensional face photographs has become very popular.
Already now, some retail chains are testing the possibilities of organizing fully autonomous stores in which there are no familiar sellers and cashiers. Agree that a similar structure of outlets requires a different approach to work and security services.
It is easy to imagine a store selling luxury watches or jewelry in the club system. Before visiting such a salon, you will be asked to provide your biometric data in advance, and only after scanning them at the entrance will the doors swing open in front of you. Then, taking into account your interests, the holographic guide will show you the most suitable assortment of products, and you can choose and try on the model you are interested in.
Payment of the purchase, of course, will also be made using biometric authentication.
If this approach seems fantastic to you, remember that recently the head of Sberbank G. Gref announced the imminent transition of the company to biometric customer identification. Other banks do not stand aside from this initiative.
Already now, many of them can voluntarily submit their biometric data and use them instead of a passport in the future. So the times when we submitted our passports to bank employees will soon become history!
Instead of a conclusion
The maximum protection of the facility is ensured by the combined use of several technologies - for example, Ivideon ACS . So far, developers have not created a single ideal system that guarantees one hundred percent protection against hacking or fraud. But the use of several systems together can significantly complicate the life of the attacker and give the security service a temporary head start to identify and suppress attempts to penetrate the object.
