Security Week 07: Local IoT Device Vulnerabilities
In the traditional rubric of “what else is wrong with IoT,” last week a scientific study of specialists from American University of Michigan and the Brazilian Federal University of Pernambuco was added. As part of the study, 96 IoT devices for smart homes from the list of best-selling sites on the Amazon site were studied. Scientists have analyzed applications for managing these devices from a smartphone, both manually and using automated tools for analyzing network communications. First of all, we looked for vulnerabilities that allow us to seize control of IoT devices due to an inadequately secure connection.

For 96 different devices, we managed to assemble 32 unique control applications. Of these, half either do not encrypt traffic when working with IoT, or use fixed encryption keys. Accordingly, not only the owner can control the devices, but anyone else, with one reservation - if there is access to the local network. The study in PDF is here , a summary in Russian is in this news . We will focus on the most interesting details of the work.
Unlike a generic safety study, usually focused on the specific vulnerability of a particular device, the Brazilian and American scientific work offers a comprehensive approach. It can theoretically be used to assess the security of any IoT devices capable of connecting to the Internet and / or local network. The approach turned out to be the following: we will limit ourselves to the study of control applications and how they interact with the devices of the smart home. Gaps in the devices themselves are not taken into account - it is assumed that if the client part is vulnerable, then you can not dig, and everything is bad enough.
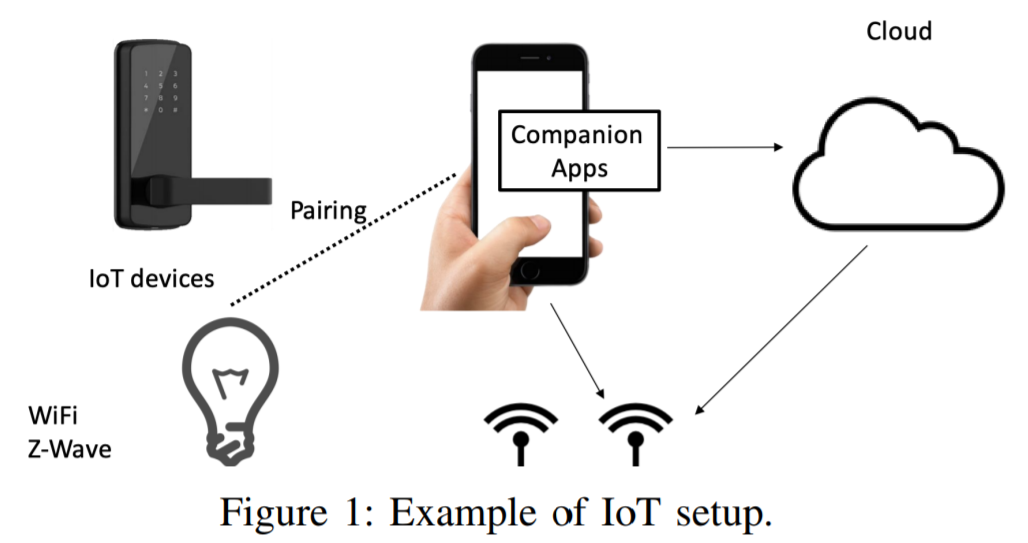
The operation scheme of a typical device, such as a video surveillance camera, involves interaction with a smartphone via a controller — either directly via a local network or through a cloud system on the manufacturer’s side. To begin with, the researchers purchased the five most popular smart home devices and studied them manually. Problems were immediately detected - for example, with such a remotely controlled TP-Link socket:

The initial setup of the device through the application on the smartphone is completely unencrypted. In normal operation, data encryption is provided, but the encryption key is the same for all devices in the series. To confirm the practical consequences of this approach, the researchers posted a video confirming the possibility of intercepting control over the device. The study of the five devices allowed us to formulate questions, the answers to which were later found using (mostly) an automated analysis system:
The answers for the four selected applications are the following:

Kasa Smart is an application for TP-Link devices, such as the smart socket above. LIFX is a manufacturer of remote controlled light bulbs. WeMo is being developed by Belkin, and e-Control by BroadLink , in both cases it is about controlling lighting and electrical appliances, televisions and household appliances via infrared, as well as security systems. In the case of WeMo, the researchers found the lack of encryption and any authorization when communicating with devices on the local network. Intercepting network packets, scientists were able to create a script that manages Belkin smart devices without the knowledge of the owner.

General research results: 16 applications either do not use encryption, or they are encrypted using a fixed key. 18 applications communicate with devices over a local network, 14 communicate only through the manufacturer's server. 6 applications use vulnerable communication protocols. The Register has requested comments from the companies mentioned in the study. The commentary of the manufacturer of smart bulbs LIFX boils down to the fact that the company is looking for a balance between security and convenience, and this is, in general, a key problem for IoT devices.
Communication directly between devices (or a controller) and a smartphone over a local area network protects the user from a sudden bankruptcy of the manufacturer or the termination of support for outdated devices. If your IoT is tied to a cloud in such a situation, you are alone with a non-working piece of hardware. But the manufacturers' argument that there is no need to protect communications in the local network is also controversial. The local network can be hacked, it is also possible to compromise a device that has access to it. Multiple vulnerabilities of routers, the settings in which can be changed by opening the correct link in the browser, confirm this.
The study provides examples of "correct" devices in which interaction with the control application occurs only through the cloud system, with the necessary level of encryption of the transmitted data. These are products of Nest and EZVIZ. It also implements a relatively safe way to initialize the device. In the first case, this is a random authorization code displayed on the device screen. In the second case, a unique authorization string is applied to the device in the form of a QR code that needs to be scanned.
The priorities set by researchers in this work can be challenged, as well as ideas about the correct approach to protecting communications of smart home systems. At a minimum, the study confirms once again that it is not worth consciously lowering the protection of communication channels even in a local network. The consequences can be serious, especially if unsafe methods are using smart alarms or an internet-connected door lock.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.

For 96 different devices, we managed to assemble 32 unique control applications. Of these, half either do not encrypt traffic when working with IoT, or use fixed encryption keys. Accordingly, not only the owner can control the devices, but anyone else, with one reservation - if there is access to the local network. The study in PDF is here , a summary in Russian is in this news . We will focus on the most interesting details of the work.
Unlike a generic safety study, usually focused on the specific vulnerability of a particular device, the Brazilian and American scientific work offers a comprehensive approach. It can theoretically be used to assess the security of any IoT devices capable of connecting to the Internet and / or local network. The approach turned out to be the following: we will limit ourselves to the study of control applications and how they interact with the devices of the smart home. Gaps in the devices themselves are not taken into account - it is assumed that if the client part is vulnerable, then you can not dig, and everything is bad enough.

The operation scheme of a typical device, such as a video surveillance camera, involves interaction with a smartphone via a controller — either directly via a local network or through a cloud system on the manufacturer’s side. To begin with, the researchers purchased the five most popular smart home devices and studied them manually. Problems were immediately detected - for example, with such a remotely controlled TP-Link socket:

The initial setup of the device through the application on the smartphone is completely unencrypted. In normal operation, data encryption is provided, but the encryption key is the same for all devices in the series. To confirm the practical consequences of this approach, the researchers posted a video confirming the possibility of intercepting control over the device. The study of the five devices allowed us to formulate questions, the answers to which were later found using (mostly) an automated analysis system:
- Is the "default" encryption key specified in the firmware used?
- Is the direct connection between the device and the smartphone over a local network used?
- Is the application and device broadcasting messages over the network?
- Is a known vulnerable communication protocol used?
The answers for the four selected applications are the following:

Kasa Smart is an application for TP-Link devices, such as the smart socket above. LIFX is a manufacturer of remote controlled light bulbs. WeMo is being developed by Belkin, and e-Control by BroadLink , in both cases it is about controlling lighting and electrical appliances, televisions and household appliances via infrared, as well as security systems. In the case of WeMo, the researchers found the lack of encryption and any authorization when communicating with devices on the local network. Intercepting network packets, scientists were able to create a script that manages Belkin smart devices without the knowledge of the owner.

General research results: 16 applications either do not use encryption, or they are encrypted using a fixed key. 18 applications communicate with devices over a local network, 14 communicate only through the manufacturer's server. 6 applications use vulnerable communication protocols. The Register has requested comments from the companies mentioned in the study. The commentary of the manufacturer of smart bulbs LIFX boils down to the fact that the company is looking for a balance between security and convenience, and this is, in general, a key problem for IoT devices.
Communication directly between devices (or a controller) and a smartphone over a local area network protects the user from a sudden bankruptcy of the manufacturer or the termination of support for outdated devices. If your IoT is tied to a cloud in such a situation, you are alone with a non-working piece of hardware. But the manufacturers' argument that there is no need to protect communications in the local network is also controversial. The local network can be hacked, it is also possible to compromise a device that has access to it. Multiple vulnerabilities of routers, the settings in which can be changed by opening the correct link in the browser, confirm this.
The study provides examples of "correct" devices in which interaction with the control application occurs only through the cloud system, with the necessary level of encryption of the transmitted data. These are products of Nest and EZVIZ. It also implements a relatively safe way to initialize the device. In the first case, this is a random authorization code displayed on the device screen. In the second case, a unique authorization string is applied to the device in the form of a QR code that needs to be scanned.
The priorities set by researchers in this work can be challenged, as well as ideas about the correct approach to protecting communications of smart home systems. At a minimum, the study confirms once again that it is not worth consciously lowering the protection of communication channels even in a local network. The consequences can be serious, especially if unsafe methods are using smart alarms or an internet-connected door lock.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
