PVS-Studio 7.00
 Today is an important day - after 28 releases of the sixth version, we release PVS-Studio 7.00, where the key innovation is support for the Java language. However, in 2018, there were many other important changes regarding C ++, C #, infrastructure and support for coding standards. Therefore, we bring to your attention a note that summarizes the main changes that have occurred in PVS-Studio lately.
Today is an important day - after 28 releases of the sixth version, we release PVS-Studio 7.00, where the key innovation is support for the Java language. However, in 2018, there were many other important changes regarding C ++, C #, infrastructure and support for coding standards. Therefore, we bring to your attention a note that summarizes the main changes that have occurred in PVS-Studio lately.PVS-Studio is a tool for detecting errors and potential vulnerabilities in the source code of programs written in C, C ++, C # and Java. Works on Windows, Linux and macOS.
The analyzer's capabilities are well demonstrated by an extensive collection of errors in the code that we found in the process of checking various open projects.
We will start with the change, because of which, in fact, it was decided to change the version number from 6.x to 7.x. This is support in the Java language analyzer, for which we have been preparing for a long time .
Java
The most important thing about Java analyzer is that it appeared :). We invite Java developers to download the tool and check out the projects they are working on.
We have made available to users the most popular ways to integrate the analyzer into the build system:
- Plugin for maven.
- Plugin for gradle.
- Plugin for IntelliJ IDEA.
In the case of using samopisnyh assembly systems, it is possible to run the analyzer directly by listing the source code and the classpath .
You can find detailed information on all methods of launching the analyzer on the " How to run PVS-Studio Java " documentation page .
We could not ignore the SonarQube code quality control platform, which is so popular among Java developers, so we added Java language support to our SonarQube plugin .
C, C ++
In 2018, our team actively worked on the development of a C ++ analyzer. There are many new diagnostics, as well as improved algorithms that allow you to collect and process information extracted from the syntax tree.
CWE, CERT
Analyzer C ++ messages (as well as C # analyzer) were classified according to the Common Weakness Enumeration ( CWE ). CWE is a classification system for potential and proven vulnerabilities. It is supported by the community to identify software problems and create automated tools that can be used to identify and fix these problems.
Additionally, messages were classified according to CERT C Coding Standard and CERT C ++ Coding Standard.SEI CERT Coding Standards is a set of standards for writing software (software) in C, C ++, Java and Perl, developed by the CERT Coordination Center (CERT Coordination Center, CERT / CC) to improve software reliability and security.
The classification of C and C ++ diagnostics according to these warnings allows using PVS-Studio as an SAST solution .
MISRA
In 2018, the PVS-Studio static code analyzer began to classify its warnings according to the MISRA C and MISRA C ++ standards. Thanks to the support of these standards, it has become possible to effectively use the analyzer to improve the security, portability and reliability of programs for embedded systems.
Read more: "PVS-Studio: support of MISRA C and MISRA C ++ coding standards ".
MISRA support became relevant due to the development in the analyzer of support for various embedded systems, which will be discussed in the next section of the article.
Embedded Development
In 2018, the PVS-Studio analyzer supported :
- Windows IAR Embedded Workbench, C / C ++ Compiler for ARM C, C ++
- Windows / Linux. Keil µVision, DS-MDK, ARM Compiler 5/6 C, C ++
- Windows / Linux. Texas Instruments Code Composer Studio, ARM Code Generation Tools C, C ++
- Windows / Linux / macOS. GNU Arm Embedded Toolchain, Arm Embedded GCC compiler, C, C ++
Two notes on the topic of support for embedded systems:
- The PVS-Studio 6.22 static code analyzer is adapted for ARM compilers (Keil, IAR) .
- Support for GNU Arm Embedded Toolchain has been added to PVS-Studio .
Extending user annotations
Sometimes, projects use their own implementations of various system functions, for example, memcpy , malloc , etc. The analyzer is very good at finding errors using standard functions, but in the user code it was impossible to use such algorithms until recently. Now, using the V_FUNC_ALIAS annotation , you can assign the names of your functions to the corresponding system ones.
Comment format:
//V_FUNC_ALIAS, implementation:sysf, function:f, namespace:ns, class:c- Key implementation - sets the name of the standard function for which the alias is defined.
- Key function - sets the name of the alias. The signature of the function whose name is specified in this key must match the signature of the function specified in the implementation key.
- The class key is the name of the class. May be absent.
- The namespace key is the name of the namespace. May be absent.
Consider an example:
//V_FUNC_ALIAS, implementation:memcpy, function:MyMemCpyNow the analyzer will handle calls to the MyMemCpy function in the same way as calls to memcpy . For example, on such a code will be issued a warning V512:
int buf[] = { 1, 2, 3, 4 };
int out[2];
MyMemCpy (out, buf, 4 * sizeof(int)); // Warning!C #
This year there were no significant changes to the C # analyzer. There were separate improvements in diagnostics and correction of defects. The messages of the C # analyzer, as well as the C ++ analyzer, were classified according to the Common Weakness Enumeration ( CWE ). Correspondence of C # diagnostics with CWE identifiers is given here (see diagnostics with 3xxx numbers).
We plan to return to a more active development of the C # analyzer in 2019. It is planned to develop new diagnostics and improve the mechanism of data flow analysis (Data-Flow Analysis).
Report Converters
The PlogConverter.exe and plog-converter utilities are included in the PVS-Studio distributions for Windows and Linux / macOS, respectively. Also the source code for these utilities is available on GitHub .
With the advent of PVS-Studio for Java, we reworked the code highlighting for C, C ++, C # and added Java in FullHtml format ( for a web browser ).
Also for the report in this format was added column MISRA:
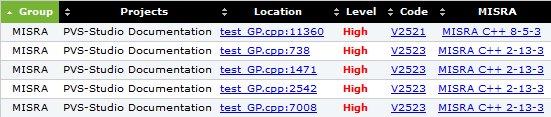
Like the CWE ID, the MISRA column is optional and is included by code security researchers when examining the analysis results.
SonarQube Plugins
1. Full update
We rewrote our plugins using the new API. This made it possible to add new functionality and ensure compatibility with SonarQube 7.x. The minimum supported version is now SonarQube 6.7 LTS .
2. PVS-Studio for Java
A new version of plug-ins has been added diagnostic support for the Java language. Now you can add PVS-Studio to other quality control tools of your Java project.
3. MISRA Standard
We recently announced support for the MISRA C and MISRA C ++ standards. New plug-ins also have their support. For example, a parameter was added (in addition to CWE):
sonar.pvs-studio.misra=activewhich includes adding the MISRA identifier to the analyzer alerts:
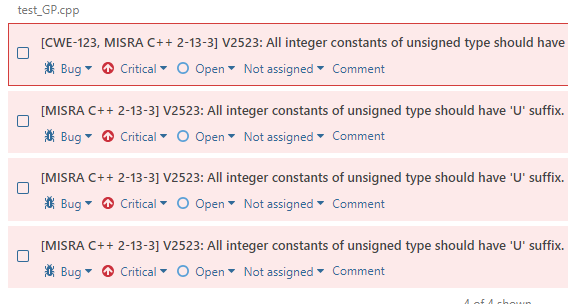
Regardless of this setting, the search for misra and pvs-studio # misra tags will be available in the analysis results. Information about the number of found warnings MISRA was added to the metrics, which will be discussed further.
4. New metrics
In the Projects -> Your Project -> Measures menu , various code metrics are available, among which there is now various information from PVS-Studio:
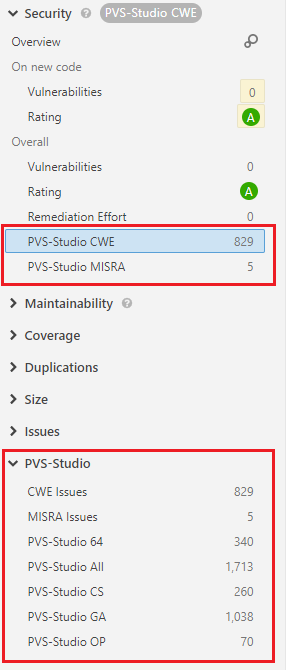
For each of the metrics, you can build graphs and monitor the dynamics of the appearance of certain warning groups of the analyzer.
4. Multiline transitions
Some analyzer diagnostics give warnings on several lines of a file. Sometimes they are very far from each other. In the new version we added multiline transitions:
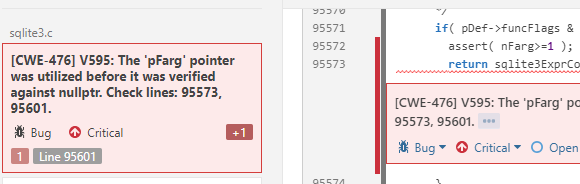
SonarQube also supports transitions between different files. Later we will add such transitions for diagnostics, in which there is an intermodular analysis.
6. Documentation
Documentation has undergone great changes. PVS-Studio is a cross-platform and multilanguage product, so all the reworkings were aimed at writing more general and understandable instructions for working on a particular system.
SAST
Until recently, in our articles we positioned PVS-Studio as a tool for detecting errors in the code. At the same time, we almost did not consider PVS-Studio in the security context. This year we corrected this situation and took a look at the tool in terms of testing application security and DevSecOps practices.
PVS-Studio is a tool for static testing of application security (Static Application Security Testing, SAST). In other words, the PVS-Studio analyzer reveals not only typos, dead code and other errors, but also potential vulnerabilities.
For the convenience of specialists who will use PVS-Studio as a SAST tool, the analyzer displays its warnings on the Common Weakness Enumeration , SEI CERT Coding Standards. PVS-Studio diagnostics correspondence tables for various standards:
This topic is described in more detail in the article " PVS-Studio as SAST Solution ".
We also offer to get acquainted with the publications:
- How can PVS-Studio help in finding vulnerabilities?
- We shoot in the foot, processing the input data .
- We provide the PVS-Studio analyzer to security experts .
PVS-Studio Free
On the eve of the celebration of the new 2019, the PVS-Studio team decided to make a nice gift to all contributors of open-source projects hosted on GitHub or Bitbucket. They are given the opportunity to use the free PVS-Studio static analyzer for the development of open source projects.
Details: " Free PVS-Studio for those who develop open source projects ."
macOS
In 2018, PVS-Studio learned how to work under macOS. For this event, our team timed the XNU Kernel test: " Release of PVS-Studio for macOS: 64 weaknesses in the Apple XNU Kernel ."
XNU is the core of computer operating systems developed by Apple and used in OS OS OS (macOS, iOS, tvOS, watchOS).
If you want to share this article with an English-speaking audience, then please use the link to the translation: Andrey Karpov, Svyatoslav Razmyslov. PVS-Studio 7.00 .

