Biometric protection bypass methods
 A month ago, a journalist from the Forbes publication clearly demonstrated the (un) reliability of biometric protection in consumer-class devices. For the test, he ordered a plaster 3D copy of his head, after which he tried using this model to unlock five models of smartphones: LG G7 ThinQ, Samsung S9, Samsung Note 8, OnePlus 6 and iPhone X. A
A month ago, a journalist from the Forbes publication clearly demonstrated the (un) reliability of biometric protection in consumer-class devices. For the test, he ordered a plaster 3D copy of his head, after which he tried using this model to unlock five models of smartphones: LG G7 ThinQ, Samsung S9, Samsung Note 8, OnePlus 6 and iPhone X. A plaster copy was enough to unlock four out of five tested models. Although the iPhone did not succumb to the snag (it scans in the infrared range), but the experiment showed that face detection is not the most reliable method to protect confidential information. In general, like many other methods of biometrics.
Representatives of the “affected” companies said in the comments that facial recognition makes unlocking the phones “convenient”, but for “the highest level of biometric authentication” it is recommended to use a fingerprint scanner or an iris.
The experiment also showed that a couple of photographs of the victim are not enough for real hacking, because they will not allow creating a full-fledged 3D copy of the skull. For the manufacture of an acceptable prototype requires shooting from several angles with good lighting. On the other hand, thanks to social networks, it is now possible to get a large amount of such photo and video material, and the resolution of cameras increases every year.
Other methods of biometric protection are also not without vulnerabilities.
Fingerprints
 Fingerprint scanning systems became popular in the 1990s and were immediately attacked.
Fingerprint scanning systems became popular in the 1990s and were immediately attacked. In the early 2000s, hackers sharpened the mechanism for making artificial silicone copies of the existing pattern. If you stick a thin film on your own finger, then you can fool almost any system, even with other sensors, which checks the temperature of the human body and makes sure that a finger of a living person is attached to the scanner, and not a printout.
A classic tutorial on the manufacture of artificial prints is considered to be the manual of Tsutomu Matsumoto from 2002.. It explains in detail how to treat the victim's fingerprint with graphite powder or cyanoacrylate vapors (superglue), how to process the photo before making the mold and, finally, make a convex mask using gelatin, latex milk or wood glue.
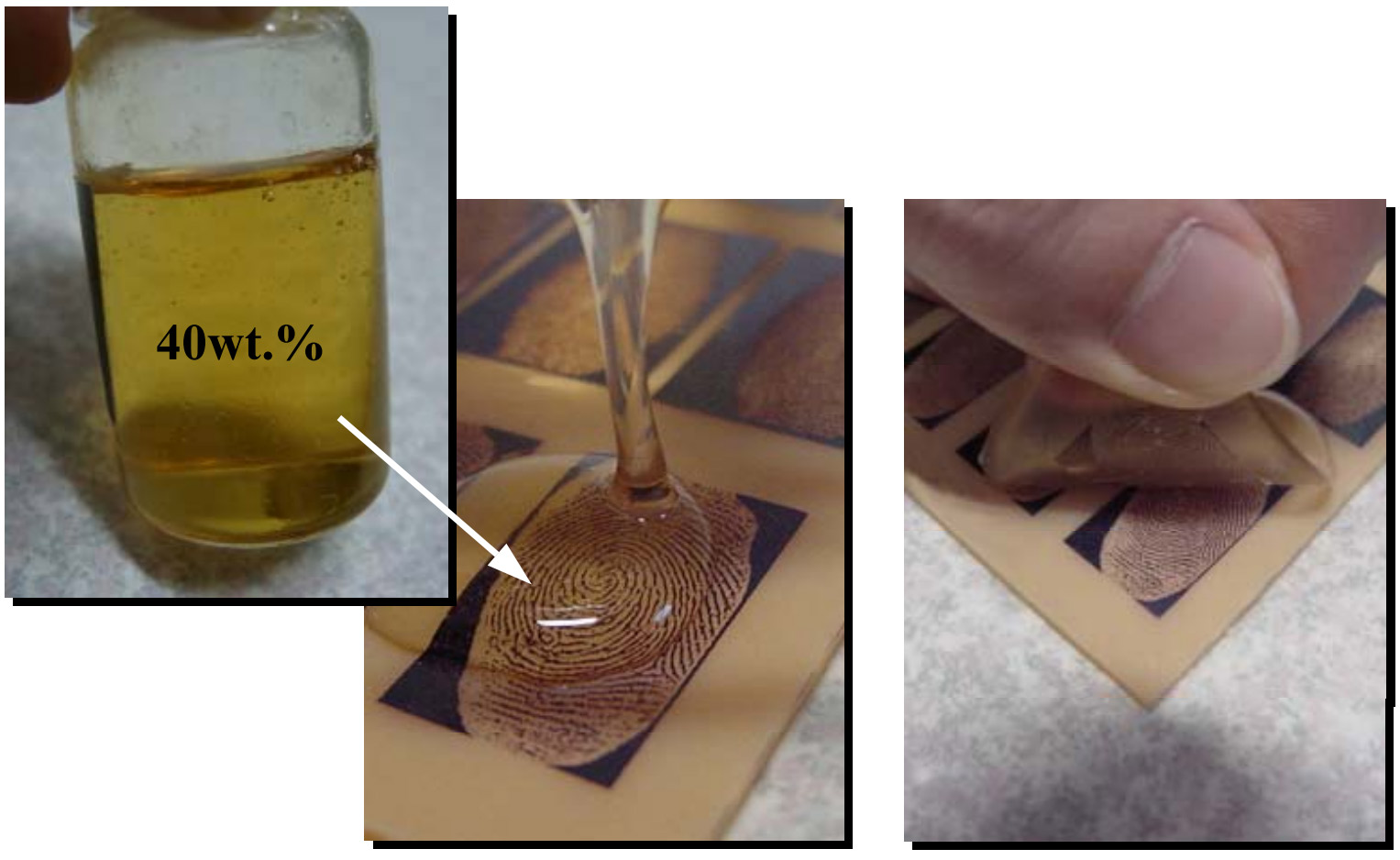
Making gelatinous film with a fingerprint pattern on a contour mold with a fingerprint. Source: Tsutomu Matsumoto manual.
The biggest difficulty in this procedure is to copy the real fingerprint. They say that the highest quality prints remain on glass surfaces and door handles. But in our time there is another way: the resolution of some photos allows you to restore the picture directly from the photo.
In 2017, the project was reportedresearchers from the National Institute of Informatics of Japan. They proved the possibility of recreating a fingerprint pattern from photographs taken with a digital camera from a distance of three meters . Back in 2014, at the hacker conference Chaos Communication Congress , the fingerprints of the German Defense Minister were shown , recreated from official high-resolution photographs from open sources.
Other biometrics
In addition to fingerprint scanning and facial recognition, modern smartphones do not yet use other methods of biometric protection, although there is a theoretical possibility. Some of these methods have been experimentally tested, others have been introduced into commercial operation in various applications, including retinal scanning, voice verification and vein drawing on the palm.
But all methods of biometric protection have one fundamental vulnerability: unlike a password, it is almost impossible to replace your biometric characteristics . If your fingerprints are leaked to the public, you will not change them. This can be said to be lifelong vulnerability.
“As the camera resolution becomes higher, it becomes possible to view smaller objects such as a fingerprint or iris. [...] As soon as you share them on social networks, you can say goodbye. Unlike a password, you cannot change your fingers. So this is the information you need to protect. ” - Isao Echizen , Professor at the National Institute of Informatics of Japan
A 100% guarantee is not provided by any biometric protection method. When testing each system, the following parameters are indicated, including:
- accuracy (several types);
- false positive rate (false alarm);
- The percentage of false negatives (event skipping).
No system demonstrates 100% accuracy with zero false positive and false negative responses, even in optimal laboratory conditions.
These parameters depend on each other. Due to the system settings, for example, it is possible to increase the recognition accuracy up to 100% - but then the number of false positives will increase. Conversely, you can reduce the number of false positives to zero - but then accuracy will suffer.
Obviously, now many methods of protection are easily cracked for the reason that manufacturers primarily think about ease of use, and not about reliability. In other words, their priority is the minimum number of false positives.
Hacking economy
As in economics, in information security there is also a concept of economic expediency. Let absolute protection does not exist. But protective measures correlate to the value of the information itself. In general, the principle is about the fact that the cost of hacking efforts for a hacker should exceed the value for him of the information he wants to receive. The greater the ratio - the more durable protection.
If you take an example with a plaster copy of the head to deceive a system like Face ID, it cost the Forbes journalistat about $ 380. Accordingly, it makes sense to use such technology to protect information that costs less than $ 380. This is a great protection technology to protect your kopeck information, and useless technology for corporate trade secrets, so everything is relative. It turns out that in each case it is necessary to evaluate the minimum allowable degree of protection. For example, face recognition in combination with a password - as two-factor authentication - already increases the degree of protection by an order of magnitude, compared with only face recognition or only one password.
In general, you can hack any protection. The issue is the cost of effort.

