ModPOS - Trojan for sale
Welcome to our readers on the iCover Blog Pages ! As you know, the volume of sales made on days of large-scale stocks by retailers is growing by orders of magnitude. And it is precisely on these days that hackers have a great opportunity to test promising types of cyber weapons, created for the active redistribution of cash flows, in the most “field” conditions. It is precisely such a malware - the new ModPOS Trojan, or rather its latest version that was virtuoso imprisoned for retailers in the USA and Eastern Europe, that was told by a group of virus analysts iSight Partners . And this beast, dear readers, is worth learning about it “in advance”.

As you probably guessed from the name of the Trojan, the purpose of ModPOS is POS terminals, or rather, the terminals of large retailers. This is a trojan with its own unique history. For a long time, ModPOS was hiding from any existing antiviruses and was active, mainly during periods of sales.
The first cases of infection with early ModPOS, as the study showed, took place back in 2012. And some fragments of the malware have attracted the attention of viral analysts since 2013. At the same time, ModPOS managed to get lost among hundreds of thousands and tens of millions of spyware samples processed by anti-virus networks automatically. At the same time, problems with the identification of ModPOS in a virtual machine were complicated by sophisticated methods to counteract debugging and obfuscation of code.
To restore the source code, study it in detail and get an idea of the general structure of ModPOS and the functions of its individual segments, virus analysts were forced to do an incredible amount of manual operations.
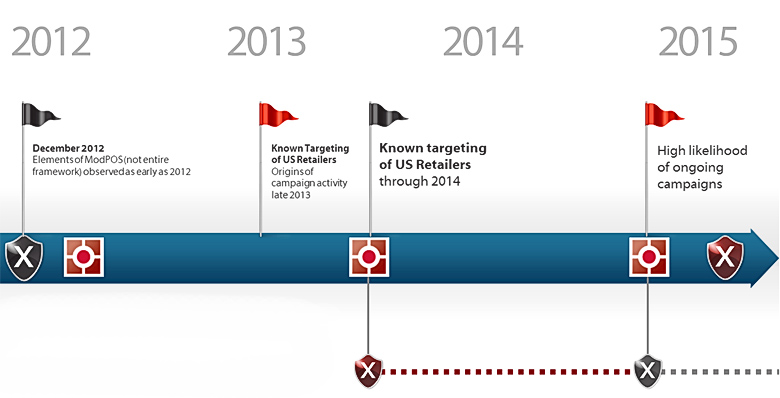
4 year marathon. modpos - a history of confrontation (illustration: isight partners).
According to Maria Noboa, senior iSight analyst: “Usually reverse engineering malware takes about twenty minutes. In the case of ModPOS, it took us about three weeks just to confirm its malicious nature. The same amount of time we restored its structure and tried to comprehend the mechanisms of work. This is the most difficult threat we have ever encountered. ”
The authors of the ModPOS development have demonstrated exceptional competence. So only one piece of shell code, the study says, contained more than six hundred functions. The Trojan, according to the analysts of the decryption group, was distinguished by its highest functionality and modularity, with a special emphasis on obfuscation of the code, sophisticated sweeping of traces of work, the use of non-standard methods of hiding the current activity and guaranteed recovery in case of removal of its individual components.
“We can say that this is not a separate Trojan, but a large-scale framework - a complex platform that includes many modules and plugins. Together, they allow attackers to collect comprehensive information about the target company, including all information about payments directly from the sales systems and personal credentials of managers, ”Noboa shares his impressions.
ModPOS is a qualitatively new extension in the segment of theft of data from bank cards, where the bulk of fraudulent transactions has traditionally been carried out and continues to be carried out using skimmers (overlays on the ATM keyboard in tandem with a miniature camera) or shimmers (ultra-thin skimmers integrated directly into the card reader) . The ModPOS Trojan is able to transform taking into account the unique features of the specific system that it infects. This makes it possible that the hashes of its modules are never the same, as well as automatically generated signatures. For at least three years, he managed to circumvent not only the capabilities of signature scanners, but also heuristic analyzers, as well as behavioral analysis tools, since ModPOS worked at the lowest level.
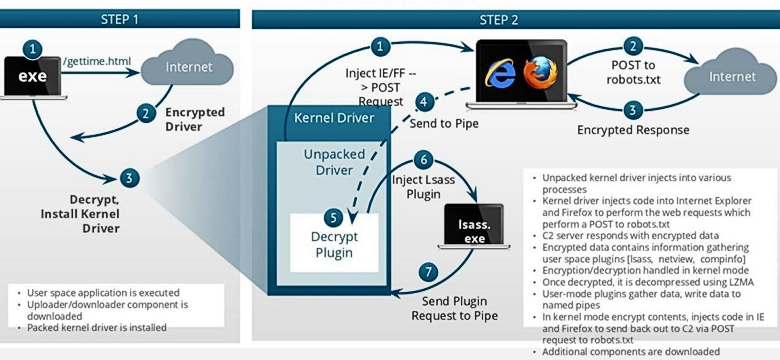
modpos working algorithm (illustration: isight partners).
Acting as a rootkit at the kernel level, ModPOS introduces its own drivers that can intercept system functions and use encryption to counter attempts to analyze the code and hide its real actions. Among ModPOS modules, a sniffer, a keylogger, and a loader for new components were detected.
Analysts from the iSIGHT group who studied ModPOS concluded that using the international standard for bank card transactions (EMV) as a means of protecting against a trojan is not effective. ModPOS has the ability to directly copy data from payment terminals and RAM. Moreover, the malware is able to simulate transactions already after the card is deleted. Only those payment systems that provide end-to-end encryption of the chain from the terminal to the payment processing center have sufficient immunity to ModPOS. In the hands of fraudsters and the fact that in many places the old-style terminals are still installed, which work in compatibility mode. Ignoring the chip, they read data from the magnetic strip of the card in the old fashioned way, as was the case everywhere before EMV integration.
The analysis of the ModPOS code by iSIGHT experts, in their opinion, leads to the idea that the development was focused primarily on payment systems of American retailer systems. At the same time, teams were also identified for interacting with network nodes whose IP addresses are located in Eastern Europe.
The analysis of the information received and the decoding of the ModPOS code allowed iSIGHT Partners to compile a base of payment systems that, with a high degree of probability, have already become victims of the malware. Their owners are already notified. The expert group is actively collaborating with the R-CISC Cyber Threat Center, with the hope that joint efforts will significantly accelerate the detection and neutralization of ModPOS.
Sources ofcomputerra.ru, isightpartners.com.
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review articles and other publications and will try to do our best to make the time spent with us useful for you. And, of course, do not forget to subscribe to our columns .
Our other articles and events

As you probably guessed from the name of the Trojan, the purpose of ModPOS is POS terminals, or rather, the terminals of large retailers. This is a trojan with its own unique history. For a long time, ModPOS was hiding from any existing antiviruses and was active, mainly during periods of sales.
Pedigree
The first cases of infection with early ModPOS, as the study showed, took place back in 2012. And some fragments of the malware have attracted the attention of viral analysts since 2013. At the same time, ModPOS managed to get lost among hundreds of thousands and tens of millions of spyware samples processed by anti-virus networks automatically. At the same time, problems with the identification of ModPOS in a virtual machine were complicated by sophisticated methods to counteract debugging and obfuscation of code.
To restore the source code, study it in detail and get an idea of the general structure of ModPOS and the functions of its individual segments, virus analysts were forced to do an incredible amount of manual operations.

4 year marathon. modpos - a history of confrontation (illustration: isight partners).
According to Maria Noboa, senior iSight analyst: “Usually reverse engineering malware takes about twenty minutes. In the case of ModPOS, it took us about three weeks just to confirm its malicious nature. The same amount of time we restored its structure and tried to comprehend the mechanisms of work. This is the most difficult threat we have ever encountered. ”
The authors of the ModPOS development have demonstrated exceptional competence. So only one piece of shell code, the study says, contained more than six hundred functions. The Trojan, according to the analysts of the decryption group, was distinguished by its highest functionality and modularity, with a special emphasis on obfuscation of the code, sophisticated sweeping of traces of work, the use of non-standard methods of hiding the current activity and guaranteed recovery in case of removal of its individual components.
“We can say that this is not a separate Trojan, but a large-scale framework - a complex platform that includes many modules and plugins. Together, they allow attackers to collect comprehensive information about the target company, including all information about payments directly from the sales systems and personal credentials of managers, ”Noboa shares his impressions.
ModPOS is a qualitatively new extension in the segment of theft of data from bank cards, where the bulk of fraudulent transactions has traditionally been carried out and continues to be carried out using skimmers (overlays on the ATM keyboard in tandem with a miniature camera) or shimmers (ultra-thin skimmers integrated directly into the card reader) . The ModPOS Trojan is able to transform taking into account the unique features of the specific system that it infects. This makes it possible that the hashes of its modules are never the same, as well as automatically generated signatures. For at least three years, he managed to circumvent not only the capabilities of signature scanners, but also heuristic analyzers, as well as behavioral analysis tools, since ModPOS worked at the lowest level.

modpos working algorithm (illustration: isight partners).
Acting as a rootkit at the kernel level, ModPOS introduces its own drivers that can intercept system functions and use encryption to counter attempts to analyze the code and hide its real actions. Among ModPOS modules, a sniffer, a keylogger, and a loader for new components were detected.
Analysts from the iSIGHT group who studied ModPOS concluded that using the international standard for bank card transactions (EMV) as a means of protecting against a trojan is not effective. ModPOS has the ability to directly copy data from payment terminals and RAM. Moreover, the malware is able to simulate transactions already after the card is deleted. Only those payment systems that provide end-to-end encryption of the chain from the terminal to the payment processing center have sufficient immunity to ModPOS. In the hands of fraudsters and the fact that in many places the old-style terminals are still installed, which work in compatibility mode. Ignoring the chip, they read data from the magnetic strip of the card in the old fashioned way, as was the case everywhere before EMV integration.
The analysis of the ModPOS code by iSIGHT experts, in their opinion, leads to the idea that the development was focused primarily on payment systems of American retailer systems. At the same time, teams were also identified for interacting with network nodes whose IP addresses are located in Eastern Europe.
The analysis of the information received and the decoding of the ModPOS code allowed iSIGHT Partners to compile a base of payment systems that, with a high degree of probability, have already become victims of the malware. Their owners are already notified. The expert group is actively collaborating with the R-CISC Cyber Threat Center, with the hope that joint efforts will significantly accelerate the detection and neutralization of ModPOS.
Sources ofcomputerra.ru, isightpartners.com.
Dear readers, we are always happy to meet and wait for you on the pages of our blog. We are ready to continue to share with you the latest news, review articles and other publications and will try to do our best to make the time spent with us useful for you. And, of course, do not forget to subscribe to our columns .
Our other articles and events
