Confrontation: results

The long-awaited cyber battle “Confrontation” took place, unfolding on the basis of the eighth annual IB forum Positive Hack Days. We tell on behalf of the direct participants of the competition - the Jet Secuirty Team and Jet Antifraud Team, about the most striking technical details of the competition between hackers and defenders. Dirty tricks of attackers, non-standard methods of hacking, ingenious traps and surprises of defenders - all this awaits you under the cut.
The contest participants were three structures based on their role in the “Confrontation”:
- attacking team: their goal is to gain unauthorized access to infrastructure facilities, destabilize the operation of systems and clear bank accounts;
- defender team: the main goal is to prevent hackers from successfully attacking protected urban infrastructure;
- observers: carry out operational monitoring of suspicious information security events and notify defenders of incidents.
Jet Infosystems was represented by two defense teams - the Jet Security Team and the Jet Antifraud Team. The task of the former was to protect the SCADA oil refinery, while the latter were involved in identifying fraud in the financial transactions of residents of a virtual city.

The attackers were represented mainly by several CTF teams.

Confrontation, day one
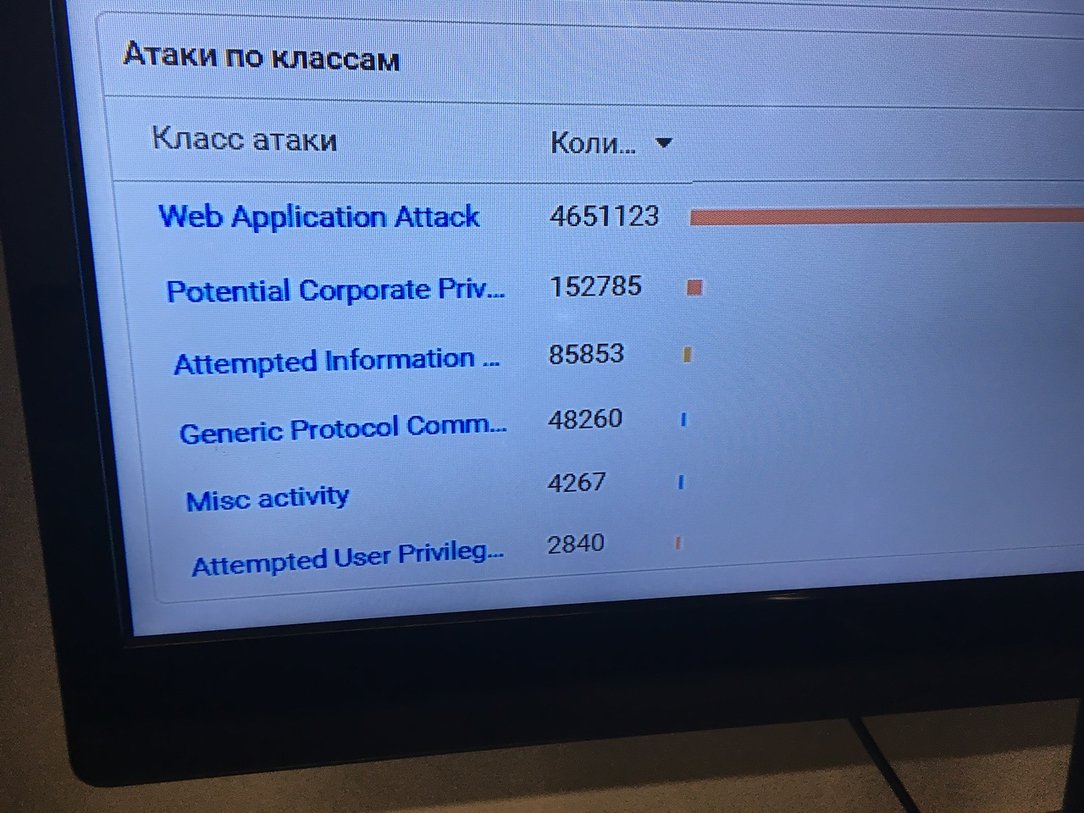
On the first day, the attackers were actively engaged in reconnaissance of network infrastructure and unsuccessful attempts to attack protected network infrastructure objects in the forehead.
First of all, one of the city’s offices was attacked, which, according to legend, is unprotected. Attackers gained access to office workstations through the already classic exploits SambaCry (CVE-2017-7494) and EternalBlue / MS17-010 (CVE-2017-0144).
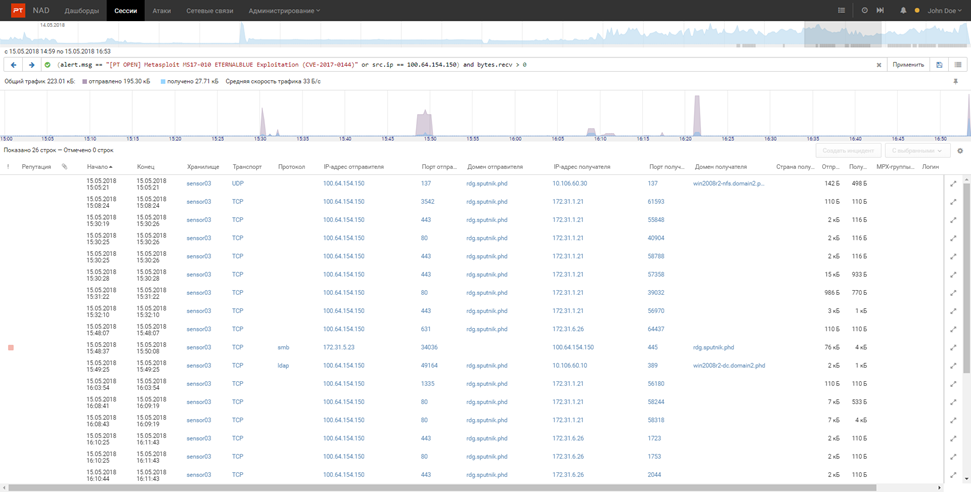
Also, the attackers actively “brutalized” the service credentials, administrative and user accounts. They managed to access TeamViewer.
Web applications were also a tidbit - attackers tried to identify critical content using utilities such as dirbuster, exploit the XML External Entity (XXE) vulnerability, and many others.
The organizers did not pass by the fresh vulnerability of Drupalgeddon2 - attackers were able to successfully exploit this attack vector and fill the so-called. web shells to the web server.
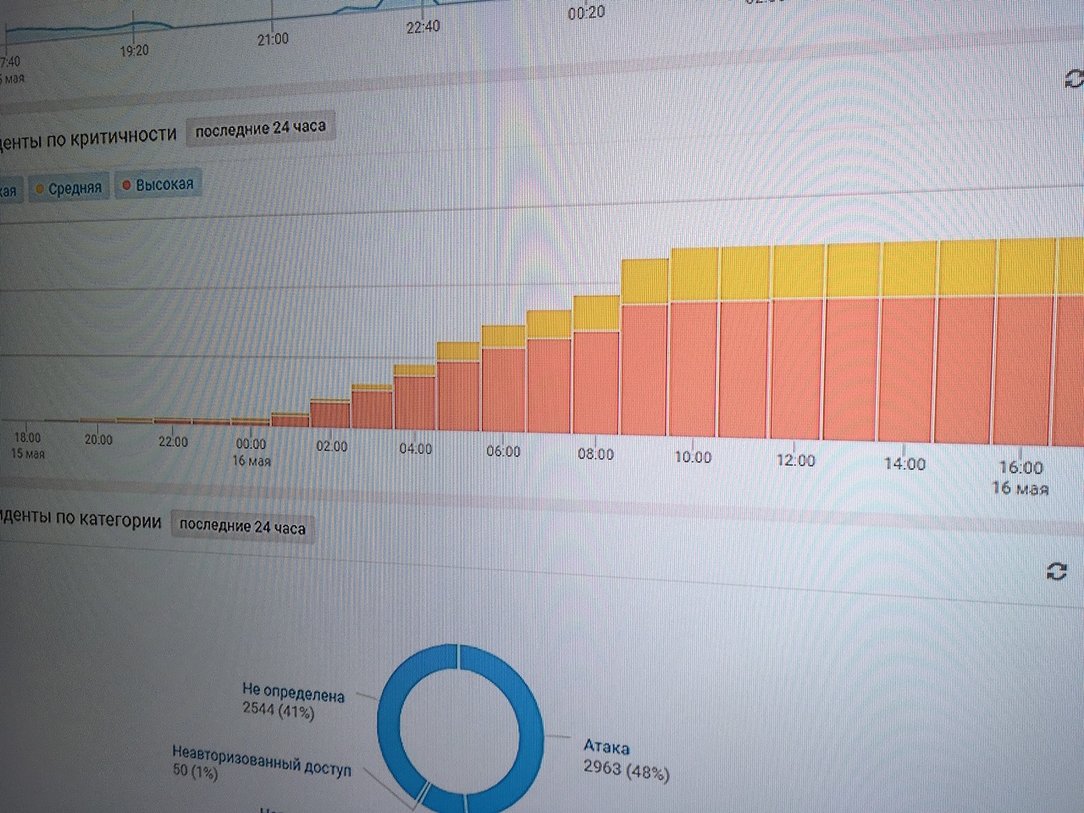
Jet Antifaud Team managed to block 4 illegitimate transactions - these were samples of the pen of the attackers before the next day's attack.
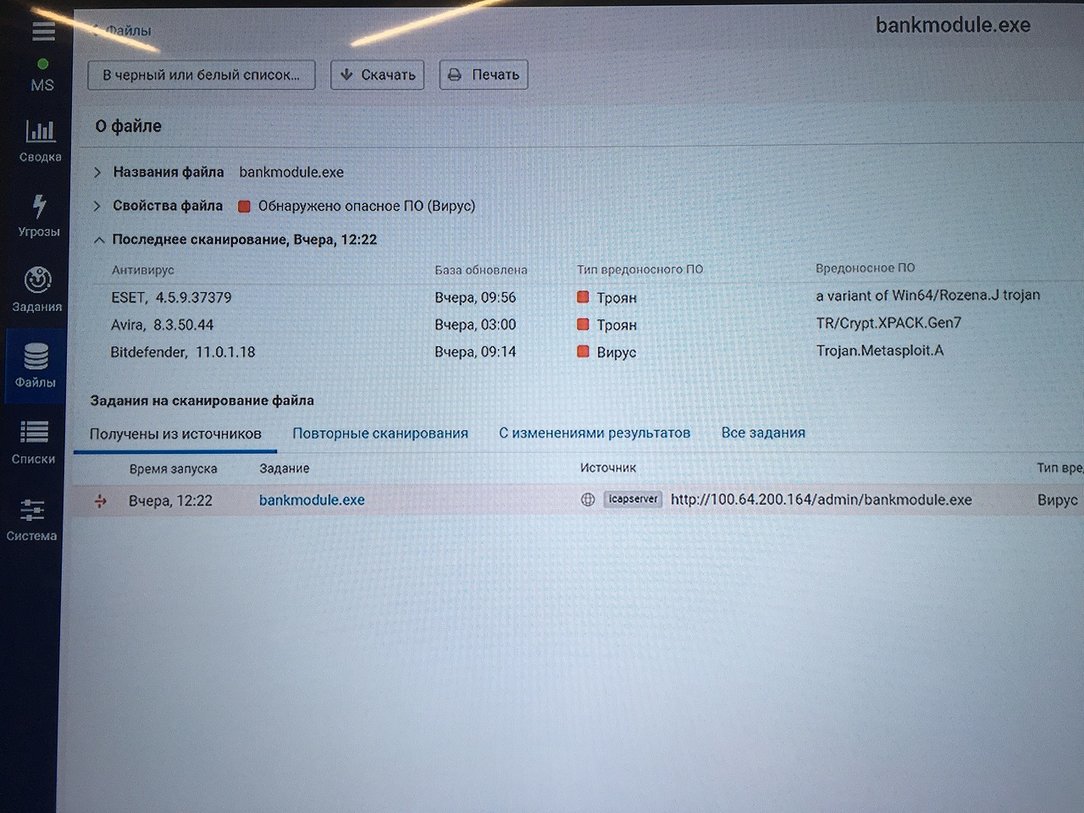
It was possible to identify and mute the activity of attackers, in addition to observer monitoring systems (SOC), using several techniques of the so-called. offensive defense from manually created ones (zip-bombs, bankmodule.exe module containing back-connect functionality) to the automated TrapX system.
The TrapX Deception in Depth architecture is used to misinform, distract, and detect sophisticated criminals and is a new generation of honeypots. This is achieved through the use of masking techniques, including the creation of automatic false markers (lures), as well as traps with medium and high levels of interaction (false targets). It attracts attackers by introducing hidden traps and markers. Traps look in every sense identical to real working IT assets and connected loT devices. All of these factors disorient attackers by creating and maintaining a simulation of real network traffic between traps.
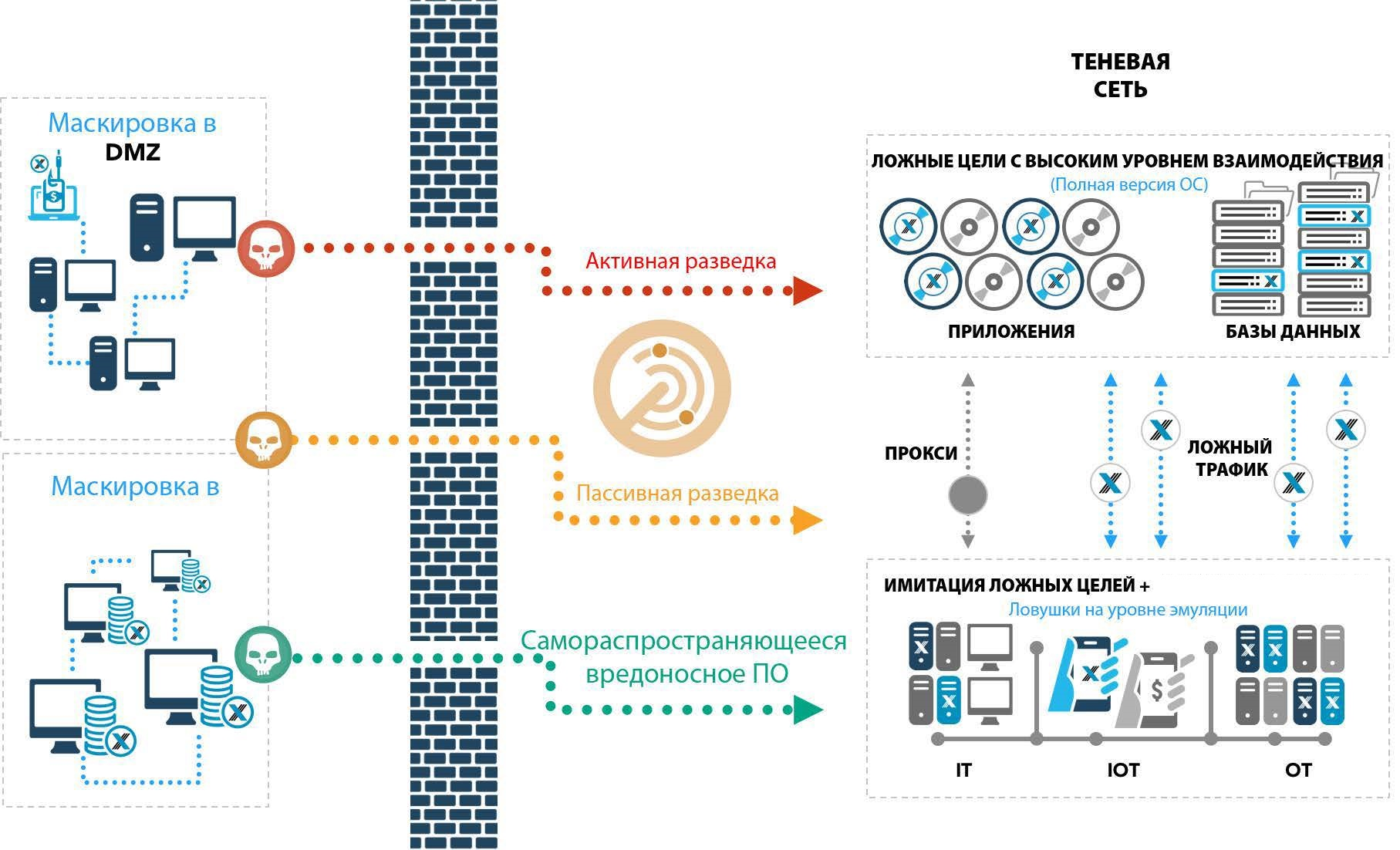
The attackers managed to compromise the access point, which was connected to the protected network through 2 intermediate network devices (which is why the Wi-Fi point leading to the ACS TP segment was not immediately detected). Once in the network 172.20.5.0/24, the attacker began carefully, trying not to attract attention, scan the network without going beyond it and without touching the gate.
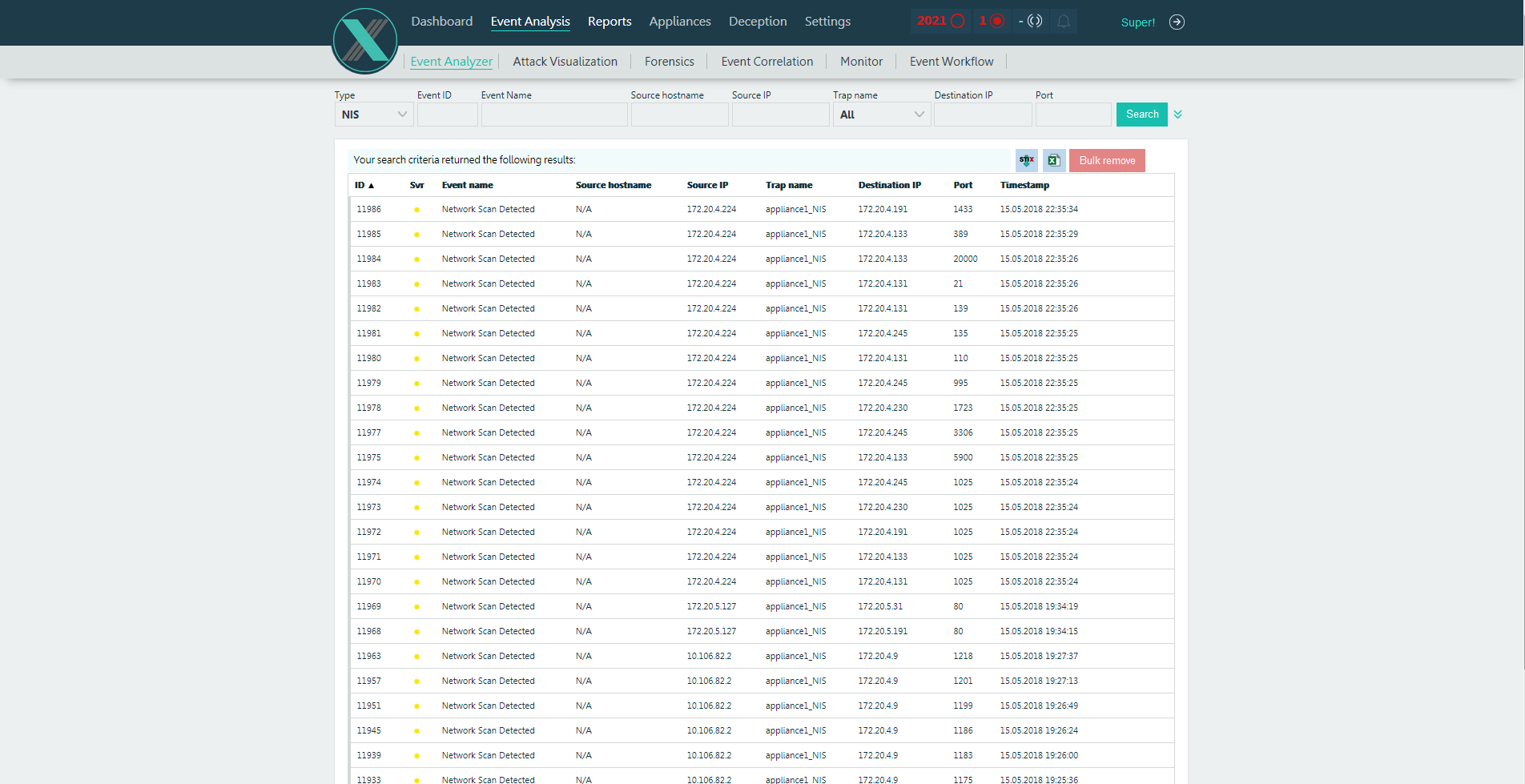
Thanks to the deployed traps in this network segment, its scan was easy to detect. However, no other traces were found on the network.
Also, when scanning on traps, an attempt was made to exploit the EternalBlue vulnerability, since network balls were opened on the traps without authorization.

Then the attacker began to change his IP address and scan the network again. This was repeated 3-4 times, and each time the scan was more massive, the “attacker” no longer tried to hide his presence in this segment of the network.
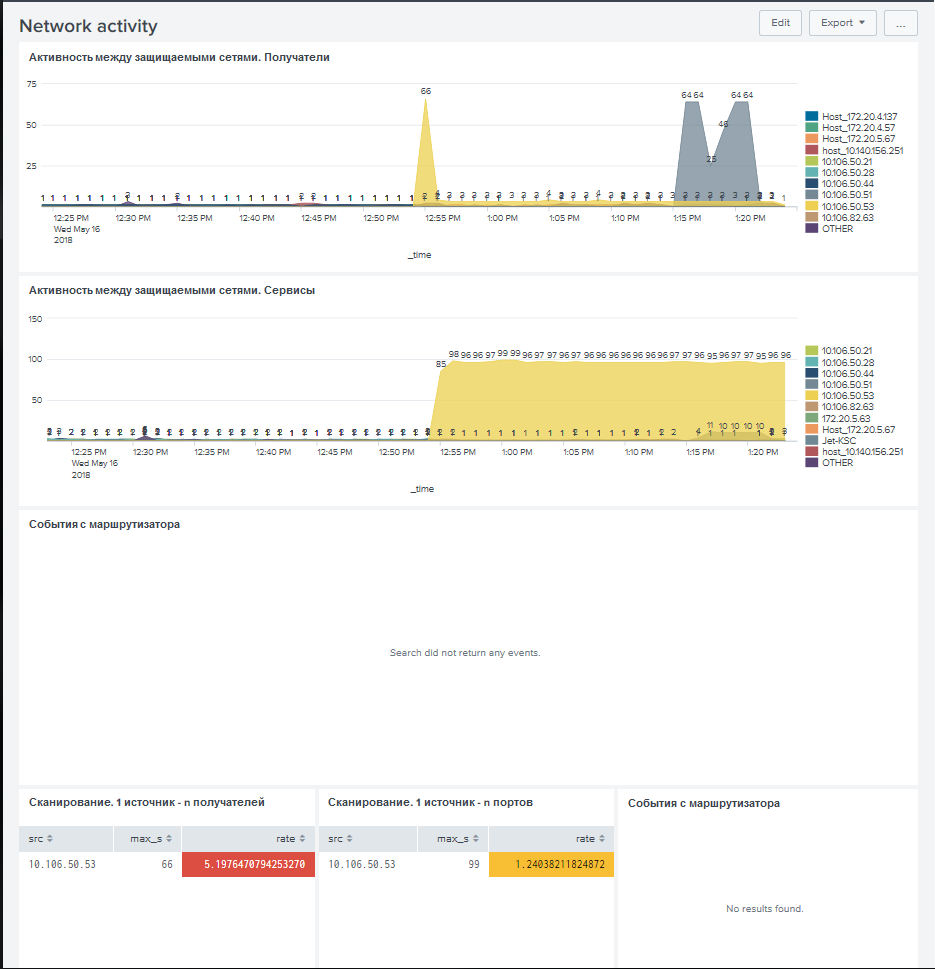
Early detection of an attacker helped to react in time to search for its connection point. Upon detection, the Wi-Fi point was immediately turned off, and then the password was changed to a more complex one.
During the night, scans within the network were also detected, but it turned out to be the organizers who inventory the network. Scanner addresses have been whitelisted in TrapX.
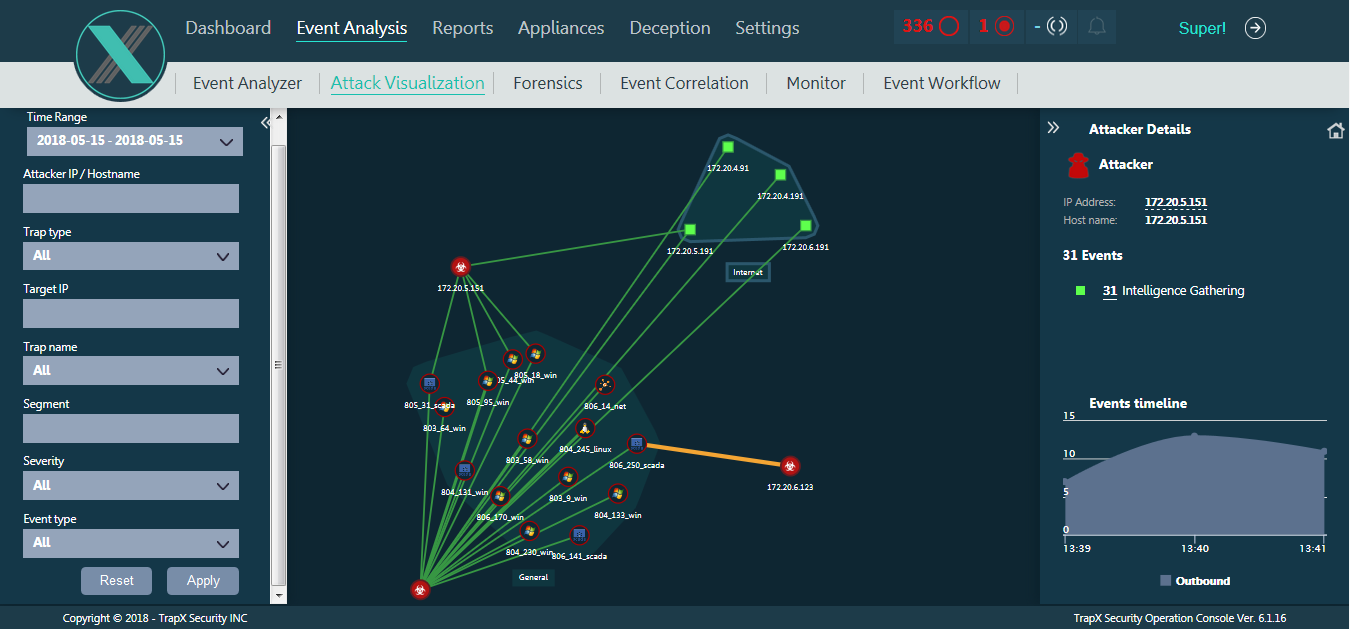
A more interesting case was last year. At the end of the confrontation, the organizers let the attackers into the ICS segment via Wi-Fi, offering to simply attack vulnerable hosts, among which were full of outdated systems, such as Windows XP, which were forbidden to patch. The attackers had about 40 minutes left until the end. Having entered the network and scanned it, they stumbled upon traps, attracting again with their open network resources. Observing the actions of “intruders” in the TrapX interface, it was clear that they spent at least 5-7 minutes on each trap in order to understand that there was nothing useful to get from this host. Attempts were also identified to exploit vulnerabilities and copy malicious files to the host. Files were automatically placed in the TrapX sandbox and analyzed. All of them could be downloaded later for a detailed analysis and investigation of the attackers. Due to the fact that the attackers got stuck in the set traps, they did not have time to attack real targets.
Also, baits with fake accounts and addresses of other traps were scattered on all traps. The baits were also located on real hosts in order to lead attackers out of the way. After the hackers tried to use the credentials thrown in, they were immediately displayed in the SIEM system.
Confrontation, night
Night is the time of dirty tricks. In the dark, attackers made a sortie into the camp of the defenders of the virtual city and connect directly to the virtual city system. Despite the fact that they were driven away by huge fighting humanoid robots, the attackers were able to realize several attack vectors. Including having received the password from the access point.
As I wrote earlier, the city falls asleep, hackers wake up - at night the intensity of attacks has increased significantly. The attacking teams hoped that the defenders would lose their vigilance and compromise the systems.
Confrontation, day two
On the last day of the “Confrontation,” hackers made every effort to attack the infrastructure.
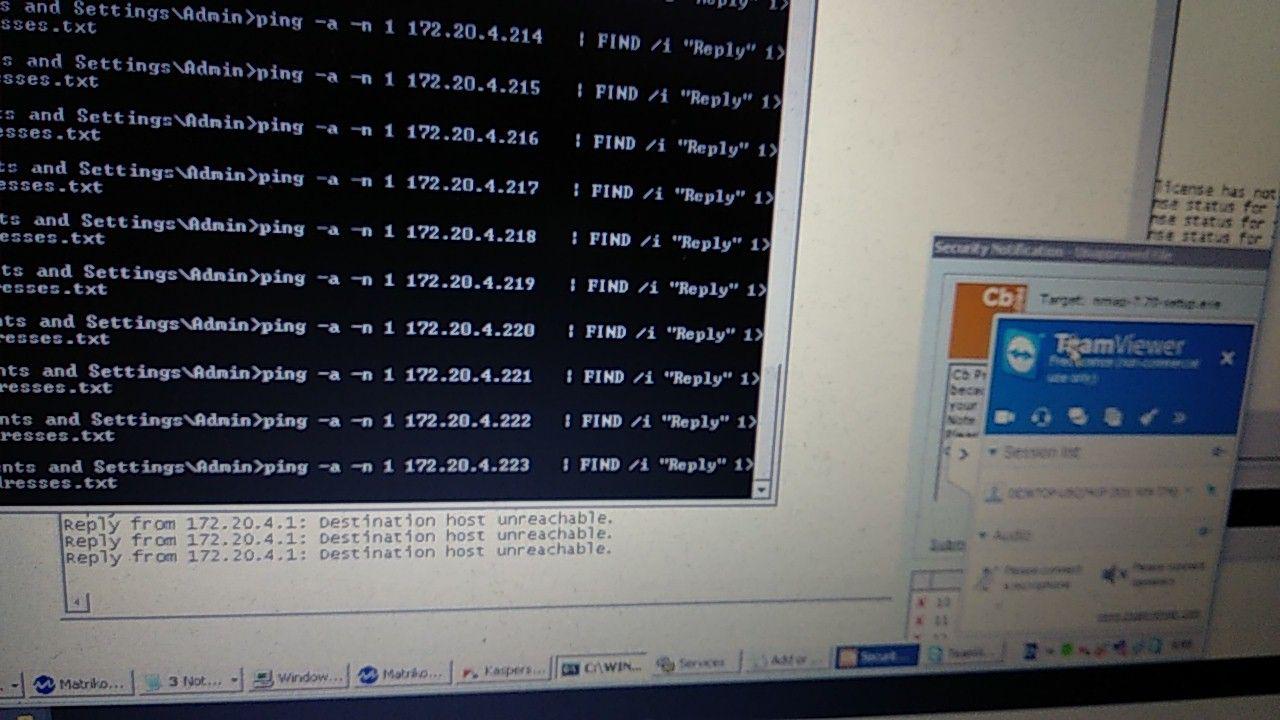
“We must pay tribute to the attackers, they were experienced and trained guys. On the second day of the confrontation, the attack team was able to gain access to the operator’s station through the contractor’s TeamViewer session, which, according to legend, was setting up the ICS. After unsuccessful attempts to install malware, they made a network scanner in 5 minutes using notepad and ping command. The children are set off! Participation in such a competition requires a concentrate of knowledge, effort, experience and ingenuity for all participants in the defense team. In this “battle”, we used the arsenal of what we use when implementing projects to protect our real customers, ”commented Ilya Sapunov, captain of the Jet Security Team, deputy chief of the security systems design department at Jet Infosystems.
Attackers secured themselves on a compromised SCADA AWP and examined the subnet for new targets. What is noteworthy - the attackers used what was at hand (since nmap, Metasploit, etc., were blocked by anti-virus tools): using the ping command, they detected “live” hosts.
The forces of one of the teams in the attacked network raised a VPN server to connect to help from the external Internet. Others poured control programs and specifications for control systems from torrents.
Attacks on the financial system have also intensified - the defenders from the Jet Antifaud Team have repelled several thousand illegitimate transactions.
To prevent fraudulent transactions, the Jet Detective software package was used, in which the entire amount of transaction data was analyzed using both expert rules and ML models. Jet Detective contains a set of algorithms for detecting illegal actions, developed based on the experience of anti-fraud specialists.
To cope with a huge flow of data, experts were helped by mathematical models. Three types of models were used in the solution: classic “with a teacher”, allowing to identify events similar to a previously identified fraud; models aimed at identifying anomalies in the behavior of business objects and the flow of various processes, both trainees and experts; models of control of business processes aimed at identifying anomalies in the technological and process chains of actions, allowing to assess the permissible deviations from the standard conduct of a particular operation or their sequence.
The business objects that the system works with are data combined from various sources into an integrated business entity (for example, “Client”, “Payment”, “Service Point”, etc.). The system forms a profile of typical object behavior and identifies deviations from it. In this way, suspicious events that were not previously recorded are detected.
Despite active attacks by hackers on the financial system, especially intensified at night, the defenders from the Jet Antifraud Team reflected several tens of thousands of illegitimate transactions, not allowing any of them to be conducted. Despite the fact that not one component of the classical information security system in the protected “bank” has been installed. At the end of the 30-hour non-stop competition, the organizers decided to turn off the anti-fraud system to enable attackers to implement part of the attacks to withdraw money from the accounts of city residents. Taking advantage of this fact in the end and became the winners of the "Confrontation" on the part of the attackers.
“It was a very stressful 2 days. And if on the first day of attack attempts there were very few, which gave us a good margin of time to train the components and collect statistics, then the night, like last year, was full of attacks. Someone played a fairly direct game, trying to withdraw money to the target accounts of attacking teams, someone explicitly checked our mechanisms for vulnerabilities, trying different types of operations, messing up traces through internal accounts, ”notes Alexey Sizov, captain of the Jet Antifraud Team, head of the Jet Infosystems anti-fraud solutions implementation department, - In general, it’s quite difficult to make high-quality decisions when incorrect blocking of operations is immediately reflected in your account - the organizers did a lot to antifraud b l closest to the battle mode, and the hefty flows of legitimate operations to replenish the accounts of a mobile operator, utility bills and simply the operations of “respectable residents” did not let analysts relax for a minute. But the result speaks for itself: in 29 hours there’s not a single missed operation, and for every 1000 fraudulent attempts there are only a few false positives, and after our shutdown there are more than 60,000 operations and the withdrawal of all the bank’s “reserves” in just 20 minutes. ”
With the Jet Detective system running, the attacker was unable to conduct any illegitimate transaction. Only after a complete shutdown of the system, the attackers were able to transfer funds to their account. The Hack.ERS team managed to do this at the very end of the competition, quickly taking first place. Everything is as in life - if you do not protect finances, they will be taken away right there.
Impressions:
Alexey Sizov, captain of the Jet Antifraud Team, head of the Jet Infosystems anti-fraud solutions implementation department: “The impressions are unforgettable, our result speaks for itself. However, in our segment, some attacking teams clearly did not have enough time and experience in attacks on banking mechanisms. At night, I wanted to tell the attackers a couple of options for trying. Brute force allowed us to achieve a result after our shutdown, but there were many more interesting options. We will be waiting for their implementation next year) ”
Ilya Sapunov, captain of the Jet Security Team:“The event was mixed. There was preparation in a very short time. The serious composition of the enemy kept our team in suspense and constant readiness. Unfortunately, the time for attack development for attackers was significantly limited. I hope that the next event will result in a more active and dense confrontation. "
Conclusion
The contest “Confrontation” is one of the most striking events of the Russian information security community, which allows real-time testing of your skills in penetration and protection of critical infrastructure, and confirming the correctness of your decisions and tactics.
See you next year!
