Blocking surveillance from Windows 10 is not easy, says security specialist
A week ago, Mark Burnett, an independent security expert, published the results of a small incorrect investigation of security settings in Windows 10 Enterprise. The system was installed in his virtual machine under Linux exclusively for research purposes, with a minimal set of software and all the default Windows Store applications removed.
These results caused a lively discussion on Twitter because they make it clear that the OS seems to ignore some settings set by the user - and still connects to various monitoring servers and sends some data there. Burnett's first test with the results published on Twitter, was carried out with errors. There is actually a better way to limit telemetry. But to completely get rid of data collection in Windows 10 is generally impossible.
Mark Burnett is a hacker and researcher, not a Microsoft system engineer, although he wrote the ASP.NET security book, received the Most Valuable Professional (MVP) title from Microsoft seven times, was engaged in technical support for Windows and exclusively used this OS on the desktop for about 25 years, until Windows 10 came out with a sharp change in Microsoft's policy on the massive collection of user personal data.
You can refer to the official Microsoft manual for managing connections in Windows 10 , but all the same, Burnett’s opinion cannot be called unqualified. In fact, with Windows 10 Group Policies is not so simple.
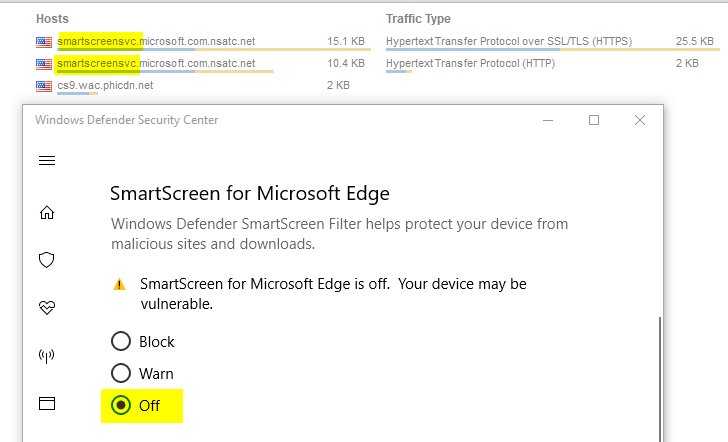
The first screenshot shows that SmartScreen is disabled on the system, but Windows 10 still connects to Microsoft's SmartScreen servers. Disabling telemetry in Windows 10 is also not so simple. Just changing two group policies is not enough. The screenshot shows that the OS still sends data to Microsoft, despite the explicit twofold indication that this should not be done in group policies and a couple of changes in the registry.
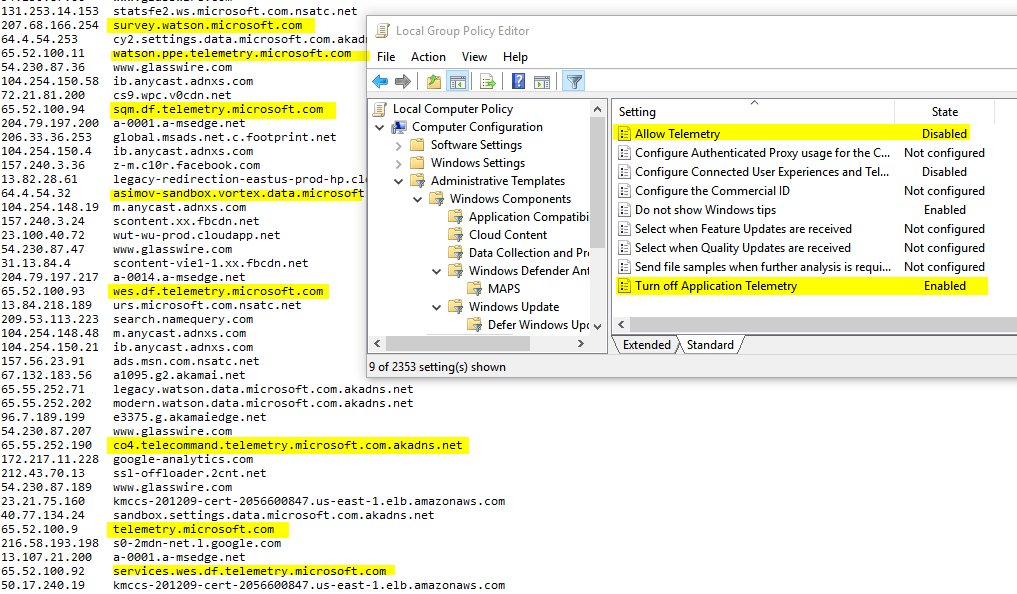
All connections were blocked by the router's firewall, the screenshots show only blocked attempts by Windows 10 to connect to different hosts. Therefore, it is not known which packets she could send there. For example, in the case of telemetry, etc.
The same goes for synchronization settings, which involve connecting to Microsoft servers. In group policies, all policies associated with this are disabled, but Windows 10 still connects. The same goes for error message settings, online account validation (AVS) policies in the Key Management Service (KMS) client.
The specialist tried to change all system settings to block any connection with Microsoft servers, except for receiving updates, but still registered a lot of connections with servers that clearly had an advertising and tracking purpose. Typically
, according to the Glasswire firewall, all these advertising hosts belong to Microsoft system processes, so you can’t write them to third-party software (by the way, this is a really good firewall for Windows and Android, free and easy to use).
Mark Burnett concludes that Windows 10 does not seem to respect its own group policies. Probably, some types of connections can be blocked by changes in the registry - of course, these are undocumented keys in the registry. That is, you cannot guarantee that you will find all the keys you need without exception.
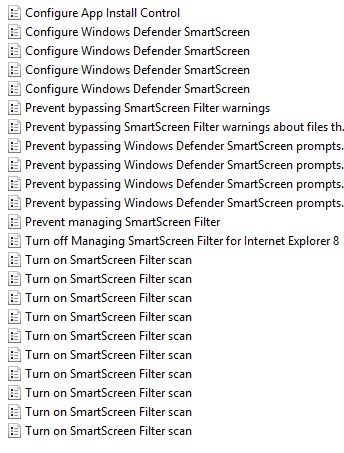
Burnett himself admits that the first test was not completely clean. In a subsequent blog posthe talked about a more thorough test and explained the testing methodology. A second test still showed unpleasant activity in Windows 10, although in smaller quantities. For example, it turned out that to block SmartScreen, you need to change not two settings, as Burnett did, but more:
There are a number of applications that help cope with spying by Microsoft and block the connections that Windows 10 establishes with remote servers bypassing system settings and which cannot be or is very difficult to block in other ways. Actually, the fact of the presence of such applications already indicates the presence of a problem. People would not create such programs and would not use them if surveillance in Windows 10 were turned off by trivial methods. As an example of an anti-spyware program that shuts up unnecessary connections in Windows 10, ShutUp 10 can be recommended . Burnett himself also used it on a test machine. But as you can see, even anti-spyware software does not help.
PS Some experts recommend that to disable telemetry in group policies, do not stop the service, as Burnett did, but start the service with parameter 0, in this way:
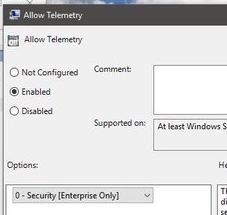
This may seem counterintuitive, but it may indeed appear possible to block connections to Microsoft monitoring servers that are not blocked at the usual stop of the telemetry service.
Burnett believes that some of the different Windows 10 group policies for surveillance are implemented in different ways, and are disabled in different ways. By accident or on purpose, but this makes it difficult to turn them off. Microsoft's recommended way to disable telemetry through the Windows Restricted Traffic Limited Functionality Baseline causes a lot of problems. In addition, telemetry is collected by .NET, Office, Windows Error Reporting, Windows DRM, other applications and components. And for many users, the default data collection settings for Microsoft are set to the maximum level.
