Why two-factor authorization in Telegram does not work
After the recent high-profile hacking of Telegram accounts in Russia, service founder Pavel Durov said that two-factor authorization "allows you to protect important information."
Yes, if two-factor authorization in Telegram is enabled, then the attacker who hijacked your account will not receive the history of your correspondence - but this two-factor does not protect against theft, although it seems to be like it should.
That is, if an attacker can receive your SMS with a login code, then he is guaranteed to steal your account, regardless of whether you have two-factor authorization enabled or not.
By “steal” I mean “can enter the Telegram application under your phone number” and write messages to your contacts on your behalf.
It happens as follows:
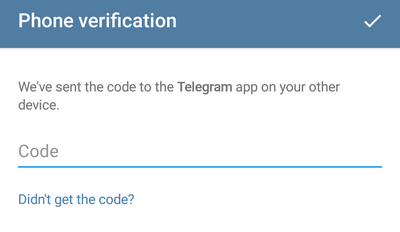
1. The attacker in the application indicates the victim’s phone number and tries to log into the account. Then he sees a message that the code was sent not by SMS, but to the application registered to this number on another device:
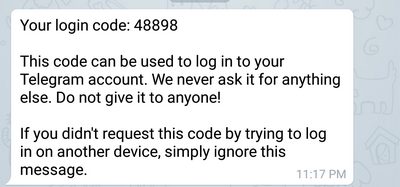
2. At this point, the victim receives a system notification in his Telegram application (or applications):
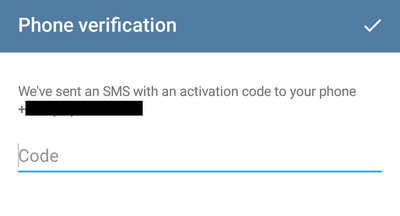
3. The attacker clicks “Didn 't get the code? ”and Telegram sends the code via SMS:
4. Then the attacker enters the code from SMS and finds out that two-factor authentication is enabled in the account settings and that he needs to enter the password (in this case“ 10 ”is a hint for the password, selected when turning on two-factor):

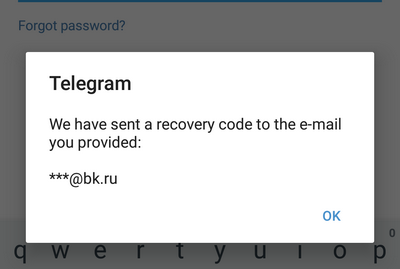
5. Next, the attacker pretends to have forgotten the password - “Forgot password?”. Here, the attacker is informed that the recovery code has been sent to e-mail (if the victim specified the email address when turning on two-factor authorization). The attacker does not see the email address - he sees only that after the “dog”:
6. At this point, the victim receives a code to reset the password to the email address (if she provided the email address when two-factor authentication is enabled):
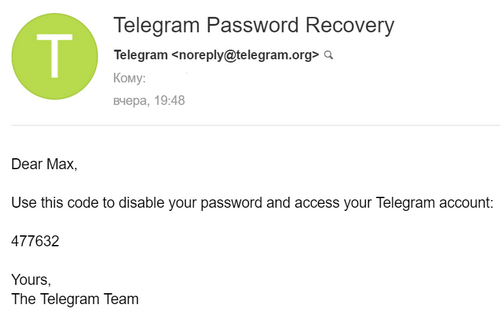
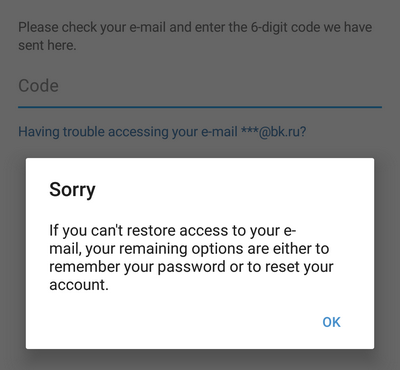
7. The attacker clicks “Ok” and sees a window where you need to enter the code to reset the password that was sent by e-mail. Then the attacker says that he has problems accessing his e-mail - “Having trouble accessing your e-mail?”. Then Telegram offers "reset your account":
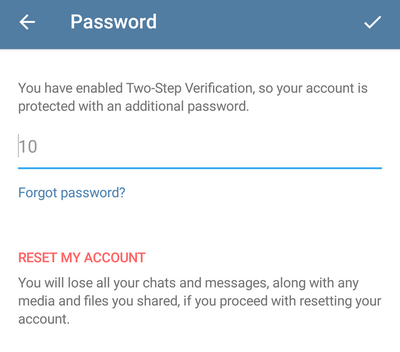
8. The attacker clicks “ok” and sees two options - either enter the password, or press “RESET MY ACCOUNT”. Telegram explains that when “reinstalling” the account, all correspondence and files from all chats are lost:
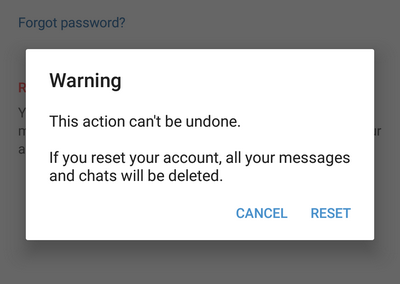
9. The attacker clicks “RESET MY ACCOUNT” and sees a warning that this action will not be canceled and that all messages and chats will be deleted:
10. The attacker presses “RESET” and Telegram asks for the name for the “reset” account:
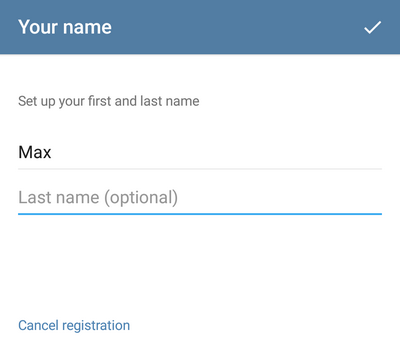
11. Actually, everything, the attacker successfully hijacked the account: he entered under the victim’s phone number and can write messages on her behalf:
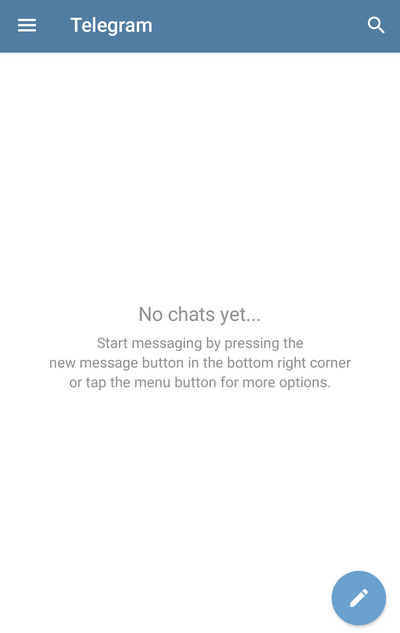
12. The victim sees the application as what it was right after installation. The welcome screen talks about Telegram and offers to register or log into an existing account:

13. When the attacker writes on behalf of the victim to one of the victim's contacts, this contact sees that the victim has just joined Telegram (which is suspicious), as well as a new message (or messages) in a new chat from the victim. After 12-16 hours, the contact will also see that in the old chats, instead of the victim’s name, “Deleted Account” is indicated:
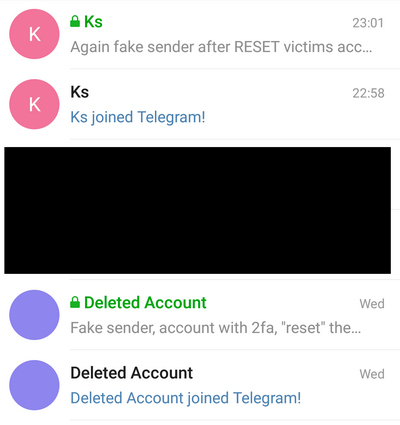
If the victim has the opportunity to receive SMS to this phone number, she can enter the Telegram application on her device. If the attacker on the hijacked account has not enabled two-factor authentication, the victim can enter the Settings => Privacy and Security => Active Sessions menu and terminate all other sessions (i.e., the attacker's sessions):

If the attacker on the hijacked account has enabled two-factor authorization, the victim, in turn, can “steal back” his account in the same way.
It turns out that the only benefit of two-factor authorization in Telegram is that the attacker does not receive correspondence from ordinary non-secret chats (if you steal an account without two-factor chat enabled, the attacker will receive the entire history of correspondence from unclassified chats, he will not get anything from secret chats anyway ) That is, Telegram with enabled two-factor authorization gives approximately the same thing that Signal and WhatsApp provide, and so, without any two-factor authorization.
In other words, two-factor authorization in Telegram is not quite real, Telegram still allows you to log in using only one factor - the code from SMS.
The situation is somewhat anecdotal: here you are, users, two-factor authorization. The first factor is the code from SMS (what I have), the second factor is the password (what I know). It sounds super, but when the user says - but I forgot the password, Telegram says - well, it’s okay, come in without a password and use your health :)
This was found out experimentally as part of a slightly larger study on Telegram, WhatsApp and Signal - " How "secure" messengers are protected from theft of SMS "
Yes, if two-factor authorization in Telegram is enabled, then the attacker who hijacked your account will not receive the history of your correspondence - but this two-factor does not protect against theft, although it seems to be like it should.
That is, if an attacker can receive your SMS with a login code, then he is guaranteed to steal your account, regardless of whether you have two-factor authorization enabled or not.
By “steal” I mean “can enter the Telegram application under your phone number” and write messages to your contacts on your behalf.
It happens as follows:
1. The attacker in the application indicates the victim’s phone number and tries to log into the account. Then he sees a message that the code was sent not by SMS, but to the application registered to this number on another device:

2. At this point, the victim receives a system notification in his Telegram application (or applications):

3. The attacker clicks “Didn 't get the code? ”and Telegram sends the code via SMS:

4. Then the attacker enters the code from SMS and finds out that two-factor authentication is enabled in the account settings and that he needs to enter the password (in this case“ 10 ”is a hint for the password, selected when turning on two-factor):

5. Next, the attacker pretends to have forgotten the password - “Forgot password?”. Here, the attacker is informed that the recovery code has been sent to e-mail (if the victim specified the email address when turning on two-factor authorization). The attacker does not see the email address - he sees only that after the “dog”:

6. At this point, the victim receives a code to reset the password to the email address (if she provided the email address when two-factor authentication is enabled):

7. The attacker clicks “Ok” and sees a window where you need to enter the code to reset the password that was sent by e-mail. Then the attacker says that he has problems accessing his e-mail - “Having trouble accessing your e-mail?”. Then Telegram offers "reset your account":

8. The attacker clicks “ok” and sees two options - either enter the password, or press “RESET MY ACCOUNT”. Telegram explains that when “reinstalling” the account, all correspondence and files from all chats are lost:

9. The attacker clicks “RESET MY ACCOUNT” and sees a warning that this action will not be canceled and that all messages and chats will be deleted:

10. The attacker presses “RESET” and Telegram asks for the name for the “reset” account:

11. Actually, everything, the attacker successfully hijacked the account: he entered under the victim’s phone number and can write messages on her behalf:

12. The victim sees the application as what it was right after installation. The welcome screen talks about Telegram and offers to register or log into an existing account:

13. When the attacker writes on behalf of the victim to one of the victim's contacts, this contact sees that the victim has just joined Telegram (which is suspicious), as well as a new message (or messages) in a new chat from the victim. After 12-16 hours, the contact will also see that in the old chats, instead of the victim’s name, “Deleted Account” is indicated:

If the victim has the opportunity to receive SMS to this phone number, she can enter the Telegram application on her device. If the attacker on the hijacked account has not enabled two-factor authentication, the victim can enter the Settings => Privacy and Security => Active Sessions menu and terminate all other sessions (i.e., the attacker's sessions):

If the attacker on the hijacked account has enabled two-factor authorization, the victim, in turn, can “steal back” his account in the same way.
It turns out that the only benefit of two-factor authorization in Telegram is that the attacker does not receive correspondence from ordinary non-secret chats (if you steal an account without two-factor chat enabled, the attacker will receive the entire history of correspondence from unclassified chats, he will not get anything from secret chats anyway ) That is, Telegram with enabled two-factor authorization gives approximately the same thing that Signal and WhatsApp provide, and so, without any two-factor authorization.
In other words, two-factor authorization in Telegram is not quite real, Telegram still allows you to log in using only one factor - the code from SMS.
The situation is somewhat anecdotal: here you are, users, two-factor authorization. The first factor is the code from SMS (what I have), the second factor is the password (what I know). It sounds super, but when the user says - but I forgot the password, Telegram says - well, it’s okay, come in without a password and use your health :)
This was found out experimentally as part of a slightly larger study on Telegram, WhatsApp and Signal - " How "secure" messengers are protected from theft of SMS "
Only registered users can participate in the survey. Please come in.
What “protected” messenger do you use the most?
- 20.1% WhatsApp 234
- 29.9% Telegram secret chat 349
- 1.3% Signal 16
- 0% Wickr 0
- 0% Threema 1
- 0% Hoccer 0
- 1.9% OTR (via Pidgin, Jitsi, Chatsecure, etc.) 23
- 4.5% Tox 53
- 0% Cryptocat (new) 1
- 4.5% Other 53
- 37.2% None 434
