Comparison of LAN Scan Tools

When I worked in several government organizations with
Old and experienced
In order to smooth out our contradictions, it was decided to conduct a blitz test of network vulnerability scanners. Holivar among Pentecosters Hackenled us to a new task - to conduct a comparative characteristic according to the results of scanning. Four scanners were selected to compare scan performance: Rapid7 Nexpose, Tenable Nessus, OpenVAS 9, and Nmap. They were chosen based on analytics online publications and personal experience. Personally, I bet on Nessus, but alas, I did not guess.
Rapid7 Nexpose is a vulnerability scanner that actively scans the IT infrastructure for erroneous configurations, holes, malicious codes, and provides recommendations for resolving them. Analysis includes all infrastructure components, including networks, operating systems, databases, and web applications. Based on the scan results, Rapid7 Nexpose classifies detected threats in priority mode and generates reports on their elimination. [2]
Tenable Nessus Scanner is a scanner designed to assess the current state of protection of traditional IT infrastructure, mobile and cloud environments, containers, etc. Based on the scan results, it reports on the vulnerabilities found. Recommended for use as part of the Nessus Security Center. [3]
OpenVASIs an open source vulnerability scanner. OpenVAS is designed to actively monitor computer network nodes for security-related problems, assess the severity of these problems, and to monitor their resolution. Active monitoring means that OpenVAS performs some actions with the host: scans open ports, sends specially formed packets to simulate an attack, or even logs on to the host, accesses the management console, and executes commands on it. OpenVAS then analyzes the data collected and concludes that there are any security issues. These problems, in most cases, relate to non-updated software installed on the node, in which there are known and described vulnerabilities, or insecurely configured software. [1,6]
Nmap- A free utility designed for a variety of custom scanning of IP networks with any number of objects, determining the status of objects of a scanned network (ports and their corresponding services). Initially, the program was implemented for UNIX systems, but versions for many operating systems are now available. [4,5]
Test environment
For testing, I put together a test network on VMware Workstation 12 Pro in the circuit shown in Fig. 1.
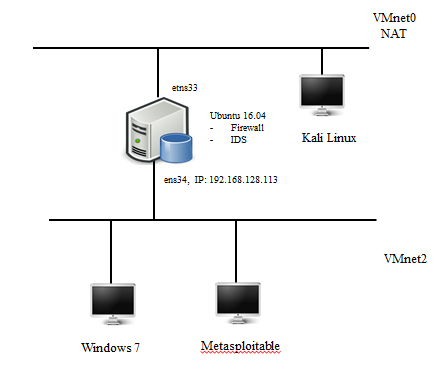
Fig. 1. Network Diagram
Raised virtual machines:
- Windows 7 with all installed updates, running the XAMPP application, deployed MySQL and Apache services. Also deployed test system DVWA.
- Metasploitable 2 is an operating system with preinstalled vulnerable services and applications, which is used for testing.
- Ubuntu 16.04 with installed IDS Suricata [10] and configured iptables [9].
- Kali Linux is a Linux distribution that is used for penetration testing.
- The list of vulnerable services in Metasploitable 2 is shown in Table 1.
Table 1
| Service | Port | Status |
| Vsftpd 2..four | 21 | Open |
| OpenSSH four.7p1 Debian 8ubuntu 1 (protocol 2.zero) | 22 | Open |
| Linux telnetd service | 23 | Open |
| Postfix smtpd | 25 | Open |
| ISC BIND 9.four.2 | 53 | Open |
| Apache httpd 2.2.eight Ubuntu DAV / 2 | 80 | Open |
| A RPCbind service | 111 | Open |
| Samba smbd .X | 139, 445 | Open |
| r companies | 512, 513, 514 | Open |
| GNU Classpath grmiregistry | 1099 | Open |
| Metasploitable root shell | 1524 | Open |
| A NFS service | 2048 | Open |
| ProFTPD 1..1 | 2121 | Open |
| MySQL 5.zero.51a-3ubuntu5 | 3306 | Open |
| PostgreSQL DB eight..zero - eight..7 | 5432 | Open |
| VNC protocol v1. | 5900 | Open |
| X11 service | 6000 | Open |
| Unreal ircd | 6667 | Open |
| Apache Jserv protocol 1. | 8009 | Open |
| Apache Tomcat / Coyote JSP engine 1.1 | 8180 | Open |
In practice, when scanning internal networks on the firewall and IPS, rules are created that exclude blocking scanning. Therefore, Suricata was used in the detection mode, and permission rules were written on the firewall.
Iptables configuration [9]:
#!/bin/sh
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -A INPUT -i lo -j ACCEPT
iptables -I FORWARD -j ACCEPT
iptables -A FORWARD -i ens34 -o ens33 -j ACCEPT
iptables -t nat -A POSTROUTING -o ens33 -s 192.168.234.0/24 -j MASQUERADE
iptables -A FORWARD -i ens33 -m state --state ESTABLISHED, RELATED -j ACCEPT
iptables -A FORWARD -i ens33 -o ens34 -j REJECTNessus Scanner ran in Basic Network Scanning mode. [3]
Rapid 7 Nexpose started in Full audit without Web Spider mode. [2]
OpenVAS 9 started in default mode. [1,6]
Nmap was launched by two commands: [4,5]
- nmap -sV -T4 -O -F --version-light 192.168.234.130-131
- nmap -Pn --script vuln 192.168.234.130-131
Test results
Nexpose detected 527 vulnerabilities (see Diagram 1), of which:
Report
167 - received the status “critical” - vulnerabilities must be closed first.
349 - received the status of “severe” - vulnerabilities are difficult to exploit, but can lead to serious consequences.
46 - received the status “moderate” - the vulnerabilities found can provide the attacker with information about the system, which he can use during the attack.
Vulnerabilities were found not only in tested systems, but also potential vulnerabilities in the virtualization system.

Tenable Nessus discovered 168 vulnerabilities (see Diagram 2), of which:
Report
3 - received the status “critical”
9 - received the status “high”
33 - received the status “medium”
5 - received the status “low”
118 received the status “info”
Vulnerabilities of the “critical” and “high” levels must be closed first.
Vulnerabilities of the “medium” level are difficult to operate, but if properly developed, they can be harmful.
Vulnerabilities of the “low” and “info” levels can provide an attacker with information about a system that he can use when conducting an attack through other vectors.

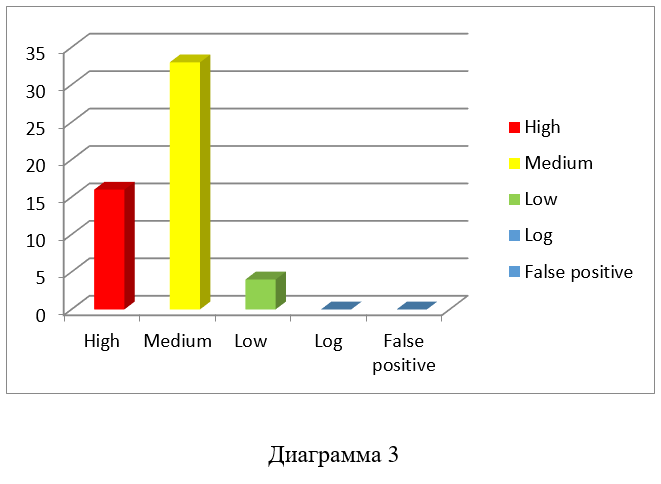
OpenVAS 9 detected 53 vulnerabilities (see Diagram 3), of which:
Report
IDS response results
16 - received the status “high”
33 - received the status “medium”
4 - received the status “low”
Vulnerabilities of the “high” level must be closed first of all .
Vulnerabilities of the “medium” level are difficult to operate, but if properly developed, they can be harmful.
Vulnerabilities of the “low” level can provide an attacker with information about a system that he can use when conducting an attack through other vectors.
Separately, it should be noted the results obtained using the Nmap scanner. Scanning was carried out by two commands, which were described above. The result of the execution was the output of information about the operating system, open services and found possible vulnerable services and links.
Using the vuln script identified the following types of vulnerabilities:
- open telnet
- http-csrf
- http-enum
- http-sql-injection
- http-vuln-cve2017-1001000
- rmi-vuln-classloader
- mysql-vuln-cve2012-2122
- ssl-ccs-injection
- ssl-dh-params
- ssl-poodle
- irc-botnet-channels
- http-cookie-flags
Nmap and IDS
Results Nmap Results Using the “vuln” and IDS Scripts
conclusions
To draw conclusions, I applied a quantitative method for assessing the total number of vulnerabilities found. As a result, it turned out that Nexpose conducts the greatest scanning depth. Nessus worked rather poorly, as in the network scan mode it issued a lot of service data about systems and services that only provide information for analytics. On a very weak side, the OpenVAS 9 scanner with the latest updates has shown itself. Nmap requires a separate word - a very good tool for conducting analytical testing with the ability to expand using NSE scripts.
During testing, IDS Suricata discovered NMap and OpenVAS scanners.
This test is not canonical, such as tests by Gartner or NSS Labs. But despite this, I think the article will be relevant for specialists in the field of system administration and technical audit.
PS And why was all this done?
It was necessary to
Sources
- habrahabr.ru/post/203766
- www.rapid7.com
- www.tenable.com/products/nessus/nessus-professional
- nmap.org
- habrahabr.ru/post/131433
- www.openvas.org
- metasploit.help.rapid7.com/docs/metasploitable-2-exploitability-guide
- blog.securitymetrics.com/2016/03/vulnerability-scanners-101-what-why-and-how.html eax.me/iptables
- suricata-ids.org
- www.resolver.com/trust/policies/threat-vulnerability-management-standard
- osxdaily.com/2014/05/20/port-scanner-mac-network-utility
