Check incoming data. The root cause of the vulnerability and attack on Cisco IOS
On Friday, April 6, 2018, a powerful attack on Cisco equipment began .
Many write that the main reason this attack is successful is the Cisco Smart Install service ports that are open on external networks.
These ports are open by default. And for the most part, people leave what is configured / selected / configured as it was by default. As you can see, on the example of this case, this applies not only to home routers, but also to serious equipment in large companies, where the cost of an error is much higher.
When creating a system, you do not have the right to rely on the fact that the default values that should be changed will be changed, and in the right direction.
You can only force to change these values with the help of any limiting the use of techniques. What many will not be happy. “Foolproof” is one example of these binding restrictions.
Pro default selection
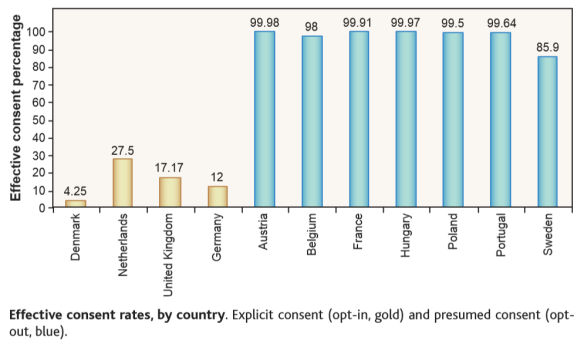
There is a 2003 study, “Does Life Save Default Choices?” , in which there is a diagram
in Russian in more detail .
It shows that the number of those who are ready to participate in the organ donation program greatly depends on what default choice is already made in the medical questionnaire.

in Russian in more detail .
It shows that the number of those who are ready to participate in the organ donation program greatly depends on what default choice is already made in the medical questionnaire.
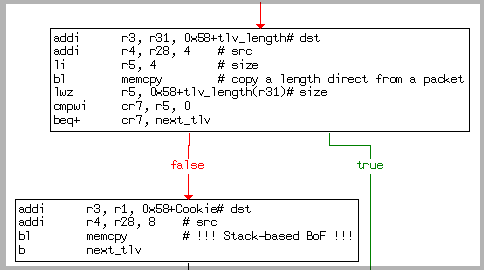
I want to pay attention to the root of the vulnerability itself. The report has such a part:
Buffer overflows occur in the smi_ibc_handle_ibd_init_discovery_msg functionThose. when receiving data from outside, there is no verification of their correctness.
due to the fact that their size is not checked when copying data to a fixed-size buffer. The size of the data and they themselves are directly taken from the network packet.
I believe that this is the main reminder that needs to be done again.
The programmer must check the data coming from outside. No data entered into the system by the user (whoever and whatever) may not be trusted.
PS By the way, this function is just an example of the fact that the programmer just took the default value, from where it is - from the network packet.
Only registered users can participate in the survey. Please come in.
Does your software product use input validation?
- 47% Yes, at the framework / system level 47
- 53% Yes, manually 53
- 19% No, internal product 19
- 5% No, product for third-party use 5
