DEFCON 23. “Let'sEncrypt: Minting Free Encryption Certificates for the Internet.” Yang Zhu, Peter Eckersley, James Casten
- Transfer
My name is Yang Zhu, I am a Yahoo security engineer, this is Peter Eckersley, a leading computer specialist at the Electronic Frontier Foundation, a technology team leader, and James Kasten, a technology and graduate student in computer science and engineering at the University of Michigan. So, which of you was shocked by the ability to encrypt the entire Internet? I am delighted with your enthusiasm!
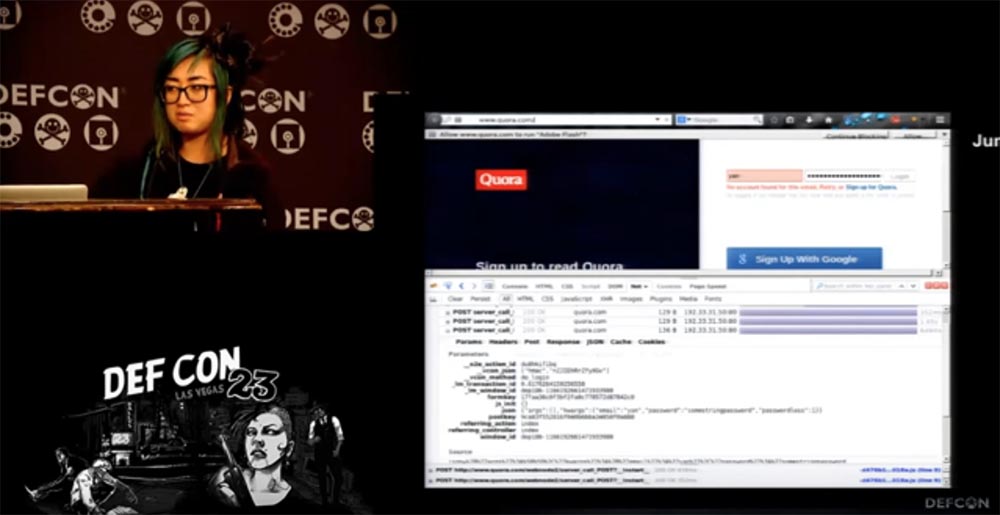
So, what problems do the world care about besides global warming, childhood hunger and all that? The problem is that TLS transport layer security protocols are still not widespread, even in 2015. Last summer, when I wanted to use the Quora website, I went to the authorization page and saw that it was implemented based on simple http, which is already bad. In addition, http is open to attack by malicious tools and transmits your passwords in clear text. This is really bad if you see every day millions of active users who enter the site in this way. The purpose of Quora is to disseminate social knowledge, and perhaps misinformation of users, this is a site of questions and answers on various topics.
There is still such a small site called Google, let those who heard about it raise their hands, so here they were always good enough in the sense of using SSL. However, some pages, like this landing page of Google Ads applications, still use the standard HTTP protocol by default. You can say that there is nothing to worry about, it is a static public page that does not require user data. But a person like me who understands these issues will check where the Log In button leads. An ordinary user, not suspecting anything, after clicking on this button can be redirected to a phishing site, where he will enter his registration data.

And since HTTP is used here, this is still a problem.
The second problem is that obtaining TLS transport layer security protocols is still very tedious, even in 2015. Whoever heard of this, let him raise his hand. I see a lot of them. If you want to do this, you can go to wiki.cremehost.com and see the 12 steps you need to take to get an electronic signature certificate certified by a CA. And although you are not Alcoholics Anonymous yet, even for you this procedure is quite tedious.
Consider how long it takes to configure TLS. I have a video here about this. I spoke with many of my EFF colleagues whether they can configure TLS, and none of them have done this before. Hope my video works.
Part 1 - Parker Higgins, EFF activist.
“Hi Parker, what are you doing today?”
- I'm trying to install HTTPS on my test site.
- Well, is that fun?
- Maybe I don’t know yet.
- Can I make a video about how you do it?
- Yes you can!
- Well!
And then you see that he does it with difficulty. He clicks on the Assistant button, the page loads again and again, but it fails. I tell him that probably he won’t succeed today, and I’m leaving.
Part 2 - Noah.
A similar process continues here, which in total took Noah for almost 9 hours. He cannot understand what is happening with his mail and how to set up a certificate, so he goes to drink coffee. Three hours later, I return to him.
“This is the site we are trying to protect.” And this button is again inactive. I can not screw the certificate here. A message arrives: "Not all fields are filled." I will try to fill them again. So, the inscription "Congratulations" popped up! Is that why I spent so much time?
Ok, let's continue, try to launch our site. We find it in the drop-down menu of the form, click on it, wait ...
Information is displayed on the screen, and Noah says in surprise: “What does this mean? In my opinion, this is my sister's letter, some kind of bill, payment. Is this my browser at all? ”
Another hour passes. I return to Noah, who is still waiting for his letter confirming the success of receiving the certificate of the encryption security key for his site. He says that he received a letter of gratitude for using the certification service, but when he tries to follow the link indicated in the letter, nothing comes out of him, perhaps this is due to problems with the proxy server on his side.
Noah says that an hour passed, during which he made several more unsuccessful attempts to obtain a certificate, but nothing came of it. I apologize for this sad video.
So, we made sure that the certification process takes several hours, is associated with many errors and is often unsuccessful.
Problem three is that TLS has a confusing configuration.

Suppose that everything went perfectly for us, we got our certificate and want to install it on the server. But all of his settings are really very confusing. A few years ago, people said: "We have a stream cipher RC4, excellent, it is very effective!" But now, in 2015, experts such as Nick from the CloudFlare content delivery network claim that we must destroy RC4.
Another example is the Secure Hash Algorithm SHA-1 cryptographic hashing algorithm, which is also recognized as unsafe because sooner or later your site that uses this hashing and certificate chains will be recognized as unsafe by Chrome and Firefox browsers.

Therefore, I bring to your attention a film called "SHA-256: Deliverance." This movie is about a man who was mistakenly accused of using SHA-1 on his website and kicked out of work. He meets Morgan Freeman and spends all his time to convince people that he actually used SHA-256. Watch in all cinemas of the country! It was a joke!
Now let's move on to the next problem, entitled "How to protect the server from the POODLE SSlv3 vulnerability." People say that they abandoned the SSL v.3 cryptographic protocol because it was susceptible to Logjam attacks that could decrypt or crack any TLS connection established with improperly configured web services or mail servers.
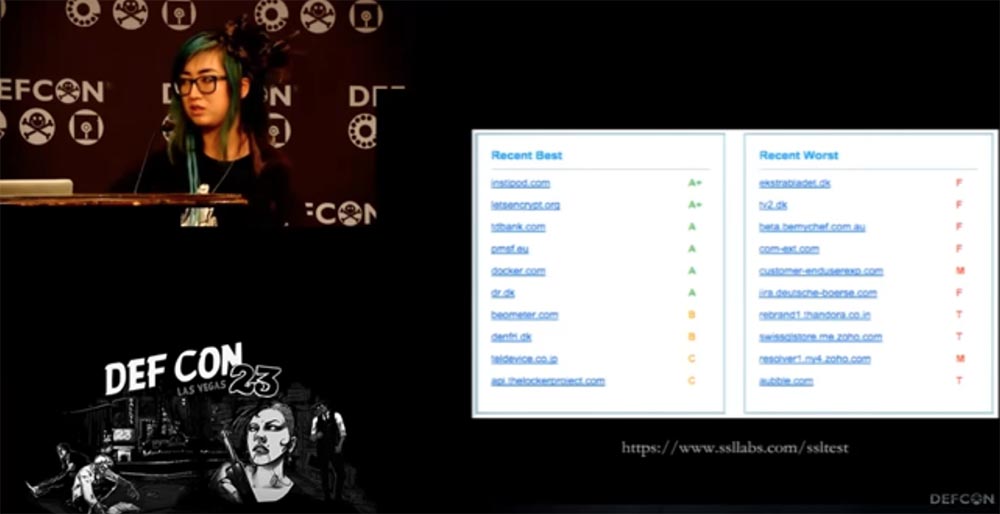
I want to show you the results of a site audit performed by the independent laboratory ssllabs.com. As you can see, our letsencrypt.org site has the highest A + rating and is one of the best sites in terms of security, because ssllabs is a serious organization and you can trust them. We use the latest ciphers from the recommended list. You see other sites that have received a minimum rating of F. The problem is that many people still cannot correctly configure SSL and they use broken encryption.
Problem # 4 is blocking mixed content. Your site may be blocked when you use SSL, but download all resources via HTTP. The browser believes that it should move this user to the HTTPS security level and therefore blocks its HTTP content. As a result, the site ceases to function if you download scripts via HTTP. In the case of Lenovo, which I checked a few nights ago, they could use HTTPS, but they could not even upload their fonts through it, because by default they had to use HTTP. I will show you on the slide which sites use only HTTPS.
Peter and I are working on browser extension support. Therefore, if you use the Chrome browser, you can see that all its resources can be read as HTTPS. That is, we have a useful tool so that you can turn your site from insecure to secure. If you use third-party content and don’t know if it supports SSL, then you can use the developer's tool in the form of a table and play with it. This will help rewrite resources, which can help you a lot.
There is a new page title called “upgrade insecure request”, “updating unsafe requests”, and when the browser sees it, it understands that all subresource of the site and links must be converted to HTTPS, even if they are written in HTTP. So you can use this header for your sites.
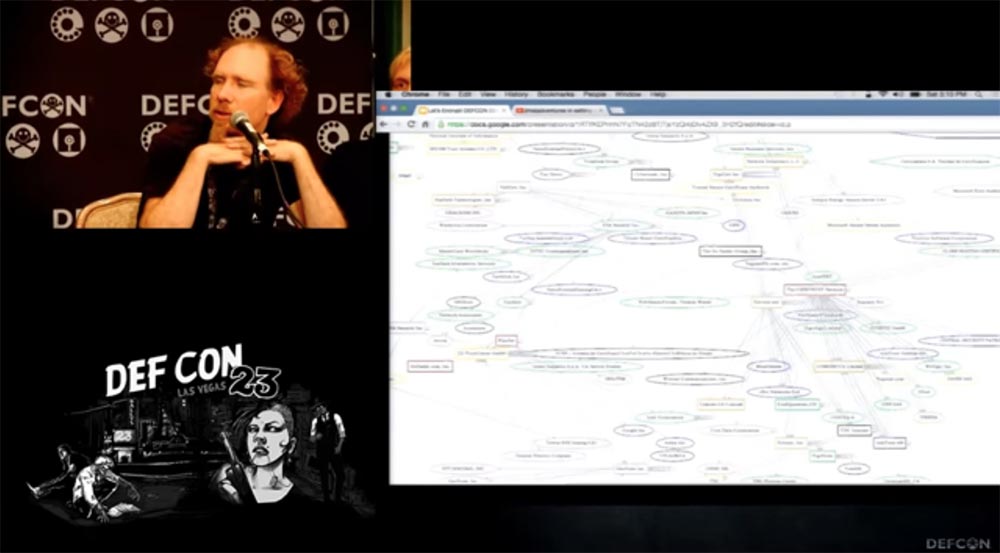
Problem # 5 is that there are too many trusted organizations that issue security certificates. A year ago, Peter even drew a very complex table that you see on the screen. Peter, explain what she means!
Peter Eckersley says this is far from a complete map, but just a part. It was presented at DEFCON in 2010 by the SSL Odservatory project. We found out that at that time there were 66 authorization centers in Firefox and almost 150 in IE. When we scanned the Internet, we made sure that they were all authorized and certified by other certificate authorities, and they were trusted by browsers. There were thousands of CASs, Authentication Service Centers that could compromise hundreds of organizations and domains on the network, and it looked horrific. Last year, Google discovered erroneous certificates issued by the Chinese certification authority, so this is not just a theoretical attack on website security.
And now I give the floor to Peter, who will tell how we see the world in the future.
I will tell you about how we see a solution to these problems. Firstly, you can create your own LetsEncrypt Certificate Authorization Center, free, automated and open. I see you enjoyed this joke!
In fact, we need a detailed review of both security and all sites that need it. We need a solution that would both provide security and usability.
People who call themselves web developers do not want to go deep into all the details of using SSL vulnerabilities and do not need it. Therefore, the most important question we must answer is how we are going to issue certificates. Because the current situation is reminiscent of the scenes from the Holy Grail, when you are ordered to go there - I don’t know where and bring that - I don’t know what. And when you bring it, it turns out that this is not at all what was required of you.
The question, which I will designate by the number “zero”, is called “Self-loading”. This refers to the use of an existing option to create a new one. Which solution should we use based on the old encryption? The usual answer to this question is Domain Validation DV, or the legalization of a domain name. This does not require a thousand-dollar payment, it is enough to send a letter to the address or place a request on the site to upgrade the security protocol.
What types of DV does Let's Encrypt use? For download, this is the DVSNI protocol through port 443 or simple HTTP through port 88 for those using a proxy server. In this case, CAS checks your administrative rights to manage the site so that you can configure it. Using the link to the resource indicated in the letter, we go to you and check the response “handshake” of TLS, and conduct several test attacks on your resource to make sure it is secure.

Many people ask me about the possibility of legalizing DNS names, maybe later we will implement this function for clients along with the ability to upgrade the protocol for DVSNI 2 domains for ports 443 and 100. If you have thousands of domains on your shared hosting, you can make just one change to the protocol instead of a thousand changes. This can be done on various ports, including special ones, such as port 443, which usually hosts a firewall. We have the ability to audit ports that users want to use through a wide scan of the Internet.
Many are afraid of everything related to domain validation. The Internet in this case seems to be a dark hole, the way you send packets of information, they disappear in the middle of the path, and some come back to you and say: “yes, I really am this domain!” Whether your packages will be eaten by evil monsters or modified along the way, you do not know. You can be attacked if your router or DNS server is not properly secured. The methods described above are not very perfect, so we can use a more "advanced" verification technique. We can use a multivariate verification path in which we use data center servers and other resources of the world wide web and create several versions of validation requests or several versions of DNS queries. This method does not protect you from the attack of a more powerful opponent, because he can exploit the vulnerability of his victim’s router and get to you through him. So DV is not the best way to protect when creating a security infrastructure for the entire Internet.
However, we have a better protection option. Fortunately, the “travel on the unlit Internet highway” described above needs to be completed only once. We discussed the SSL study project at the DEFCON conference 5 years ago, and since then we have conducted a series of studies thanks to the support of users of Firefox and Google who have sent us millions of certificates and thanks to the ZMap project, which James is working with the University of Michigan team. Now that we have a huge database of certificates and a whole syllabus (list of misconceptions), we can help a person even when he asks us to check the domain name of the New Zealand Bank. We have never heard of this bank's corporate network mail, but we can advise our client to look at the certificate database and see

Access to the database is provided by scanning ports 443, viewing logs of the CT standard (Certificate Transparency), or at the request of the client. We are not going to verify your unencrypted domain, but ask you to prove that you own the private key of the existing legalized certificate. Thus, you can always get our certificate or a certificate of another CAS, if you already own the fingerprint of a key of an authorized security certificate.
This is not very convenient, because it forces you to look for this very key. If you lost it, you will have to go through the entire certification procedure again and pay for the entire package of settings.
If you have heard anything about TOFU authentication, Trust on first use, you know that this mechanism relies on the fact that the first transmission of the key was not compromised, remembers this key and rejects the security confirmation when it is suddenly changed. Most likely, you are familiar with it by the SSH secure shell model. This is a good solution in some cases.
The next important issue is the problems of TLS and HTTPS. We encounter this problem when configuring TLS incorrectly, as Ian has already talked about. In this case, you are vulnerable to poodles, logjam and hotblades attacks. All that is needed to solve this problem is a client that runs on your server and magically configures it as it should. Because there is a huge number of sites, servers and a huge array of information, and serious knowledge is needed to meet all the requirements. We are a small team of people who are trying to contribute to solving the problem. We want to configure TLS correctly and share our tools with everyone who needs it.
What is the goal of the client that we are going to support? It consists in the fact that the user receives this client for six months or a year and with its help maintains the settings of the existing server on the Apache / Nginx engine or another in the current state, making the necessary changes and then installing the resulting certificate. At the same time, the client adjusts the security functions in an optimal way to obtain the best result for the specific configuration of your server and automatically updates the security system in accordance with current requirements. That is, it automatically counteracts security incidents that create massive problems when using HTTP.
What is meant by security automation? This is a whole range of tasks of varying complexity, which are solved in automatic mode. Easy tasks include configuring Cipher encryption sets, OCSP stapling, and CSP upgrade. More complicated is the translation of HTTP 302 (redirection code) to HTTPS for modern clients, because mixed content can be blocked even if security settings are updated, and mixed certificates must be used here: new for new content and old for old HTTP content . A task of medium complexity is also auto-renewal and reassignment of keys in case of domain name changes, because again you need to have a set for the old name and a set for the new one.
The challenge is to completely rewrite certificates and HSTS. HSTS is a mechanism that activates a forced secure connection via the HTTPS protocol instead of using the HTTP protocol, which allows you to immediately establish a secure connection. If you do not use HSTS, your site is completely unprotected, however, this mechanism has some secret properties that can put your site in case of incorrect security settings.
The biggest challenge is auditing and fixing mixed content. Its solution is possible, but it is a serious engineering task.
The third important issue is that CA authorization centers themselves are terrifying things because they control the security of the entire Internet, and we are trying to create an automatic giant certification authority, such a crazy machine that we are afraid of. What security design do we choose for this giant?
Launching your own CA is no less terrifying thing, however, we not only conduct research into existing threats, but also plan to detect and reflect security threats in advance in order to target our automatic giant.
Next, we consider the issue of protection from ourselves, that is, protection of our reputation as an SA. It implies full transparency of certification processes:
To protect against other CAs, we provide support for HPKP, or HTTP Public Key Pinning, if you are brave or crazy enough. Key Pinning is the binding of a public key to a network resource (by name or address) on the client side. With this technology, changing the fingerprint of a key allows you to detect key spoofing during an attack using the “man in the middle” scheme.
In addition, we provide recertification services if your resource has been unreasonably compromised by other certification authorities or attackers, as well as restore damaged keys.
I want to tell you about the institutions and organizations that support our Let'sEncrypt certificate authorization center, which was launched as a joint project of EFF, Mozilla and the University of Michigan.
This project was created so that most of the Internet sites could switch to encrypted HTTPS connections without paying, changing server configurations, using e-mail, so we have a very simple process of installing and configuring TLS encryption. For example, on a typical Linux-based web server, you only need to execute two commands that configure HTTPS encryption, receive and install a certificate in about 20-30 seconds.
Now it is based on our own informal group of Internet security research ISRG, the largest sponsors of which are EFF, Mozilla, Cisco, Akamai, IdenTrust and Automatic. CAS servers are developed by ISRG and Mozilla specialists, server codes are created by EFF and Mozilla, client codes are created by EFF and University of Michigan, and everyone else is involved in politics, legalization and bureaucracy.
We plan to release the first certificate on September 7, we will launch validation and beta version of the client in mid-October, and we will present the full version of our CA to the public on November 16.
Meanwhile, bureaucratic procedures take a whole bunch of time when we issue a document, then a document for this document and so on. All this makes certification more expensive and time consuming. We have several people involved in all of this, and if you are interested in our codes, client, server and specifications, or if you want to hack them, or help, or take part in our development, welcome the sources to the resources on the slide.
And now I want to invite James to the microphone so that he will tell you in more detail about our client and demonstrate his work.
James Casten takes the floor.
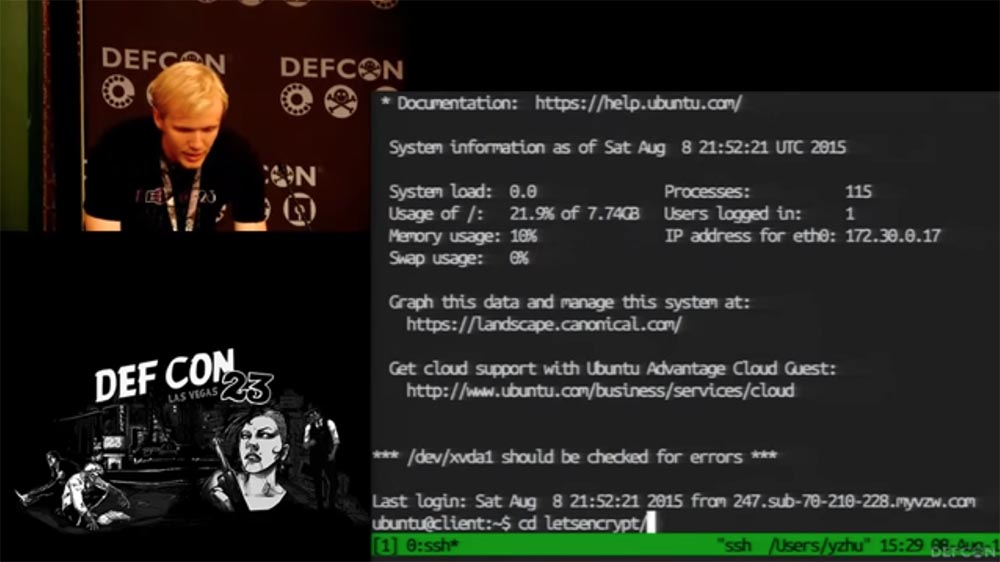
Now I’ll increase the font size so that what is happening on the screen of my laptop is clearly visible to you. I run our client, made in Python, in a virtual environment.
As an example, I will go to the site encryption-example.com, it was created by an enthusiast who loves to teach people encryption, but unfortunately, he does not know anything about it - we can not access this site via HTTPS.
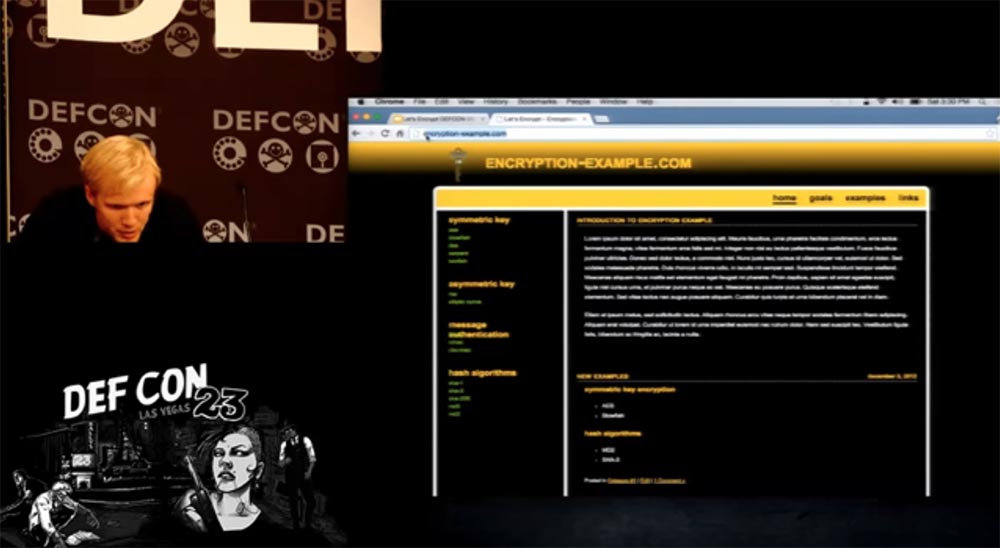
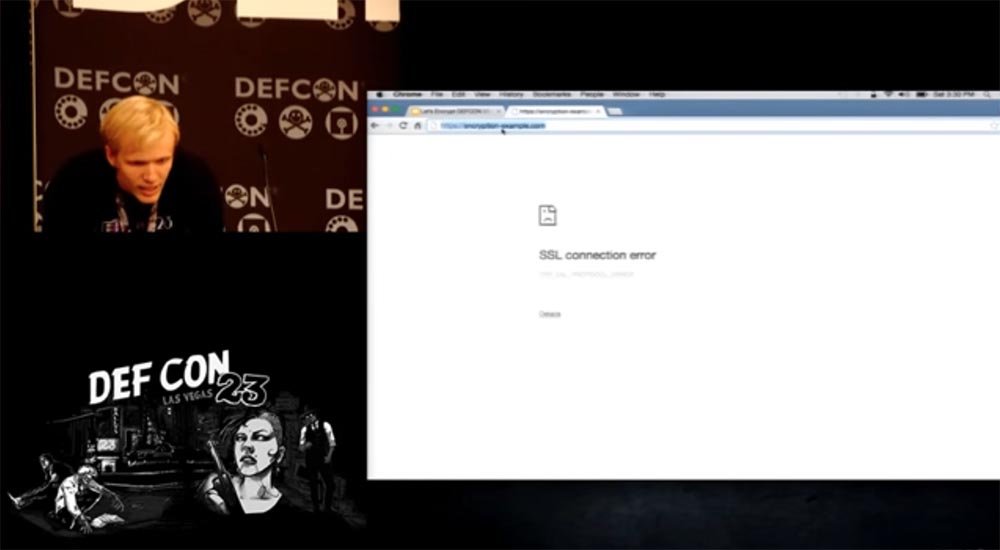
In addition, he is very interested in how to make money, so he registered a site to receive TLS Trust certificates of trust. There is everything for you to feel safe - there is both a logo and an icon with a lock, but this all doesn’t work with TLS at all - when you try to enter here via HTTPS, the site page does not open.

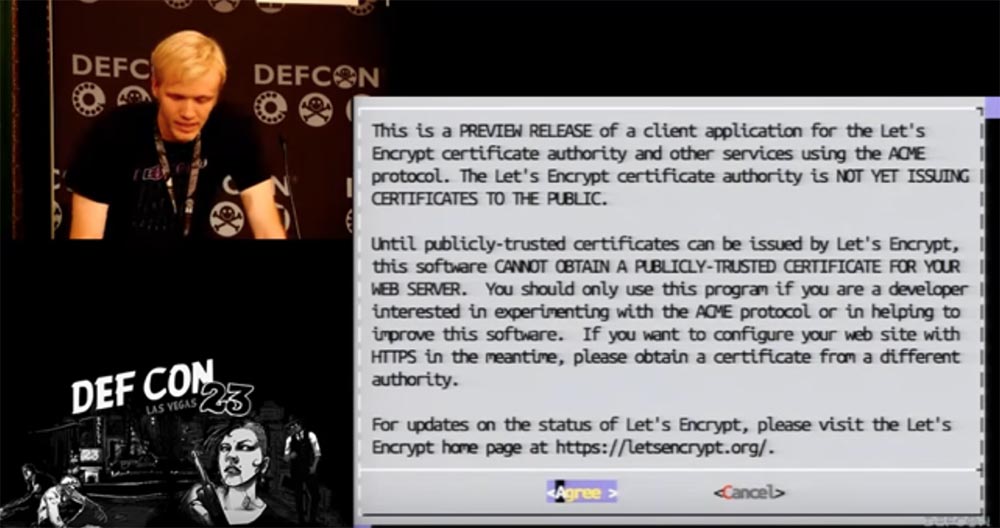
We will return to our client. It uses an Apache server. To continue, you must read the end user agreement and bear in mind that this version of the client is not intended to receive a public certificate.
The working version of the client will test the configuration of your server and check which names you use as the host, that is, it will examine the configuration files. Then she will make the necessary changes to the configuration file and configure TLS so that the site becomes secure and can be opened via HTTPS.
You can choose which domain name you want to use for verification, in the first test I use the encryption-example.com tested above. Our client will go through this resource, update the configuration of security settings, self-sign and save the test result for you, which will be reported on the screen. The whole process took 30 seconds.
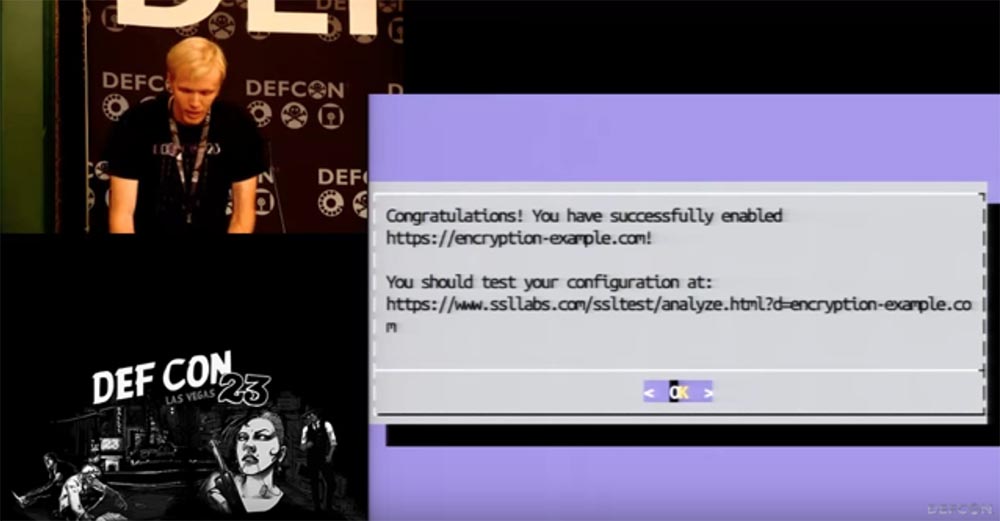
It says here that encryption-example.com has become available. Let's check through a public connection - indeed, now I can log in to it via HTTPS. As you can see, the result is on the face.
I want to note that you can always make all the necessary changes using the command line and not use any hints at all, our client will still install the settings and solve the server problems. It can also create a redirect from the original HTTP host to the new host. You can also optionally set up a dozen or a couple dozen security settings, such as HTTP redirection, OCSP stapling, and other configuration options.
People sometimes don’t want us to touch their configurations, but we have three rollback points for each configuration change process, so you can easily roll back all changes and again make the server unsafe for SSL connections via HTTPS. In this version, it is impossible to revoke the certificate, but we will have another management system that allows you to manually revoke all issued certificates when returning to the original configuration of the server security settings, as if we had not touched anything.
I wanted to show this in demo mode, but I could not quickly create the appropriate codes, especially for such a heterogeneous Internet.
But you should know that if we do not yet support your server, you can easily use a different configuration technology. In total, we have three authentication methods through the Let'sEncrypt client.
We have a manual authenticator that does not require root-rights, but simply creates for you a file that needs to be placed on the server. There is also a standalone authenticator, which is quite simple to run, after which the mathematical algorithm will create a certificate for you and place it in the correct server directory.
That is all I wanted to tell. Now you can ask us questions.
Question:
- How difficult was it for you to become an Authorization Center and get permission for this from the company - the developer and owner of the browser?
Peter:
- We did not talk about this! Tell me, how many people in the room think that in order to become a CA, you need to get permission from the browser? You think wrong! No permissions are required from the owner of the browser. All you need for this is to get one single authentication certificate, which guarantees you the right to certify certificates under the contract. And then you can work with any browsers that have been certified in existing CAs. Now we are going through an audit, and you can’t imagine how much time and money it takes and how much documentation we need to prepare. But soon we will finish with this, and it’s good that you need to go through this only once.
Question:
- Your demonstration of client capabilities through the command line was impressive, but are you planning to be integrated into products such as cPanel or VPS hosting environments?
Peter:
- Yes, we plan to use more convenient tools, for example, the API, just the command line is better adapted to work with Python. We have a simple API for new servers that will help you understand new types of services.
Question:
- Have you been working with the CRL certificate revocation list?
Peter:
- In fact, I can’t remember the case when we needed it. Such a need may arise if we are confident that Google and people who revoke certificates need a new way to implement this procedure. Our client will be launched with a three-month validation window, so we risk a little less in relation to work certificates than other CAs, since now the revocation mechanism on the Internet practically does not work.
Question:
- Now your client works with Apache and Nginx engines. Do you have plans to integrate with configuration management tools such as Chef and Puppet?
James:
- Yes, we have installers for Chef and Puppet. Now their use is not an urgent need, but we have the ability to integrate them into our client.
Question:
- Do you use the policy of your own public API in your client, and this is good, but do you plan to use third-party APIs somewhere?
Peter:
- No, we do not plan to use any other APIs except the existing ones.
Question:
- Why do some people say that not all sites need to have SSL? Probably they mean phishing sites?
Peter:
- We have two plans, or rather, two types of plans to combat phishing sites. But there is an X.509 public key certificate format that needs to be replaced with a more robust format. If the lock icon is used on a site with a public key, then this looks like a mockery, since in fact the connection is not secure enough. Therefore, we are looking for ways to make sure that the user does not initially get to an unsecured site, so as not to undergo a phishing attack, for example, redirecting it to a trusted site with a secure domain name. We mark such sites with a special label.
Question:
- The main goal of TLS is to eliminate the “man in the middle” threat. Suppose I connect to the encryption-example.com site and my browser selects port 80, in which case I become that very “man in the middle” and quietly bypass TLS. How can this be avoided?
Peter:
- The fact is that people do not know that they need to set a security flag on their “cookies”, and a huge number of sites do not miss “cookies” without such a flag. Therefore, all you need to ensure the security of sites is to install the HSTS suite. We are going to help in this site, but this method applies to things that can cause problems in the site. Therefore, we need good tools to quickly turn on HSTS, return to the previous state and the ability to inform the site administration that there are broken pages due to the attack and fix them. Perhaps this will help in time to find the "man in the middle" and isolate him.
Question:
- Are you going to support higher-level Wildcard certificates?
Peter:
- The APIs used do not allow support for such certificates, but we do not exclude this possibility in the future.
Question:
- Can your client be used to check .local domains?
Peter:
I think it makes no sense to use TLS in this case. We must strive to create non-conflicting domain names or create a new browser interface for these domains. Perhaps a new TOFU model should be created for this local namespace, but it should be separated from the public web naming space.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
So, what problems do the world care about besides global warming, childhood hunger and all that? The problem is that TLS transport layer security protocols are still not widespread, even in 2015. Last summer, when I wanted to use the Quora website, I went to the authorization page and saw that it was implemented based on simple http, which is already bad. In addition, http is open to attack by malicious tools and transmits your passwords in clear text. This is really bad if you see every day millions of active users who enter the site in this way. The purpose of Quora is to disseminate social knowledge, and perhaps misinformation of users, this is a site of questions and answers on various topics.

There is still such a small site called Google, let those who heard about it raise their hands, so here they were always good enough in the sense of using SSL. However, some pages, like this landing page of Google Ads applications, still use the standard HTTP protocol by default. You can say that there is nothing to worry about, it is a static public page that does not require user data. But a person like me who understands these issues will check where the Log In button leads. An ordinary user, not suspecting anything, after clicking on this button can be redirected to a phishing site, where he will enter his registration data.

And since HTTP is used here, this is still a problem.
The second problem is that obtaining TLS transport layer security protocols is still very tedious, even in 2015. Whoever heard of this, let him raise his hand. I see a lot of them. If you want to do this, you can go to wiki.cremehost.com and see the 12 steps you need to take to get an electronic signature certificate certified by a CA. And although you are not Alcoholics Anonymous yet, even for you this procedure is quite tedious.
Consider how long it takes to configure TLS. I have a video here about this. I spoke with many of my EFF colleagues whether they can configure TLS, and none of them have done this before. Hope my video works.
Part 1 - Parker Higgins, EFF activist.
“Hi Parker, what are you doing today?”
- I'm trying to install HTTPS on my test site.
- Well, is that fun?
- Maybe I don’t know yet.
- Can I make a video about how you do it?
- Yes you can!
- Well!
And then you see that he does it with difficulty. He clicks on the Assistant button, the page loads again and again, but it fails. I tell him that probably he won’t succeed today, and I’m leaving.
Part 2 - Noah.
A similar process continues here, which in total took Noah for almost 9 hours. He cannot understand what is happening with his mail and how to set up a certificate, so he goes to drink coffee. Three hours later, I return to him.
“This is the site we are trying to protect.” And this button is again inactive. I can not screw the certificate here. A message arrives: "Not all fields are filled." I will try to fill them again. So, the inscription "Congratulations" popped up! Is that why I spent so much time?
Ok, let's continue, try to launch our site. We find it in the drop-down menu of the form, click on it, wait ...
Information is displayed on the screen, and Noah says in surprise: “What does this mean? In my opinion, this is my sister's letter, some kind of bill, payment. Is this my browser at all? ”
Another hour passes. I return to Noah, who is still waiting for his letter confirming the success of receiving the certificate of the encryption security key for his site. He says that he received a letter of gratitude for using the certification service, but when he tries to follow the link indicated in the letter, nothing comes out of him, perhaps this is due to problems with the proxy server on his side.
Noah says that an hour passed, during which he made several more unsuccessful attempts to obtain a certificate, but nothing came of it. I apologize for this sad video.
So, we made sure that the certification process takes several hours, is associated with many errors and is often unsuccessful.
Problem three is that TLS has a confusing configuration.

Suppose that everything went perfectly for us, we got our certificate and want to install it on the server. But all of his settings are really very confusing. A few years ago, people said: "We have a stream cipher RC4, excellent, it is very effective!" But now, in 2015, experts such as Nick from the CloudFlare content delivery network claim that we must destroy RC4.
Another example is the Secure Hash Algorithm SHA-1 cryptographic hashing algorithm, which is also recognized as unsafe because sooner or later your site that uses this hashing and certificate chains will be recognized as unsafe by Chrome and Firefox browsers.

Therefore, I bring to your attention a film called "SHA-256: Deliverance." This movie is about a man who was mistakenly accused of using SHA-1 on his website and kicked out of work. He meets Morgan Freeman and spends all his time to convince people that he actually used SHA-256. Watch in all cinemas of the country! It was a joke!
Now let's move on to the next problem, entitled "How to protect the server from the POODLE SSlv3 vulnerability." People say that they abandoned the SSL v.3 cryptographic protocol because it was susceptible to Logjam attacks that could decrypt or crack any TLS connection established with improperly configured web services or mail servers.
I want to show you the results of a site audit performed by the independent laboratory ssllabs.com. As you can see, our letsencrypt.org site has the highest A + rating and is one of the best sites in terms of security, because ssllabs is a serious organization and you can trust them. We use the latest ciphers from the recommended list. You see other sites that have received a minimum rating of F. The problem is that many people still cannot correctly configure SSL and they use broken encryption.
Problem # 4 is blocking mixed content. Your site may be blocked when you use SSL, but download all resources via HTTP. The browser believes that it should move this user to the HTTPS security level and therefore blocks its HTTP content. As a result, the site ceases to function if you download scripts via HTTP. In the case of Lenovo, which I checked a few nights ago, they could use HTTPS, but they could not even upload their fonts through it, because by default they had to use HTTP. I will show you on the slide which sites use only HTTPS.

Peter and I are working on browser extension support. Therefore, if you use the Chrome browser, you can see that all its resources can be read as HTTPS. That is, we have a useful tool so that you can turn your site from insecure to secure. If you use third-party content and don’t know if it supports SSL, then you can use the developer's tool in the form of a table and play with it. This will help rewrite resources, which can help you a lot.
There is a new page title called “upgrade insecure request”, “updating unsafe requests”, and when the browser sees it, it understands that all subresource of the site and links must be converted to HTTPS, even if they are written in HTTP. So you can use this header for your sites.
Problem # 5 is that there are too many trusted organizations that issue security certificates. A year ago, Peter even drew a very complex table that you see on the screen. Peter, explain what she means!
Peter Eckersley says this is far from a complete map, but just a part. It was presented at DEFCON in 2010 by the SSL Odservatory project. We found out that at that time there were 66 authorization centers in Firefox and almost 150 in IE. When we scanned the Internet, we made sure that they were all authorized and certified by other certificate authorities, and they were trusted by browsers. There were thousands of CASs, Authentication Service Centers that could compromise hundreds of organizations and domains on the network, and it looked horrific. Last year, Google discovered erroneous certificates issued by the Chinese certification authority, so this is not just a theoretical attack on website security.

And now I give the floor to Peter, who will tell how we see the world in the future.
I will tell you about how we see a solution to these problems. Firstly, you can create your own LetsEncrypt Certificate Authorization Center, free, automated and open. I see you enjoyed this joke!
In fact, we need a detailed review of both security and all sites that need it. We need a solution that would both provide security and usability.
People who call themselves web developers do not want to go deep into all the details of using SSL vulnerabilities and do not need it. Therefore, the most important question we must answer is how we are going to issue certificates. Because the current situation is reminiscent of the scenes from the Holy Grail, when you are ordered to go there - I don’t know where and bring that - I don’t know what. And when you bring it, it turns out that this is not at all what was required of you.
The question, which I will designate by the number “zero”, is called “Self-loading”. This refers to the use of an existing option to create a new one. Which solution should we use based on the old encryption? The usual answer to this question is Domain Validation DV, or the legalization of a domain name. This does not require a thousand-dollar payment, it is enough to send a letter to the address or place a request on the site to upgrade the security protocol.
What types of DV does Let's Encrypt use? For download, this is the DVSNI protocol through port 443 or simple HTTP through port 88 for those using a proxy server. In this case, CAS checks your administrative rights to manage the site so that you can configure it. Using the link to the resource indicated in the letter, we go to you and check the response “handshake” of TLS, and conduct several test attacks on your resource to make sure it is secure.

Many people ask me about the possibility of legalizing DNS names, maybe later we will implement this function for clients along with the ability to upgrade the protocol for DVSNI 2 domains for ports 443 and 100. If you have thousands of domains on your shared hosting, you can make just one change to the protocol instead of a thousand changes. This can be done on various ports, including special ones, such as port 443, which usually hosts a firewall. We have the ability to audit ports that users want to use through a wide scan of the Internet.
Many are afraid of everything related to domain validation. The Internet in this case seems to be a dark hole, the way you send packets of information, they disappear in the middle of the path, and some come back to you and say: “yes, I really am this domain!” Whether your packages will be eaten by evil monsters or modified along the way, you do not know. You can be attacked if your router or DNS server is not properly secured. The methods described above are not very perfect, so we can use a more "advanced" verification technique. We can use a multivariate verification path in which we use data center servers and other resources of the world wide web and create several versions of validation requests or several versions of DNS queries. This method does not protect you from the attack of a more powerful opponent, because he can exploit the vulnerability of his victim’s router and get to you through him. So DV is not the best way to protect when creating a security infrastructure for the entire Internet.
However, we have a better protection option. Fortunately, the “travel on the unlit Internet highway” described above needs to be completed only once. We discussed the SSL study project at the DEFCON conference 5 years ago, and since then we have conducted a series of studies thanks to the support of users of Firefox and Google who have sent us millions of certificates and thanks to the ZMap project, which James is working with the University of Michigan team. Now that we have a huge database of certificates and a whole syllabus (list of misconceptions), we can help a person even when he asks us to check the domain name of the New Zealand Bank. We have never heard of this bank's corporate network mail, but we can advise our client to look at the certificate database and see

Access to the database is provided by scanning ports 443, viewing logs of the CT standard (Certificate Transparency), or at the request of the client. We are not going to verify your unencrypted domain, but ask you to prove that you own the private key of the existing legalized certificate. Thus, you can always get our certificate or a certificate of another CAS, if you already own the fingerprint of a key of an authorized security certificate.
This is not very convenient, because it forces you to look for this very key. If you lost it, you will have to go through the entire certification procedure again and pay for the entire package of settings.
If you have heard anything about TOFU authentication, Trust on first use, you know that this mechanism relies on the fact that the first transmission of the key was not compromised, remembers this key and rejects the security confirmation when it is suddenly changed. Most likely, you are familiar with it by the SSH secure shell model. This is a good solution in some cases.
The next important issue is the problems of TLS and HTTPS. We encounter this problem when configuring TLS incorrectly, as Ian has already talked about. In this case, you are vulnerable to poodles, logjam and hotblades attacks. All that is needed to solve this problem is a client that runs on your server and magically configures it as it should. Because there is a huge number of sites, servers and a huge array of information, and serious knowledge is needed to meet all the requirements. We are a small team of people who are trying to contribute to solving the problem. We want to configure TLS correctly and share our tools with everyone who needs it.
What is the goal of the client that we are going to support? It consists in the fact that the user receives this client for six months or a year and with its help maintains the settings of the existing server on the Apache / Nginx engine or another in the current state, making the necessary changes and then installing the resulting certificate. At the same time, the client adjusts the security functions in an optimal way to obtain the best result for the specific configuration of your server and automatically updates the security system in accordance with current requirements. That is, it automatically counteracts security incidents that create massive problems when using HTTP.
What is meant by security automation? This is a whole range of tasks of varying complexity, which are solved in automatic mode. Easy tasks include configuring Cipher encryption sets, OCSP stapling, and CSP upgrade. More complicated is the translation of HTTP 302 (redirection code) to HTTPS for modern clients, because mixed content can be blocked even if security settings are updated, and mixed certificates must be used here: new for new content and old for old HTTP content . A task of medium complexity is also auto-renewal and reassignment of keys in case of domain name changes, because again you need to have a set for the old name and a set for the new one.
The challenge is to completely rewrite certificates and HSTS. HSTS is a mechanism that activates a forced secure connection via the HTTPS protocol instead of using the HTTP protocol, which allows you to immediately establish a secure connection. If you do not use HSTS, your site is completely unprotected, however, this mechanism has some secret properties that can put your site in case of incorrect security settings.
The biggest challenge is auditing and fixing mixed content. Its solution is possible, but it is a serious engineering task.
The third important issue is that CA authorization centers themselves are terrifying things because they control the security of the entire Internet, and we are trying to create an automatic giant certification authority, such a crazy machine that we are afraid of. What security design do we choose for this giant?
Launching your own CA is no less terrifying thing, however, we not only conduct research into existing threats, but also plan to detect and reflect security threats in advance in order to target our automatic giant.
Next, we consider the issue of protection from ourselves, that is, protection of our reputation as an SA. It implies full transparency of certification processes:
- open publication of ACME server logs and the transactions we make;
- publication of a complete certificate verification history;
- publication of certificate Transparency standard logs.
To protect against other CAs, we provide support for HPKP, or HTTP Public Key Pinning, if you are brave or crazy enough. Key Pinning is the binding of a public key to a network resource (by name or address) on the client side. With this technology, changing the fingerprint of a key allows you to detect key spoofing during an attack using the “man in the middle” scheme.
In addition, we provide recertification services if your resource has been unreasonably compromised by other certification authorities or attackers, as well as restore damaged keys.
I want to tell you about the institutions and organizations that support our Let'sEncrypt certificate authorization center, which was launched as a joint project of EFF, Mozilla and the University of Michigan.
This project was created so that most of the Internet sites could switch to encrypted HTTPS connections without paying, changing server configurations, using e-mail, so we have a very simple process of installing and configuring TLS encryption. For example, on a typical Linux-based web server, you only need to execute two commands that configure HTTPS encryption, receive and install a certificate in about 20-30 seconds.
Now it is based on our own informal group of Internet security research ISRG, the largest sponsors of which are EFF, Mozilla, Cisco, Akamai, IdenTrust and Automatic. CAS servers are developed by ISRG and Mozilla specialists, server codes are created by EFF and Mozilla, client codes are created by EFF and University of Michigan, and everyone else is involved in politics, legalization and bureaucracy.
We plan to release the first certificate on September 7, we will launch validation and beta version of the client in mid-October, and we will present the full version of our CA to the public on November 16.
Meanwhile, bureaucratic procedures take a whole bunch of time when we issue a document, then a document for this document and so on. All this makes certification more expensive and time consuming. We have several people involved in all of this, and if you are interested in our codes, client, server and specifications, or if you want to hack them, or help, or take part in our development, welcome the sources to the resources on the slide.

And now I want to invite James to the microphone so that he will tell you in more detail about our client and demonstrate his work.
James Casten takes the floor.

Now I’ll increase the font size so that what is happening on the screen of my laptop is clearly visible to you. I run our client, made in Python, in a virtual environment.
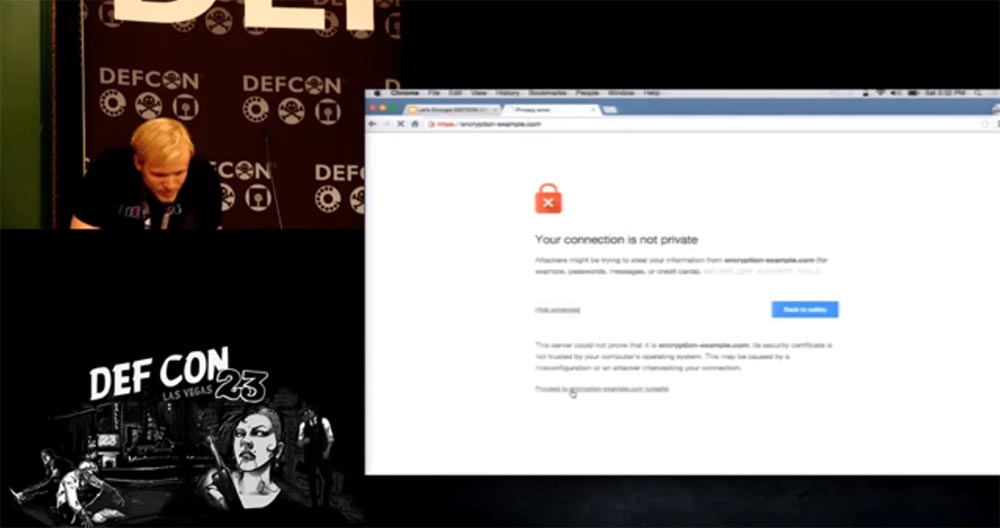
As an example, I will go to the site encryption-example.com, it was created by an enthusiast who loves to teach people encryption, but unfortunately, he does not know anything about it - we can not access this site via HTTPS.


In addition, he is very interested in how to make money, so he registered a site to receive TLS Trust certificates of trust. There is everything for you to feel safe - there is both a logo and an icon with a lock, but this all doesn’t work with TLS at all - when you try to enter here via HTTPS, the site page does not open.

We will return to our client. It uses an Apache server. To continue, you must read the end user agreement and bear in mind that this version of the client is not intended to receive a public certificate.

The working version of the client will test the configuration of your server and check which names you use as the host, that is, it will examine the configuration files. Then she will make the necessary changes to the configuration file and configure TLS so that the site becomes secure and can be opened via HTTPS.
You can choose which domain name you want to use for verification, in the first test I use the encryption-example.com tested above. Our client will go through this resource, update the configuration of security settings, self-sign and save the test result for you, which will be reported on the screen. The whole process took 30 seconds.

It says here that encryption-example.com has become available. Let's check through a public connection - indeed, now I can log in to it via HTTPS. As you can see, the result is on the face.


I want to note that you can always make all the necessary changes using the command line and not use any hints at all, our client will still install the settings and solve the server problems. It can also create a redirect from the original HTTP host to the new host. You can also optionally set up a dozen or a couple dozen security settings, such as HTTP redirection, OCSP stapling, and other configuration options.
People sometimes don’t want us to touch their configurations, but we have three rollback points for each configuration change process, so you can easily roll back all changes and again make the server unsafe for SSL connections via HTTPS. In this version, it is impossible to revoke the certificate, but we will have another management system that allows you to manually revoke all issued certificates when returning to the original configuration of the server security settings, as if we had not touched anything.
I wanted to show this in demo mode, but I could not quickly create the appropriate codes, especially for such a heterogeneous Internet.
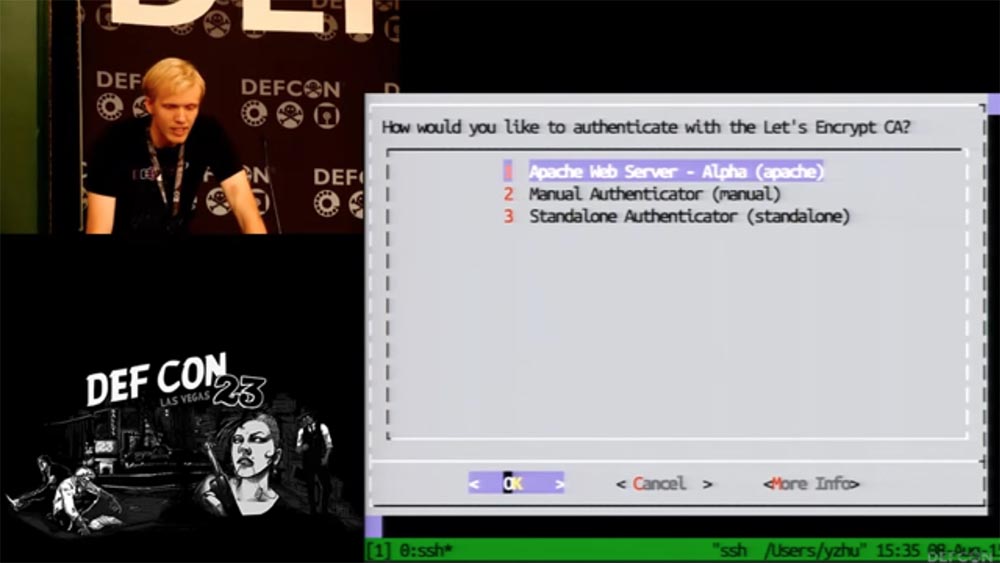
But you should know that if we do not yet support your server, you can easily use a different configuration technology. In total, we have three authentication methods through the Let'sEncrypt client.

We have a manual authenticator that does not require root-rights, but simply creates for you a file that needs to be placed on the server. There is also a standalone authenticator, which is quite simple to run, after which the mathematical algorithm will create a certificate for you and place it in the correct server directory.
That is all I wanted to tell. Now you can ask us questions.
Question:
- How difficult was it for you to become an Authorization Center and get permission for this from the company - the developer and owner of the browser?
Peter:
- We did not talk about this! Tell me, how many people in the room think that in order to become a CA, you need to get permission from the browser? You think wrong! No permissions are required from the owner of the browser. All you need for this is to get one single authentication certificate, which guarantees you the right to certify certificates under the contract. And then you can work with any browsers that have been certified in existing CAs. Now we are going through an audit, and you can’t imagine how much time and money it takes and how much documentation we need to prepare. But soon we will finish with this, and it’s good that you need to go through this only once.
Question:
- Your demonstration of client capabilities through the command line was impressive, but are you planning to be integrated into products such as cPanel or VPS hosting environments?
Peter:
- Yes, we plan to use more convenient tools, for example, the API, just the command line is better adapted to work with Python. We have a simple API for new servers that will help you understand new types of services.
Question:
- Have you been working with the CRL certificate revocation list?
Peter:
- In fact, I can’t remember the case when we needed it. Such a need may arise if we are confident that Google and people who revoke certificates need a new way to implement this procedure. Our client will be launched with a three-month validation window, so we risk a little less in relation to work certificates than other CAs, since now the revocation mechanism on the Internet practically does not work.
Question:
- Now your client works with Apache and Nginx engines. Do you have plans to integrate with configuration management tools such as Chef and Puppet?
James:
- Yes, we have installers for Chef and Puppet. Now their use is not an urgent need, but we have the ability to integrate them into our client.
Question:
- Do you use the policy of your own public API in your client, and this is good, but do you plan to use third-party APIs somewhere?
Peter:
- No, we do not plan to use any other APIs except the existing ones.
Question:
- Why do some people say that not all sites need to have SSL? Probably they mean phishing sites?
Peter:
- We have two plans, or rather, two types of plans to combat phishing sites. But there is an X.509 public key certificate format that needs to be replaced with a more robust format. If the lock icon is used on a site with a public key, then this looks like a mockery, since in fact the connection is not secure enough. Therefore, we are looking for ways to make sure that the user does not initially get to an unsecured site, so as not to undergo a phishing attack, for example, redirecting it to a trusted site with a secure domain name. We mark such sites with a special label.
Question:
- The main goal of TLS is to eliminate the “man in the middle” threat. Suppose I connect to the encryption-example.com site and my browser selects port 80, in which case I become that very “man in the middle” and quietly bypass TLS. How can this be avoided?
Peter:
- The fact is that people do not know that they need to set a security flag on their “cookies”, and a huge number of sites do not miss “cookies” without such a flag. Therefore, all you need to ensure the security of sites is to install the HSTS suite. We are going to help in this site, but this method applies to things that can cause problems in the site. Therefore, we need good tools to quickly turn on HSTS, return to the previous state and the ability to inform the site administration that there are broken pages due to the attack and fix them. Perhaps this will help in time to find the "man in the middle" and isolate him.
Question:
- Are you going to support higher-level Wildcard certificates?
Peter:
- The APIs used do not allow support for such certificates, but we do not exclude this possibility in the future.
Question:
- Can your client be used to check .local domains?
Peter:
I think it makes no sense to use TLS in this case. We must strive to create non-conflicting domain names or create a new browser interface for these domains. Perhaps a new TOFU model should be created for this local namespace, but it should be separated from the public web naming space.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
