Sysadmin needs long arms
A couple of years ago we wrote about ITSM systems, comparing them with the all-seeing eye of the sysadmin and even with a tambourine. The realities have changed. Information security has become the focus of attention not only of intergalactic large corporations, but even of small and medium-sized businesses. Too many risks surround companies in cyberspace, the most dangerous and obvious of which is the human factor associated with employees. They can harm intentionally, can be thoughtlessly, but always with any damage. In general, they need an eye and an eye. No special software is indispensable here. So what should they be, long arms of a system administrator?

Many companies rank ITSM systems as a set of elitist and unnecessary attributes such as ISO certification. This is because many people think that such systems are a reflection of the principles of ITIL, which over the past 10 years have not changed much, unlike the IT infrastructure. But this is absolutely not the case. As a rule, the software that helps build the ITSM strategy in the company uses the best practices of the ITIL library, but at the same time keeps pace with the development of business requirements and is much ahead of the postulates set forth in the treasured volumes. Today this is, first of all, the second reliable hands of the system administrator and the entire IT service, and only then the company's asset.
In fact, ITSM systems are needed for several purposes that an IT service faces literally every day.
To work with users. This is the most important functionality, coupled with saving resources (temporary, human, financial), improving business processes and keeping the IT infrastructure up to date. The ticket system solves several issues at once: it helps to collect information about incidents in a single database, accumulate a knowledge base and best practices, display the progress of solving a problem in a convenient form, comply with deadlines and even consider KPI of system administrators and evaluate the effectiveness of the technical support service based on a number of KPI if required by the company.
Pay attention to the ticket card in Alloy Navigator 8.0. It contains several fields, tabs and statuses from which you can get comprehensive information about the incident and its resolution. In addition, the program (as in most professional software of this kind) implements a powerful system of cross-connections, which allows you to see related objects and quickly gain access to them.
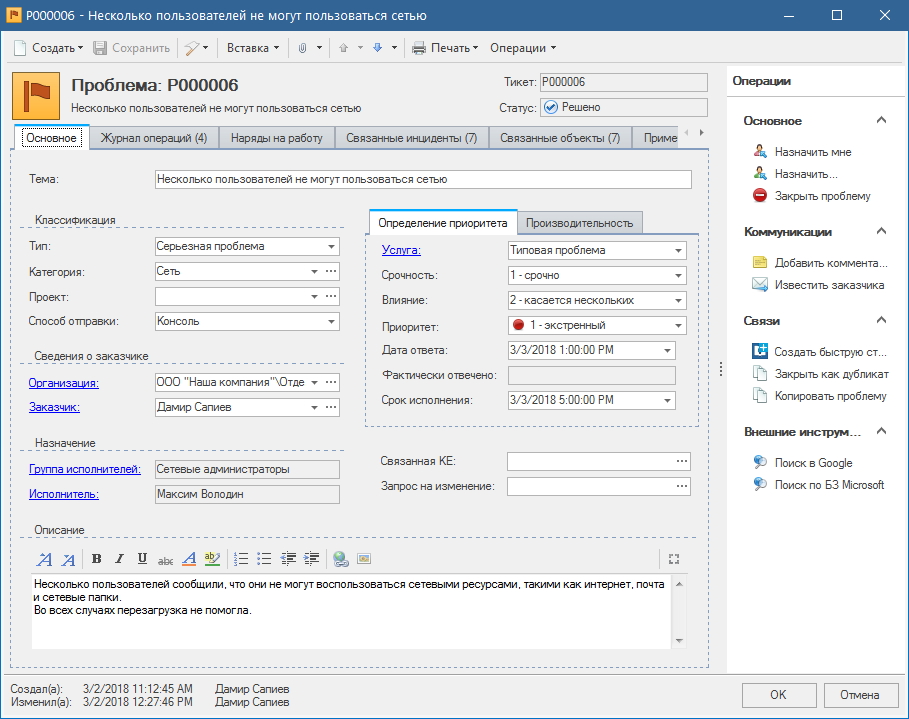
A ticket card is not the only such entity in the system; equipment, consumables, suppliers, employees, etc. have their own cards. Such data organization helps to access objects from different modules and connect them together.
But the main task of the ITSM system is working with the company's IT assets, that is, with hardware, peripherals, networks, software, consumables, etc. This makes IT infrastructure management transparent, tasks completed on time, tickets completed, and the work of the IT department as a whole is consistent with the SLA (even if you don’t have one).
And almost in the first place in the list of the most important system functions is license management, because this process is today one of the key elements of information security.
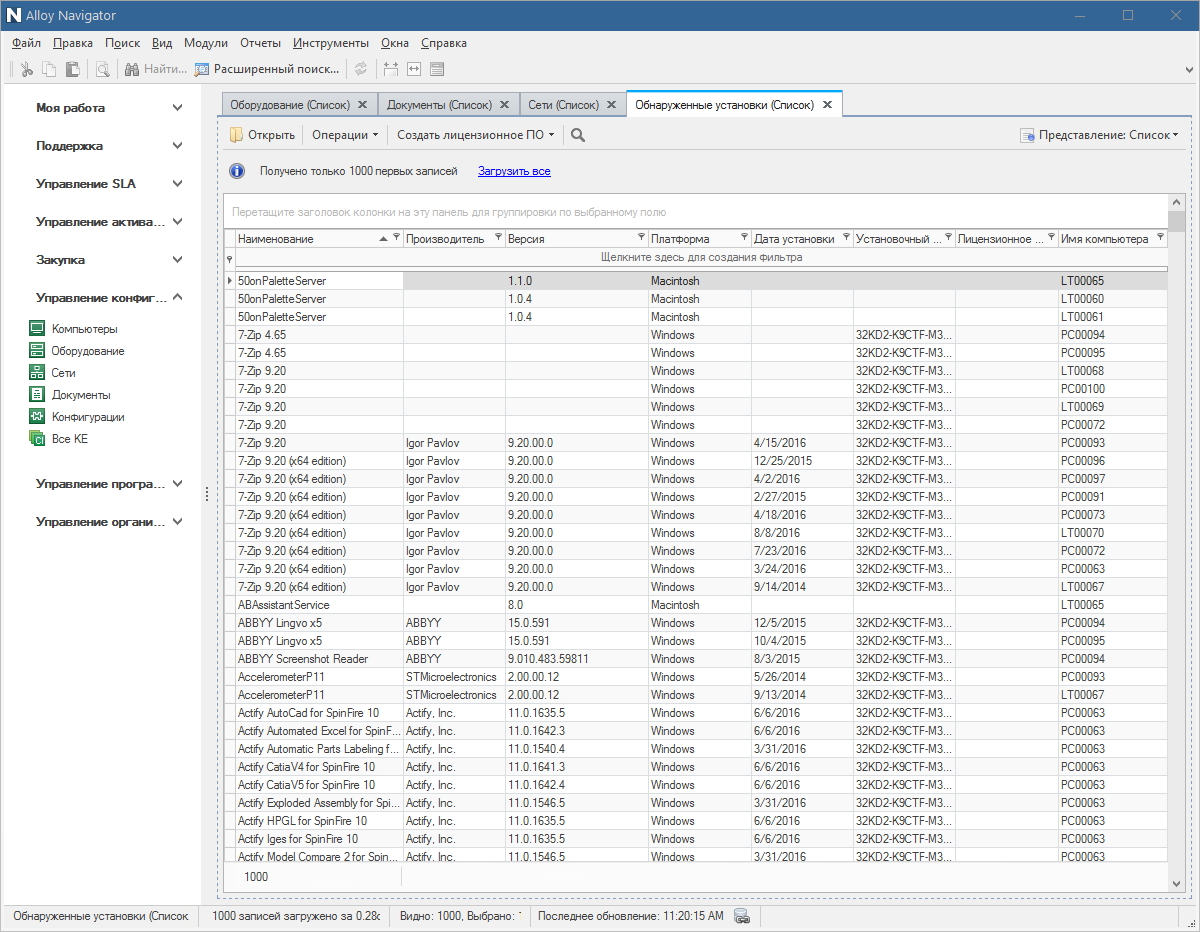
It is very convenient when in the ITSM system you can view exactly one software installation that users have with exactly one click, and filter the information as necessary. There are many pluses in the application, but the two main ones are the quick response to changes and the availability of complete information about the event. Now users will have no arguments like “it is itself”, “I see it for the first time” and “yes, it’s all installed here from the beginning”.
To support and maintain an asset inventory and audit, reducing the number of related routine operations in the work of the IT service. Inventory and audit - a tremendous stress not only for accounting and system administrator, it is also an interruption of the work process, and nerves, and great difficulties in working with equipment. The limit has already been reached when it is impossible to do everything with your hands, even in a relatively small company. It is much more convenient when all the equipment is collected in lists, you can view its attributes, analyze the condition, plan purchases and monitor the warehouse. You also won’t have to rewrite inventory numbers and re-stick labels - everything can be done using a mobile application that recognizes assets by a barcode and brings them into the system. Thus, the inventory takes place automatically with a minimum of manual operations.
Information on workstations, other equipment and networks is collected in the system interface in the configuration management module. Related documents created and uploaded by you are also available there (for example, financial or functional documentation, structural diagrams, service plans, etc.).
For the purposes of accounting, warehouse and financial accounting.Alloy Navigator 8.0 helps you track financial accounting information about the computer throughout the entire life cycle of the machine: standard depreciation is calculated, information about orders, warranty periods, rental cost (software or capacity), etc. is stored. This information is extremely important not only for the system administrator and technical service, but also for accounting. In general, in service and IT companies, ITSM systems are also in the service of financial workers - they are so interested in competent accounting that they even attend and take an active part in specialized conferences. Sometimes it seems to us that IT accountants understand the need for specialized software and monitoring almost earlier than administrators. And all because accounting is a tough business.
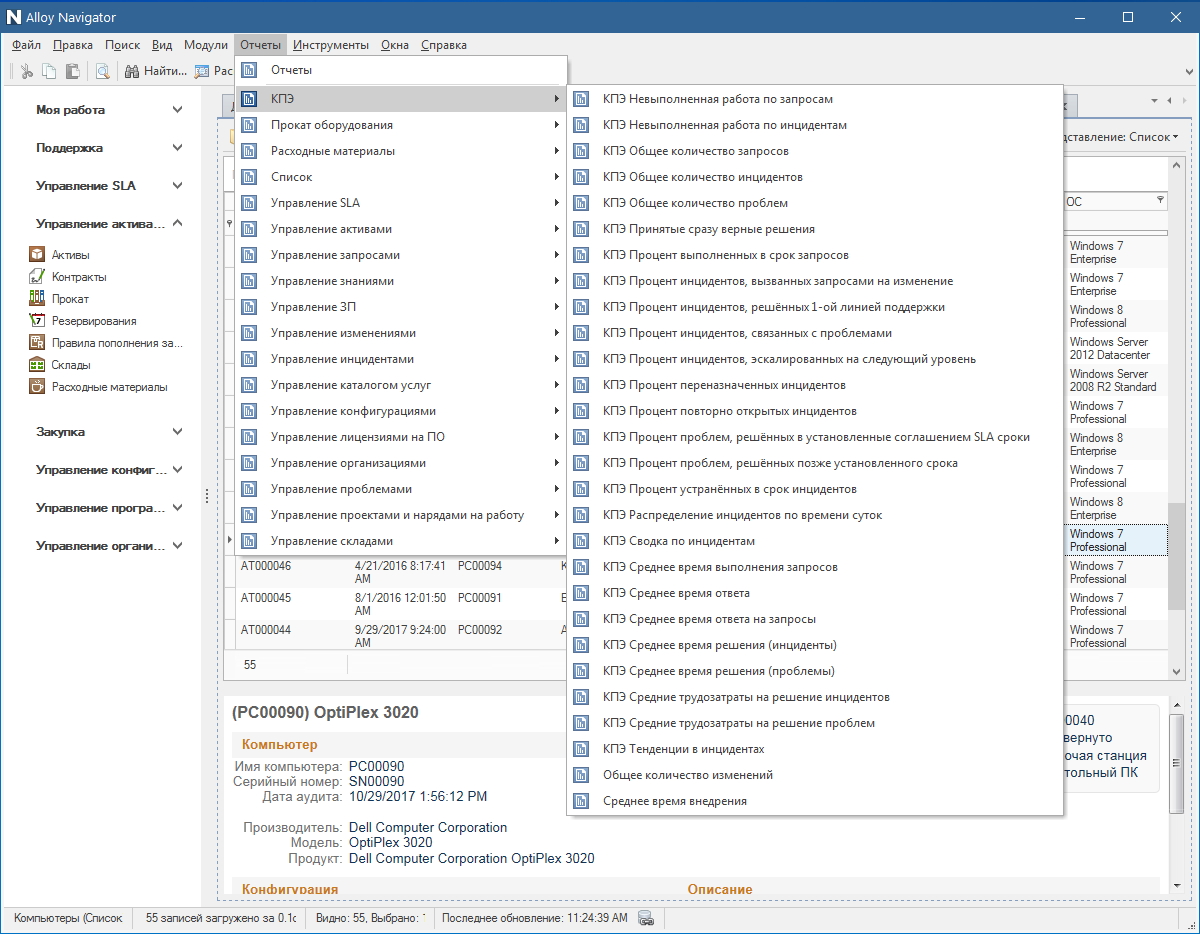
Another monetary problem that can be solved relatively successfully using ITSM systems is the calculation of KPI (KPIs - key performance indicators). Many copies were broken both at conferences, and in negotiation companies and vendors, and in comments on Habré in attempts to determine how to measure the work of the system administrator, how to evaluate unmeasurable factors, to arrange weights so that it really reflects the state of affairs, and does not give out monthly matrix for show. In Alloy Navigator 8.0, all work with KPI is done for you - indicators are generated in the form of 28 reports, all information is aggregated and easily accessible. The thing is small: take and use ready-made KPIs in the combinations that are necessary and significant for your company.
To plan the capacity of IT resources in the company.It is the users who believe that the task of the system administrator is to put the radiotelephone in the back pocket and rush to run to solve their problems, upload reports on the implementation or plan of the company in a month, and even be a “tyco programmer”. In fact, working with users, that is, essentially ensuring the smooth operation of business processes, is nothing but a part of the huge task of managing the complex set of all elements of the IT infrastructure. IT staff are required to control the appropriateness of technical resources, their location, operation and planning. And just planning is the main key to the effectiveness of all IT assets of the company. When working with the ITSM system, the administrator and the IT service can fairly accurately predict the timing of equipment replacement, decommissioning, etc. This means that equipment will change according to plan, and not be purchased as

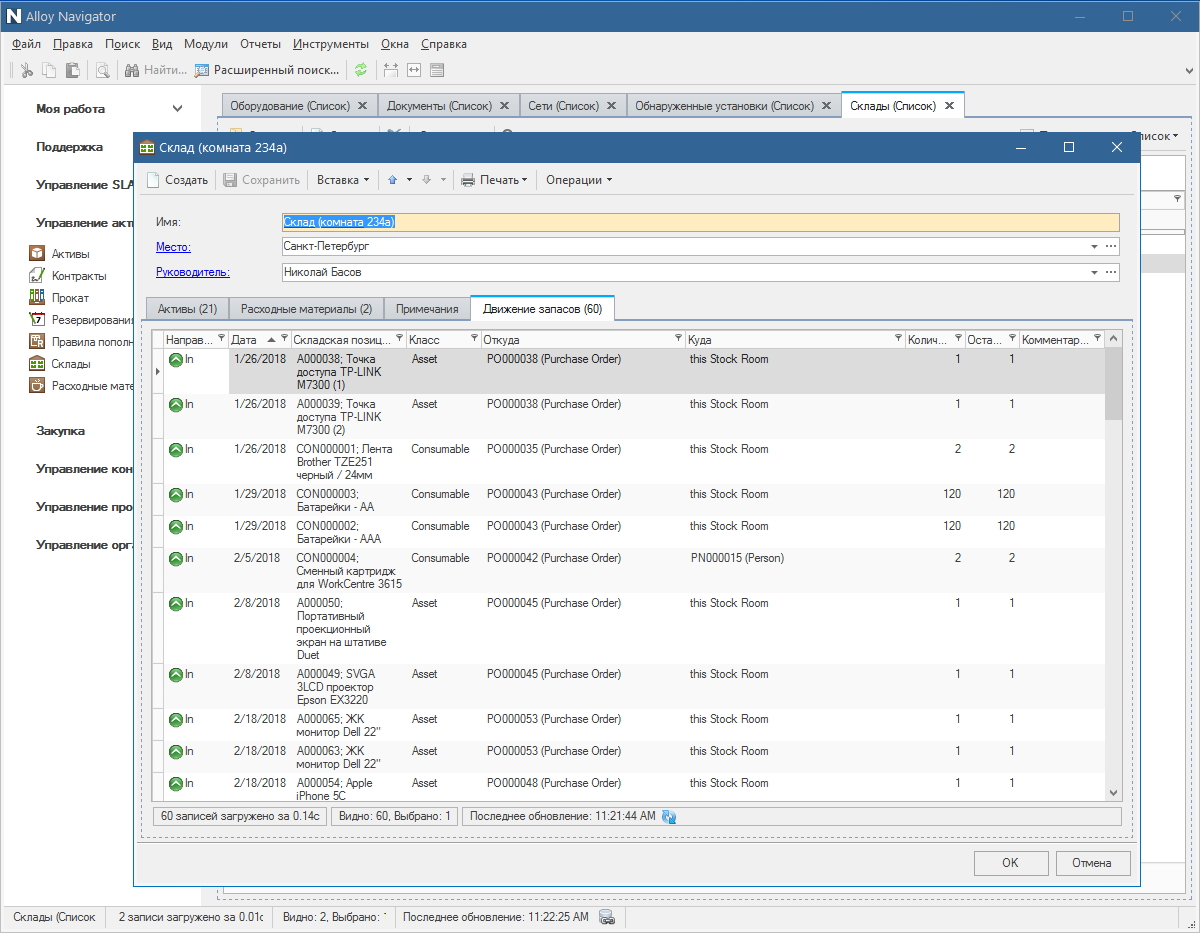
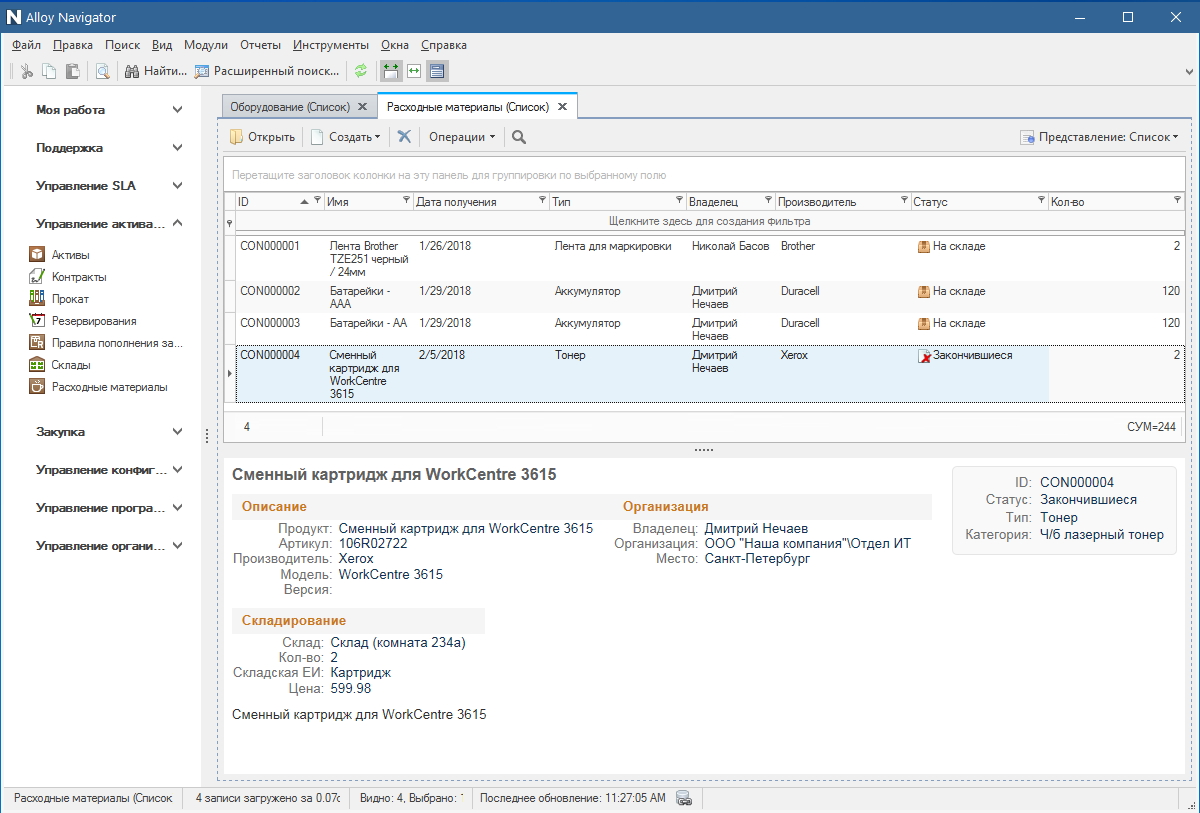
By the way, special attention should be paid to working with supplies. For example, a printer lives in a company for a long time, rarely breaks, but cartridges run out often. The office can only get up because they forgot to order toner on time. So, the use of the ITSM system eliminates such situations - the administrator can control the replenishment of consumables. Everything is simple: we looked at the consumables in the warehouse, estimated how much you need for the smooth operation of the office, if necessary, click on the neighboring module and form an order for the supplier from the existing list.
To ensure the security of the company's IT infrastructure. Here we are talking about information, economic and physical security. Alloy Navigator 8.0 is able to collect detailed information about the equipment that makes up the employee’s PC, settings, and installed software. Information is collected and stored in the form of snapshots (snapshots at a point in time) on a regular basis. This makes it possible to track all configuration changes. When is this important?
Snapshots make it possible to do a retrospective analysis of the state of working machines, track the timeliness and adequacy of changes.
To organize a support service. The ITSM system is invaluable software for outsourcing technical support services, for system integrators, vendors, and for technical services within companies. The program becomes a point of contact between users and IT services, while relations are formally and strictly regulated, saving time.
The IT service staff themselves also gain valuable experience in the form of a knowledge base and thereby increase both the speed of response to user requests and the speed of adaptation and training of new employees, which is especially important in the context of a sharp scaling of the company (when merging, expanding, changing the organizational structure and etc.)
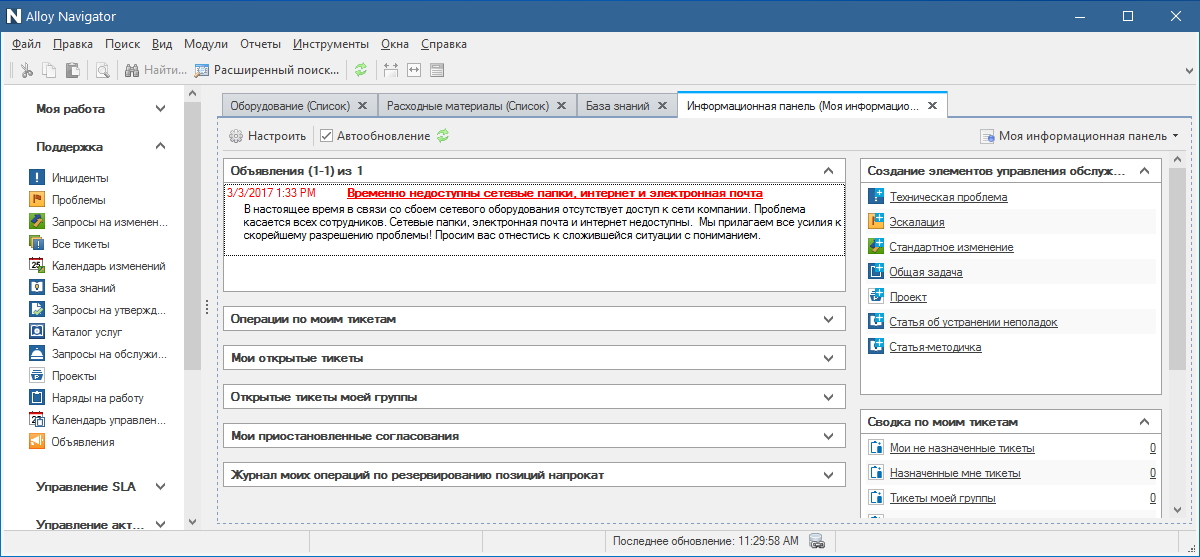
A good ITSM system is convenient to work with. For example, it has the desktop of a service engineer or system administrator (information panel), on which he can see tickets and a calendar, manage escalation and delegation of tasks.
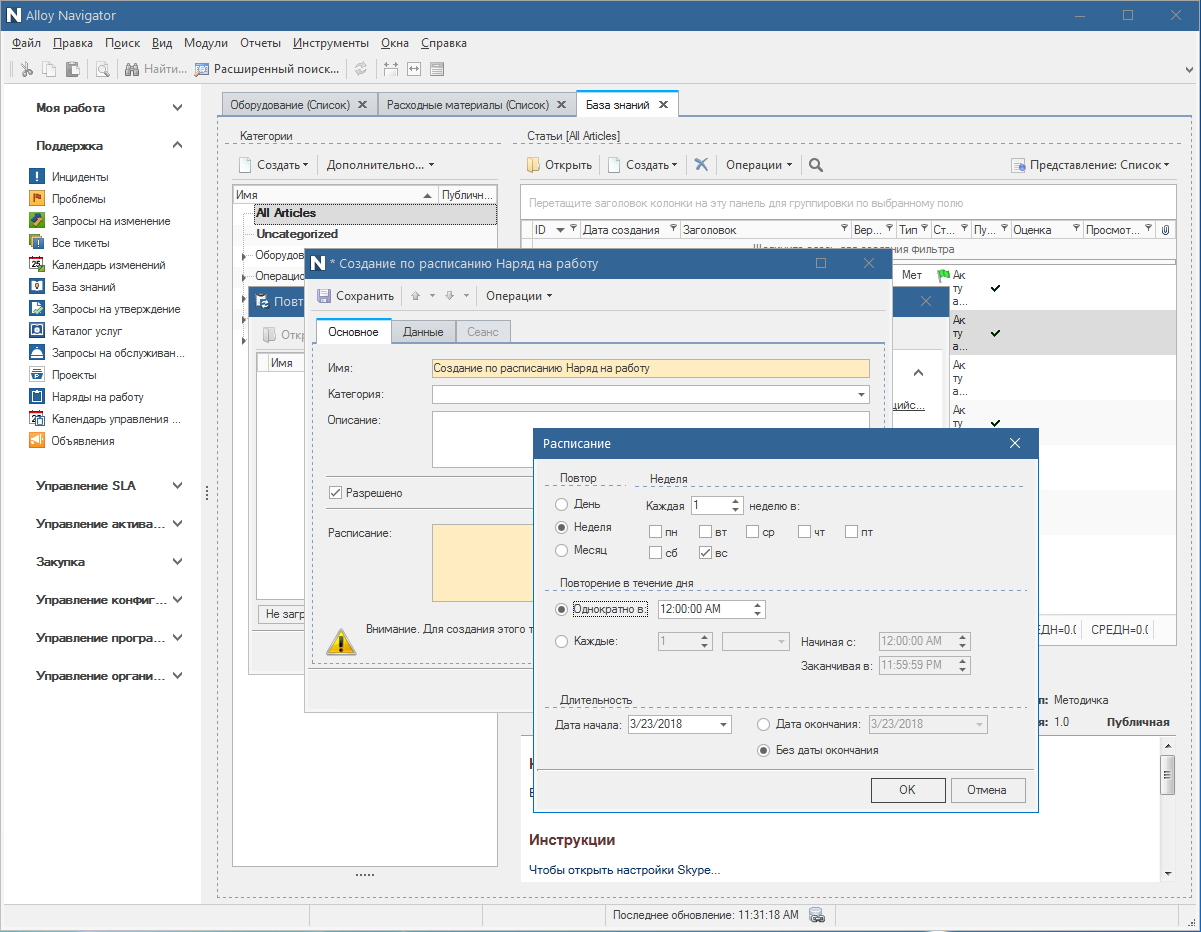
By the way, another useful feature of Alloy Navigator 8.0 is the recurring tickets, which guarantee the timely execution of regularly recurring actions (for example, the preparation of monthly reports). It is possible to bring matters into them and not to worry about someone forgetting to create a task in time for the next time, the system will notify those responsible. If you have been working in system administration for a long time, you will understand how cool it is and how many routine tasks you can reset to such cyclic tickets.
If you are too lazy to put a demo version of Alloy Navigator 8.0 (but in vain, there are a lot of interesting and narrowly professional ones, which you don’t have enough space to talk about on the blog), you can see a list of all available modules.
As you can see, the system includes all the key elements of a competent ITSM: configuration management, license management, SLA, warehouse and order formation, and most importantly, work with incidents and tickets.
If you open foreign publications about ITSM systems, you will find approximately the same words that the systems are designed to support the delivery of IT services to business users. That is, when 1C hangs up with the accountant, and the secretary has lost the Internet and they hysterically call the administrator’s mobile phone just gone for lunch, and he throws food and runs to the workplace, remembering a bit of profanity, this is the delivery of the service to a business user. In fact, we are so ironic, but only in part. The Russian reality is that in companies of any level, the relationship between the IT service and the rest of the employees is rather difficult. There are several reasons:
Of course, one system ( Alloy Navigator 8.0 ) cannot fully cope with these problems , we need help from detection and monitoring systems such as Alloy Discovery, antiviruses, CRM systems, well-thought-out methods of preventing violations at the operating system level, and competent use of group policies. But even without an ITSM system, the problems cannot be completely resolved.
Recently, many topics related to ITSM have appeared on Habré in the key to information security. Nevertheless, we believe that you should not limit yourself to protection, it is important to work with prevention, that is, use ITSM as a strategy for daily management of IT infrastructure. If you think that the costs of monitoring, accounting and automation are too high, you are mistaken - the system and the ecosystem created around it are paid off by reducing costs associated with service and incident response times, increasing the efficiency of resources and, of course, by preventing downtime in work.
The challenges that cyber reality sends to companies are reminiscent of the flu virus. As soon as a remedy for one strain is found and the world exhales with relief, a new, not yet fully studied mutation appears. And again, a threat to all of humanity. So it is with the IT infrastructure: neither external agents nor internal employees will let you get bored. For such a fight, you really need a cold head, cool skills and long arms.

We share great news.
At the very beginning of the article, we want to share the news, which already in January provided us with an excellent mood for the whole of 2018 - Alloy Navigator 8.0 is now available in Russian. Moreover, this is not a Hindu translation from the category of "watch the patch computer", but a high-quality native Russian-language interface. That is, the one you go into and feel likeathomein 1C.
By the way, one of the evidence of an awesome translation is our fact-finding guide , translated with character. You rarely see a manual without bureaucracy, which is just cool to read.
Here is an excerpt for you:
What is an ITSM system for?
Many companies rank ITSM systems as a set of elitist and unnecessary attributes such as ISO certification. This is because many people think that such systems are a reflection of the principles of ITIL, which over the past 10 years have not changed much, unlike the IT infrastructure. But this is absolutely not the case. As a rule, the software that helps build the ITSM strategy in the company uses the best practices of the ITIL library, but at the same time keeps pace with the development of business requirements and is much ahead of the postulates set forth in the treasured volumes. Today this is, first of all, the second reliable hands of the system administrator and the entire IT service, and only then the company's asset.
In fact, ITSM systems are needed for several purposes that an IT service faces literally every day.
To work with users. This is the most important functionality, coupled with saving resources (temporary, human, financial), improving business processes and keeping the IT infrastructure up to date. The ticket system solves several issues at once: it helps to collect information about incidents in a single database, accumulate a knowledge base and best practices, display the progress of solving a problem in a convenient form, comply with deadlines and even consider KPI of system administrators and evaluate the effectiveness of the technical support service based on a number of KPI if required by the company.
Pay attention to the ticket card in Alloy Navigator 8.0. It contains several fields, tabs and statuses from which you can get comprehensive information about the incident and its resolution. In addition, the program (as in most professional software of this kind) implements a powerful system of cross-connections, which allows you to see related objects and quickly gain access to them.

The same thing, but in the web interface of Alloy Navigator 8.0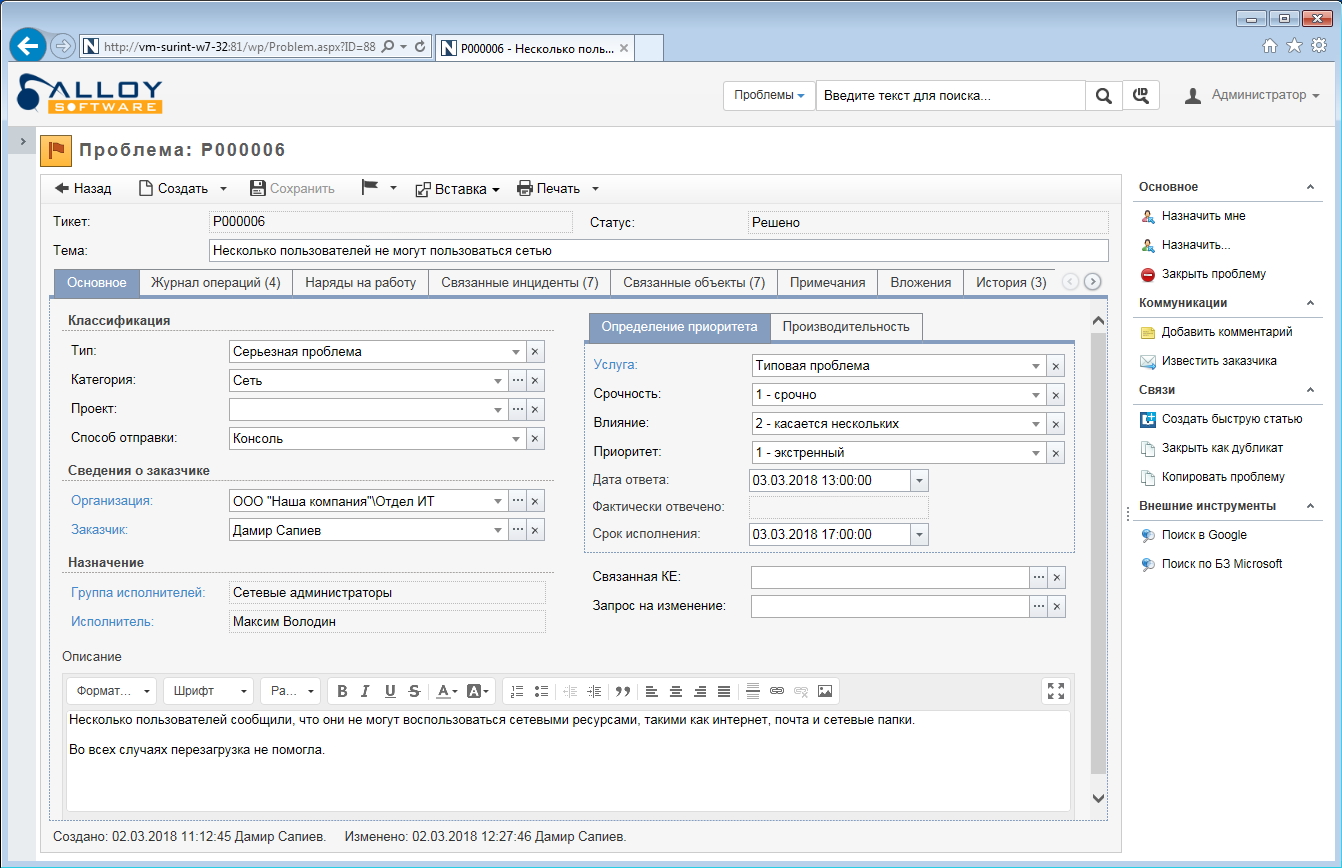

A ticket card is not the only such entity in the system; equipment, consumables, suppliers, employees, etc. have their own cards. Such data organization helps to access objects from different modules and connect them together.
But the main task of the ITSM system is working with the company's IT assets, that is, with hardware, peripherals, networks, software, consumables, etc. This makes IT infrastructure management transparent, tasks completed on time, tickets completed, and the work of the IT department as a whole is consistent with the SLA (even if you don’t have one).
And almost in the first place in the list of the most important system functions is license management, because this process is today one of the key elements of information security.
It is very convenient when in the ITSM system you can view exactly one software installation that users have with exactly one click, and filter the information as necessary. There are many pluses in the application, but the two main ones are the quick response to changes and the availability of complete information about the event. Now users will have no arguments like “it is itself”, “I see it for the first time” and “yes, it’s all installed here from the beginning”.

The same thing, but in the web interface of Alloy Navigator 8.0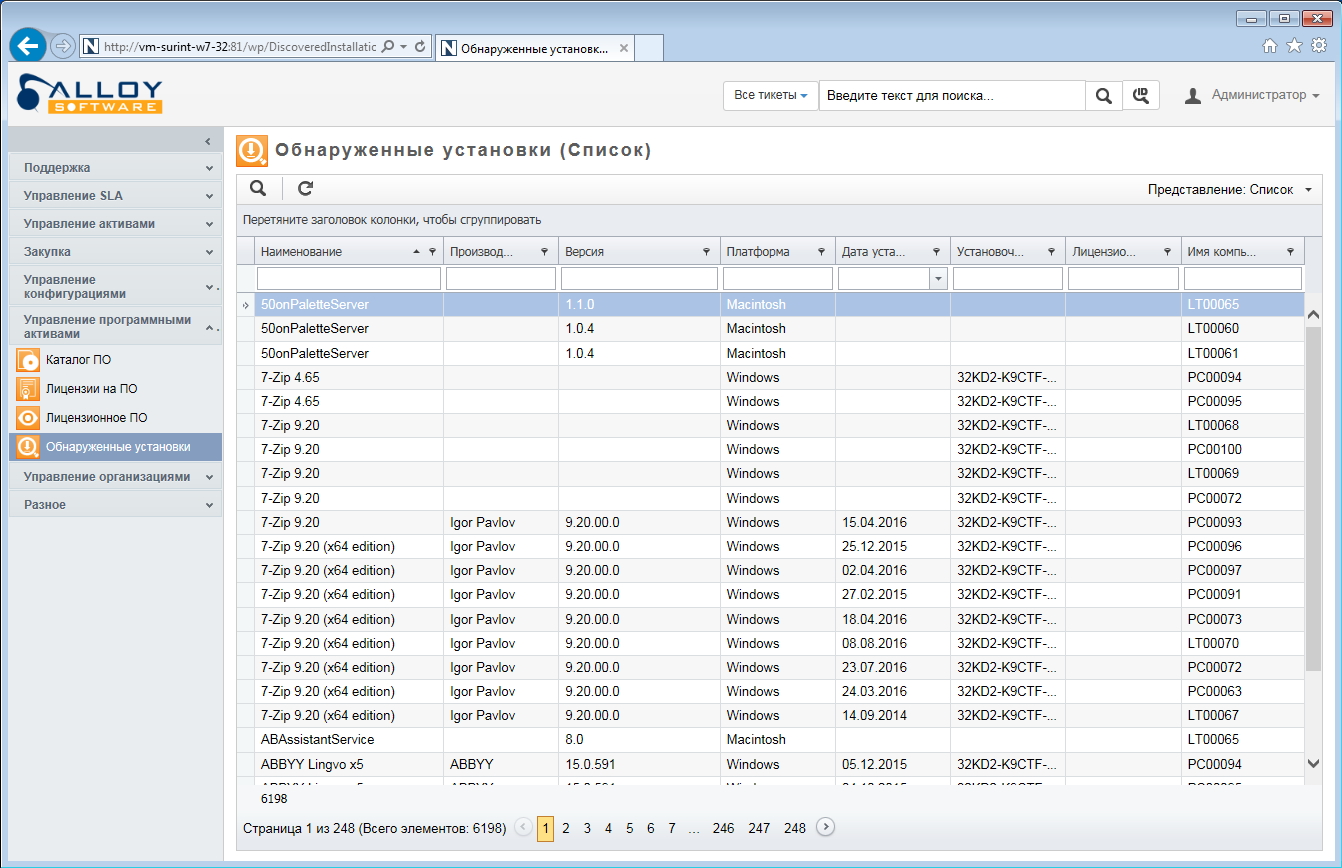

To support and maintain an asset inventory and audit, reducing the number of related routine operations in the work of the IT service. Inventory and audit - a tremendous stress not only for accounting and system administrator, it is also an interruption of the work process, and nerves, and great difficulties in working with equipment. The limit has already been reached when it is impossible to do everything with your hands, even in a relatively small company. It is much more convenient when all the equipment is collected in lists, you can view its attributes, analyze the condition, plan purchases and monitor the warehouse. You also won’t have to rewrite inventory numbers and re-stick labels - everything can be done using a mobile application that recognizes assets by a barcode and brings them into the system. Thus, the inventory takes place automatically with a minimum of manual operations.
Information on workstations, other equipment and networks is collected in the system interface in the configuration management module. Related documents created and uploaded by you are also available there (for example, financial or functional documentation, structural diagrams, service plans, etc.).
For the purposes of accounting, warehouse and financial accounting.Alloy Navigator 8.0 helps you track financial accounting information about the computer throughout the entire life cycle of the machine: standard depreciation is calculated, information about orders, warranty periods, rental cost (software or capacity), etc. is stored. This information is extremely important not only for the system administrator and technical service, but also for accounting. In general, in service and IT companies, ITSM systems are also in the service of financial workers - they are so interested in competent accounting that they even attend and take an active part in specialized conferences. Sometimes it seems to us that IT accountants understand the need for specialized software and monitoring almost earlier than administrators. And all because accounting is a tough business.

The same thing, but in the web interface of Alloy Navigator 8.0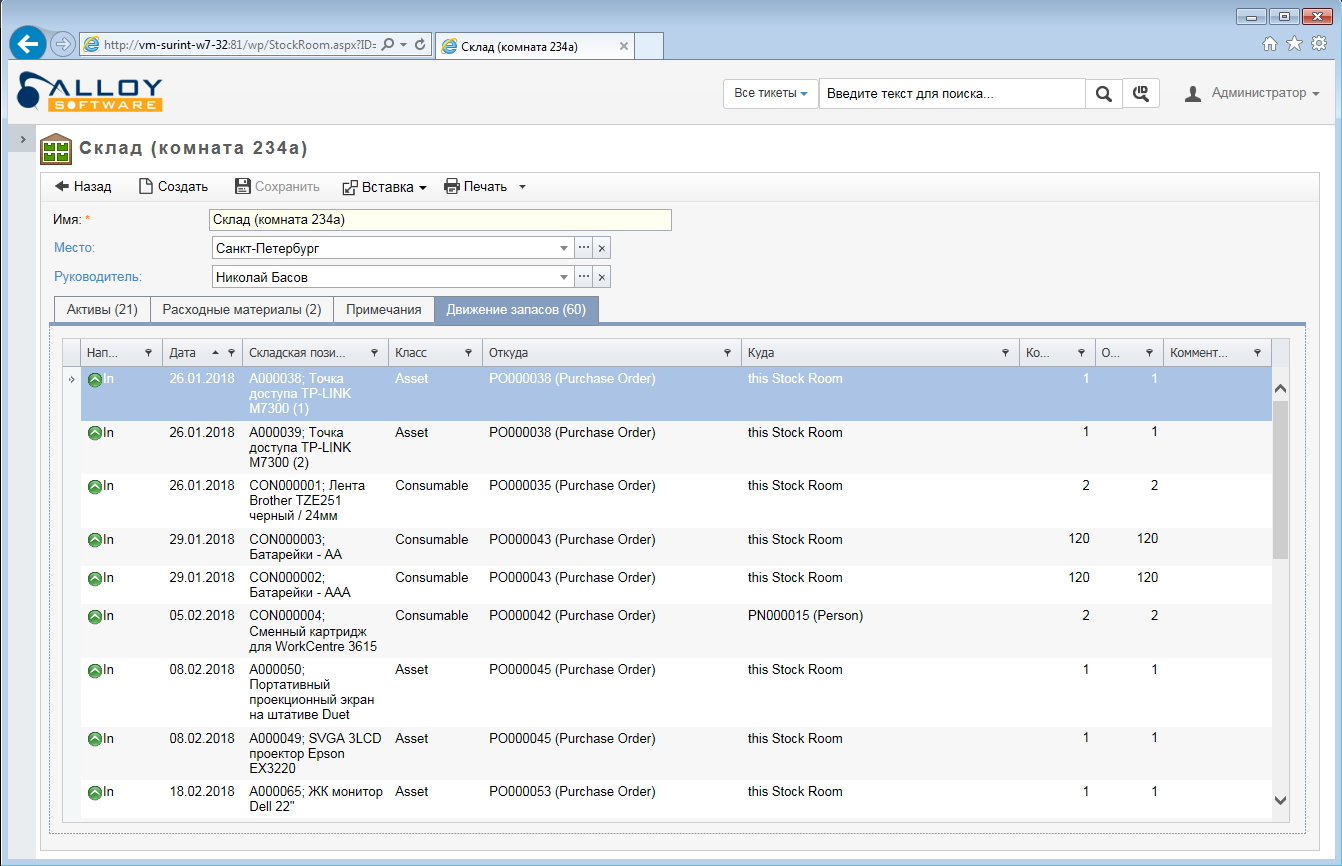

Another monetary problem that can be solved relatively successfully using ITSM systems is the calculation of KPI (KPIs - key performance indicators). Many copies were broken both at conferences, and in negotiation companies and vendors, and in comments on Habré in attempts to determine how to measure the work of the system administrator, how to evaluate unmeasurable factors, to arrange weights so that it really reflects the state of affairs, and does not give out monthly matrix for show. In Alloy Navigator 8.0, all work with KPI is done for you - indicators are generated in the form of 28 reports, all information is aggregated and easily accessible. The thing is small: take and use ready-made KPIs in the combinations that are necessary and significant for your company.

The same thing, but in the web interface of Alloy Navigator 8.0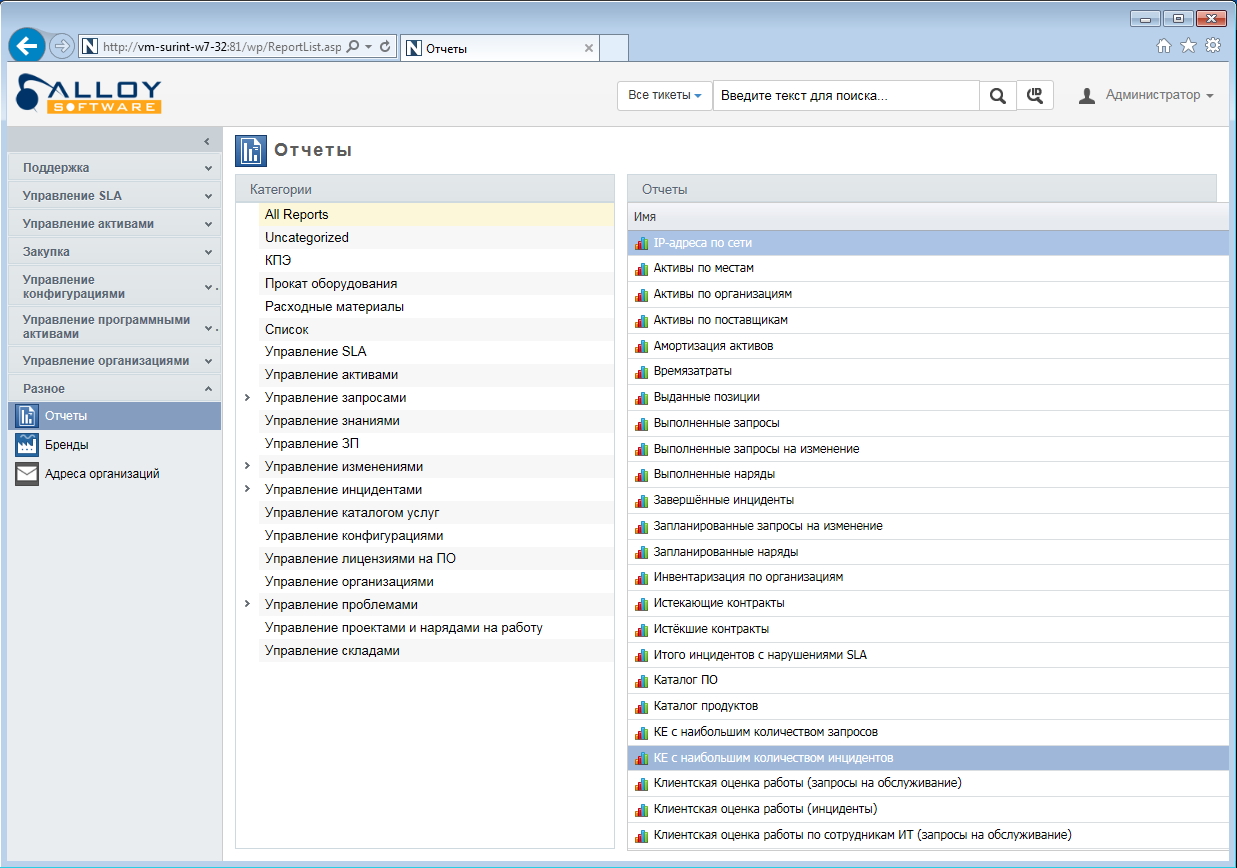

To plan the capacity of IT resources in the company.It is the users who believe that the task of the system administrator is to put the radiotelephone in the back pocket and rush to run to solve their problems, upload reports on the implementation or plan of the company in a month, and even be a “tyco programmer”. In fact, working with users, that is, essentially ensuring the smooth operation of business processes, is nothing but a part of the huge task of managing the complex set of all elements of the IT infrastructure. IT staff are required to control the appropriateness of technical resources, their location, operation and planning. And just planning is the main key to the effectiveness of all IT assets of the company. When working with the ITSM system, the administrator and the IT service can fairly accurately predict the timing of equipment replacement, decommissioning, etc. This means that equipment will change according to plan, and not be purchased as

By the way, special attention should be paid to working with supplies. For example, a printer lives in a company for a long time, rarely breaks, but cartridges run out often. The office can only get up because they forgot to order toner on time. So, the use of the ITSM system eliminates such situations - the administrator can control the replenishment of consumables. Everything is simple: we looked at the consumables in the warehouse, estimated how much you need for the smooth operation of the office, if necessary, click on the neighboring module and form an order for the supplier from the existing list.

The same thing, but in the web interface of Alloy Navigator 8.0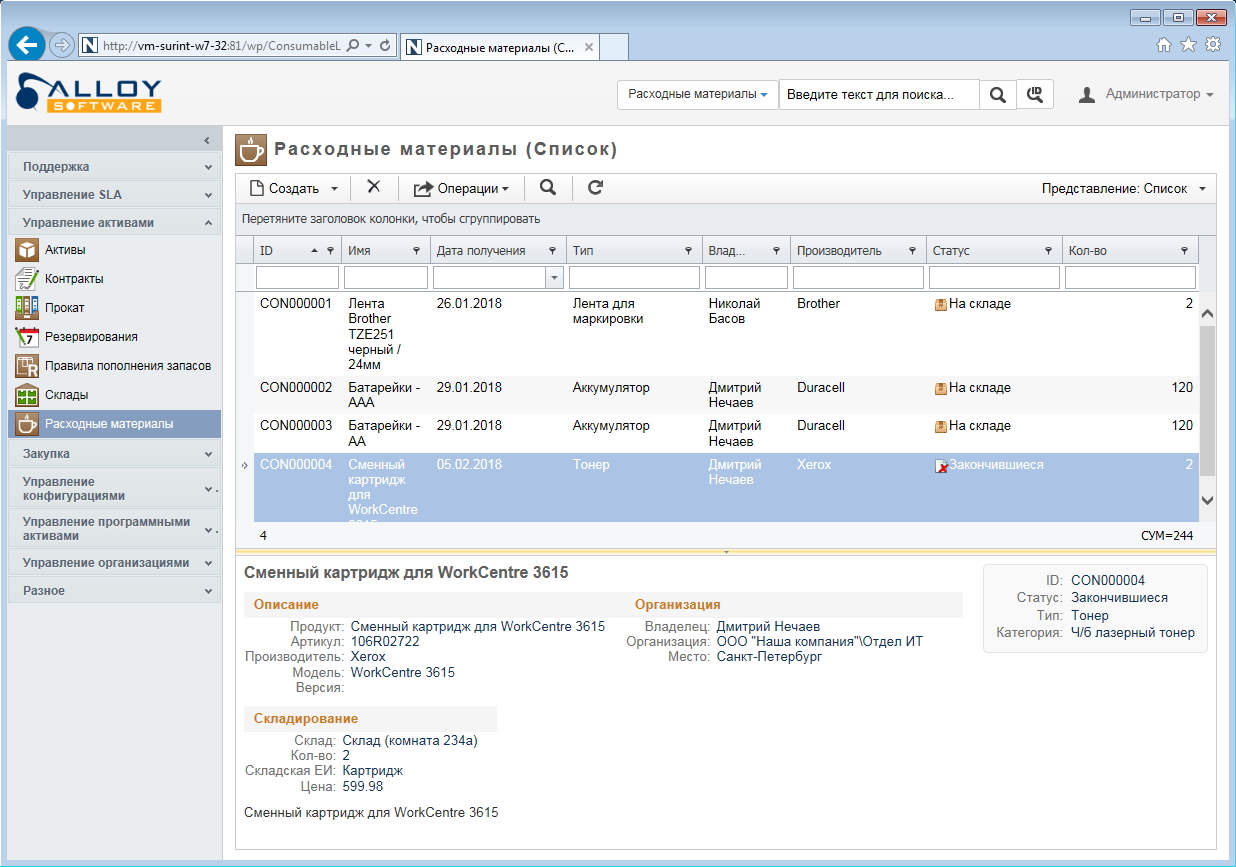

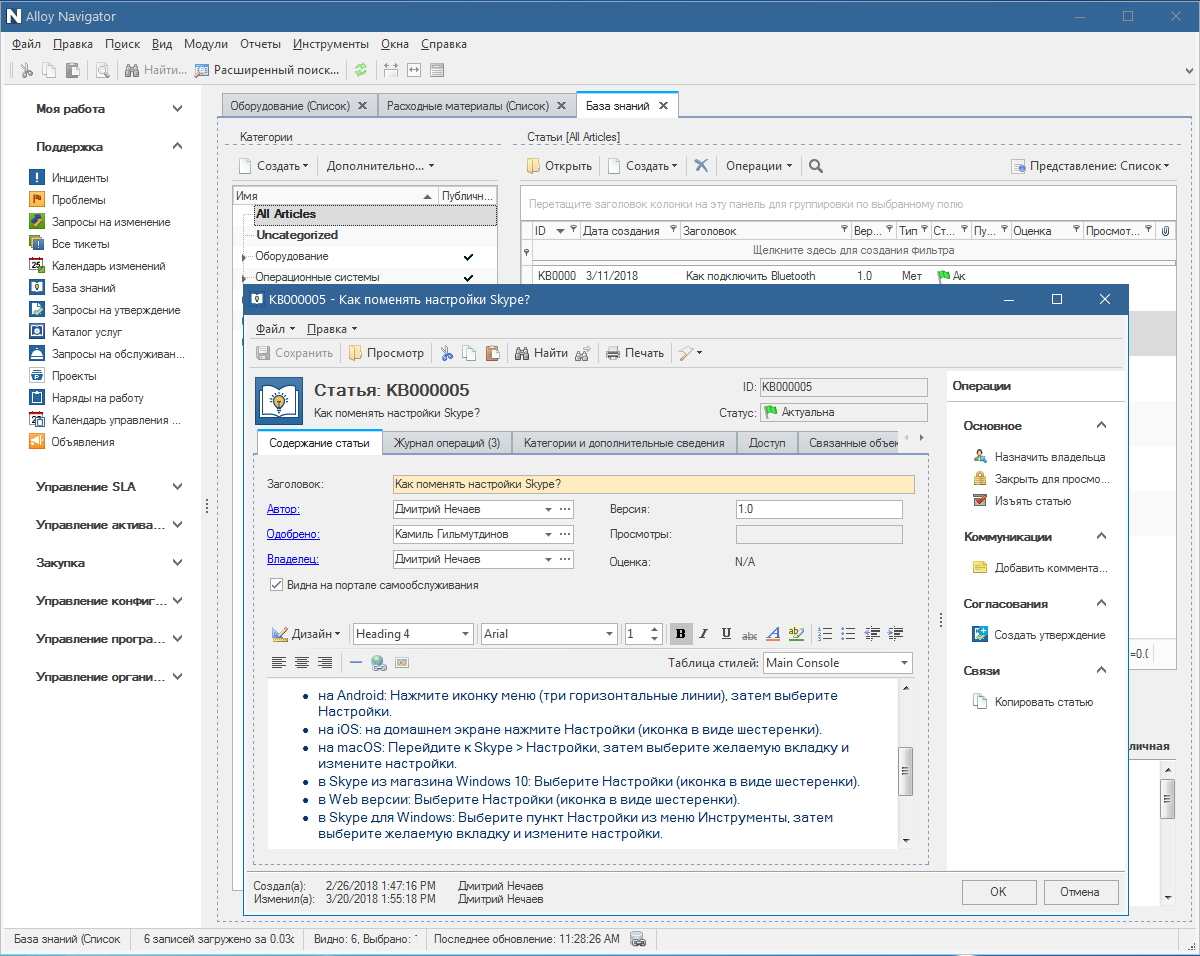
To ensure the security of the company's IT infrastructure. Here we are talking about information, economic and physical security. Alloy Navigator 8.0 is able to collect detailed information about the equipment that makes up the employee’s PC, settings, and installed software. Information is collected and stored in the form of snapshots (snapshots at a point in time) on a regular basis. This makes it possible to track all configuration changes. When is this important?
- Unauthorized changes to your PC configuration have occurred.
- Unwanted software has been installed.
Snapshots make it possible to do a retrospective analysis of the state of working machines, track the timeliness and adequacy of changes.
To organize a support service. The ITSM system is invaluable software for outsourcing technical support services, for system integrators, vendors, and for technical services within companies. The program becomes a point of contact between users and IT services, while relations are formally and strictly regulated, saving time.
The IT service staff themselves also gain valuable experience in the form of a knowledge base and thereby increase both the speed of response to user requests and the speed of adaptation and training of new employees, which is especially important in the context of a sharp scaling of the company (when merging, expanding, changing the organizational structure and etc.)

The same thing, but in the web interface of Alloy Navigator 8.0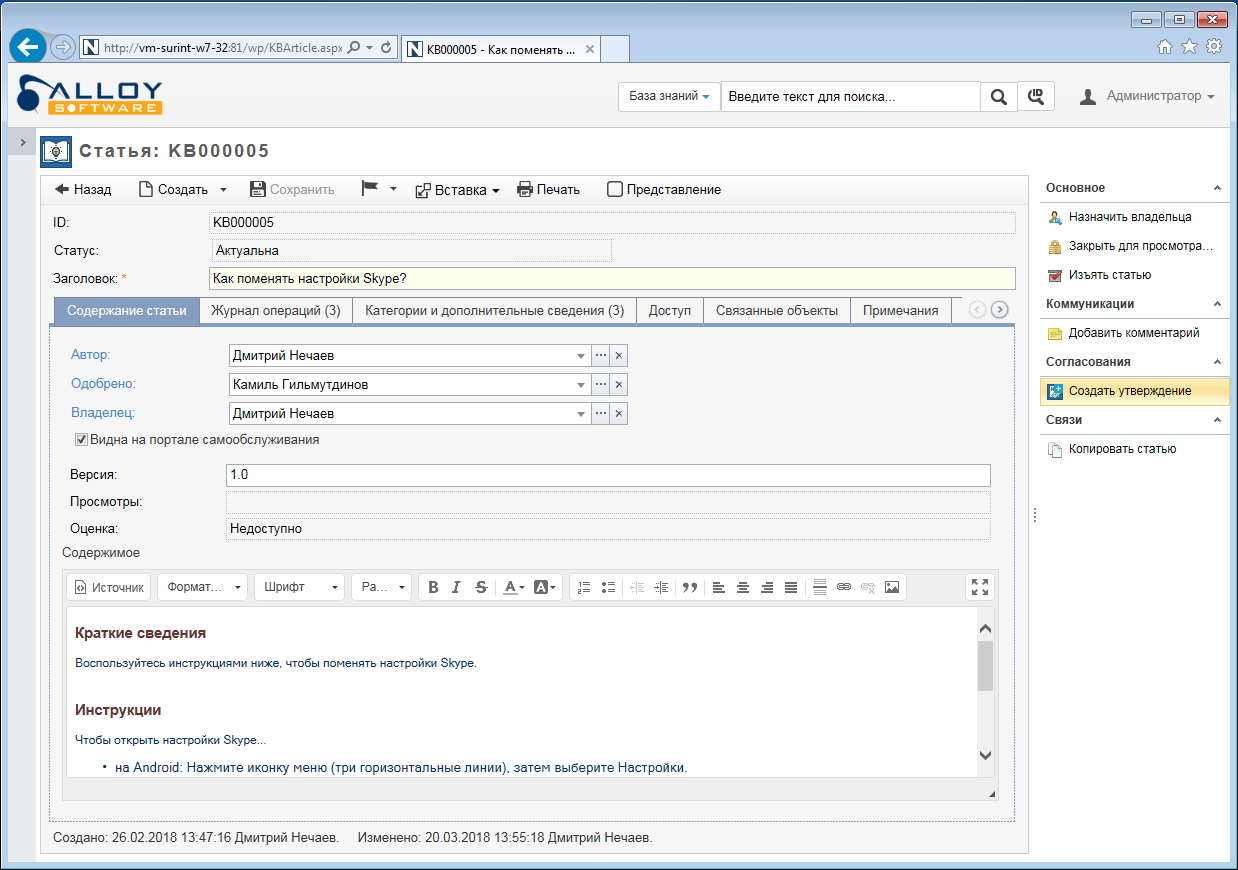

A good ITSM system is convenient to work with. For example, it has the desktop of a service engineer or system administrator (information panel), on which he can see tickets and a calendar, manage escalation and delegation of tasks.

The same thing, but in the web interface of Alloy Navigator 8.0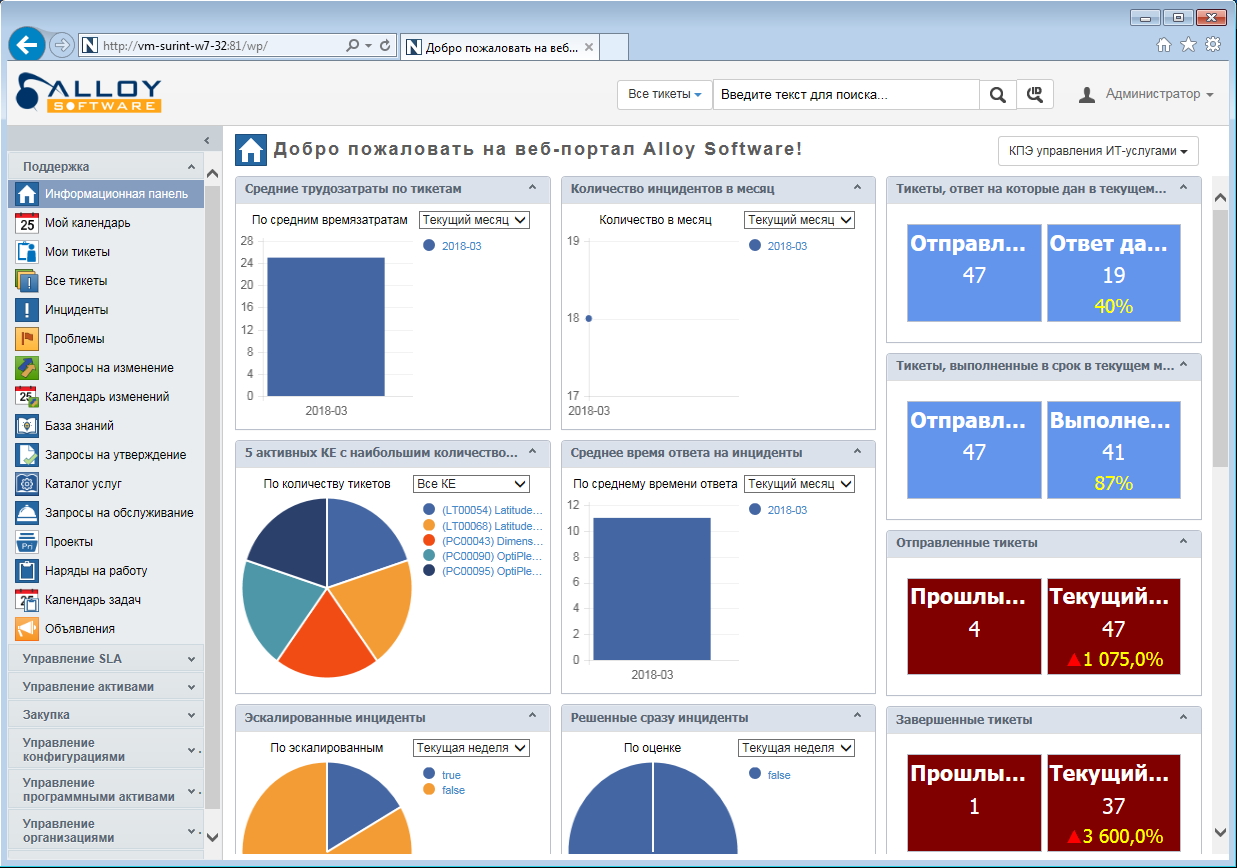

By the way, another useful feature of Alloy Navigator 8.0 is the recurring tickets, which guarantee the timely execution of regularly recurring actions (for example, the preparation of monthly reports). It is possible to bring matters into them and not to worry about someone forgetting to create a task in time for the next time, the system will notify those responsible. If you have been working in system administration for a long time, you will understand how cool it is and how many routine tasks you can reset to such cyclic tickets.

If you are too lazy to put a demo version of Alloy Navigator 8.0 (but in vain, there are a lot of interesting and narrowly professional ones, which you don’t have enough space to talk about on the blog), you can see a list of all available modules.
Available Modules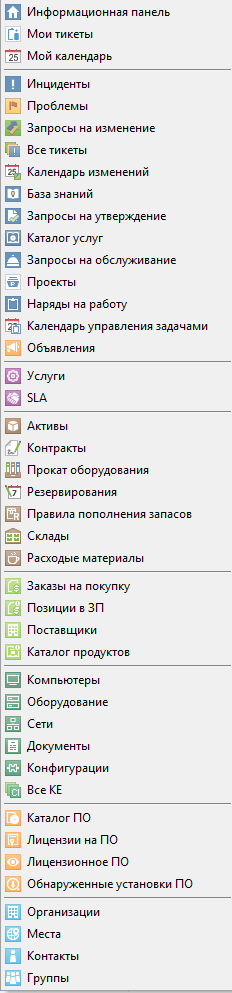

As you can see, the system includes all the key elements of a competent ITSM: configuration management, license management, SLA, warehouse and order formation, and most importantly, work with incidents and tickets.
Why has there been so much noise around ITSM systems?
If you open foreign publications about ITSM systems, you will find approximately the same words that the systems are designed to support the delivery of IT services to business users. That is, when 1C hangs up with the accountant, and the secretary has lost the Internet and they hysterically call the administrator’s mobile phone just gone for lunch, and he throws food and runs to the workplace, remembering a bit of profanity, this is the delivery of the service to a business user. In fact, we are so ironic, but only in part. The Russian reality is that in companies of any level, the relationship between the IT service and the rest of the employees is rather difficult. There are several reasons:
- The level of computer literacy of users often leaves much to be desired. Regardless of whether this generation is older or young people, many employees of non-technical services and departments from PC to “you”, some do not even understand the difference between a search engine and a browser, and a browser from the Internet. The reasons for this state of affairs deserve a separate study, but for company admins it’s just a given and a large amount of small work and contingencies that arose out of ignorance.
- Against the background of the previous factor, everyone considers himself an advanced user, some even know how to run the command line and regedit in it. Such employees complicate their lives several times, since it is they who can make changes to the system, but will not remember how they did it. In addition, it is in this group that those who are able to commit an offense and go unnoticed: merge commercial information, replace PC parts, change the configuration of the workplace for personal purposes. And believe me, replacing a memory card, a powerful video card installed for gaming during business hours or a VPN is the most harmless thing that can happen.
- Each employee has too many gadgets and devices, and all of these devices can interact with workstations and corporate networks. In the commercial service, it will be completely out of place to monitor the facts of the frequent connection of external drives and smartphones to a PC and the use of Wi-Fi for personal purposes.
- The employees have an enduring love for left work at work, as well as for various kinds of entertainment. This often requires some kind of software - so employees install pirated copies and cracked versions. The presence of such software can result in problems and fines for the company. Not to mention that the employee will spend the time paid by the employer on his needs.
- The vendor licensing policy has become too tight, checks by software manufacturers can lead to significant fines. Therefore, it is extremely important to monitor the installed software on each working machine.
- Users can start working with competitors and use corporate information for personal gain. Such situations arise more often and are especially acute in startups, where everyone knows everything and has the most trusted access to information and documents. Therefore, it is important to have the largest possible set of information: about connected devices, changeable configuration, and much more.
- Users are not able to adequately describe the problem that has arisen if they do not have guidelines (for example, fields to fill out, application forms, etc.) This is a problem that kills the time and effort of the system administrator: you need to find out what happened, what the breakdown is, due to confusing explanations go to the employee’s workplace. And if it's not three rooms, but thirteen floors or three buildings? The ticket establishment system in this case is simply irreplaceable; it helps to present the information as concisely and in essence as possible.
Of course, one system ( Alloy Navigator 8.0 ) cannot fully cope with these problems , we need help from detection and monitoring systems such as Alloy Discovery, antiviruses, CRM systems, well-thought-out methods of preventing violations at the operating system level, and competent use of group policies. But even without an ITSM system, the problems cannot be completely resolved.
Recently, many topics related to ITSM have appeared on Habré in the key to information security. Nevertheless, we believe that you should not limit yourself to protection, it is important to work with prevention, that is, use ITSM as a strategy for daily management of IT infrastructure. If you think that the costs of monitoring, accounting and automation are too high, you are mistaken - the system and the ecosystem created around it are paid off by reducing costs associated with service and incident response times, increasing the efficiency of resources and, of course, by preventing downtime in work.
The challenges that cyber reality sends to companies are reminiscent of the flu virus. As soon as a remedy for one strain is found and the world exhales with relief, a new, not yet fully studied mutation appears. And again, a threat to all of humanity. So it is with the IT infrastructure: neither external agents nor internal employees will let you get bored. For such a fight, you really need a cold head, cool skills and long arms.

