FastTrack Training. "Network Basics." "Security basics". Eddie Martin December 2012
- Tutorial
About a year ago, I noticed an interesting and fascinating series of lectures by Eddie Martin, which is incredibly intelligible, thanks to its history and real life examples, as well as colossal experience in teaching, which allows us to gain an understanding of rather complex technologies.

We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the field of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Essentials”
25: “Cisco Security Software Products”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here's the twenty-fourth of them.
People can go to jail if network security is not ensured. Security is one of the most important issues in a conversation with senior management companies. The integrity of a large volume of information for customers today is of paramount importance.
In 2003, a survey was conducted on why network security is important to people. In first place was concern for the indestructibility of the brand. This task still remains important, and I think today this reason takes both first and second place in importance. Unfortunately, the third reason was such a reason: "We want to ensure network security, because we are obliged to do this." Because customers could not protect their network until this requirement became a prerequisite.

Security is a very important condition, because any progress can stop if the user is at risk of losing his data or compromising his business.
There is a huge scope for the provision of security services. Because in one place one company may have a secure network, and another may try to crack it to make sure that the competitor has strong protection. It is so important that a lot of money is being invested in this area.
Cisco certainly has security. Customers do not want to integrate anything into the network except routers and switches, so Cisco has always released only secure equipment. However, security conditions must vary depending on the nature of the hacker attacks.
Once, at the beginning of our activity, we called the client and asked if his network was secure, and he answered: “Yes, of course, because I use your PIX firewall.” And we said: "Then you are protected, everything is fine, thank you for being with us!" But times have changed, and the requirements applied to security have changed.
Where do you think the threats of network hacking come from? That's right, from anywhere, and more often they come from the inside of the network than from the outside. Closest to security is the IT area. Cisco has a whole portfolio of network security solutions, and they are designed to be used in several different situations.
Consider what access security is. It is like a locked door. To go inside, you need a username and password. Moreover, passwords must be periodically changed, and the password should not be the name of your child, and so on - there are rules for how a secure password should correspond. Secure access means not only that you were able to connect to the network, but also that you can use network equipment.
We want to give customers the opportunity to bring their own device to work on the network, but we also want to ensure their safety. We want guests to be able to enter our network, but that it is safe for us.
To do this, we must provide a special level of access - guest access, and give a special username and password for the specific location of the user, that is, for an external network client. We should not only have the opportunity to do this, but also the ability to regulate and control such a process.
When I worked at Blue Cross & Blue Shield, we had a guy who served the mainframe, the main fault-tolerant server. He adhered to the rule not to enter the server room with anything but a cup of coffee, because everything else could threaten the security of the server. Security people are always against giving unrestricted access; they regulate access rights to protect us and our work.
We must make sure that our customers focus on this problem and do not say that they need to be given access to anyone to do their job, communicate, pay bills, and we do not give them such an opportunity. We must adhere to a specific policy in this matter, because users do not adhere to a single security policy. We must teach them that security is part of the business process.
I can give many examples of customers' attitude to security 3-5 years ago and now - it has seriously changed.
How fast is a security risk? It exists every second, every minute and every day.
We collect information and need it to be distributed very, very quickly if necessary.
Cisco has an SIO Intelligent Security Organization. She monitors all threats to network security, hacking attempts, viruses and studies the information about threats that comes from our customers and our units. She publishes any information about new threats on the network so that all members of the network know about it. It posts data on the vulnerability of the programs that we use, about new viruses and other dangerous things.
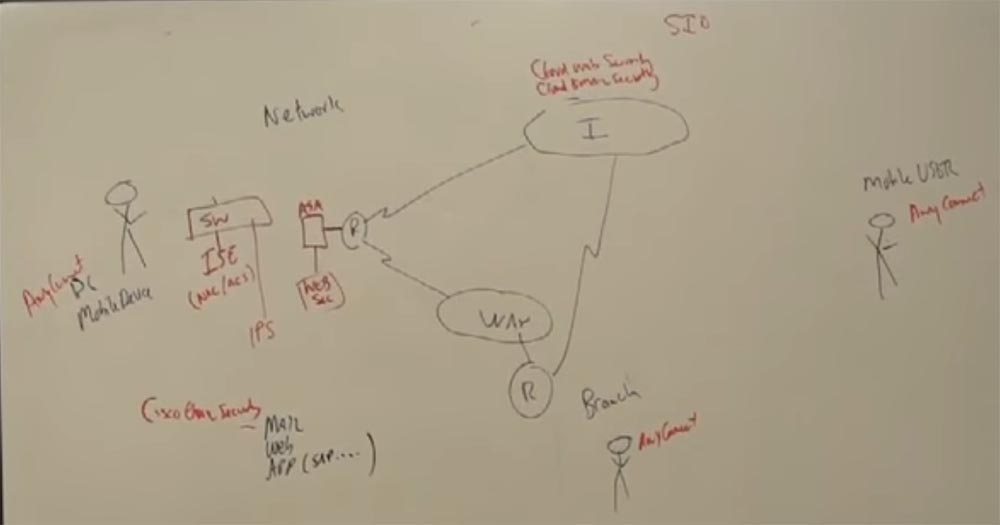
And if we are attacked by malefactors, we will report this to the SIO and it will repel the attack. If a new threat arises to the application that you use, for example SIP, then the security service will immediately “push” it out of the network and send it to your IPS, the network intrusion prevention system, which will block suspicious data.
If you remember, on Wednesday we talked about the session level when we configure its operation and the devices associated with it. So, when the SIO detects a threat at this level, it drops it in IPS. That is, I protect myself from the troubles that occur within the network. This is the service that we must provide the client so that he can protect himself at any level of interaction with the network.
What does this mean? That we are more and more delving into the cloud. This is the area where we accumulate information and from where we distribute it throughout the network through our products. Therefore, you need to constantly interact with SIO to be aware of new threats and vulnerabilities for our devices. Cisco describes all this and distributes such information to everyone.
So, the first thing we need to do for a new client is to implement the 802.IX protocol. This protocol defines the main components and algorithms used in Ethernet / IEEE 802.3 networks to limit the unauthorized connection of a subscriber to network devices using the authentication procedure. It contains a list of subscribers and devices that can be allowed into the network. It supports security certificates on your phone and indicates which clients it is safe to work with and which not. This protocol provides authentication of devices and people.
We call this the administrative control of the NAC network. However, if we pay attention to your PC, we will see that most of the vulnerabilities are in your own head. We will see that you do not use antivirus software or update it, that you use applications without security patches.

So, to prevent this from happening, Cisco does this for you by using the 802.IX protocol. It will not allow the application to run if it threatens network security. Some trade-related customers said that Cisco was making things complicated again. However, two years passed, they looked at our authentication system and realized that we were right. It is enough to have a username and password to protect the network and your business from a lot of troubles. We have given customers the opportunity to use the devices and applications that they want to use safely. And if at first people dismissed our demands, now they agree to fulfill them.
So, the basis of security is first of all access control. The switch contains NAC and ACS - access control server. Authentication data - our username and password are sent to ACS. Then NAC decides to give us a certain level of access. We have integrated the NAC / ACS functions in the ISE platform - Identity Services Engine. Depending on the size of your network and what you want to do, it can be placed in one “box”, or maybe six.
This solution is used to manage identification and access control processes. Thanks to it, clients in real time can receive from the networks, from users and devices the contextual information necessary for making proactive decisions on providing access based on a single access policy.
This platform also provides guest access. For example, you give your guest an e-mail and say you want to give him access to such and such network resources for such and such a time. You give it authentication on the guest network. This way you can really control access. If I can open the door, then I get into the network. If I have a key, I open the door.
ISE gives you the ability to configure guest access settings, such as visit time, create a guest profile, etc. Customers are reluctant to do this because they think: “How do I configure this large matrix? How to classify all your employees and create a table of access levels? I probably need an Oracle database for access control for this. ” Etc. This is really a problem for us, we must ensure that the client stops thinking about it and convinces him that he is obliged to do this if he wants to realize the full potential of his organization. But they really resist such innovations.
The PIX firewall is no longer in use, we now have the Cisco ASA product, the Adaptive Security Appliance. It provides multitasking service. First of all, these are the capabilities of the firewall. The new version of the firewall provides a bandwidth of 40 Gb / s, it is a very powerful defender. The second thing that the ASA provides is a VPN. All ASA devices have the ability to create a VPN. You can connect 2000 users to such a network. The third component is IPS support, that is, the ASA contains a protection module against unauthorized access.
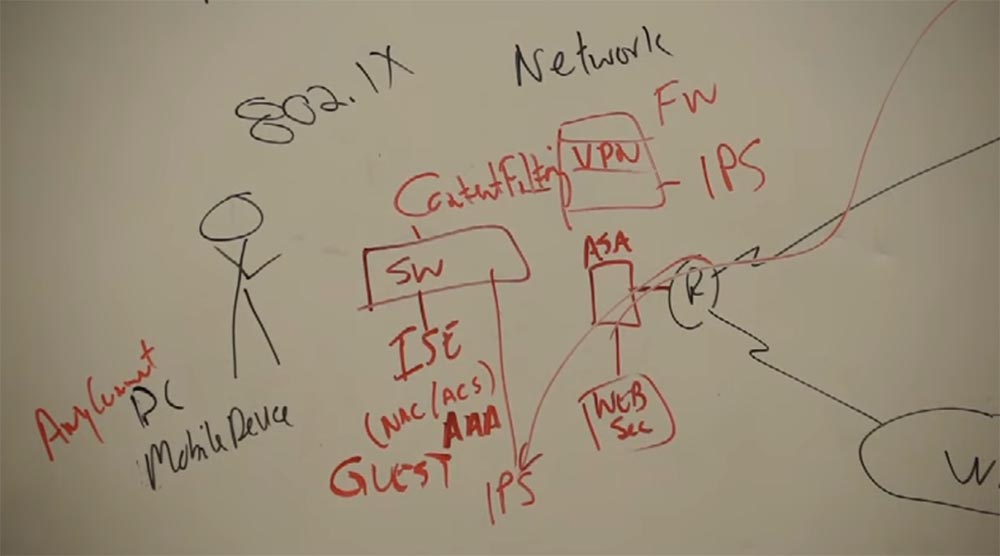
This is a “three in one” solution combined in one “box”. Another feature the ASA has is Content Filtering. You can filter the Internet content that your employees use. The rules by which this device works can be changed if necessary. This is what provides the Internet path.
Suppose the user drawn on the right wants to go to the Internet page. Can I limit it to this? Our user can access not only the Cisco network, but also any third-party Internet resource. Let's look at the reason why a client might want to restrict your access. The first is labor productivity; you should not be distracted at work with extraneous things. The responsibility follows, because you can catch the virus by visiting third-party sites.
I have a friend - a professional computer engineer. He knows everything about it, he can fix everything, cure you of viruses. So, he told me that he caught a virus with porn ads. And when I asked how he had managed, he replied that this infection had come to him from the website of one bank.
We cannot just control other people. It's like persuading them to drive at a speed of 45 miles per hour, but they will still drive at a speed of 60, although this is against the law. But we can forbid them to force it by blocking access to certain sites. We have a WEB-security module that checks sites for threats. We may allow you to visit your Facebook page during business hours, but first we will check it. This solution, WEB Sec, came to us from a company called Ironport, which we acquired. Therefore, the ASA is really a very good box.
If you do not want to support this solution, it is possible to deploy Ironport in the cloud using a cloud-based security solution. You can make sure that you work in the Cloud all the time you are on the Internet, but this Cloud also has rules that you must adhere to. That is, you choose your client policy, ensuring security in one way or another.
If we put SIO on our cloud Internet, we can also filter out content, checking its vulnerability, susceptibility to attacks, and so on. We have many different possibilities. And we must implement them, because customers are not able to do this on their own, for them it is too difficult.
Email security is also very important. And this will help Cisco Ironport - perhaps this is the best security solution that the company has ever developed. I will draw a mail server with a green marker and Ironport IP below it. Before you get to this server, you go through IP and in the same way sent mail goes through it. Suppose someone from the external Internet sends a letter.
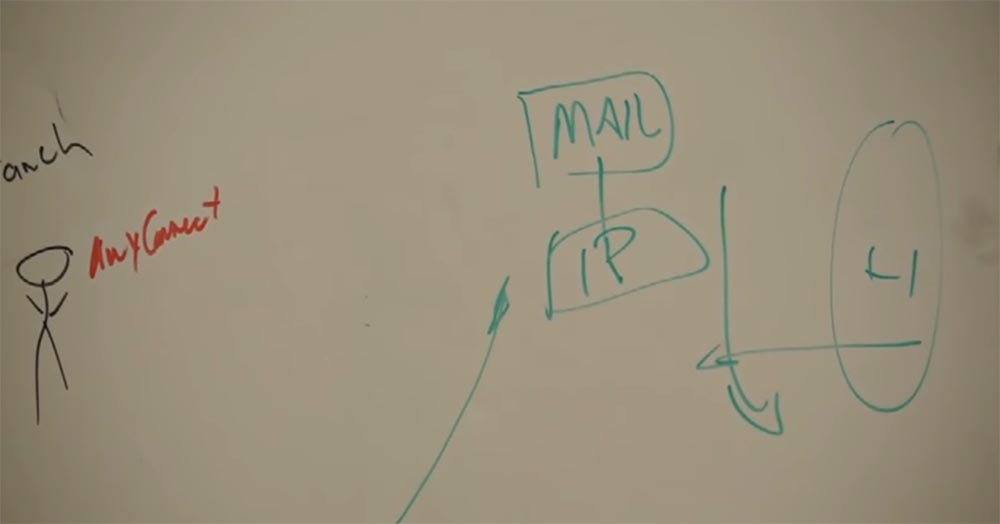
First of all, Ironport checks where this letter came from and classifies it on a scale from -10 to +10 in accordance with the SIO classification. And if this letter receives a rating of "- 4", it will never reach our mail server. If the letter receives a rating of "+2", its contacts are checked. If they are not known by the SIO, the letter is also blocked. Next, the attachment contained in the letter is checked. If this is an executable file with the extension .exe, you will not receive this letter. Even if the sender changes the file extension from .exe to .jpg, it still does not deceive our Ironport and SIO, they will perfectly understand that the attachment is not a picture, but a program. Because they classify any investment.
And again, you can place this solution inside the network or outside the network in a cloud service. You can even place your mail server inside the network, and receive mail through the Cloud. This is a hybrid version of the mail service using 2 different technologies. You can both send and receive mail this way.
Regarding IPS, I’ll say that we can study all new problems and update the network in accordance with new security requirements. Suppose your new SIP application contains a vulnerability, and we know how important these applications are for the business process. So, within a few minutes in our network you can find a solution that will protect it from threats.
Many customers are overwhelmed by the capabilities Cisco presents to them in the area of security. Particularly amazing to them is the ability to use cloud services. If the user is located on the network, he can receive security updates from the SIO at any time.
I showed you the SIO web page - this is our division, the office of Cisco. Ironport checks 40% of all mail, which is composed of letters arriving to us via the Internet. He sees all the security problems that arise every day, and is constantly expanding his capabilities to counter threats.
In branch networks, we have the same capabilities as in headquarters networks. There is a firewall in the router that is associated with the branch. And it also interacts with WEB SEC. If we need to block all external Internet traffic, we quickly configure filters and block it.
If some external user is looking for contact with us - this little man on the right - and in this case we are talking about working together and communicating with us from our home, we direct him through cloud I and through ASA to our person at headquarters apartment. And all Internet traffic that comes to us from the outside follows the same rules as internal traffic.
With whom should we discuss security issues, with which customer representative? With an officer or company security officer? Of course not! Consider it just a guy who stands at the door and checks everyone at the entrance. CIO, IT Director? Perhaps, but completely different issues need to be discussed with him.
That's right, you need to talk with the CEO! It is the CEO who determines the strategy of the company, and not the guy with the badge and gun.

Therefore, we say that security issues are very important for the top management of the company that runs the entire business. Only these people have the right to say yes or no to our proposal. You need to tell them how important security policies are, how the BYOD feature (“bring your own device to work”) can make a difference in their lives, how security applications can be sent to the Cloud, and how we do it. Cloud technology is extremely expanding business opportunities. And I think customers will agree that this is a great solution.
And if you understand your business, it will not be difficult for you to explain this to the client in plain language. Everything that we do sounds complicated to the client. For example, 19 steps of device authentication. Therefore, it is not necessary to explain such subtleties to the client. He needs to tell how our solutions will help in organizing the network, and how they will ensure the safe development of the business.
Continuation:
FastTrack Training. "Network Basics." "Cisco Security Products." Eddie Martin December, 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the field of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Essentials”
25: “Cisco Security Software Products”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here's the twenty-fourth of them.
FastTrack Training. "Network Basics." "Security basics". Eddie Martin December 2012
People can go to jail if network security is not ensured. Security is one of the most important issues in a conversation with senior management companies. The integrity of a large volume of information for customers today is of paramount importance.
In 2003, a survey was conducted on why network security is important to people. In first place was concern for the indestructibility of the brand. This task still remains important, and I think today this reason takes both first and second place in importance. Unfortunately, the third reason was such a reason: "We want to ensure network security, because we are obliged to do this." Because customers could not protect their network until this requirement became a prerequisite.

Security is a very important condition, because any progress can stop if the user is at risk of losing his data or compromising his business.
There is a huge scope for the provision of security services. Because in one place one company may have a secure network, and another may try to crack it to make sure that the competitor has strong protection. It is so important that a lot of money is being invested in this area.
Cisco certainly has security. Customers do not want to integrate anything into the network except routers and switches, so Cisco has always released only secure equipment. However, security conditions must vary depending on the nature of the hacker attacks.
Once, at the beginning of our activity, we called the client and asked if his network was secure, and he answered: “Yes, of course, because I use your PIX firewall.” And we said: "Then you are protected, everything is fine, thank you for being with us!" But times have changed, and the requirements applied to security have changed.
Where do you think the threats of network hacking come from? That's right, from anywhere, and more often they come from the inside of the network than from the outside. Closest to security is the IT area. Cisco has a whole portfolio of network security solutions, and they are designed to be used in several different situations.
Consider what access security is. It is like a locked door. To go inside, you need a username and password. Moreover, passwords must be periodically changed, and the password should not be the name of your child, and so on - there are rules for how a secure password should correspond. Secure access means not only that you were able to connect to the network, but also that you can use network equipment.
We want to give customers the opportunity to bring their own device to work on the network, but we also want to ensure their safety. We want guests to be able to enter our network, but that it is safe for us.
To do this, we must provide a special level of access - guest access, and give a special username and password for the specific location of the user, that is, for an external network client. We should not only have the opportunity to do this, but also the ability to regulate and control such a process.
When I worked at Blue Cross & Blue Shield, we had a guy who served the mainframe, the main fault-tolerant server. He adhered to the rule not to enter the server room with anything but a cup of coffee, because everything else could threaten the security of the server. Security people are always against giving unrestricted access; they regulate access rights to protect us and our work.
We must make sure that our customers focus on this problem and do not say that they need to be given access to anyone to do their job, communicate, pay bills, and we do not give them such an opportunity. We must adhere to a specific policy in this matter, because users do not adhere to a single security policy. We must teach them that security is part of the business process.
I can give many examples of customers' attitude to security 3-5 years ago and now - it has seriously changed.
How fast is a security risk? It exists every second, every minute and every day.
We collect information and need it to be distributed very, very quickly if necessary.
Cisco has an SIO Intelligent Security Organization. She monitors all threats to network security, hacking attempts, viruses and studies the information about threats that comes from our customers and our units. She publishes any information about new threats on the network so that all members of the network know about it. It posts data on the vulnerability of the programs that we use, about new viruses and other dangerous things.

And if we are attacked by malefactors, we will report this to the SIO and it will repel the attack. If a new threat arises to the application that you use, for example SIP, then the security service will immediately “push” it out of the network and send it to your IPS, the network intrusion prevention system, which will block suspicious data.
If you remember, on Wednesday we talked about the session level when we configure its operation and the devices associated with it. So, when the SIO detects a threat at this level, it drops it in IPS. That is, I protect myself from the troubles that occur within the network. This is the service that we must provide the client so that he can protect himself at any level of interaction with the network.
What does this mean? That we are more and more delving into the cloud. This is the area where we accumulate information and from where we distribute it throughout the network through our products. Therefore, you need to constantly interact with SIO to be aware of new threats and vulnerabilities for our devices. Cisco describes all this and distributes such information to everyone.
So, the first thing we need to do for a new client is to implement the 802.IX protocol. This protocol defines the main components and algorithms used in Ethernet / IEEE 802.3 networks to limit the unauthorized connection of a subscriber to network devices using the authentication procedure. It contains a list of subscribers and devices that can be allowed into the network. It supports security certificates on your phone and indicates which clients it is safe to work with and which not. This protocol provides authentication of devices and people.
We call this the administrative control of the NAC network. However, if we pay attention to your PC, we will see that most of the vulnerabilities are in your own head. We will see that you do not use antivirus software or update it, that you use applications without security patches.

So, to prevent this from happening, Cisco does this for you by using the 802.IX protocol. It will not allow the application to run if it threatens network security. Some trade-related customers said that Cisco was making things complicated again. However, two years passed, they looked at our authentication system and realized that we were right. It is enough to have a username and password to protect the network and your business from a lot of troubles. We have given customers the opportunity to use the devices and applications that they want to use safely. And if at first people dismissed our demands, now they agree to fulfill them.
So, the basis of security is first of all access control. The switch contains NAC and ACS - access control server. Authentication data - our username and password are sent to ACS. Then NAC decides to give us a certain level of access. We have integrated the NAC / ACS functions in the ISE platform - Identity Services Engine. Depending on the size of your network and what you want to do, it can be placed in one “box”, or maybe six.
This solution is used to manage identification and access control processes. Thanks to it, clients in real time can receive from the networks, from users and devices the contextual information necessary for making proactive decisions on providing access based on a single access policy.
This platform also provides guest access. For example, you give your guest an e-mail and say you want to give him access to such and such network resources for such and such a time. You give it authentication on the guest network. This way you can really control access. If I can open the door, then I get into the network. If I have a key, I open the door.
ISE gives you the ability to configure guest access settings, such as visit time, create a guest profile, etc. Customers are reluctant to do this because they think: “How do I configure this large matrix? How to classify all your employees and create a table of access levels? I probably need an Oracle database for access control for this. ” Etc. This is really a problem for us, we must ensure that the client stops thinking about it and convinces him that he is obliged to do this if he wants to realize the full potential of his organization. But they really resist such innovations.
The PIX firewall is no longer in use, we now have the Cisco ASA product, the Adaptive Security Appliance. It provides multitasking service. First of all, these are the capabilities of the firewall. The new version of the firewall provides a bandwidth of 40 Gb / s, it is a very powerful defender. The second thing that the ASA provides is a VPN. All ASA devices have the ability to create a VPN. You can connect 2000 users to such a network. The third component is IPS support, that is, the ASA contains a protection module against unauthorized access.

This is a “three in one” solution combined in one “box”. Another feature the ASA has is Content Filtering. You can filter the Internet content that your employees use. The rules by which this device works can be changed if necessary. This is what provides the Internet path.
Suppose the user drawn on the right wants to go to the Internet page. Can I limit it to this? Our user can access not only the Cisco network, but also any third-party Internet resource. Let's look at the reason why a client might want to restrict your access. The first is labor productivity; you should not be distracted at work with extraneous things. The responsibility follows, because you can catch the virus by visiting third-party sites.
I have a friend - a professional computer engineer. He knows everything about it, he can fix everything, cure you of viruses. So, he told me that he caught a virus with porn ads. And when I asked how he had managed, he replied that this infection had come to him from the website of one bank.
We cannot just control other people. It's like persuading them to drive at a speed of 45 miles per hour, but they will still drive at a speed of 60, although this is against the law. But we can forbid them to force it by blocking access to certain sites. We have a WEB-security module that checks sites for threats. We may allow you to visit your Facebook page during business hours, but first we will check it. This solution, WEB Sec, came to us from a company called Ironport, which we acquired. Therefore, the ASA is really a very good box.
If you do not want to support this solution, it is possible to deploy Ironport in the cloud using a cloud-based security solution. You can make sure that you work in the Cloud all the time you are on the Internet, but this Cloud also has rules that you must adhere to. That is, you choose your client policy, ensuring security in one way or another.
If we put SIO on our cloud Internet, we can also filter out content, checking its vulnerability, susceptibility to attacks, and so on. We have many different possibilities. And we must implement them, because customers are not able to do this on their own, for them it is too difficult.
Email security is also very important. And this will help Cisco Ironport - perhaps this is the best security solution that the company has ever developed. I will draw a mail server with a green marker and Ironport IP below it. Before you get to this server, you go through IP and in the same way sent mail goes through it. Suppose someone from the external Internet sends a letter.
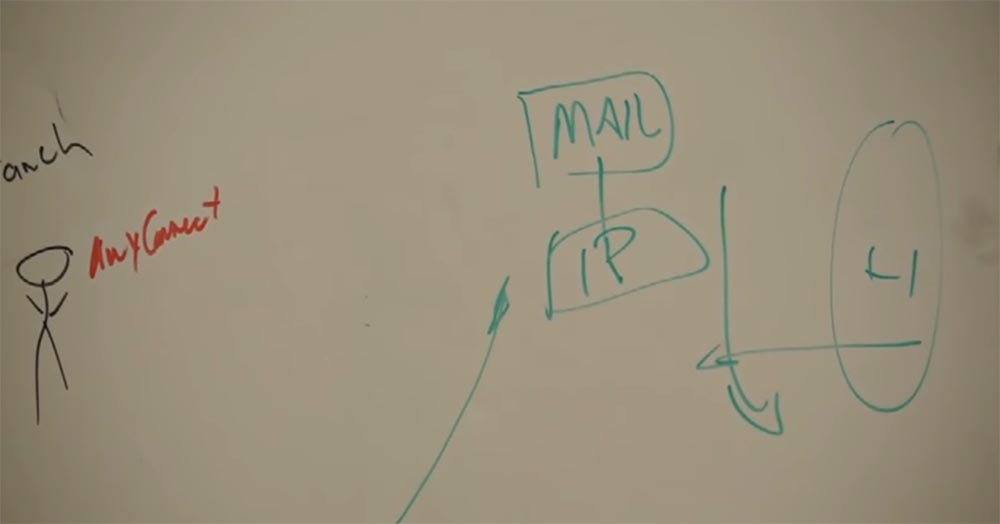
First of all, Ironport checks where this letter came from and classifies it on a scale from -10 to +10 in accordance with the SIO classification. And if this letter receives a rating of "- 4", it will never reach our mail server. If the letter receives a rating of "+2", its contacts are checked. If they are not known by the SIO, the letter is also blocked. Next, the attachment contained in the letter is checked. If this is an executable file with the extension .exe, you will not receive this letter. Even if the sender changes the file extension from .exe to .jpg, it still does not deceive our Ironport and SIO, they will perfectly understand that the attachment is not a picture, but a program. Because they classify any investment.
And again, you can place this solution inside the network or outside the network in a cloud service. You can even place your mail server inside the network, and receive mail through the Cloud. This is a hybrid version of the mail service using 2 different technologies. You can both send and receive mail this way.
Regarding IPS, I’ll say that we can study all new problems and update the network in accordance with new security requirements. Suppose your new SIP application contains a vulnerability, and we know how important these applications are for the business process. So, within a few minutes in our network you can find a solution that will protect it from threats.
Many customers are overwhelmed by the capabilities Cisco presents to them in the area of security. Particularly amazing to them is the ability to use cloud services. If the user is located on the network, he can receive security updates from the SIO at any time.
I showed you the SIO web page - this is our division, the office of Cisco. Ironport checks 40% of all mail, which is composed of letters arriving to us via the Internet. He sees all the security problems that arise every day, and is constantly expanding his capabilities to counter threats.
In branch networks, we have the same capabilities as in headquarters networks. There is a firewall in the router that is associated with the branch. And it also interacts with WEB SEC. If we need to block all external Internet traffic, we quickly configure filters and block it.
If some external user is looking for contact with us - this little man on the right - and in this case we are talking about working together and communicating with us from our home, we direct him through cloud I and through ASA to our person at headquarters apartment. And all Internet traffic that comes to us from the outside follows the same rules as internal traffic.
With whom should we discuss security issues, with which customer representative? With an officer or company security officer? Of course not! Consider it just a guy who stands at the door and checks everyone at the entrance. CIO, IT Director? Perhaps, but completely different issues need to be discussed with him.
That's right, you need to talk with the CEO! It is the CEO who determines the strategy of the company, and not the guy with the badge and gun.

Therefore, we say that security issues are very important for the top management of the company that runs the entire business. Only these people have the right to say yes or no to our proposal. You need to tell them how important security policies are, how the BYOD feature (“bring your own device to work”) can make a difference in their lives, how security applications can be sent to the Cloud, and how we do it. Cloud technology is extremely expanding business opportunities. And I think customers will agree that this is a great solution.
And if you understand your business, it will not be difficult for you to explain this to the client in plain language. Everything that we do sounds complicated to the client. For example, 19 steps of device authentication. Therefore, it is not necessary to explain such subtleties to the client. He needs to tell how our solutions will help in organizing the network, and how they will ensure the safe development of the business.
Continuation:
FastTrack Training. "Network Basics." "Cisco Security Products." Eddie Martin December, 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
