2017 Annual Cyber and Information Security Report
Hello, Habr. We would like to present you a short version of the annual report on cyber and information security for 2017, written by us together with the main partner - Wallarm , which provided information on the most noticeable vulnerabilities and hacks.
In 2017, Qrator Labs and Wallarm noted a growing diversification of threats due to the increasing number of possible attack vectors. The range of critical vulnerabilities of today's global network is so wide that attackers can choose various ways to create problems for almost any organization. And a growing number of tools can work automatically, making centralized management redundant.
If 2016 can be called the year of botnets and terabit attacks, then 2017 was the year of networks and routing. Such incidents as Google’s provoked leak of Japanese network routes , the interception of someone else’s Level3 traffic in the United States, and Rostelecom in Russia, like many others, demonstrate persistent and high risks associated with human factors based on mismanagement and insufficient automation of processes. A brave engineer, confidently stopping an important automatic script, can create serious problems in the availability of network resources.
Dynamics of the number of attacks for 2016–2017
We have already seen how quickly the world last year passed from one state to another. Emails, through which attackers extort cryptocurrency by threats of organizing DDoS attacks, can cause panic among employees. The panic state does not contribute to either long-term planning or active protection of the resource in the present. Threats should be considered from afar, looking for time for familiarization and preliminary preparation.
Looking at BlueBorne, you can easily predict the appearance of much larger and larger devices and, of course, much more dangerous botnets in terms of capabilities.
We expect the emergence of even larger botnets than Mirai, capable of flood attacks even without the use of amplification protocols.
Application-level attacks are extremely dangerous, as before.If your company is connected by a dedicated L2 channel to a communication provider, then it is only a matter of time before a vulnerability in separately taken insecure equipment or a third-party service used to maintain operability will be used against you. Commercial DDoS attacks became much more complicated in 2017: get around here, hack there, and ultimately find a way to do damage. 2017 also demonstrated that botnets based on infected Windows machines have not gone away. The effects and consequences of ransomware epidemics such as WannaCry, Petya, and NotPetya can be recreated in the form of a DDoS attack when invisible software will command the generation of traffic from each individual infected machine within a network of any scale. According to our observations, botnets are growing in size - the point is not far,
High-speed attacks based on Windows botnets turned last year’s joke about attacks at 1 Tbps. on an applied level into a sad reality, seen more and more often. Not far off is the day when hundreds of Gbit / s, beating on the same L7 (application level), enter our daily lives. Most likely, this will happen in 2018, because now everything that can be broken by such an attack is turned off much faster than the attack reaches the maximum levels of channel capacity.

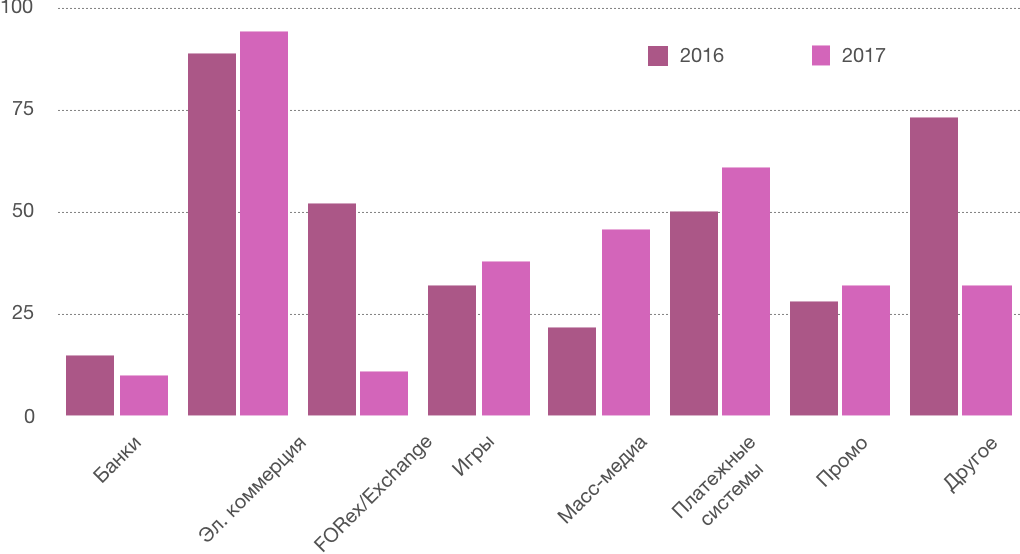
The average number of attacks in specific consumer segments
In 2017, routing incidents became as notorious as botnets in 2016. A successful DDoS attack could always make a single, separate resource or application inaccessible. In the case of popular social networks or libraries that developers use to create and maintain the normal functioning of Internet services, an attack can threaten entire ecosystems that use interconnected parts of the infrastructure (including hosting and a common Internet provider). As we have seen, routing incidents can be no less large-scale and dangerous than attacks of a record botnet, leaving almost an entire country without access to popular resources. What happens if one day you cannot even open a single web page? This makes electronic communication impossible.
The network incident caused by Google in Japan was perhaps the clearest example of what could happen if BGP is not configured correctly by a large, nonetheless, sole content provider.
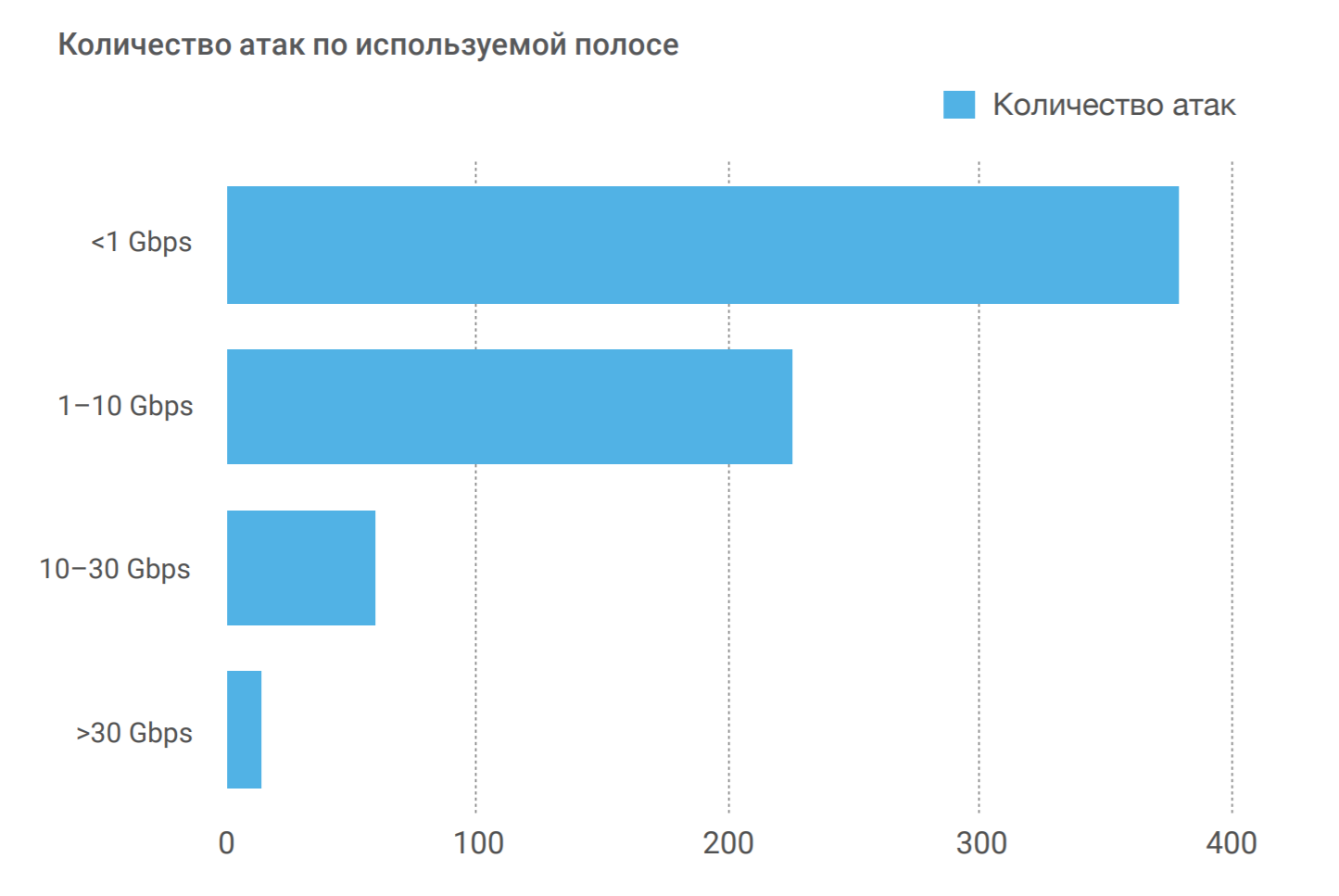
The number of attacks on the used band
2017 was a real year of hacking. From ransomware epidemics to the openings of the Vault7 and Shadow Brokers archives, in addition to notable leaks due to human errors, where Uber and Equifax are the two most notorious examples.
Everything is vulnerable. So the conversation should not be about "what is most vulnerable", but "where the vulnerability can be found earlier." Where vulnerabilities exist, there are attacks. Moreover, there are a number of widespread technologies that reproduce vulnerabilities - when one is fixed and the other breaks. Attackers closely monitor such activities - they know that the larger the supplier in front of them, the more time it will take for it to develop and deliver the update to its customers.
The cloud also becomes legacy with all the problems that are inherited by new generations of devices and technologies. The leaks of Uber and OneLogin began with the fact that the keys to the Amazon store were published on GitHub or elsewhere - it is possible that a sticker stuck to the monitor.
Another serious problem is the situation with MongoDB, Cassandra, Memcached and other popular databases. When their administrators forget to establish an appropriate level of security, it is not difficult for an attacker to find loopholes. This is exactly what happened in the case of the software keyboard for Ai.Type smartphones, which lost all the data of 31 million of its own users.
The main goal of creating a solution to neutralize DDoS is ultimately the establishment of protection, whose support is cheaper than organizing attacks. Only by taking economic advantage from the attackers can we begin to fight on the same conditions. And this is a difficult task, primarily in terms of two factors:
A.Reckless approach to the basics of information security and threat analysis;
B. Fear of news and publicity, attempts to hide information in case of problems.
The new and large ICO market was a real revelation for hackers in 2017. The attack trend at the most stressful moment for the organization (fundraising, advertising campaigns) continues, and with a growing number of cryptocurrency projects, hacking attacks are combined with DDoS. If the cryptocurrency token issuing market continues to grow, this trend will only intensify.
ICOs are of particular interest to all market parties. Due to cryptocurrencies and ICOs, a new hacking industry has grown before our very eyes. Huge amounts of funds are already involved in this market, and the technical side of the implementation of many projects is frankly weak, which we spoke about in 2017. They are constantly hacked.
Mining pools are attacked in the last seconds of the signature of each block in order to receive rewards for signing the block by a competing pool. Cloud cryptocurrency wallets are constantly under attack - during 2017 we saw major hacks of such services with the loss of all cryptocurrencies by their creators. Even mining using scripts in a browser can be profitable, not to mention the infection of a large number of old computers, servers or game consoles with malware that performs calculations at the expense of victims.
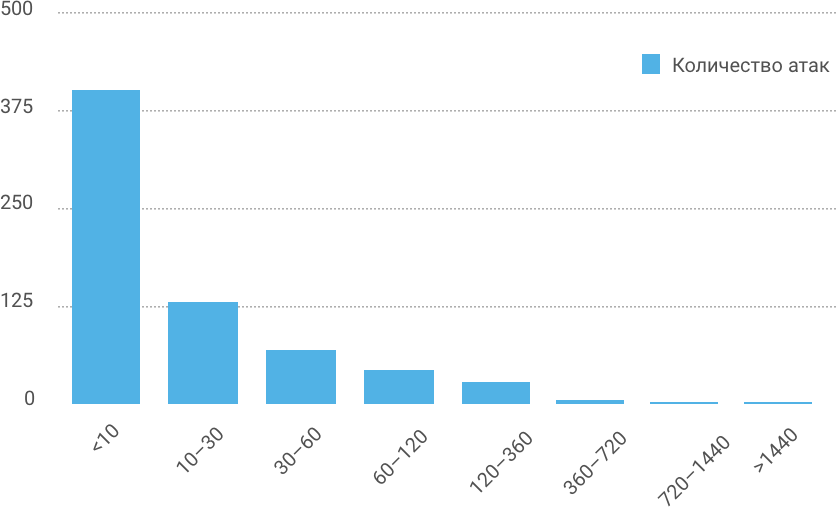
Duration of attacks, minutes
APIs are becoming more and more important for large customers - they are professional and want to have maximum control over the processes of cleaning and filtering traffic. This process should not be underestimated.
The most noticeable fact in this area is not even the attacks themselves, but the progress that all security solution providers have made in the process of training, communication and cooperation, not just competition, in order to find answers to the most serious questions of our time, such as countering botnets. When such large-scale threats appear that call into question the existence of not separate web services, but the entire industry as such, companies are united at several levels: formal, informal, B2G and B2C. We have already seen the successes associated with such cooperation in countering large botnets in 2017 among the largest companies working in the field of information security - we hope that this will happen more often in the future.
Thanks for reading.
Direct link to Russian-language PDF.
In 2017, Qrator Labs and Wallarm noted a growing diversification of threats due to the increasing number of possible attack vectors. The range of critical vulnerabilities of today's global network is so wide that attackers can choose various ways to create problems for almost any organization. And a growing number of tools can work automatically, making centralized management redundant.
If 2016 can be called the year of botnets and terabit attacks, then 2017 was the year of networks and routing. Such incidents as Google’s provoked leak of Japanese network routes , the interception of someone else’s Level3 traffic in the United States, and Rostelecom in Russia, like many others, demonstrate persistent and high risks associated with human factors based on mismanagement and insufficient automation of processes. A brave engineer, confidently stopping an important automatic script, can create serious problems in the availability of network resources.

Dynamics of the number of attacks for 2016–2017
How deep is the rabbit hole
We have already seen how quickly the world last year passed from one state to another. Emails, through which attackers extort cryptocurrency by threats of organizing DDoS attacks, can cause panic among employees. The panic state does not contribute to either long-term planning or active protection of the resource in the present. Threats should be considered from afar, looking for time for familiarization and preliminary preparation.
Many IoT devices are still hacked using trivial methods, such as vulnerabilities in the web interface. Almost all of these vulnerabilities are critical, but the manufacturer has extremely limited ability to quickly create a patch and deliver it as an update.Hacking IoT devices has become more frequent since the Mirai toolkit became the base framework for creating the botnet in 2017. However, earlier incarnations of botnet frameworks became known, from where Mirai drew inspiration for its own code, for example Hajime.
Looking at BlueBorne, you can easily predict the appearance of much larger and larger devices and, of course, much more dangerous botnets in terms of capabilities.
We expect the emergence of even larger botnets than Mirai, capable of flood attacks even without the use of amplification protocols.
Application-level attacks are extremely dangerous, as before.If your company is connected by a dedicated L2 channel to a communication provider, then it is only a matter of time before a vulnerability in separately taken insecure equipment or a third-party service used to maintain operability will be used against you. Commercial DDoS attacks became much more complicated in 2017: get around here, hack there, and ultimately find a way to do damage. 2017 also demonstrated that botnets based on infected Windows machines have not gone away. The effects and consequences of ransomware epidemics such as WannaCry, Petya, and NotPetya can be recreated in the form of a DDoS attack when invisible software will command the generation of traffic from each individual infected machine within a network of any scale. According to our observations, botnets are growing in size - the point is not far,
High-speed attacks based on Windows botnets turned last year’s joke about attacks at 1 Tbps. on an applied level into a sad reality, seen more and more often. Not far off is the day when hundreds of Gbit / s, beating on the same L7 (application level), enter our daily lives. Most likely, this will happen in 2018, because now everything that can be broken by such an attack is turned off much faster than the attack reaches the maximum levels of channel capacity.

The average number of attacks in specific consumer segments
Infrastructure Heritage
In 2017, routing incidents became as notorious as botnets in 2016. A successful DDoS attack could always make a single, separate resource or application inaccessible. In the case of popular social networks or libraries that developers use to create and maintain the normal functioning of Internet services, an attack can threaten entire ecosystems that use interconnected parts of the infrastructure (including hosting and a common Internet provider). As we have seen, routing incidents can be no less large-scale and dangerous than attacks of a record botnet, leaving almost an entire country without access to popular resources. What happens if one day you cannot even open a single web page? This makes electronic communication impossible.
The network incident caused by Google in Japan was perhaps the clearest example of what could happen if BGP is not configured correctly by a large, nonetheless, sole content provider.
In the case of BGP, you must be extremely careful, as the potential damage can be huge. Since BGP controls the transfer of all traffic from one AS to another, we are talking not only about increased delays in access to resources for users, but, more importantly, about the likelihood of a MiTM attack on encrypted traffic. Such incidents can affect millions of users in different countries.We still live in an open network world, but the farther, the more it is perceived as a luxury, and not for granted. In 2017, the fact that any organization can still obtain LIR status and master the autonomous system, thereby becoming a communications operator, deserves separate words of gratitude.
On the one hand, human factors have always been, are and will remain the most vulnerable points for any company or Internet service. On the other hand, the human element is also the strongest defense, since people carry out their work, fully controlling the circumstances in which they are. Technological problems are highly interconnected, since all the code was written by man.

The number of attacks on the used band
Vulnerabilities and Intranets
2017 was a real year of hacking. From ransomware epidemics to the openings of the Vault7 and Shadow Brokers archives, in addition to notable leaks due to human errors, where Uber and Equifax are the two most notorious examples.
Everything is vulnerable. So the conversation should not be about "what is most vulnerable", but "where the vulnerability can be found earlier." Where vulnerabilities exist, there are attacks. Moreover, there are a number of widespread technologies that reproduce vulnerabilities - when one is fixed and the other breaks. Attackers closely monitor such activities - they know that the larger the supplier in front of them, the more time it will take for it to develop and deliver the update to its customers.
The cloud also becomes legacy with all the problems that are inherited by new generations of devices and technologies. The leaks of Uber and OneLogin began with the fact that the keys to the Amazon store were published on GitHub or elsewhere - it is possible that a sticker stuck to the monitor.
Another serious problem is the situation with MongoDB, Cassandra, Memcached and other popular databases. When their administrators forget to establish an appropriate level of security, it is not difficult for an attacker to find loopholes. This is exactly what happened in the case of the software keyboard for Ai.Type smartphones, which lost all the data of 31 million of its own users.
2017 showed how diverse types of equipment can be vulnerable to different types of cyber attacks. In the future we will see even more incidents related to outdated software and hardware.Attacks using smartphones can be carried out both on the basis of infection by malicious applications, even if they are installed from official stores, and using vulnerabilities like BlueBorne. Browser extensions and plugins, network devices (which have already suffered enough over the past three years), any equipment at the junction of providers - everything can be tested for resistance to attacks again and again and probably will not survive in the long run.
The main goal of creating a solution to neutralize DDoS is ultimately the establishment of protection, whose support is cheaper than organizing attacks. Only by taking economic advantage from the attackers can we begin to fight on the same conditions. And this is a difficult task, primarily in terms of two factors:
A.Reckless approach to the basics of information security and threat analysis;
B. Fear of news and publicity, attempts to hide information in case of problems.
Cryptomania
The new and large ICO market was a real revelation for hackers in 2017. The attack trend at the most stressful moment for the organization (fundraising, advertising campaigns) continues, and with a growing number of cryptocurrency projects, hacking attacks are combined with DDoS. If the cryptocurrency token issuing market continues to grow, this trend will only intensify.
ICOs are of particular interest to all market parties. Due to cryptocurrencies and ICOs, a new hacking industry has grown before our very eyes. Huge amounts of funds are already involved in this market, and the technical side of the implementation of many projects is frankly weak, which we spoke about in 2017. They are constantly hacked.
Mining pools are attacked in the last seconds of the signature of each block in order to receive rewards for signing the block by a competing pool. Cloud cryptocurrency wallets are constantly under attack - during 2017 we saw major hacks of such services with the loss of all cryptocurrencies by their creators. Even mining using scripts in a browser can be profitable, not to mention the infection of a large number of old computers, servers or game consoles with malware that performs calculations at the expense of victims.
Network attacks on the hyperledger infrastructure (such as DDoS attacks on mining pools at the end of each block calculation) will grow in number in proportion to the growth of cryptocurrency projects. Every sophisticated technology has a foundation. Finding cracks in it, you can destroy a house of any size.

Duration of attacks, minutes
Epilogue
APIs are becoming more and more important for large customers - they are professional and want to have maximum control over the processes of cleaning and filtering traffic. This process should not be underestimated.
The most noticeable fact in this area is not even the attacks themselves, but the progress that all security solution providers have made in the process of training, communication and cooperation, not just competition, in order to find answers to the most serious questions of our time, such as countering botnets. When such large-scale threats appear that call into question the existence of not separate web services, but the entire industry as such, companies are united at several levels: formal, informal, B2G and B2C. We have already seen the successes associated with such cooperation in countering large botnets in 2017 among the largest companies working in the field of information security - we hope that this will happen more often in the future.
Thanks for reading.
Direct link to Russian-language PDF.
Link to Slideshare
