The "nonexistent" crypto machine of the "nonexistent" agency: NSA (No Such Agency) and KL-7
The US National Security Agency (NSA), Fort Meade (Maryland), is considered the largest and most closed American intelligence agency. In the fall of 1952, US President Truman signed a memorandum on the formation of the NSA. The new body was established under the heading "secret" and only in 1957 did it appear in the directory of US government agencies. There were even jokes about this, the name "NSA" was deciphered as "No Such Agency" (there is no such agency), "Never Say Anything" (never say anything).

Ensuring the national security of the United States and all state communications is the main task of the "nonexistent" agency. Interception and cryptanalysis, the creation and application of cryptographic protection measures, the development of codes and cryptosystems, the creation and implementation of special communication technology are the components of a top-secret institution.
Depending on the required (and acceptable) level of security, the NSA has identified various types of encryption. The lower the number, the higher the level of security. For example: Type 1 products are intended for use by the US government as classified materials. There are 1, 2, 3, 4 types of products:
1. TOP SECRET
This includes algorithms such as AES (256), BATON, FIREFLY, HAVEQUICK and SAVILLE, used in STU-III and in many military communication devices KG-84, KIV- 7, KY-57 and KY-99.
2. National Information Security
Includes products such as CORDOBA, KEA and SKIPJACK, used in Cypris cypto equipment and Fortezza (Plus) crypto cards.
3. Unclassified government or commercial information
Approved (unclassified) algorithms DES, Tripple DES 1, AES, DSA and SHA.
4. Commercial cryptographic equipment not for public use.
Here is not a complete list of devices that are supposed to be (partially) developed in / or for the NSA:

KL-7 is an electromechanical rotary crypto machine developed by the National Security Agency (NSA) in the United States. It was commissioned in 1952, and for many years served as the main encryption machine of the United States and NATO. The relatively light weight (9.3 kg) of the KL-7 allows us to consider it a more advanced version of the German Enigma machine. In wartime, she replaced SIGABA (ECM Mark II) in the UK and Canada, as well as CCM and British Typex cars.

SIGABA (ECM Mark II)
Initially, the machine was called AFSAM-7, but in the early 1960s it was replaced by TSEC / KL-7. The device, depending on the level of security of keys, was codenamed ADONIS (high level) and POLLUX (low level). KL-7 was removed from service in 1983.
Unlike Enigma, the KL-7 had eight rotors, seven of which were placed in one step module. The cars were produced in several versions and were used by the US Army, Navy and NATO for many years.
Unfortunately, the KL-7 is still a classified device and only a few copies have survived to this day. Most of the cars that are on display today were “cleaned up” (without wiring).
Despite the secrecy regarding the KL-7 and its history, over time the information becomes partially available, the NSA produces more and more historical documents, as a result of which researchers are able to find out the technical details of the machine’s structure. In 2011, crypto-historian Dirk Raimannant from Belgium, thanks to computer modeling (under Windows), was able to recreate KL-7, and in 2013 the JAVA-simulator KL-7 from MIT (USA) appeared.
KL-7 remained in service until the 1970s. In some countries, KL-7s served as backup devices for many years until they were finally removed from service in 1983. The last message was sent on June 30, 1983 by the Canadian Navy. The KL-7 has been replaced by a number of electronic machines known as the KW-26, KW-37, KL-51 (RACE) and Aroflex.

Aroflex
The KL-7 machine consisted of the following main elements:
KLX-7 . I / O interface for 5-level (print printers) data. It consists of two blocks: one is installed between the keyboard and the base unit, the second - behind the rotor basket.
EZ-KL7 . An additional unit developed by the German army (Bundeswehr), allowing two KL-7s to work in tandem to detect errors. EX-KL7 was installed in front of the keyboard.
KL-7 was an electromechanical rotary crypto machine controlled by electronic circuits with valves (vacuum valves). The device was powered from an external 24 V DC source, essentially as a power supply or battery, for example, a truck. For the synchronous operation of the machine, a complex mechanical assembly consisting of several rotating parts connected by a common axis was responsible. The flow chart below shows exactly how this happened. The main 24 V motor was operating at a speed of 6600 rpm. He ran mechanical parts as well as an alternator that provided 400 V for controlling valves / gate valves.
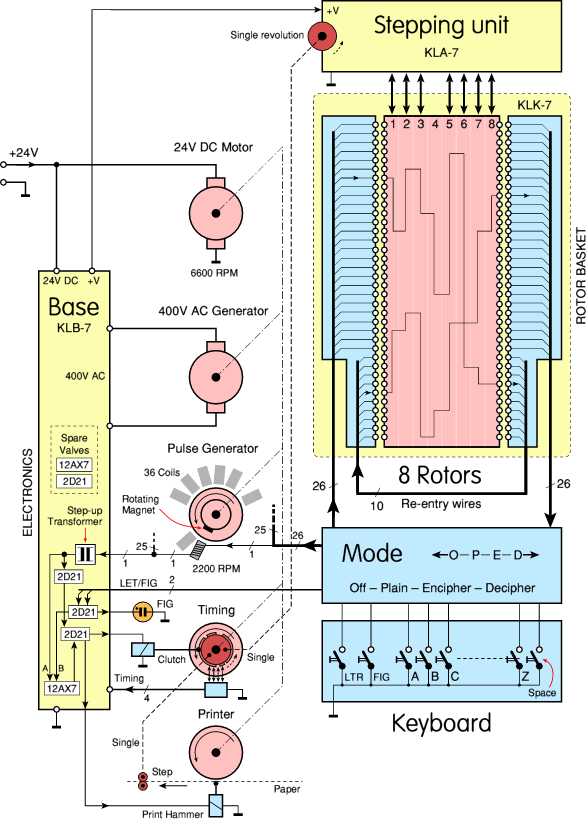
When a specific key on the keyboard was pressed, containing 26 pulse transmission lines (due to the mode switch), a pulse was transmitted to the rotors, and then to one of the 26 coils of the pulse generator. Pulses were applied to the printing device. Since all rotating parts (DC motor, alternator, pulse generator, printer, and step module) were connected, everything worked synchronously.
KLB-7 - was actually the chassis on which the machine was built, including electronic circuits and a (mechanical) transmission system. The latter consisted of an engine, synchronization unit, printer, etc. Note that the KLB-7 was (never) a classified item. Apparently, the electromechanical base module was not considered one that could give out cryptographic secrets.
KL-7 rotors resemble the rotors of the famous German Enigma machine and other rotary-based crypto machines. Each rotor (disk) had electrical contacts on the left and right. The disc contained an adjustable index ring with the letters of the alphabet on it and an inner part that connected the contacts on one side with the contacts on the other side. However, there were some significant differences from Enigma.

First of all, the KL-7 rotor had 36 contacts, while the Enigma rotor had 26 contacts. Of the 36 contacts, 26 were used to encrypt 26 letters of the alphabet, and the remaining 10 contacts were used to “loop” during input (see below). This led to the re-encryption of part of the text (US patent 2998700, filed by Albert W. Small September 22, 1944).
Each rotor had an index ring with 36 positions, each of which was divided by a narrow gap. Only 26 positions were identified by letters of the alphabet. The rest are empty. In a U-turn it looks like this:

Another important difference from Enima is the absence of a reflector (Umkehrwalze). In coding mode, one side of the rotary basket is the input, and the other side is the output. In decoding mode - by changing contacts - vice versa. However, replacing all the contacts is a rather complicated “procedure”; a whole complex of multi-contact switches were integrated that were integrated into the KL-7 keyboard.
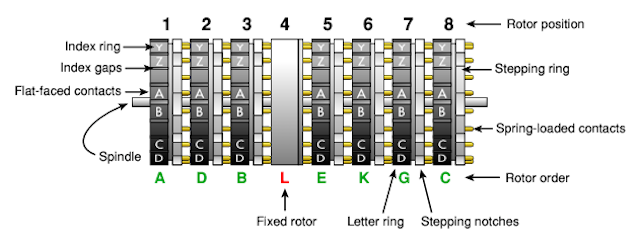
The rotor drum or rotary basket KL-7 was a metal box containing 8 wheels on a spindle (KLK-7). The fourth wheel on the left was fixed in place. It never spun, and therefore had no window, and did not show its setting. This wheel is sometimes called the NSA rotor. For each of the remaining 7 wheels in the drum there was a window. Three consecutive letters of the rotor were visible through this window. The upper letter is the current setting, the position was indicated by a white line, reading took place from left to right.
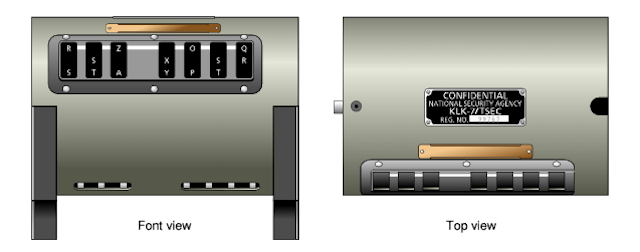
Each KL-7 was shipped with 12 rotors marked AL in a metal box. The L-rotor was the so-called fixed NSA wheel used in position 4. Of the remaining 11 rotors (AK), 7 were inserted into the rotor drum according to the code book: on a certain day, in a certain order.
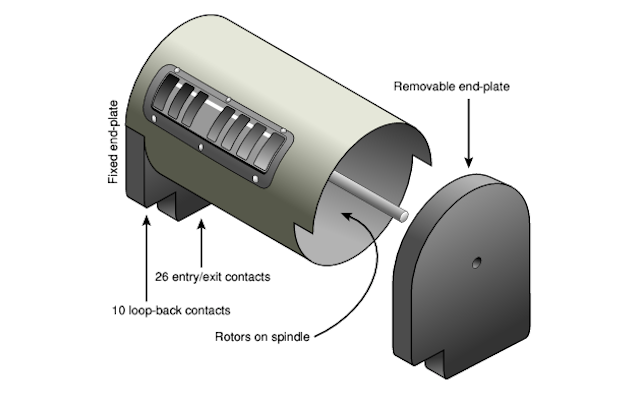
The user could remove the rotor drum by releasing two levers on both sides of it. After removal, the right wall of the drum was disconnected and the rotors could be removed from the spindle. The spindle itself remained inside, since it was attached to the left wall, which, in turn, was attached to the cylindrical drum itself.
Each wheel had 36 contacts on both sides, but only 26 of them were used to encrypt 26 letters of the Latin alphabet. The remaining 10 contacts were looped from the right end plate to the left, which caused transcoding. This principle is known as “return” and was invented during World War II by Albert W. Maly, during his work in the US Army Intelligence Service (ASIS), when he tried to decode the cipher of the Japanese PURPLE crypto machine.
US patent 2984700 for the invention was filed by scientists on September 22, 1944. Since the invention was considered to belong to the U.S. Army, the patent was classified and was classified secretly until May 16, 1961. In the meantime, inventor Boris Hagelin put forward a similar idea, successfully patented it on October 16, 1953. The existence of an earlier (secret) patent did not affect the process in any way and Hagelin received the patent 2,802,047 on August 6, 1957. Hagelin intended to use the re-entry principle for his HX cryptographic machine. To his surprise, the same patent was rejected in Japan. He was simply not aware of the existence of a secret similar patent.
Although Hagelin claimed that it was his whole idea, it is quite possible (if not likely) that the idea visited him after he had been dealing with the KL-7 crypto machine in the early 1950s and had discussed its properties with the German chief cryptographer Erich Huttenhain in Bonn (1952). The principle of re-entry was used in the Soviet M-125 Violet.
KL-7 rotors are identical to the rotors used in the British Singlet BID / 60. It is possible that the cryptographic wheels were a joint production of the USA / Great Britain, or the Americans allowed the British to use KL-7 rotors in a British encryption machine. In any case, Singlet rotors were manufactured in the UK.

The British Singlet had 10 rotors (instead of 8), but it was reported that they are compatible with the KL-7, and can use the same eight rotors, two of which will be dummies.
Each KL-7 rotor contained 36 connections, connected via flat contacts on one side with spring-loaded contacts on the other side, apparently in a random order. The connection of the KL-7 rotors has always been kept secret, whether there was any sense in this - remains to be seen.
For safety reasons, it was forbidden to monitor the rotary connection of the KL-7. Even the technical staff involved in the repair of the crypto device did not have the right to track each contact to identify and eliminate the faulty connection. All that was allowed was to establish spring-loaded contacts on a conductive (metal) surface and check each flat contact. Defective rotors never opened; they had to be returned to the NSA for repair.
If you manage to find the KL-7 and track the rotor connections, the sense of this will be exactly “0”, since the rotor connections for different users were different and often changed for security reasons. Nevertheless, over the years, the Soviet Union successfully read information about the movements of submarines of the US Navy (encrypted on KL-7).
The rotors were held in place by the locking levers. These are spring-loaded levers located under the rotors. At the end of the lever is a small sharp wedge that fits into the groove between the desired letters on the circumference of the rotor. Closer to the front in the lower part of the rotary drum were the "transportation" levers. They were driven by the main mechanism and locked in the gaps on the index rotor. Their forward movement rotated the rotor to the next position. With a single keystroke, the rotor could take only one step.


Whether the rotor will move when a key is pressed depends on the presence or absence of a notch on the stepping ring on one of the rotors. The step ring of each rotor was determined by a switch (3) located in front of the rotor drum.

Interestingly, the switch determined the 10th position of the step ring on the circumference of the rotor. In other words: when the rotor was at point A (visible in the window on the white line), the notch in front of the letter H was determined by the switch (that is, the 10th position after A). The switch, in turn, activated the solenoid (L1 - L7), as a result, the rotor rotated.

When setting the daily key, the initial position of the rotors could be changed manually: by pressing the keys while in plain text mode (P). When the key was pressed briefly, the rotor advanced one step. Keeping the key pressed, the rotor took steps continuously.
Rotor motion control - was a whole complex, and was fixed by internal connection (wiring). Details about the arrangement of the rotor stepper mechanism were never published, but in 2011, the Crypto Museum using deduction during machine operation was able to restore the circuit shown below:
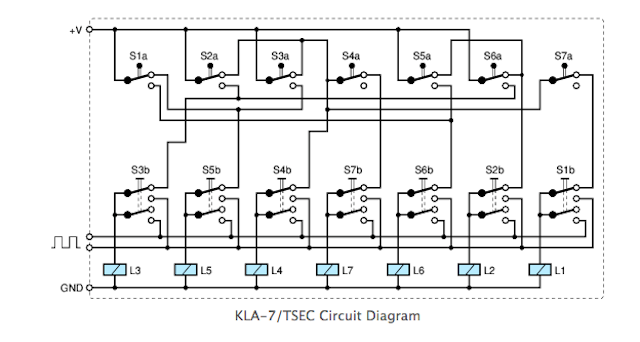
Please note that the switches at the top are in the proper order (from 1 to 7), and the order is manual switches and solenoids mixed. This is done so as not to clutter up the circuit. The step module presented here is implemented in the KL-7 Dirk Rijmenants simulator, the correctness of which is confirmed by former users.
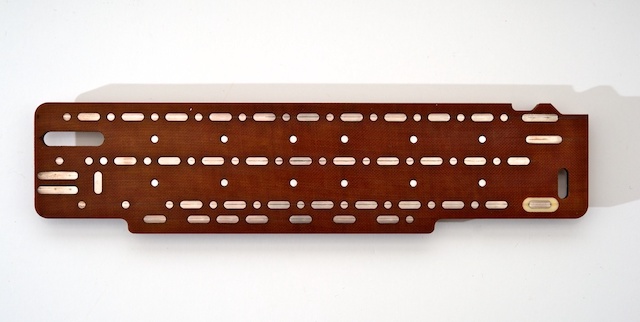
The KL-7 keyboard is part of the KLB-7 base module. It consisted of 29 green keys and a black strip. There was a standard QWERTY layout divided into three rows. The numbers were separated by the top line. In the lower right corner were 3 special keys, marked as LET, FIG and RPT.

Each key was actually an electrical switch, consisting of a contact and a spring mounted under the key. Each time, when a key was pressed, the contact was grounded (i.e. connected to 0V), allowing the pulse generator to give out a pulse.

When entering numbers, the user first had to press the FIG key (numbers). It acted like a removable key on a modern computer. While the machine was in number mode, a large neon lamp was lit behind the keyboard. To return to the literal values, you must first press the LET key.

The coded message KL-7 consisted of only 26 letters of the Latin alphabet. In order for the source text to contain letters, numbers and spaces, it was necessary to use special techniques. This was done by converting / replacing some letters while holding down SPACE, LET and FIG.

In addition, when switching from encoding to decoding, operations (SPACE, LET and FIG) should have been canceled. All this was done using the MODE switch, which was located under the keyboard. The MODE switch was a large board made of an electrically insulating laminated pressed material, with contacts on both sides (very similar to a printed circuit board, but thicker).

To control the switch, there was a knob to the left of the keyboard. The MODE switch had 4 positions: Off (O), paintext (P), encoding (E) and decoding (D).

The mode switch is actually a large slide switch. As the handle rotates, the large brown getinax board moved from right to left. As mentioned earlier, there were various provisions.

At the heart of the KL-7 is a very compact but sophisticated mechanical module. It consisted of a DC motor and a high-voltage alternator, a printing device, a pulse generator and a synchronization module. All devices were powered by a DC motor, either directly or using 3: 1 gears.
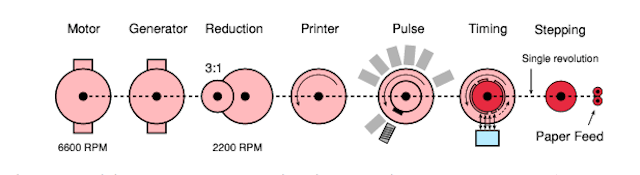
The engine and generator were mounted on the same axis, the rotation speed was 6600 rpm (revolutions per minute). Thanks to the gear mechanism (3: 1), the pulse generator and the printing device were set in motion, and their rotation speed was 2200 rpm. The synchronization module was also driven.
Unlike other components, the synchronization module did not rotate continuously. It was also controlled by the KLA-7 stepping module (and therefore rotors). At each revolution, the rotors could advance one position.

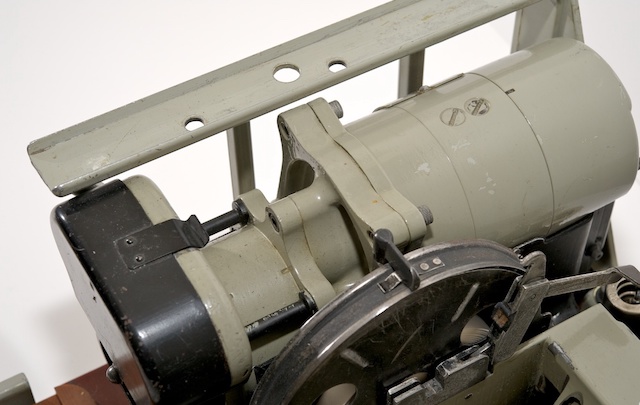
The module complex was located in the left half of the KL-7, as shown in the figure. The engine was located behind the module (on the right in the image). Directly in front of the engine is a generator (sometimes called an inverter) with two large bolts at the top.
Synchronization with the printer was due to the pulse generator, which was connected to all other rotating parts of the main device module. The pulse generator consisted of 36 coils, divided into two rings, with a rotating magnet in the center. 26 coils were used for 26 letters of the alphabet. The remaining 10 coils are for numbers. Each of them was connected in series with one of the letters, but was mounted on the ring at a slightly different angle. This resulted in a short delay in the numeric mode (FIG), which allowed enough time to select the next character on the printing wheel.
The KL-7 was designed with an integrated printer with a continuously rotating print head. The output was printed on a narrow paper strip of 9.5 mm (3/8 "), similar to the American M-209 and Soviet Violet.

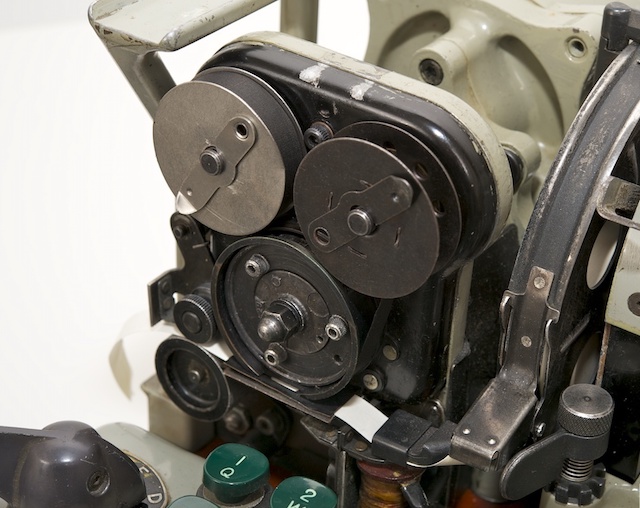
Letters and numbers were placed on the circumference of the print head. When the letter was printed (i.e., the pulse generator issued impulse), the paper ribbon moved one position, and the squeezing hammer fell.

Synchronization was guaranteed, since the pulse generator and print head were controlled by one axis. A small ink ribbon was hidden under the black cover, it passed between the print head and the paper tape.
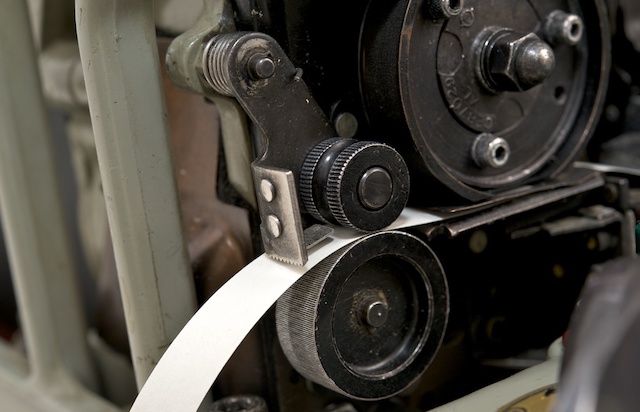
The design of the printer can be said to be identical to the design of the printer in SIGABA, the predecessor of the wartime KL-7. Like the KL-7, it had a rotating print head with two coloring ribbon coils.
The KL-7 is not considered one of the most reliable machines. In fact, it was reputed to be notorious due to the numerous problems associated with its operation. Many former users recall their “struggle” with the KL-7 in order to correctly (de) encode messages on it.
The German Bundeswehr even developed an assembly known as the EZ-KL7, which allowed two machines to work in tandem (in parallel) to detect errors. The EZ-KL7 unit was installed in front of the keyboard of one of the two KL-7 machines and constantly compared their findings. As soon as a difference was detected, an alarm was raised. Please note that the EZ-KL7 is pronounced “Easy KL-7”.
This option required the installation of the KLX-7 I / O interface.
By itself, the KL-7 received input information only through the built-in keyboard, and displayed information in the form of printed text on 9.5 mm paper tape. To connect the KL-7 directly to the teleprinter, the KLX-7 I / O interface was available. As far as we know, the KLX-7 consisted of two parts, one of which was installed between the keyboard and the base.
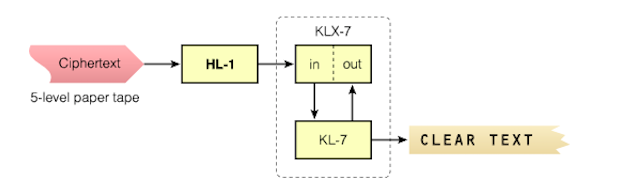
All this required removing the keyboard, and a contact module was installed in its place. Later the keyboard was made removable, now it could be placed on top of the contact module. In reality, an I / O interface was installed on the rear of the machine, behind a drum with rotors.
Secret are - a drum with rotors (KLK-7 / TSEC), a stepper mechanism (KLA-7 / TSEC) and an electric circuit. All other modules of the device are free from the heading "secret". Given the age of KL-7 and the fact that more and more principles of the cryptocurrency machine are becoming understood by researchers, it is assumed that in the near future it will be fully declassified. The NSA recently released a document that describes the history of the KL-7.
Over the course of its life, the KL-7 was at risk several times. It is believed that in the Soviet Union they were able to intercept and decrypt KL-7 messages.

The most famous story is the story of John Anthony Walker, born in 1937, who worked in the U.S. Navy and successfully spied on the side of the USSR for almost 17 years. Walker joined the U.S. Navy in 1955 and became a Soviet spy since December 1967, explaining all the financial difficulties in life. From that moment, until his retirement from the Navy (1983), he provided the USSR with key lists and other critical encryption materials KL-47, KW-7 and other crypto machines.
For the information he received, he received several thousand dollars every month. In 1969, he began to seek help in his espionage business and made friends with Jerry Whitworth, a student who later became a senior naval officer. In 1973, Anthony was able to enlist his help. In 1984, the circle of his spies was replenished with new members - older brother Arthur and son Michael. Walker also tried to attract his daughter, a newly-made officer in the US Army, but she dropped out of the “game”, becoming pregnant and giving up her military career.
In 1976, Walker and his wife Barbara divorced due to beatings and alcohol abuse by Walker. Walker refused to pay child support (1985) and Barbara handed him over to the FBI, which ultimately led to his arrest. After his arrest, Walker partnered with the authorities and entered into a plea bargain to lower his sentence to his son Michael. Suffering from diabetes and throat cancer, John Walker died in prison on August 28, 2014. His son Michael was released on parole in February 2000.
Information transmitted by John Walker and his espionage group allowed the USSR to build an analogue of the KL-7. As a result, at least a million secret messages (TOP SECRET) were decrypted. The KL-7 analogue was even equipped with a small device called a rotary reader, which made it easy to trace the internal wiring of each rotor.
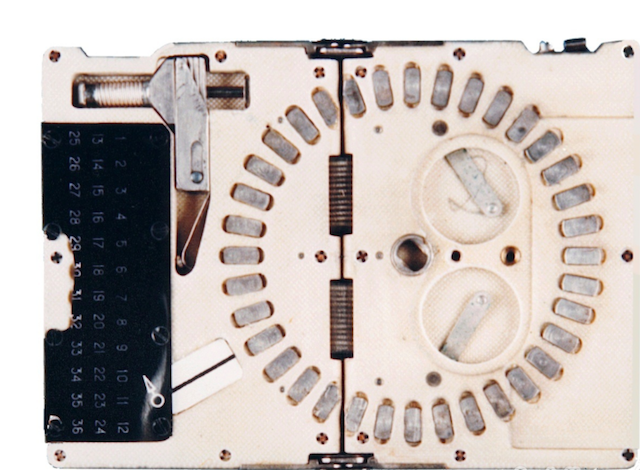
In the photo above - the device itself, though it was confiscated by the FBI. Small enough so that it can be imperceptibly carried and easily hidden in your pocket. When folding, its dimensions were 7.5 x 10 cm (such as a pack of cigarettes).
The KL-7 was once again compromised in its history. Here is how it was. During the Vietnam War (1970), the Americans decided to provide the Republic of Vietnam (RVN) with a limited amount of cryptographic equipment: M-209 and KL-7 encryption machines, various One-Time Pad (OTP) systems, voice authentication codes and NESTOR ( KY-8).
After the withdrawal of US troops from Vietnam, the base with cryptographic equipment and the American employees in charge of this equipment, known as Don Vi '600, remained in place. In late 1974 and early 1975, the situation worsened, and the Americans began to recall part of the equipment with the intention of sending it back to CONUS or Hawaii.
In January - February, the situation became critical, it was decided to immediately remove the equipment from Don Vi '600 and forward it to CONUS. In three weeks, about 700 pieces of ADONIS and NESTOR equipment were prepared for shipment to CONUS, but, unfortunately, none of these devices were sent or destroyed on time. In the end, the equipment fell into the hands of North Vietnam.
It is likely that the North Vietnamese eventually sold some cars to the USSR and the Chinese, along with key materials (received over 12 months) and One-Time Pad (OTP) systems.

The National Museum of Cryptography (created by the NSA) has become home to many exhibits that lift the veil of secrecy and fill the gaps in the history of cryptography from the time of the War of Independence to the present day.
The source was the amazing work of the Cypto Museum .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analog entry-level server that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4 RAM).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read aboutHow to build an infrastructure class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

Ensuring the national security of the United States and all state communications is the main task of the "nonexistent" agency. Interception and cryptanalysis, the creation and application of cryptographic protection measures, the development of codes and cryptosystems, the creation and implementation of special communication technology are the components of a top-secret institution.
Depending on the required (and acceptable) level of security, the NSA has identified various types of encryption. The lower the number, the higher the level of security. For example: Type 1 products are intended for use by the US government as classified materials. There are 1, 2, 3, 4 types of products:
1. TOP SECRET
This includes algorithms such as AES (256), BATON, FIREFLY, HAVEQUICK and SAVILLE, used in STU-III and in many military communication devices KG-84, KIV- 7, KY-57 and KY-99.
2. National Information Security
Includes products such as CORDOBA, KEA and SKIPJACK, used in Cypris cypto equipment and Fortezza (Plus) crypto cards.
3. Unclassified government or commercial information
Approved (unclassified) algorithms DES, Tripple DES 1, AES, DSA and SHA.
4. Commercial cryptographic equipment not for public use.
Here is not a complete list of devices that are supposed to be (partially) developed in / or for the NSA:
- HY-2 - narrowband voice encoder
- STU-I - Secure First Generation Digital Telephone Device (STU)
- STU-II - second generation telephone set (STU)
- STU-III - the latest in a series of digital telephone sets (STU)
- STE - a telephone that provides voice and data protection through ISDN and PSTN telephone lines
- KL-7 - Rotary Encryption Machine
- KW-7 - a highly reliable online crypto machine
- KG-13 - Universal Digital Transistor Full Duplex Key Generator
- KW-26 - large electronic encryption device
- KG-84 - military digital encoder
- Fortezza - Hardware Security Module (HSM), which is implemented as a PCMCIA board
- FLYBALL modules - functional electronic circuits
Crypto machine KL-7

KL-7 is an electromechanical rotary crypto machine developed by the National Security Agency (NSA) in the United States. It was commissioned in 1952, and for many years served as the main encryption machine of the United States and NATO. The relatively light weight (9.3 kg) of the KL-7 allows us to consider it a more advanced version of the German Enigma machine. In wartime, she replaced SIGABA (ECM Mark II) in the UK and Canada, as well as CCM and British Typex cars.

SIGABA (ECM Mark II)
Initially, the machine was called AFSAM-7, but in the early 1960s it was replaced by TSEC / KL-7. The device, depending on the level of security of keys, was codenamed ADONIS (high level) and POLLUX (low level). KL-7 was removed from service in 1983.
Unlike Enigma, the KL-7 had eight rotors, seven of which were placed in one step module. The cars were produced in several versions and were used by the US Army, Navy and NATO for many years.
Unfortunately, the KL-7 is still a classified device and only a few copies have survived to this day. Most of the cars that are on display today were “cleaned up” (without wiring).
Despite the secrecy regarding the KL-7 and its history, over time the information becomes partially available, the NSA produces more and more historical documents, as a result of which researchers are able to find out the technical details of the machine’s structure. In 2011, crypto-historian Dirk Raimannant from Belgium, thanks to computer modeling (under Windows), was able to recreate KL-7, and in 2013 the JAVA-simulator KL-7 from MIT (USA) appeared.
KL-7 remained in service until the 1970s. In some countries, KL-7s served as backup devices for many years until they were finally removed from service in 1983. The last message was sent on June 30, 1983 by the Canadian Navy. The KL-7 has been replaced by a number of electronic machines known as the KW-26, KW-37, KL-51 (RACE) and Aroflex.

Aroflex
The constituent elements of the device
The KL-7 machine consisted of the following main elements:
- KLB-7 is a basic module consisting of an engine, generator and electronics (valves or vacuum tubes).
- KLK-7 - eight KL-7 rotors were placed on the spindle inside the rotor drum (basket). Having released two levers located on both sides of the basket with rotors, it was possible to pull it out of the car.
- OAK-7 - step module.
Options
KLX-7 . I / O interface for 5-level (print printers) data. It consists of two blocks: one is installed between the keyboard and the base unit, the second - behind the rotor basket.
EZ-KL7 . An additional unit developed by the German army (Bundeswehr), allowing two KL-7s to work in tandem to detect errors. EX-KL7 was installed in front of the keyboard.
Flow chart
KL-7 was an electromechanical rotary crypto machine controlled by electronic circuits with valves (vacuum valves). The device was powered from an external 24 V DC source, essentially as a power supply or battery, for example, a truck. For the synchronous operation of the machine, a complex mechanical assembly consisting of several rotating parts connected by a common axis was responsible. The flow chart below shows exactly how this happened. The main 24 V motor was operating at a speed of 6600 rpm. He ran mechanical parts as well as an alternator that provided 400 V for controlling valves / gate valves.

When a specific key on the keyboard was pressed, containing 26 pulse transmission lines (due to the mode switch), a pulse was transmitted to the rotors, and then to one of the 26 coils of the pulse generator. Pulses were applied to the printing device. Since all rotating parts (DC motor, alternator, pulse generator, printer, and step module) were connected, everything worked synchronously.
KLB-7 base module
KLB-7 - was actually the chassis on which the machine was built, including electronic circuits and a (mechanical) transmission system. The latter consisted of an engine, synchronization unit, printer, etc. Note that the KLB-7 was (never) a classified item. Apparently, the electromechanical base module was not considered one that could give out cryptographic secrets.
KLK-7 rotors
KL-7 rotors resemble the rotors of the famous German Enigma machine and other rotary-based crypto machines. Each rotor (disk) had electrical contacts on the left and right. The disc contained an adjustable index ring with the letters of the alphabet on it and an inner part that connected the contacts on one side with the contacts on the other side. However, there were some significant differences from Enigma.

First of all, the KL-7 rotor had 36 contacts, while the Enigma rotor had 26 contacts. Of the 36 contacts, 26 were used to encrypt 26 letters of the alphabet, and the remaining 10 contacts were used to “loop” during input (see below). This led to the re-encryption of part of the text (US patent 2998700, filed by Albert W. Small September 22, 1944).
Each rotor had an index ring with 36 positions, each of which was divided by a narrow gap. Only 26 positions were identified by letters of the alphabet. The rest are empty. In a U-turn it looks like this:

Another important difference from Enima is the absence of a reflector (Umkehrwalze). In coding mode, one side of the rotary basket is the input, and the other side is the output. In decoding mode - by changing contacts - vice versa. However, replacing all the contacts is a rather complicated “procedure”; a whole complex of multi-contact switches were integrated that were integrated into the KL-7 keyboard.

The rotor drum or rotary basket KL-7 was a metal box containing 8 wheels on a spindle (KLK-7). The fourth wheel on the left was fixed in place. It never spun, and therefore had no window, and did not show its setting. This wheel is sometimes called the NSA rotor. For each of the remaining 7 wheels in the drum there was a window. Three consecutive letters of the rotor were visible through this window. The upper letter is the current setting, the position was indicated by a white line, reading took place from left to right.

Each KL-7 was shipped with 12 rotors marked AL in a metal box. The L-rotor was the so-called fixed NSA wheel used in position 4. Of the remaining 11 rotors (AK), 7 were inserted into the rotor drum according to the code book: on a certain day, in a certain order.

The user could remove the rotor drum by releasing two levers on both sides of it. After removal, the right wall of the drum was disconnected and the rotors could be removed from the spindle. The spindle itself remained inside, since it was attached to the left wall, which, in turn, was attached to the cylindrical drum itself.
Re-entry principle
Each wheel had 36 contacts on both sides, but only 26 of them were used to encrypt 26 letters of the Latin alphabet. The remaining 10 contacts were looped from the right end plate to the left, which caused transcoding. This principle is known as “return” and was invented during World War II by Albert W. Maly, during his work in the US Army Intelligence Service (ASIS), when he tried to decode the cipher of the Japanese PURPLE crypto machine.
US patent 2984700 for the invention was filed by scientists on September 22, 1944. Since the invention was considered to belong to the U.S. Army, the patent was classified and was classified secretly until May 16, 1961. In the meantime, inventor Boris Hagelin put forward a similar idea, successfully patented it on October 16, 1953. The existence of an earlier (secret) patent did not affect the process in any way and Hagelin received the patent 2,802,047 on August 6, 1957. Hagelin intended to use the re-entry principle for his HX cryptographic machine. To his surprise, the same patent was rejected in Japan. He was simply not aware of the existence of a secret similar patent.
Although Hagelin claimed that it was his whole idea, it is quite possible (if not likely) that the idea visited him after he had been dealing with the KL-7 crypto machine in the early 1950s and had discussed its properties with the German chief cryptographer Erich Huttenhain in Bonn (1952). The principle of re-entry was used in the Soviet M-125 Violet.
British Singlet BID / 60
KL-7 rotors are identical to the rotors used in the British Singlet BID / 60. It is possible that the cryptographic wheels were a joint production of the USA / Great Britain, or the Americans allowed the British to use KL-7 rotors in a British encryption machine. In any case, Singlet rotors were manufactured in the UK.

The British Singlet had 10 rotors (instead of 8), but it was reported that they are compatible with the KL-7, and can use the same eight rotors, two of which will be dummies.
Rotor connection
Each KL-7 rotor contained 36 connections, connected via flat contacts on one side with spring-loaded contacts on the other side, apparently in a random order. The connection of the KL-7 rotors has always been kept secret, whether there was any sense in this - remains to be seen.
For safety reasons, it was forbidden to monitor the rotary connection of the KL-7. Even the technical staff involved in the repair of the crypto device did not have the right to track each contact to identify and eliminate the faulty connection. All that was allowed was to establish spring-loaded contacts on a conductive (metal) surface and check each flat contact. Defective rotors never opened; they had to be returned to the NSA for repair.
If you manage to find the KL-7 and track the rotor connections, the sense of this will be exactly “0”, since the rotor connections for different users were different and often changed for security reasons. Nevertheless, over the years, the Soviet Union successfully read information about the movements of submarines of the US Navy (encrypted on KL-7).
Step module
The rotors were held in place by the locking levers. These are spring-loaded levers located under the rotors. At the end of the lever is a small sharp wedge that fits into the groove between the desired letters on the circumference of the rotor. Closer to the front in the lower part of the rotary drum were the "transportation" levers. They were driven by the main mechanism and locked in the gaps on the index rotor. Their forward movement rotated the rotor to the next position. With a single keystroke, the rotor could take only one step.


Whether the rotor will move when a key is pressed depends on the presence or absence of a notch on the stepping ring on one of the rotors. The step ring of each rotor was determined by a switch (3) located in front of the rotor drum.

Interestingly, the switch determined the 10th position of the step ring on the circumference of the rotor. In other words: when the rotor was at point A (visible in the window on the white line), the notch in front of the letter H was determined by the switch (that is, the 10th position after A). The switch, in turn, activated the solenoid (L1 - L7), as a result, the rotor rotated.

When setting the daily key, the initial position of the rotors could be changed manually: by pressing the keys while in plain text mode (P). When the key was pressed briefly, the rotor advanced one step. Keeping the key pressed, the rotor took steps continuously.
Rotor Stepper
Rotor motion control - was a whole complex, and was fixed by internal connection (wiring). Details about the arrangement of the rotor stepper mechanism were never published, but in 2011, the Crypto Museum using deduction during machine operation was able to restore the circuit shown below:

Please note that the switches at the top are in the proper order (from 1 to 7), and the order is manual switches and solenoids mixed. This is done so as not to clutter up the circuit. The step module presented here is implemented in the KL-7 Dirk Rijmenants simulator, the correctness of which is confirmed by former users.
Keyboard
The KL-7 keyboard is part of the KLB-7 base module. It consisted of 29 green keys and a black strip. There was a standard QWERTY layout divided into three rows. The numbers were separated by the top line. In the lower right corner were 3 special keys, marked as LET, FIG and RPT.

Each key was actually an electrical switch, consisting of a contact and a spring mounted under the key. Each time, when a key was pressed, the contact was grounded (i.e. connected to 0V), allowing the pulse generator to give out a pulse.

When entering numbers, the user first had to press the FIG key (numbers). It acted like a removable key on a modern computer. While the machine was in number mode, a large neon lamp was lit behind the keyboard. To return to the literal values, you must first press the LET key.

Mode switch
The coded message KL-7 consisted of only 26 letters of the Latin alphabet. In order for the source text to contain letters, numbers and spaces, it was necessary to use special techniques. This was done by converting / replacing some letters while holding down SPACE, LET and FIG.

In addition, when switching from encoding to decoding, operations (SPACE, LET and FIG) should have been canceled. All this was done using the MODE switch, which was located under the keyboard. The MODE switch was a large board made of an electrically insulating laminated pressed material, with contacts on both sides (very similar to a printed circuit board, but thicker).

To control the switch, there was a knob to the left of the keyboard. The MODE switch had 4 positions: Off (O), paintext (P), encoding (E) and decoding (D).


The mode switch is actually a large slide switch. As the handle rotates, the large brown getinax board moved from right to left. As mentioned earlier, there were various provisions.

Device module
At the heart of the KL-7 is a very compact but sophisticated mechanical module. It consisted of a DC motor and a high-voltage alternator, a printing device, a pulse generator and a synchronization module. All devices were powered by a DC motor, either directly or using 3: 1 gears.

The engine and generator were mounted on the same axis, the rotation speed was 6600 rpm (revolutions per minute). Thanks to the gear mechanism (3: 1), the pulse generator and the printing device were set in motion, and their rotation speed was 2200 rpm. The synchronization module was also driven.

Unlike other components, the synchronization module did not rotate continuously. It was also controlled by the KLA-7 stepping module (and therefore rotors). At each revolution, the rotors could advance one position.

The module complex was located in the left half of the KL-7, as shown in the figure. The engine was located behind the module (on the right in the image). Directly in front of the engine is a generator (sometimes called an inverter) with two large bolts at the top.
Pulse generator
Synchronization with the printer was due to the pulse generator, which was connected to all other rotating parts of the main device module. The pulse generator consisted of 36 coils, divided into two rings, with a rotating magnet in the center. 26 coils were used for 26 letters of the alphabet. The remaining 10 coils are for numbers. Each of them was connected in series with one of the letters, but was mounted on the ring at a slightly different angle. This resulted in a short delay in the numeric mode (FIG), which allowed enough time to select the next character on the printing wheel.
Printing device
The KL-7 was designed with an integrated printer with a continuously rotating print head. The output was printed on a narrow paper strip of 9.5 mm (3/8 "), similar to the American M-209 and Soviet Violet.


Letters and numbers were placed on the circumference of the print head. When the letter was printed (i.e., the pulse generator issued impulse), the paper ribbon moved one position, and the squeezing hammer fell.

Synchronization was guaranteed, since the pulse generator and print head were controlled by one axis. A small ink ribbon was hidden under the black cover, it passed between the print head and the paper tape.

The design of the printer can be said to be identical to the design of the printer in SIGABA, the predecessor of the wartime KL-7. Like the KL-7, it had a rotating print head with two coloring ribbon coils.
German tandem version EZ-KL7
The KL-7 is not considered one of the most reliable machines. In fact, it was reputed to be notorious due to the numerous problems associated with its operation. Many former users recall their “struggle” with the KL-7 in order to correctly (de) encode messages on it.
The German Bundeswehr even developed an assembly known as the EZ-KL7, which allowed two machines to work in tandem (in parallel) to detect errors. The EZ-KL7 unit was installed in front of the keyboard of one of the two KL-7 machines and constantly compared their findings. As soon as a difference was detected, an alarm was raised. Please note that the EZ-KL7 is pronounced “Easy KL-7”.
This option required the installation of the KLX-7 I / O interface.
KLX-7 I / O Interface
By itself, the KL-7 received input information only through the built-in keyboard, and displayed information in the form of printed text on 9.5 mm paper tape. To connect the KL-7 directly to the teleprinter, the KLX-7 I / O interface was available. As far as we know, the KLX-7 consisted of two parts, one of which was installed between the keyboard and the base.

All this required removing the keyboard, and a contact module was installed in its place. Later the keyboard was made removable, now it could be placed on top of the contact module. In reality, an I / O interface was installed on the rear of the machine, behind a drum with rotors.
Secret are - a drum with rotors (KLK-7 / TSEC), a stepper mechanism (KLA-7 / TSEC) and an electric circuit. All other modules of the device are free from the heading "secret". Given the age of KL-7 and the fact that more and more principles of the cryptocurrency machine are becoming understood by researchers, it is assumed that in the near future it will be fully declassified. The NSA recently released a document that describes the history of the KL-7.
Compromising facts
Over the course of its life, the KL-7 was at risk several times. It is believed that in the Soviet Union they were able to intercept and decrypt KL-7 messages.

The most famous story is the story of John Anthony Walker, born in 1937, who worked in the U.S. Navy and successfully spied on the side of the USSR for almost 17 years. Walker joined the U.S. Navy in 1955 and became a Soviet spy since December 1967, explaining all the financial difficulties in life. From that moment, until his retirement from the Navy (1983), he provided the USSR with key lists and other critical encryption materials KL-47, KW-7 and other crypto machines.
For the information he received, he received several thousand dollars every month. In 1969, he began to seek help in his espionage business and made friends with Jerry Whitworth, a student who later became a senior naval officer. In 1973, Anthony was able to enlist his help. In 1984, the circle of his spies was replenished with new members - older brother Arthur and son Michael. Walker also tried to attract his daughter, a newly-made officer in the US Army, but she dropped out of the “game”, becoming pregnant and giving up her military career.
In 1976, Walker and his wife Barbara divorced due to beatings and alcohol abuse by Walker. Walker refused to pay child support (1985) and Barbara handed him over to the FBI, which ultimately led to his arrest. After his arrest, Walker partnered with the authorities and entered into a plea bargain to lower his sentence to his son Michael. Suffering from diabetes and throat cancer, John Walker died in prison on August 28, 2014. His son Michael was released on parole in February 2000.
Information transmitted by John Walker and his espionage group allowed the USSR to build an analogue of the KL-7. As a result, at least a million secret messages (TOP SECRET) were decrypted. The KL-7 analogue was even equipped with a small device called a rotary reader, which made it easy to trace the internal wiring of each rotor.

In the photo above - the device itself, though it was confiscated by the FBI. Small enough so that it can be imperceptibly carried and easily hidden in your pocket. When folding, its dimensions were 7.5 x 10 cm (such as a pack of cigarettes).
Lost in Vietnam
The KL-7 was once again compromised in its history. Here is how it was. During the Vietnam War (1970), the Americans decided to provide the Republic of Vietnam (RVN) with a limited amount of cryptographic equipment: M-209 and KL-7 encryption machines, various One-Time Pad (OTP) systems, voice authentication codes and NESTOR ( KY-8).
After the withdrawal of US troops from Vietnam, the base with cryptographic equipment and the American employees in charge of this equipment, known as Don Vi '600, remained in place. In late 1974 and early 1975, the situation worsened, and the Americans began to recall part of the equipment with the intention of sending it back to CONUS or Hawaii.
In January - February, the situation became critical, it was decided to immediately remove the equipment from Don Vi '600 and forward it to CONUS. In three weeks, about 700 pieces of ADONIS and NESTOR equipment were prepared for shipment to CONUS, but, unfortunately, none of these devices were sent or destroyed on time. In the end, the equipment fell into the hands of North Vietnam.
It is likely that the North Vietnamese eventually sold some cars to the USSR and the Chinese, along with key materials (received over 12 months) and One-Time Pad (OTP) systems.

The National Museum of Cryptography (created by the NSA) has become home to many exhibits that lift the veil of secrecy and fill the gaps in the history of cryptography from the time of the War of Independence to the present day.
The source was the amazing work of the Cypto Museum .
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analog entry-level server that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4 RAM).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read aboutHow to build an infrastructure class c using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
