Bitfury Crystal: how it works and where our tool is used to track suspicious crypto transactions
Today we will talk about Bitfury Crystal , a platform that analyzes Bitcoin and Bitcoin Cash blockchains and allows you to detect suspicious cryptocurrency transactions. Consider the tools used by the system, and the principles of their work.
/ Bitfury Crystal
A blockchain is an open network, so any of its members can study transaction history and set amounts sent between addresses. But to know the owner of a wallet is very problematic, since the network is anonymous. For this reason, attackers are actively using cryptocurrency for money laundering, extortion or blackmail. According to Europol , it is cryptocurrency operations that are becoming more and more popular for conducting illegal transactions.
Our team has developed a set of tools for the most complete analysis of the blockchain. Crystal groups addresses that belong to the same owner, and gives a risk assessment (what is the chance that they are related to illegal activities). Also, the service allows you to trace the movement of bitcoins to a specific address or after a certain transaction.
In general, the Crystal platform can be viewed as a combination of the following tools: clustering, risk assessment, visualization, interaction, and tracking. Their consistent application allows us to identify the connection of a cryptocurrency wallet or payment with illegal or “doubtful” activity and provide evidence of such a connection. Let's tell what tasks each of these tools solves.
To determine if the wallet is related to suspicious activity, Crystal groups the addresses on the blockchain belonging to the same owner. That is, solves the problem of clustering. Crystal clustering most commonly uses two heuristics: total spending heuristics and change heuristics .
In the first case, addresses are grouped, which are separate entries of a single transaction. Since different addresses send funds in the same transaction and have access to each other’s private keys, it can be assumed that these addresses have a common owner.
But this rule is not true for all cases. For example, the CoinJoin method allows you to combine inputs from different senders in a single transaction to anonymize it. In this case, it becomes more difficult to establish the exact distribution of funds “in tandem”.
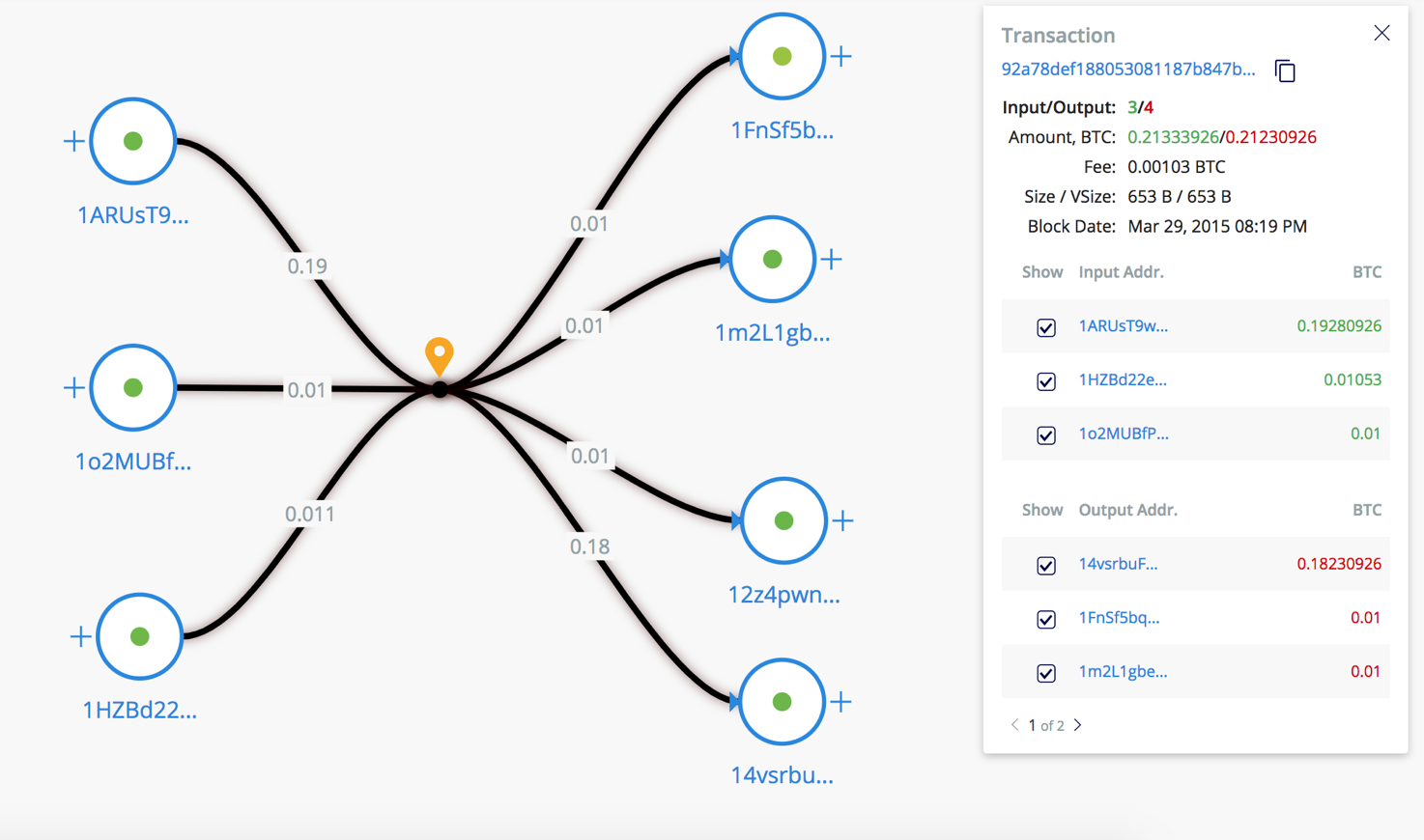
/ Example Coinjoin Transactions on our Visualization
This condition imposes a number of restrictions on the clustering algorithm. To expand the capabilities of the system, additional heuristics are used - change heuristics.
The sum of all inputs for the current transaction should be used at its outputs, otherwise, the remaining funds become the miner's commission. For this reason, a new exit address is often generated, to which the sender will receive the change. The heuristic of delivery allows you to identify such addresses and add them to the sender's cluster.
After clustering, Crystal analytics are included in the work, which, based on information about the object found in the sources available to them, determine the owner of the cluster.
Special algorithms estimate the likelihood of wallets associating with potentially harmful activities. The Risk Assessment module provides additional information about unlabelled clusters (including single addresses) based on their interaction with labeled clusters. Additional information means the risk level of a group of addresses, depending on whether they belong to any type of activity ( darkmarket, malware, miner, etc. ).
The module “Risk Assessment” uses the label propagation method , which refers to a type of training with partial involvement of a teacher ( semi-supervised learning). The label distribution method is used to classify objects that have a graph structure. In this graph, a subset of vertices is labeled into classes (the number of labeled vertices is much less than the unmarked vertices). In our case, vertices denote clusters, and edges - interactions between them. The edge weight corresponds to the number of transferred funds between addresses.
Thanks to the visualization tool, the Crystal user can, in a short period of time, construct a flow chart of all known transactions in the form of a graph. Moreover, the graph will have a minimum number of intersections of the edges for better visualization.
Usually, when drawing graphs, force-directed algorithms are used (they are called the graph-drawing power algorithm). In this case, a system of attraction and repulsion forces acting between the vertices and the edges of the graph is specified. Then there is a position in which the system has the lowest energy level (local minimum).
This approach has many problems, one of which is a local minimum of intersections instead of a global one. For this reason, we decided to write our own rendering algorithm. In the figure below you can see an example of visualization, namely the withdrawal of funds from WannaCry addresses.
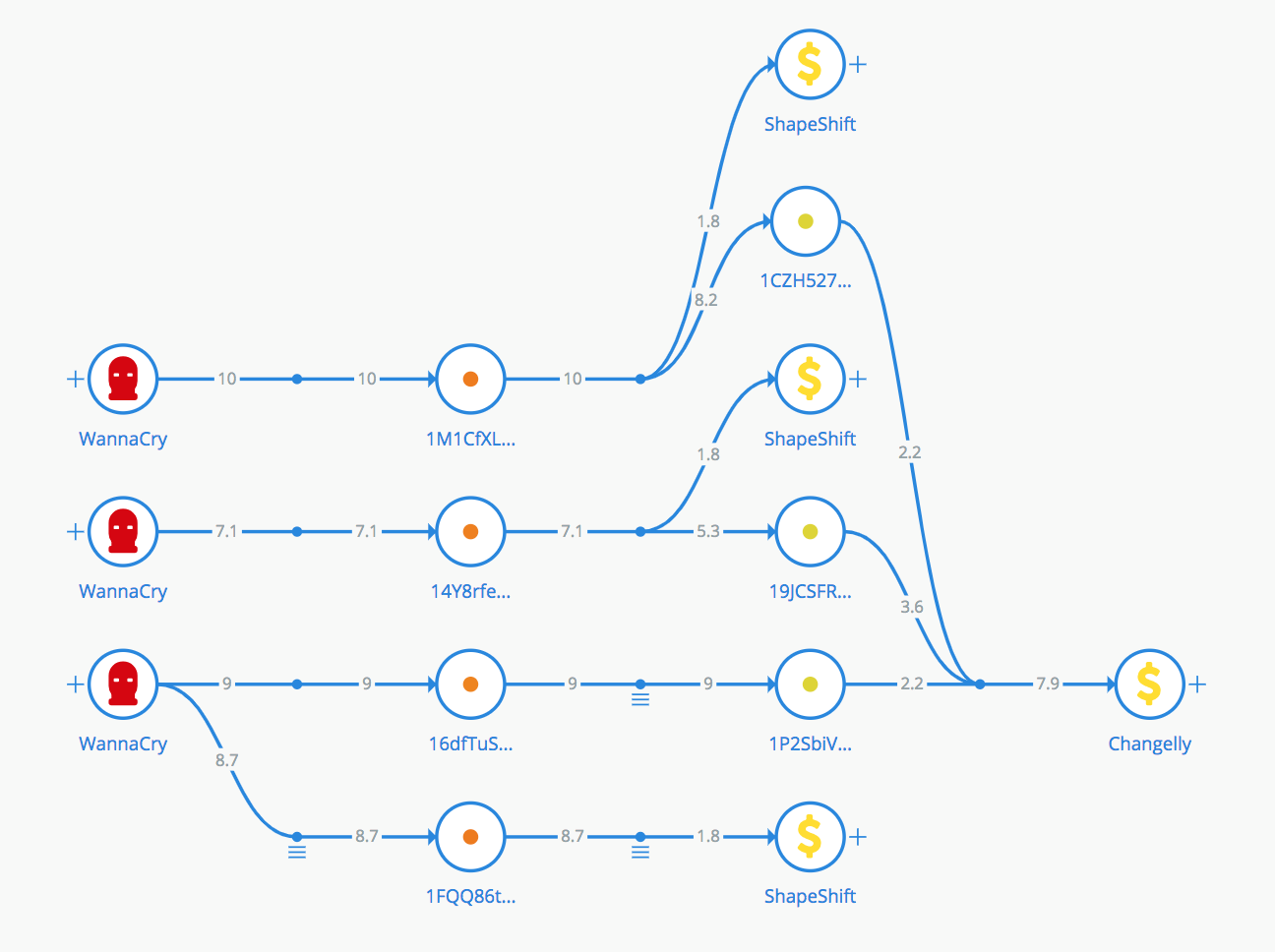
/ sample visualization of WannaCry withdrawals
It helps to find all the direct transactions between the two clusters and study them in detail. Also, the function draws graphics that allow you to assess the intensity of the interaction of the owners of addresses depending on time.
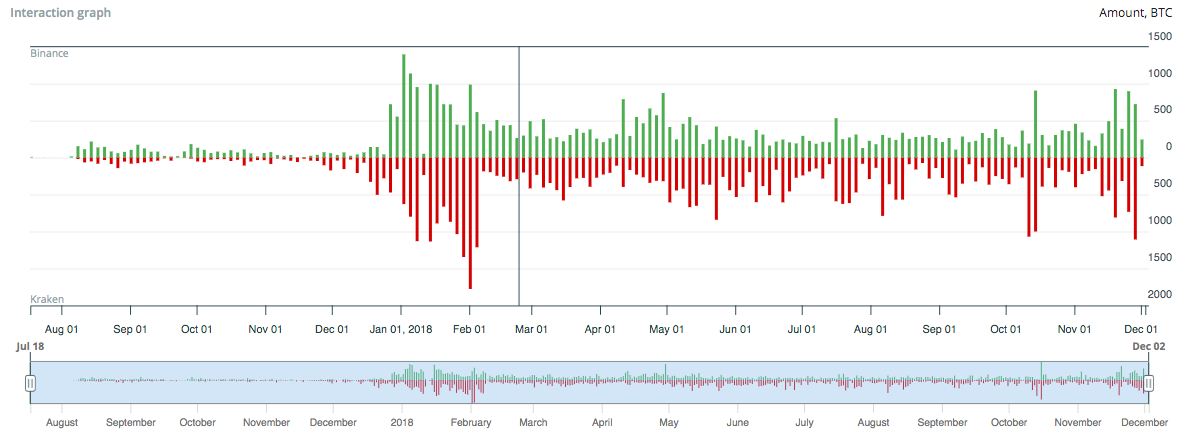
/ example of the interaction of cryptocurrency exchanges Binance and Kraken.
Our Crystal team has developed a tool that automatically tracks the flow of cryptocurrency that participated in a user-defined set of transactions. This allows, for example, to locate the stolen money or the organization through which it was withdrawn.
When you try to track such a movement manually, researchers usually face the problem of large branching: money is divided into small parts, converge on addresses, again divided. In addition, coins from other sources can be added to stolen money, since a single transaction can contain multiple entries.
The result of the tracking of Crystal is a list of cryptocurrency addresses to which the money reached, as well as the definition of all delivery routes. From this data, you can automatically build a visualization. For example, the figure below shows the “route” of withdrawal of funds by hackers from the Zaif exchange.
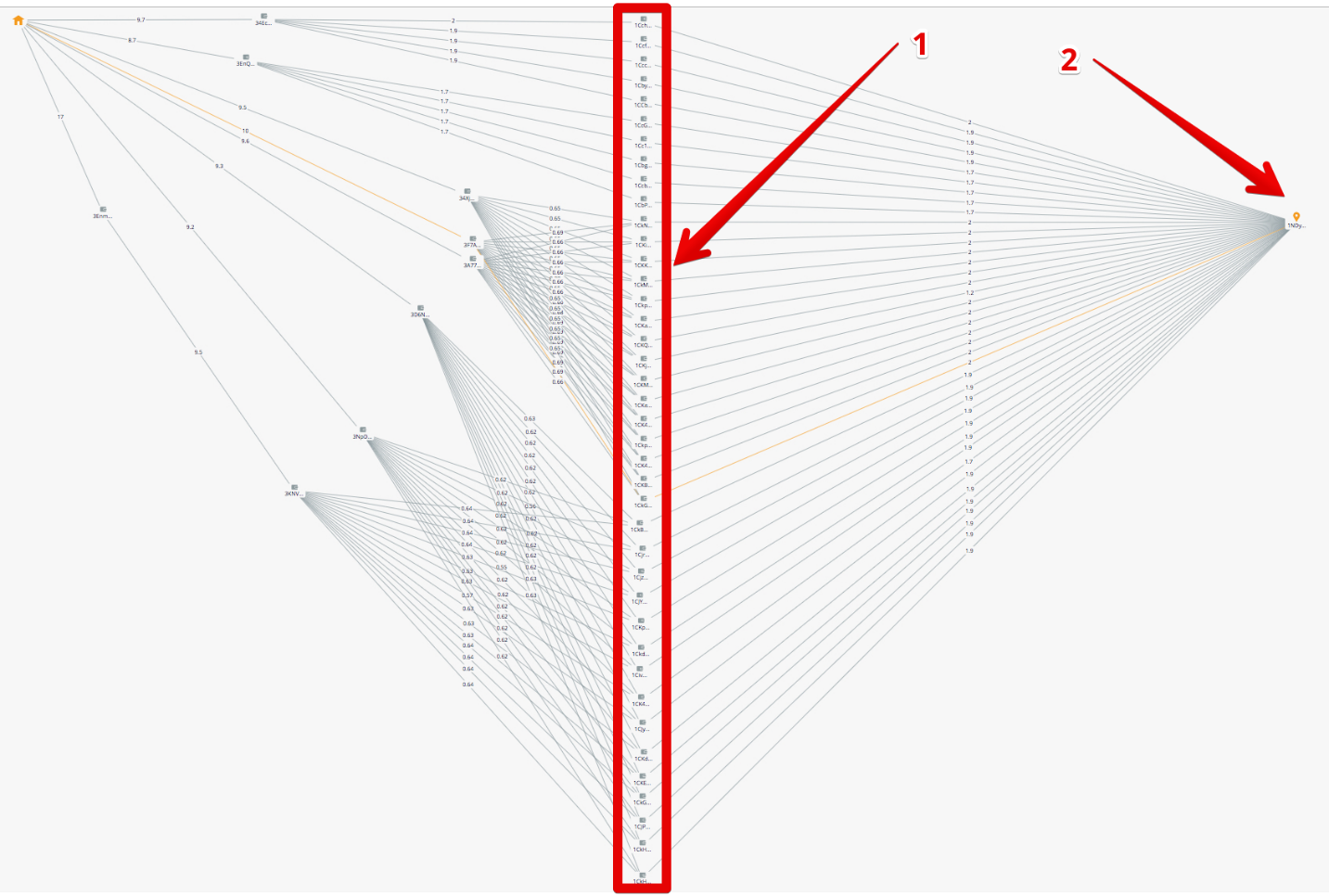
/ Transfer means for the exchange hacker Binance
Attackers cryptocurrency converted from addresses in the exchange transaction c3b9a4a0831a65523c81e6a04f6ddf5a7a89f344d990e8a13e5278efe57f4280 . The money was collected at 1FmwHh6pgkf4meCMoqo8fHH3GNRF571f9w , and we investigated the flow of funds associated with this address.
As a result, it turned out that some of the funds were sold on accounts on stock exchanges, such as Binance, Bitstamp and Livecoin. And some of the funds went to the mixers, for example ChipMixer.com.
The entire course of the investigation is described in detail in our blog on Medium .
Using the tools described above, Crystal allows organizations that accept bitcoins to determine the origin of funds and their connection to illegal activity (Risk Assessment). If the information received is not enough, organizations can conduct a deeper investigation using the tools "Visualization" and "Interaction".
Crystal also allows you to investigate cases of theft of cryptocurrency. The function "Tracking" allows you to get a list of all addresses and organizations through which the stolen money was spent. After the system in a visual form displays how they got there. Then with this data the user can contact the identified organizations with a request to freeze the funds.
The Crystal tools listed are the result of the development of the Bitfury team of professionals, which is not going to stop there. The Crystal platform is already used in Asia, the United States, Europe and the CIS by both financial institutions and law enforcement agencies. Crystal Short Video:
For cooperation please contact: contact@crystalblockchain.com

/ Bitfury Crystal
Why do you need such a system
A blockchain is an open network, so any of its members can study transaction history and set amounts sent between addresses. But to know the owner of a wallet is very problematic, since the network is anonymous. For this reason, attackers are actively using cryptocurrency for money laundering, extortion or blackmail. According to Europol , it is cryptocurrency operations that are becoming more and more popular for conducting illegal transactions.
Our team has developed a set of tools for the most complete analysis of the blockchain. Crystal groups addresses that belong to the same owner, and gives a risk assessment (what is the chance that they are related to illegal activities). Also, the service allows you to trace the movement of bitcoins to a specific address or after a certain transaction.
Crystal Tools
In general, the Crystal platform can be viewed as a combination of the following tools: clustering, risk assessment, visualization, interaction, and tracking. Their consistent application allows us to identify the connection of a cryptocurrency wallet or payment with illegal or “doubtful” activity and provide evidence of such a connection. Let's tell what tasks each of these tools solves.
Clustering
To determine if the wallet is related to suspicious activity, Crystal groups the addresses on the blockchain belonging to the same owner. That is, solves the problem of clustering. Crystal clustering most commonly uses two heuristics: total spending heuristics and change heuristics .
In the first case, addresses are grouped, which are separate entries of a single transaction. Since different addresses send funds in the same transaction and have access to each other’s private keys, it can be assumed that these addresses have a common owner.
What is a transaction entry and exit?
Все транзакции биткоин-блокчейна имеют один или несколько входов и выходов. Входы новой транзакции ссылаются на выходы предыдущей транзакции и предоставляют данные для передачи средств.
Подробно о механизме работы транзакций мы писали в одном из наших прошлых материалов.
Подробно о механизме работы транзакций мы писали в одном из наших прошлых материалов.
But this rule is not true for all cases. For example, the CoinJoin method allows you to combine inputs from different senders in a single transaction to anonymize it. In this case, it becomes more difficult to establish the exact distribution of funds “in tandem”.

/ Example Coinjoin Transactions on our Visualization
This condition imposes a number of restrictions on the clustering algorithm. To expand the capabilities of the system, additional heuristics are used - change heuristics.
The sum of all inputs for the current transaction should be used at its outputs, otherwise, the remaining funds become the miner's commission. For this reason, a new exit address is often generated, to which the sender will receive the change. The heuristic of delivery allows you to identify such addresses and add them to the sender's cluster.
After clustering, Crystal analytics are included in the work, which, based on information about the object found in the sources available to them, determine the owner of the cluster.
Risk assessment
Special algorithms estimate the likelihood of wallets associating with potentially harmful activities. The Risk Assessment module provides additional information about unlabelled clusters (including single addresses) based on their interaction with labeled clusters. Additional information means the risk level of a group of addresses, depending on whether they belong to any type of activity ( darkmarket, malware, miner, etc. ).
The module “Risk Assessment” uses the label propagation method , which refers to a type of training with partial involvement of a teacher ( semi-supervised learning). The label distribution method is used to classify objects that have a graph structure. In this graph, a subset of vertices is labeled into classes (the number of labeled vertices is much less than the unmarked vertices). In our case, vertices denote clusters, and edges - interactions between them. The edge weight corresponds to the number of transferred funds between addresses.
Visualization
Thanks to the visualization tool, the Crystal user can, in a short period of time, construct a flow chart of all known transactions in the form of a graph. Moreover, the graph will have a minimum number of intersections of the edges for better visualization.
Usually, when drawing graphs, force-directed algorithms are used (they are called the graph-drawing power algorithm). In this case, a system of attraction and repulsion forces acting between the vertices and the edges of the graph is specified. Then there is a position in which the system has the lowest energy level (local minimum).
This approach has many problems, one of which is a local minimum of intersections instead of a global one. For this reason, we decided to write our own rendering algorithm. In the figure below you can see an example of visualization, namely the withdrawal of funds from WannaCry addresses.

/ sample visualization of WannaCry withdrawals
Interaction
It helps to find all the direct transactions between the two clusters and study them in detail. Also, the function draws graphics that allow you to assess the intensity of the interaction of the owners of addresses depending on time.

/ example of the interaction of cryptocurrency exchanges Binance and Kraken.
Tracking
Our Crystal team has developed a tool that automatically tracks the flow of cryptocurrency that participated in a user-defined set of transactions. This allows, for example, to locate the stolen money or the organization through which it was withdrawn.
When you try to track such a movement manually, researchers usually face the problem of large branching: money is divided into small parts, converge on addresses, again divided. In addition, coins from other sources can be added to stolen money, since a single transaction can contain multiple entries.
The result of the tracking of Crystal is a list of cryptocurrency addresses to which the money reached, as well as the definition of all delivery routes. From this data, you can automatically build a visualization. For example, the figure below shows the “route” of withdrawal of funds by hackers from the Zaif exchange.

/ Transfer means for the exchange hacker Binance
Attackers cryptocurrency converted from addresses in the exchange transaction c3b9a4a0831a65523c81e6a04f6ddf5a7a89f344d990e8a13e5278efe57f4280 . The money was collected at 1FmwHh6pgkf4meCMoqo8fHH3GNRF571f9w , and we investigated the flow of funds associated with this address.
As a result, it turned out that some of the funds were sold on accounts on stock exchanges, such as Binance, Bitstamp and Livecoin. And some of the funds went to the mixers, for example ChipMixer.com.
The entire course of the investigation is described in detail in our blog on Medium .
Where is Crystal used
Using the tools described above, Crystal allows organizations that accept bitcoins to determine the origin of funds and their connection to illegal activity (Risk Assessment). If the information received is not enough, organizations can conduct a deeper investigation using the tools "Visualization" and "Interaction".
Crystal also allows you to investigate cases of theft of cryptocurrency. The function "Tracking" allows you to get a list of all addresses and organizations through which the stolen money was spent. After the system in a visual form displays how they got there. Then with this data the user can contact the identified organizations with a request to freeze the funds.
The Crystal tools listed are the result of the development of the Bitfury team of professionals, which is not going to stop there. The Crystal platform is already used in Asia, the United States, Europe and the CIS by both financial institutions and law enforcement agencies. Crystal Short Video:
For cooperation please contact: contact@crystalblockchain.com
