BLACK HAT conference. How to make a spy phone. Part 2
- Transfer
BLACK HAT conference. How to make a spy phone. Part 1
The next thing we need to modify is the manifest. This thing that says which services are involved in the operation of the application, what permissions they have, and so on.
So, we will start with the code itself, and exactly with the code of the smali directory. If you look at the Angry Birds directory tree, you will see a lot of folders containing various components, arranged in subdirectories.
I don’t even know which of these things I really need and what they do, but I don’t need it. Now I will do a technical thing of tremendous complexity - copy the droidwhisperer directory from here, from the SearchableDictionary directory, here, to the com / burstly / example / android sub-directory of the smali directory. That's all, I hope you understand what's the point.
So, a copy of our code is inserted where necessary, but there are a few more things that need to be done. I look again at my list of cheats and see that now it is necessary to make changes to the manifest. First of all, when we take up the manifest, we need to know the name of the application - I will highlight it in red, later we will need it, because we inserted something into the existing code.
So, updating the manifest is needed to enable the integrated spyware service and its permissions. It consists of the following steps:
- memorizing the name of the original application for later,
- defining the Droidwhisperer service
- defining the permissions necessary for the Droidwhisperer to work.

Therefore, I take this manifest and drag it to my notebook. The first thing I do in the application, it defines our service. To do this, I find the onCreate function in the manifest in the main action of the target application. In the case of Angry Birds, it was com / rovio / ka3d / App. After that, I cut out a part of the code highlighted in yellow, and place it immediately after invit-super in onCreate.
Thus, we specified in the manifest that we will have the Droidwhisperer service, which should start immediately after it becomes available. That's why we needed the name of the original application com.rovio.ka3d.App, we use it to enter the new name of our application com.rovio.ka3d. service.Droidwhisperer.
Next, I copy and paste the permissions for our spyware application into the appropriate place in the manifest - these are the lines highlighted in green.

After making changes, we save the manifest, which already includes the permissions we need and a service is defined that needs to be started when the phone boots, so that's all right.
Something is needed in Android that launches applications, so the Angry Birds application should contain code that will start my spy service as soon as the original game is launched. Now I go to the game directory and find the ka3d folder there, open it and copy the App file contained there into a notebook. This is smali code, which is a Dalvik version of the assembler code. We use the onCreate feature in Android. I use the notepad search to find the location of this function. Here, you need a little knowledge of how the Android OS works - so, the onCreate function is used to call super-classes, that is, to create or restart application activity. It is here that I insert my code, which should initiate the launch of a spyware service. I'm going back to my cheat sheet
How do I know which code needs to be inserted here? I just copied it from the original application that I wrote. I said that there is excellent documentation for smali, so you don’t need to go into all that much to do this.

Just recently some "binding" sets were announced that allow you to automate the receipt of the necessary code. Just a few weeks ago, such Android developer toolkits were released, allowing you to create any service and implement it into an existing application. All this can be done manually.
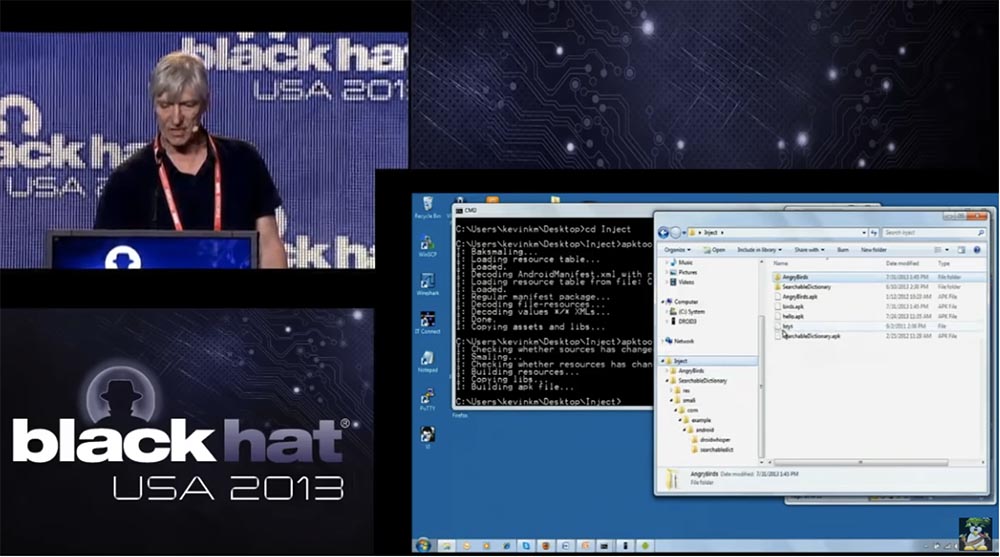
So, as soon as the onCreate function is called, it activates our service. Do not forget that after this you need to save the modified file. So, after we had the appropriate technical training, we need to build our modified application. Therefore, I return to Apk_tool and collect parts from the Angry Birds directory in the birds.apk directory. So, we rebuilt the original application, making the necessary changes to it, and placed a new assembly in a file called birds.apk.
If you try to install this modified application on the Android phone right now, he will say that this application is not signed, so we need to sign it. To do this, I create a self-signed digital certificate with the corresponding public key, and save it in my inject working directory. This is a file called keys.
This is just a certificate that I create myself. Now I’ll go back and take this powerful and laconic command from my cheat sheet:
jarsigner -verbose -keystore keys birds.apk alias_name
In order not to confuse anything, I just cut it out and paste it in the right place. So I'm going to sign the birds.apk file with my own key, it's pretty simple. Then I give the command and sign all the components of the application with this digital key. Now I can place it in the AppStore, on Google Play - anywhere.
As I already said, there is no interface on the phone that shows the user who signed what. Once the application is signed, it can be installed. No one can tell who signed this app, and this is just great.
So, the modified version of Angry Birds looks exactly the same as the original game and functions the same way, except for the fact that it contains my spyware code. Now you can see on the screen digital signatures made by Kevin McName of Kindsite.
Another interesting thing that I will show you, returning a little back. Look at the original application - it is signed by Rovio Mobile Ltd, Look at the date of signature - this digital certificate is valid until August 26, 2010, but the application is installed on the phone without question. Thus, even if your digital certificate has turned into garbage, it still gives the right to install the application, that is, no one checks it. I think this is one of the things that is one of the serious flaws of the Android security model.
The fact is that there is no strict verification of the digital certificates used. This problem can be solved by committing to register those who want to get a digital certificate. So back to our presentation. I want to once again focus on digital signatures.

All applications must be signed. Any old signature remains valid if it is self-signed. The presence of a signature is checked only when installing the application. That is, I can change any .apk file already installed in the phone, and the system will not react to it in any way. This is a pretty significant vulnerability. If you want to change the .apk file in your phone, you must have access to change the directories in which such files are stored, but it is easy to get root-rights to do anything with the phone.
The second thing that worries me is that there is no user interface that shows who signed the application. For example, when installing the application should appear the inscription that it was signed by Kevin McName of Kindsite. I note that the signature must match for the moved or updated existing application, so I could not replace the existing version of Angry Birds if I did not change the name of my spyware. But as soon as I did, no problems arose. The developers of Android claim that the certificate does not need to be signed by an authorized center, and Android applications mainly use self-signed signatures.
Before starting to answer questions, I want to say that there is a whole industry of spyware for phones. They are designed to monitor your loved ones or your children, or business partners.

Previously, they were used to spy on the wrong spouses, but now their purpose has changed. For example, you can monitor your children to ensure their safety, and this is completely legal. But I think more spy phones are suitable for use in the BYOD system. You can add any functionality to the spy module and insert it into any application, and the user will not know anything about it. This is ideally suited for industrial espionage, so these devices expand the scope of ongoing security threats.
So, this is a fully functional network device, and if I connect to Wi-Fi at work, I can install software on this phone that will scan the networks for vulnerabilities. At the same time, if necessary, it will be updated and send the stolen information to the command & control site. That is, the infected mobile phone is an extended platform of persistent security threats with great potential for attack. For example, someone just walks inside the building with such a phone, scans the network, and then attacks them from the inside. Of course, people protect their Internet connection through firewalls and similar firewalls, but this device communicates with networks directly through the air, the spy phone connects to the network in any place where there is an access point, and no firewall can help here. As a matter of fact, phones come into the network through the "back door". Spy phone is pretty cool, but here we have a remote-access trojan, and I think it's pretty dangerous.
I think I said everything I wanted to say, and now I am ready to answer any questions.
So, the first question is whether this particular application is trying to hide its presence. I answer - no, it is not, because if you view the services running on the phone, you will see it there. I think it could be made a hidden process, but in this case our “spy phone” was created just to demonstrate the concept of threat.
Can our application be detected by an antivirus program? No, the antivirus does not detect this spyware module, because it does not know anything about it. It would be possible to further confuse the code and then insert it into the application, and such a process can be automated.
What can oppose such a spy application? You can use an antivirus, which in any case detects known malicious applications, but we focused on the traffic sent to the command & control site. Probably, it would be possible to automate the process of code obfuscation, but it is very difficult to change the communication protocol with the command & control server on the fly, you will need to change the server itself, change clients and so on. Therefore, we recommend combining both methods of protection: antivirus against known malicious applications and monitoring of network traffic sent by the spy device to the command & control site.
I will answer the question what does the requirement of digital signatures coincide with when moving or updating an application. If you are installing the application on your phone for the first time, then you will not have any problems with it. But if the phone already has the original application and you want to replace it with a new copy with a different digital signature, or a modified application with the same name, you will fail, because the phone will be able to compare the original signature in the application with its modified version and note, that they do not match. In this case, I bypassed the protection by simply replacing the original name of the application with another name.
The command & control server can interact with all Android functionality and use its API. You can remotely get root access, download files to your phone, and generally manage them at your discretion, because Android provides ample opportunities for open access to the phone over the network. I think that the same functionality is available on the iOS platform, just the developers of this OS are more serious about checking the security of new applications. For example, you should receive a certificate from them certifying your identity as an application developer, and the application itself will be checked before it enters their App Store, while Google checks the application after it is placed on the Play Market.
I’m not familiar with the details of the Google Play app store, but I think that if a developer has a bad reputation or the application is compromised, it will not appear in the store. However, there are many other online mobile app stores where an attacker can host a malicious application. This is a type of phishing attack, when we force the user to download this application from anywhere, slipping him links.
The fact is that all the functions in our spyware application look as usual, there is nothing illegal that this application would try to do. When installing, it requires giving it the same permissions as legal applications. Another thing is how these functions will be used later. Of course, if someone reports that droidwhisperer is a virus, then any antivirus installed on the phone will not allow installation of the application that contains it.
As I said before, the spyware application can be downloaded from third-party sites. In this case, the phishing attack is that you will be given detailed installation instructions and will offer to download this game for free, because this is such a cool game, and you do not need to pay for it by downloading the original in the Google store. Usually the user is lured by such an offer.
I note that we did not aim to penetrate networks protected by encryption, but simply connected to any available network. Thank you for attention!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
The next thing we need to modify is the manifest. This thing that says which services are involved in the operation of the application, what permissions they have, and so on.
So, we will start with the code itself, and exactly with the code of the smali directory. If you look at the Angry Birds directory tree, you will see a lot of folders containing various components, arranged in subdirectories.

I don’t even know which of these things I really need and what they do, but I don’t need it. Now I will do a technical thing of tremendous complexity - copy the droidwhisperer directory from here, from the SearchableDictionary directory, here, to the com / burstly / example / android sub-directory of the smali directory. That's all, I hope you understand what's the point.
So, a copy of our code is inserted where necessary, but there are a few more things that need to be done. I look again at my list of cheats and see that now it is necessary to make changes to the manifest. First of all, when we take up the manifest, we need to know the name of the application - I will highlight it in red, later we will need it, because we inserted something into the existing code.
So, updating the manifest is needed to enable the integrated spyware service and its permissions. It consists of the following steps:
- memorizing the name of the original application for later,
- defining the Droidwhisperer service
- defining the permissions necessary for the Droidwhisperer to work.

Therefore, I take this manifest and drag it to my notebook. The first thing I do in the application, it defines our service. To do this, I find the onCreate function in the manifest in the main action of the target application. In the case of Angry Birds, it was com / rovio / ka3d / App. After that, I cut out a part of the code highlighted in yellow, and place it immediately after invit-super in onCreate.
Thus, we specified in the manifest that we will have the Droidwhisperer service, which should start immediately after it becomes available. That's why we needed the name of the original application com.rovio.ka3d.App, we use it to enter the new name of our application com.rovio.ka3d. service.Droidwhisperer.
Next, I copy and paste the permissions for our spyware application into the appropriate place in the manifest - these are the lines highlighted in green.

After making changes, we save the manifest, which already includes the permissions we need and a service is defined that needs to be started when the phone boots, so that's all right.
Something is needed in Android that launches applications, so the Angry Birds application should contain code that will start my spy service as soon as the original game is launched. Now I go to the game directory and find the ka3d folder there, open it and copy the App file contained there into a notebook. This is smali code, which is a Dalvik version of the assembler code. We use the onCreate feature in Android. I use the notepad search to find the location of this function. Here, you need a little knowledge of how the Android OS works - so, the onCreate function is used to call super-classes, that is, to create or restart application activity. It is here that I insert my code, which should initiate the launch of a spyware service. I'm going back to my cheat sheet
How do I know which code needs to be inserted here? I just copied it from the original application that I wrote. I said that there is excellent documentation for smali, so you don’t need to go into all that much to do this.

Just recently some "binding" sets were announced that allow you to automate the receipt of the necessary code. Just a few weeks ago, such Android developer toolkits were released, allowing you to create any service and implement it into an existing application. All this can be done manually.
So, as soon as the onCreate function is called, it activates our service. Do not forget that after this you need to save the modified file. So, after we had the appropriate technical training, we need to build our modified application. Therefore, I return to Apk_tool and collect parts from the Angry Birds directory in the birds.apk directory. So, we rebuilt the original application, making the necessary changes to it, and placed a new assembly in a file called birds.apk.
If you try to install this modified application on the Android phone right now, he will say that this application is not signed, so we need to sign it. To do this, I create a self-signed digital certificate with the corresponding public key, and save it in my inject working directory. This is a file called keys.

This is just a certificate that I create myself. Now I’ll go back and take this powerful and laconic command from my cheat sheet:
jarsigner -verbose -keystore keys birds.apk alias_name
In order not to confuse anything, I just cut it out and paste it in the right place. So I'm going to sign the birds.apk file with my own key, it's pretty simple. Then I give the command and sign all the components of the application with this digital key. Now I can place it in the AppStore, on Google Play - anywhere.
As I already said, there is no interface on the phone that shows the user who signed what. Once the application is signed, it can be installed. No one can tell who signed this app, and this is just great.
So, the modified version of Angry Birds looks exactly the same as the original game and functions the same way, except for the fact that it contains my spyware code. Now you can see on the screen digital signatures made by Kevin McName of Kindsite.
Another interesting thing that I will show you, returning a little back. Look at the original application - it is signed by Rovio Mobile Ltd, Look at the date of signature - this digital certificate is valid until August 26, 2010, but the application is installed on the phone without question. Thus, even if your digital certificate has turned into garbage, it still gives the right to install the application, that is, no one checks it. I think this is one of the things that is one of the serious flaws of the Android security model.
The fact is that there is no strict verification of the digital certificates used. This problem can be solved by committing to register those who want to get a digital certificate. So back to our presentation. I want to once again focus on digital signatures.

All applications must be signed. Any old signature remains valid if it is self-signed. The presence of a signature is checked only when installing the application. That is, I can change any .apk file already installed in the phone, and the system will not react to it in any way. This is a pretty significant vulnerability. If you want to change the .apk file in your phone, you must have access to change the directories in which such files are stored, but it is easy to get root-rights to do anything with the phone.
The second thing that worries me is that there is no user interface that shows who signed the application. For example, when installing the application should appear the inscription that it was signed by Kevin McName of Kindsite. I note that the signature must match for the moved or updated existing application, so I could not replace the existing version of Angry Birds if I did not change the name of my spyware. But as soon as I did, no problems arose. The developers of Android claim that the certificate does not need to be signed by an authorized center, and Android applications mainly use self-signed signatures.
Before starting to answer questions, I want to say that there is a whole industry of spyware for phones. They are designed to monitor your loved ones or your children, or business partners.

Previously, they were used to spy on the wrong spouses, but now their purpose has changed. For example, you can monitor your children to ensure their safety, and this is completely legal. But I think more spy phones are suitable for use in the BYOD system. You can add any functionality to the spy module and insert it into any application, and the user will not know anything about it. This is ideally suited for industrial espionage, so these devices expand the scope of ongoing security threats.
So, this is a fully functional network device, and if I connect to Wi-Fi at work, I can install software on this phone that will scan the networks for vulnerabilities. At the same time, if necessary, it will be updated and send the stolen information to the command & control site. That is, the infected mobile phone is an extended platform of persistent security threats with great potential for attack. For example, someone just walks inside the building with such a phone, scans the network, and then attacks them from the inside. Of course, people protect their Internet connection through firewalls and similar firewalls, but this device communicates with networks directly through the air, the spy phone connects to the network in any place where there is an access point, and no firewall can help here. As a matter of fact, phones come into the network through the "back door". Spy phone is pretty cool, but here we have a remote-access trojan, and I think it's pretty dangerous.
I think I said everything I wanted to say, and now I am ready to answer any questions.
So, the first question is whether this particular application is trying to hide its presence. I answer - no, it is not, because if you view the services running on the phone, you will see it there. I think it could be made a hidden process, but in this case our “spy phone” was created just to demonstrate the concept of threat.
Can our application be detected by an antivirus program? No, the antivirus does not detect this spyware module, because it does not know anything about it. It would be possible to further confuse the code and then insert it into the application, and such a process can be automated.
What can oppose such a spy application? You can use an antivirus, which in any case detects known malicious applications, but we focused on the traffic sent to the command & control site. Probably, it would be possible to automate the process of code obfuscation, but it is very difficult to change the communication protocol with the command & control server on the fly, you will need to change the server itself, change clients and so on. Therefore, we recommend combining both methods of protection: antivirus against known malicious applications and monitoring of network traffic sent by the spy device to the command & control site.

I will answer the question what does the requirement of digital signatures coincide with when moving or updating an application. If you are installing the application on your phone for the first time, then you will not have any problems with it. But if the phone already has the original application and you want to replace it with a new copy with a different digital signature, or a modified application with the same name, you will fail, because the phone will be able to compare the original signature in the application with its modified version and note, that they do not match. In this case, I bypassed the protection by simply replacing the original name of the application with another name.
The command & control server can interact with all Android functionality and use its API. You can remotely get root access, download files to your phone, and generally manage them at your discretion, because Android provides ample opportunities for open access to the phone over the network. I think that the same functionality is available on the iOS platform, just the developers of this OS are more serious about checking the security of new applications. For example, you should receive a certificate from them certifying your identity as an application developer, and the application itself will be checked before it enters their App Store, while Google checks the application after it is placed on the Play Market.
I’m not familiar with the details of the Google Play app store, but I think that if a developer has a bad reputation or the application is compromised, it will not appear in the store. However, there are many other online mobile app stores where an attacker can host a malicious application. This is a type of phishing attack, when we force the user to download this application from anywhere, slipping him links.
The fact is that all the functions in our spyware application look as usual, there is nothing illegal that this application would try to do. When installing, it requires giving it the same permissions as legal applications. Another thing is how these functions will be used later. Of course, if someone reports that droidwhisperer is a virus, then any antivirus installed on the phone will not allow installation of the application that contains it.
As I said before, the spyware application can be downloaded from third-party sites. In this case, the phishing attack is that you will be given detailed installation instructions and will offer to download this game for free, because this is such a cool game, and you do not need to pay for it by downloading the original in the Google store. Usually the user is lured by such an offer.
I note that we did not aim to penetrate networks protected by encryption, but simply connected to any available network. Thank you for attention!
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
