Configure DKIM, SPF, and DMARC in Zimbra Collaboration Suite
If you try to send a message to Gmail mail servers, you suddenly get an error like “Our system has detected that this message is 550-5.7.1 likely unsolicited mail. To reduce the amount of spam sent to Gmail, 550-5.7.1 this message has been blocked. ", This almost always means that DKIM, SFP and DMARC are not configured on your mail server. Large mail servers (Gmail, mail.ru, Yandex) require the presence of these records. Today we’ll show you how to do it in Zimbra Collaboration Suite.

DKIM (DomainKeys Identified Mail) is an e-mail authentication method based on digital signature authentication. DKIM is necessary for mail services to check the sender and protect the recipient of the letter from fraudulent mailings, which are carried out with the substitution of the sender's address.
The method involves encrypting the headers of outgoing messages with the private key of the domain, and adding the public version of the key to the DNS records of the domain, accessible to everyone. The recipient server MTA requests the public key from the sender’s DNS server to decrypt the headers of the incoming messages, and then checks whether the message is actually sent from the declared source.
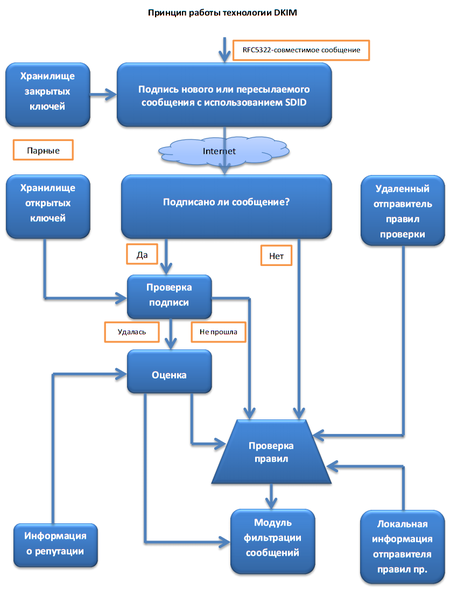
DKIM has been available since Zimbra 8.0. Signature setup consists of two steps:
Add DKIM data to a domain that does not yet have an existing DKIM configuration: Get: You can also update DKIM data for a domain: Delete DKIM data for a domain: Retrieve saved DKIM data for a domain:
You need to add the public key as a TXT record in the domain: Update the DNS, and check the result of the command: For example: If the key is retrieved, use it to make sure that the public key matches the private one. If you get an error: This means that the file /opt/zimbra/conf/opendkim.conf does not exist, you can create it with the command: If you need to revoke the DKIM signature key, set the empty "p =" tag in the TXT record. By default, a 1024-bit key is created (depending on the version of ZCS), you can change the size with the -b option.
SPF (Sender Policy Framework) - extension for the protocol for sending email via SMTP. SPF is defined in RFC 7208. An SPF record protects against forgery of your domain and allows you to prevent spam emails sent from your addresses. SPF is configured for the address used in envelope-from (SMTP envelope).

Using an spf record, the domain owner can specify the list of servers that have the right to send email messages for the domain. In general, the order is as follows:
[version] [mechanisms] [-all | ~ all | redirect]
The version is always spf1, modifiers tell who can send mail:
Parameters:
Consider the examples:
Example 1
example.com. IN TXT "v = spf1 ip4: 62.220.58.72 a mx -all"
For the example.com domain, accept letters sent from the IP address 62.220.58.72, also accept messages from the servers specified in A and MX, messages from other servers should be rejected.
Example 2
example.com. IN TXT "v = spf1 redirect: example.org"
Get the rules from the domain example.com.
Example 3
example.com. IN TXT “v = spf1 include: _spf.google.com -all”
Only receive emails from Google’s smtp servers.
Domain-based Message Authentication, Reporting and Conformance or DMARC is a technical specification created by a group of organizations to combat spammers that fake sender addresses. It is based on the identification of the sender’s mail domains based on the rules and features set on the recipient’s mail server.
Thus, the mail server decides whether the message is good or bad and acts according to the DMARC record. Thanks to the DMARC setup, domain owners can create rules for processing emails received from domains that have not been authorized.

After creating the SPF and DKIM records, you need to configure DMARC checking by adding a TXT record in the DNS (similar to SPF). Parameters may be as follows:
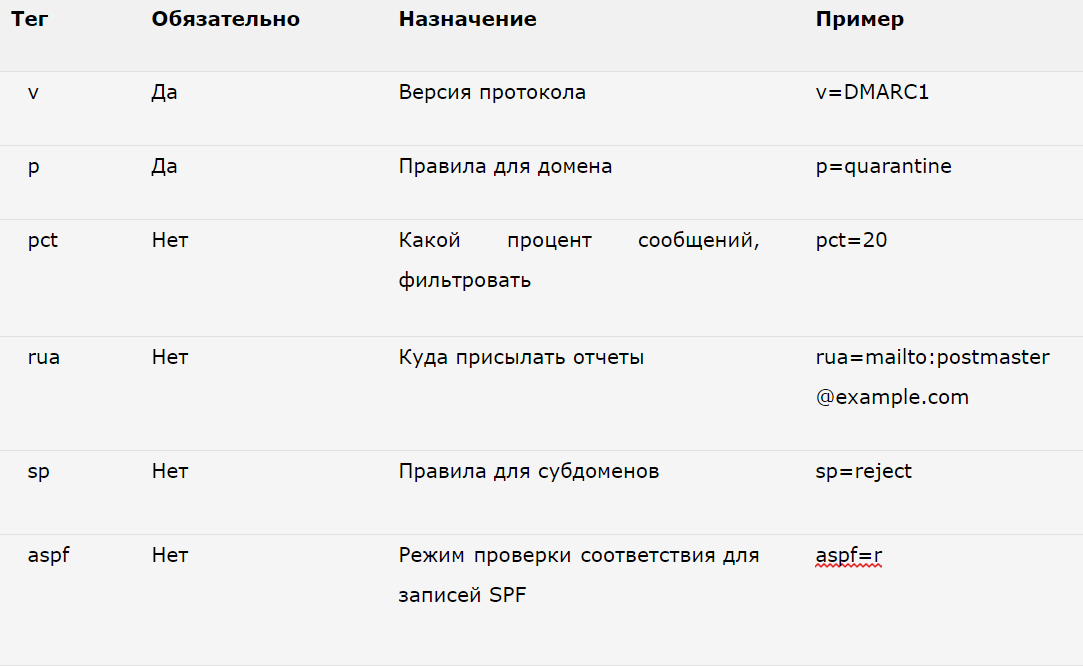
For more information, see the DMARC Tag Registry .
The rule for the domain (what to do to the recipient server if the check for spf and dkim failed) can be one of three:
If you want to receive reports, do not forget to specify the email address in the rua tag:
Below is an example of dns records for the example.com zone: For all questions related to Zextras Suite, you can contact the representative of Zextras Katerina Triandafilidi by e-mail katerina@zextras.com


Configure DKIM in Zimbra
DKIM (DomainKeys Identified Mail) is an e-mail authentication method based on digital signature authentication. DKIM is necessary for mail services to check the sender and protect the recipient of the letter from fraudulent mailings, which are carried out with the substitution of the sender's address.
The method involves encrypting the headers of outgoing messages with the private key of the domain, and adding the public version of the key to the DNS records of the domain, accessible to everyone. The recipient server MTA requests the public key from the sender’s DNS server to decrypt the headers of the incoming messages, and then checks whether the message is actually sent from the declared source.

DKIM has been available since Zimbra 8.0. Signature setup consists of two steps:
Stage one: key and selector generation
Add DKIM data to a domain that does not yet have an existing DKIM configuration: Get: You can also update DKIM data for a domain: Delete DKIM data for a domain: Retrieve saved DKIM data for a domain:
# su zimbra
$ /opt/zimbra/libexec/zmdkimkeyutil -a -d example.com
DKIM Data added to LDAP for domain example.com with selector ECAC22D2-DCA2-11E6-BA30-B554729FE32A
Public signature to enter into DNS:
ECAC22D2-DCA2-11E6-BA30-B554729FE32B._domainkey IN TXT ( "v=DKIM1; k=rsa; "
"p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAs5OCY0sX04ziF+sOHt/1kq3A7iAzAjBjb4JteaoFzu1q2uBOiQS0uyaFeY6CgSgRRbvPnq8cWLG/XMU0tM9gSGtgtWDmHOs6/+QgKp6zRmetfsyABA2Y2U+XJlVURUE5ai3KIA/njt7IGZ5yeFsdZIKmhOCAOPGCovq10xkZXHdjRwiqxbCYGXv2m3o74BcWtOLPfEvexD5PYx"
"aTWFbelJpGlDN7WdBCE+ObpLGkJ9co/1sVOcd3c9SHfPq3jcBAFm7oPX2ak7Fb7cslVK77lA2hBgMYqI2Sh+T64o6R33dU++Ej7CuImmv7PAqVUn5MjYr05t3LK9dwWM8Cm6aJ/QIDAQAA" ) ; ----- DKIM key ECAC22D2-DCA2-11E6-BA30-B554729FE32A for example.com$ /opt/zimbra/libexec/zmdkimkeyutil -u -d example.com$ /opt/zimbra/libexec/zmdkimkeyutil -r -d example.com$ /opt/zimbra/libexec/zmdkimkeyutil -q -d example.comSecond step: updating DNS records
You need to add the public key as a TXT record in the domain: Update the DNS, and check the result of the command: For example: If the key is retrieved, use it to make sure that the public key matches the private one. If you get an error: This means that the file /opt/zimbra/conf/opendkim.conf does not exist, you can create it with the command: If you need to revoke the DKIM signature key, set the empty "p =" tag in the TXT record. By default, a 1024-bit key is created (depending on the version of ZCS), you can change the size with the -b option.
$ORIGIN example.com.
ECAC22D2-DCA2-11E6-BA30-B554729FE32B._domainkey IN TXT ( "v=DKIM1; k=rsa; "
"p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAs5OCY0sX04ziF+sOHt/1kq3A7iAzAjBjb4JteaoFzu1q2uBOiQS0uyaFeY6CgSgRRbvPnq8cWLG/XMU0tM9gSGtgtWDmHOs6/+QgKp6zRmetfsyABA2Y2U+XJlVURUE5ai3KIA/njt7IGZ5yeFsdZIKmhOCAOPGCovq10xkZXHdjRwiqxbCYGXv2m3o74BcWtOLPfEvexD5PYx"
"aTWFbelJpGlDN7WdBCE+ObpLGkJ9co/1sVOcd3c9SHfPq3jcBAFm7oPX2ak7Fb7cslVK77lA2hBgMYqI2Sh+T64o6R33dU++Ej7CuImmv7PAqVUn5MjYr05t3LK9dwWM8Cm6aJ/QIDAQAA" ) ; ----- DKIM key ECAC22D2-DCA2-11E6-BA30-B554729FE32A for example.com# host -t txt SELECTOR._domainkey.DOMAIN# host -t txt ECAC22D2-DCA2-11E6-BA30-B554729FE32B._domainkey.example.com ns1.example.com /opt/zimbra/common/sbin/opendkim-testkey$ opendkim-testkey -d example.com -s ECAC22D2-DCA2-11E6-BA30-B554729FE32B -x /opt/zimbra/conf/opendkim.confopendkim-testkey: /opt/zimbra/conf/opendkim.conf: configuration error at line 0$ zmprov ms `zmhostname` +zimbraServiceEnabled opendkim ./libexec/configrewrite opendkimSender Policy Framework (SPF)
SPF (Sender Policy Framework) - extension for the protocol for sending email via SMTP. SPF is defined in RFC 7208. An SPF record protects against forgery of your domain and allows you to prevent spam emails sent from your addresses. SPF is configured for the address used in envelope-from (SMTP envelope).

Using an spf record, the domain owner can specify the list of servers that have the right to send email messages for the domain. In general, the order is as follows:
[version] [mechanisms] [-all | ~ all | redirect]
The version is always spf1, modifiers tell who can send mail:
- a, mx - servers from DNS records A or MX, respectively,
- ip4, ip6 - server address (you can specify subnets, for example: ip4: 1.2.3.4/24),
- include - take data from another address
Parameters:
- -all means do not accept mail if the mechanism check fails,
- ~ all if the verification fails, then act at the discretion of the recipient server.
- redirect means to pick up the rules from another server.
Consider the examples:
Example 1
example.com. IN TXT "v = spf1 ip4: 62.220.58.72 a mx -all"
For the example.com domain, accept letters sent from the IP address 62.220.58.72, also accept messages from the servers specified in A and MX, messages from other servers should be rejected.
Example 2
example.com. IN TXT "v = spf1 redirect: example.org"
Get the rules from the domain example.com.
Example 3
example.com. IN TXT “v = spf1 include: _spf.google.com -all”
Only receive emails from Google’s smtp servers.
DMARC Setup
Domain-based Message Authentication, Reporting and Conformance or DMARC is a technical specification created by a group of organizations to combat spammers that fake sender addresses. It is based on the identification of the sender’s mail domains based on the rules and features set on the recipient’s mail server.
Thus, the mail server decides whether the message is good or bad and acts according to the DMARC record. Thanks to the DMARC setup, domain owners can create rules for processing emails received from domains that have not been authorized.

After creating the SPF and DKIM records, you need to configure DMARC checking by adding a TXT record in the DNS (similar to SPF). Parameters may be as follows:

For more information, see the DMARC Tag Registry .
The rule for the domain (what to do to the recipient server if the check for spf and dkim failed) can be one of three:
- none - just register messages for the report, do nothing with the messages themselves;
- quarantine - flag messages like spam;
- reject - reject the receipt of the message at the SMTP level.
If you want to receive reports, do not forget to specify the email address in the rua tag:
_dmarc.example.com IN TXT "v=DMARC1; p=none; rua=mailto:postmaster@example.com" Result of adding DNS records
Below is an example of dns records for the example.com zone: For all questions related to Zextras Suite, you can contact the representative of Zextras Katerina Triandafilidi by e-mail katerina@zextras.com
$ORIGIN .
$TTL 3600
example.com IN SOA example.com. hostmaster.example.com. (
2017011011 ; serial
3600 ; refresh [1h]
600; retry [10m]
1209600 ; expire [14d]
3600 ; min TTL [1h]
)
NS ns1.example.com.
MX 10 ns1.example.com.
A 62.220.58.71
IN TXT "v=spf1 a mx ip4:62.220.58.71 ~all"
$ORIGIN example.com.
ECAC22D2-DCA2-11E6-BA30-B554729FE32B._domainkey IN TXT ( "v=DKIM1; k=rsa; "
"p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAs5OCY0sX04ziF+sOHt/1kq3A7iAzAjBjb4JteaoFzu1q2uBOiQS0uyaFeY6CgSgRRbvPnq8cWLG/XMU0tM9gSGtgtWDmHOs6/+QgKp6zRmetfsyABA2Y2U+XJlVURUE5ai3KIA/njt7IGZ5yeFsdZIKmhOCAOPGCovq10xkZXHdjRwiqxbCYGXv2m3o74BcWtOLPfEvexD5PYx"
"aTWFbelJpGlDN7WdBCE+ObpLGkJ9co/1sVOcd3c9SHfPq3jcBAFm7oPX2ak7Fb7cslVK77lA2hBgMYqI2Sh+T64o6R33dU++Ej7CuImmv7PAqVUn5MjYr05t3LK9dwWM8Cm6aJ/QIDAQAB" ) ; ----- DKIM key ECAC22D2-DCA2-11E6-BA30-B554729FE32B for example.com
_dmarc IN TXT "v=DMARC1; p=none; rua=mailto:postmaster@example.com"
ns1 IN A 62.220.58.71
www 86400 IN CNAME example.com.