Mobile access - using a smartphone in access control systems

For more than 20 years in access control systems, the prevailing type of identifier has been a contactless RFID card. Modern replacement by smartphones of everything and everything seems to have gotten to the extremely conservative ACS industry.
Moreover, the advantages of a smartphone in the ACS, in comparison with plastic cards, are absolutely destructive. Under the cut, we will destroy the card ACS and someone else.
Execution of card access control systems
In academic works, this section is usually called the justification of relevance, but since Habr is a smoking room , as I recently read, I decided to add some color to this rather industry-specific story. Moreover, since the advantages of the smartphone are destructive, I will destroy it.
For me, it all started in 2007, when I first came to China. My friend and I, almost like Bashirov and Petrov, decided to go to China for a couple of days and break away in full, and at the same time to find a supplier of the most popular EM-marine (125 KHz) format cards in Russia in 2007.
The curse of the Russian market for access control is a thick map of the EM-marine format.

It was my first trip, and besides the fact that I considered the wrong country to be a third-world country, it turned out the minute I got off the ramp at Hong Kong airport, and at that time it was the best airport in the world, it also turned out that in China itself, even at that time, EM-marine cards were practically not used, and already then Mifare standard cards and fingerprint readers prevailed there (my assessment is personal, especially by eye).
And now, the first main question: What do you think, which cards prevail in Russia in 2018? That's right, EM-marine cards.
The only thing that reassures at least a little is that the situation in them is not much better. The company the HID of Global - one of the world's largest manufacturers of security systems, roughly estimatesthat at the moment 40% of the global ACS market is HID Proximity cards (125 KHz), which in terms of security is the same hat as EM-marine. On the official HID website, these cards are fully present, and there is not a word in the description that these cards can be copied.
The funny thing about quotes is that the Em-Marine, StandProx card costs 12 rubles , while the simplest HID Proximity card, HID ProxCard II® costs 200 rubles .
The second main question immediately suggests itself: Is the Russian market doomed to the eternal use of contactless cards? And if not, what technologies are they replacing?
And here I will allow myself to express my own opinion - in the next few years the landscape of the market will seriously change, and nothing will, and no one will change it.
In place of card access control will come:
- Mobile Access Technologies
- Biometric identification
On the current state of affairs in the field of biometric identification on our website there is a huge long-term . But we will talk about mobile access technology in detail in this article.
The first company to offer mobile access to the mass consumer was HID Global, part of the ASSA ABLOY conglomerate, with a turnover for 2016 of $ 1.2 billion. Included in the top 50 largest companies in the industry of security systems.
Scan from “white paper” HID Global Let's take 2014 as the starting point for the advent of technology in the markets. Now 2018, and in the Russian market you can find 10 manufacturers offering solutions for mobile access.
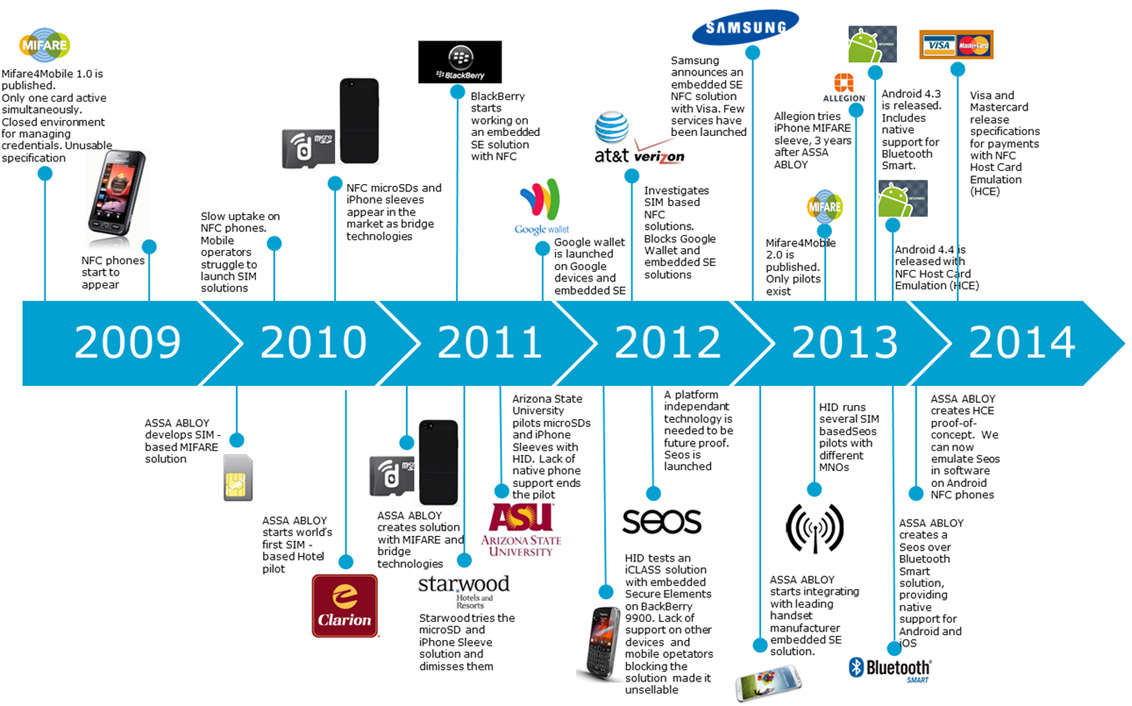
- Foreign - 4
- Russian - 6
It seems that we again beat everyone, and all the other countries of the world envy us. But the devil, as always, in detail, let's look at them.
And here is the first detail - Russian companies presented their products only in 2018, announced in 2017 at the exhibition of technical security equipment Securika . But in reality, working devices went on sale all the same in 2018.
The second detail is that Russian manufacturers, as always, benefit from the number of offers, but what about the quality. Inside - everything is bad, but there is hope.
What Russian ACS manufacturers have been waiting for for 4 years, especially with the understanding of all the catastrophic advantages of mobile access.
The advantages of mobile access
It is cheaper , even if virtual identifiers cost money, they cannot be lost, broken, they are easier to administer. And if virtual identifiers are free , it’s catastrophically cheaper.
It is safer , creating duplicate 125 KHz maps, both HID Proximity and EM-marine, a process that is not difficult even for my grandmother, my grandmother, of course, there is no interest in using “holes” in your access control system, but since install the system, you already know that there are interested.
Moreover, unlike contactless cards, the smartphones themselves support multifactor authentication, biometric identification and other security features that were not dreamed of by contactless cards.
It is easieradminister. When an identifier is lost, broken, forgotten at home, someone has to solve this issue, and this someone, depending on the size of the enterprise, can spend quite a significant amount of paid time on it.
The advantage of mobile access is that smartphones are less likely to lose, break and forget at home.
This is more effective , a significant reduction in practice, when employees mark the arrival / departure for each other. In the states, companies on this lose $ 373 million , according to data for 2017. No one thinks how many people we have, perhaps the breadth of the Russian soul does not allow, but judging by the love of memes like "this country cannot be defeated," I think no less than in the United States.
It is more environmentally friendly , contactless cards are made of plastic, which willdecompose for hundreds of years , and still need to consider that the production of plastic is not the most environmentally friendly technology. In the opinion of the UN, this reason alone is enough to refuse the use of plastic cards.
It is more convenient . Access via a mobile device can be a faster and more convenient procedure. For example, when traveling by car, Bluetooth Smart technology with an increased range of action allows you to open gates or barriers when a car approaches, and the driver does not have to lower the window of the car and reach the reader with a card.
What is mobile access?
Smartphone access means using the smartphone as an identifier.
To do this, you need a smartphone based on iOS or Android with NFC or BLE support. Also, in almost all cases, you will need to install a mobile application that is downloaded for free from the Apple Store or Google Play, regardless of the vendor.
Smartphone access can be considered as a complete replacement or use of contactless RFID identifiers. Since all readers, in addition to being able to read the identifier from the smartphone, can read conventional RFID identifiers.
This may be convenient in some cases, for example: all regular employees walk on a smartphone, and plastic cards are used to issue guest passes. Well, no one forbids tying a smartphone and a card to one person, but let's not forget that a smartphone can sometimes be discharged.
Access via a smartphone implies two technologies, at least one of which must correspond to readers supporting mobile access - NFC and BLE.
- NFC (Near field communication) - close identification technology that supports mobile HCE (Host Card Emulation) technology
- BLE (Bluetooth Low Energy) is Bluetooth low power technology .
Manufacturers of readers Parsec, Rusguard and PERCo, have in their arsenal only the NFC-module. Which, of course, is unfortunate, since it severely limits their use.
Nedap, HID Global, Suprema, ESMART, Salto, Sigur and ProxWay manufacturers have a full list of modules in their readers.
In addition, manufacturers understand that mobile access technologies do not come to the empty market, but to the market already filled with current card access control systems. Therefore, all with all the readers presented below, you can use classic contactless smart cards. First of all, it will be easier to organize a “transitional” period. you can not change all the readers to mobile at once, which can fly into the penny, and do it gradually, leaving for example most of them only on the cards.
And secondly, there is always a unique person with Nokia 3310, well, or maybe someone just wants to use maps, why not - the world is diverse.
So, what else can you use besides the smartphone:
- Contactless smart cards (mainly Mifare Classic, Mifare DESFire, Mifare Plus, iClass)
- Bank cards (Mastercard, Visa, World)
- Smartphones
Depending on the vendor, the list of identifiers will vary, but smart cards support everything.
Vendors offering solutions for mobile access in the Russian market
1. Nedap
At Nedap, work with guest passes is very conveniently organized; for guest access, a one-time bar or QR code is sent to his E-mail, which is read from the smartphone screen.
- Reader MACE Reader MM - price 27 609 rubles
- Reader MACE Reader MM QR - price 37,634 rubles
- Reader MACE Smart - price 20 816 rubles
Mobile application MACE App for Android and MACE App for iOS
2. Suprema Suprema
Readers stand out with a unique combination of identification methods, combining smartphone identification, biometric identification and contactless identification cards in one device. From biometrics, Suprema supports fingerprint technology, and face recognition.
- Street biometric terminals BioLite N2 - price 50 199 rubles
- ACS BioStation A2 biometric terminals - price 95 970 rubles
- ACS and URV Terminals BioStation L2 - price 54,629 rubles
- BioEntry P2 biometric reader controllers - price 35,241 rubles
- BioEntry W2 fingerprint readers - price 47 985 rubles
- Budget biometric reader BioEntry R2 - price 30 200 rubles
- FaceStation 2 biometric terminals - price 82 230 rubles
- BioStation 2 Biometric Terminals - price 76 214 rubles
- Xpass D2 RFID Card Readers - Price 11,811 rubles
- Xpass smart card readers - price 19 932 rubles
Mobile application for Android BioStar 2 Mobile and BioStar 2 Mobile for iOS.
3. Parsec
- The reader of the smart cards PNR-P26 - the price is 13 720 rubles
- Smart card reader PNR-P19 - price 12 250 rubles
- The reader of smart cards PNR-P15 - the price is 15 190 rubles
- OEM smart card reader PNR-P03E - price 9 800 rubles
- The reader of bank cards PNR-P19.B - the price is 14 700 rubles
- Multiformat reader PNR-X19.B - price 16 856 rubles
Android Mobile Application - Parsec Card Emulator
4. Rusgard
- The multiformat reader RDR-202-Multi-Key - the price is 18 000 rubles
- Desktop card reader Z-2 USB-MF-RG - price 6 600 rubles
Mobile application on Android - RusGuard Key
5. HID
The solution from HID Global allows the smartphone to interact with the iCLASS SE and multiCLASS SE readers in the near Tap mode (touch) or at a distance in the Twist and Go mode (turn of the smartphone). The “Twist and Go” technology allows you to unlock the blocking devices only after the user rotates the smartphone 90 degrees, which eliminates accidental opening when using Bluetooth.
Active feedback in the form of vibration and sound signals when opening doors increases the convenience for the user.
- The reader of smart cards iClass SE R10 - price 8 281 rubles
- The reader of smart cards iClass SE R15 - the price is 16,241 rubles
- Reader smart card iClass SE R40 - price 16 241 ruble
- The reader of smart cards iClass SE R90 - price 46 951 ruble
- The reader of smart cards iClass SE RK40 - the price is 29,706 rubles
- The reader of smart cards multiClass SE RP10 - price 10 807 rubles
- MultiClass SE RP15 smart card reader - price 18,721 rubles
- MultiClass SE RP40 smart card reader - price 18,721 rubles
- MultiClass SE RPK40 Smart Card Reader - price 32 186 rubles
You should add $ 75 for the Bluetooth module to the prices of each HID reader , it is delivered separately.
Mobile applications HID Mobile Access for Android and HID Mobile Access for iOS The
application allows you to get an access card to your smartphone through the administrator portal. Then the user can use the phone as an access identifier. The BLE Config App application allows you to change the reader configuration, update the firmware, receive and install the configuration, manage templates using the phone.
6. ESMART
- Reader ESMART® Reader NEO - price 11 000 rubles
- Reader ESMART® Reader STONE - price 12 000 rubles
- ESMART® Reader OEM Reader - price 9 000 rubles
Mobile application on Android - ESMART® Access
Mobile application on iOS - ESMART® Access The
mobile application ESMART® Configurator is available on iOS and on Android .
ESMART stands out for its rich configuration options:
Types of Readable IDs:
- UID read
- Work with memory Mifare ID, Classic, Plus in SL1
- Working with Mifare Plus memory in SL3 mode
- ESMART® Physical and Virtual Identifiers Access
For all Mifare cards, you can set the amount of data, the offset, the number of the block to be read, and the authorization key per sector (Crypto1 or AES128).
ESMART® Access is a secure storage and transmission technology for physical and virtual identifiers that is secured at a bank level.
Physical cards are built on a JCOP (Java) chip and use the ESMART-Access applet.
An applet is a small application that allows you to extend the functionality of a regular identifier, subject to copying, to a copy-protected identifier.
ESMART® Access technology uses the following degrees of protection:
The output interface format is Wiegand. You can set an arbitrary number of data bytes, use \ disable parity bits, as well as the sequence of output bytes.
You can customize the sound and light display, with a choice of colors or the order of colors poured among themselves.
7. ProxWay
- Readers PW-Reader BLE - prices from 3549 rubles
Mobile application PW Mobil ID for Android and PW Mobile ID for iOS
Capabilities:
- Work on NFC and BLE
- Store up to 3 identifiers simultaneously
- Intuitive interface: 2 buttons (Transfer ID to reader - “open” button and “gear” setting)
- Request mobile ID directly in the application - sending a request by mail
- Setting the on / off transfer of the identifier to the reader to enable the screen of the smartphone
- Getting a mobile ID at the invitation of the administrator.
- Configurator for Android only - ProxWay Mobile Config
8. Salto
SALTO with smartphones is supported by the XS4 2.0 series.
- SALTO XS4 2.0 - prices from 287 Euro
JustIN Mobile BLE mobile app (only with Salto controllers)
JustIN Mobile uses Bluetooth Low Energy (BLE) technology to securely transfer data between your smartphone and end devices. The encrypted key created in the SALTO access control software - ProAccess SPACE, is sent to the user's smartphone “Over the Air” - Over the Air - OTA.
The smartphone with the JustIN Mobile application and passed the registration and verification of the user receives and decrypts the mobile key, and after that the user simply touch the icon on the screen of the application on the smartphone to open the door.
9. PERCo PERCo
equipment supporting work with smartphones:
- The reader MR07.1 - the price is 7 723 rubles
- Control reader MR08 - price 9 941 rubles
- Electronic KT02.7M through passage - the price is 105 304 rubles
- Electronic checkpoint KT05.7M (MA) - price 162,796 rubles
- Electronic checkpoint KTC01.7M (MA) - price 11,910 rubles
Working with smartphones as identifiers is supported in the software for access control systems - PERCo-Web and PERCo-S-20 .
On the Android smartphone, the PERCo free application must be installed . Access . As an identifier for smartphones with Android OS, a unique IMSI identifier is used - an individual subscriber number associated with the SIM card of the smartphone.
Apple smartphones (iOS) use the unique Token as an identifier, which is tied to one of the bank cards emulated on the smartphone. Before use in the access control system on a smartphone, it is necessary to activate this particular bank card. Unique Token is not a bank card number. For Apple smartphones, installing the PERCo application. Access is not required.
10. Sigur
- Reader Sigur MR1 BLE - price 15 000 rubles
Sigur, as well as most Russian developers, rolled out their reader to Securika back in 2017, currently the Sigur MR1 BLE reader is available for order, and mobile applications are available for download.
In addition to smartphones, the reader works with contactless Mifare cards, series - Classic, DESFire, Plus - including in SL3 mode.
Just as identifiers, you can use regular bank cards (Mastercard, Visa, MIR) with contactless payment support.
Sigur is allocated free mobile identifiers, and the fact that the identifiers themselves automatically upon issuance are immediately entered into the ACS database and from there enter the controllers. Mobile applications Sigur Access for Android Sigur Accessfor iOS.
The application for configuring readers Sigur Settings only for Android.
Issuance of the identifier to the smartphone
In order for you to have the opportunity to use the smartphone as a pass, a unique identifier must be generated or issued on the smartphone , it will be transmitted from the smartphone to the reader, and from the reader to the controller, and the controller, depending on the access settings, will either provide access, or deny it.
Issuance of a virtual identifier
In this case, the generation of a virtual identifier occurs in the manufacturer’s database. Further, the already generated identifier is given to the user. The meaning of its use is that all identifiers are stored in the manufacturer’s database and cannot be issued twice. That is, a virtual identifier cannot be transferred, it can be activated only once, on one specific smartphone, in one specific mobile application. In addition, the manufacturer controls the uniqueness of the issued identifiers in order to avoid issuing the same identifier to different users.
One of the advantages of using virtual identifiers is that the user cannot see the identifier (numeric identifier code) in the application, which means that the identifier cannot be copied or transmitted.
Intercepting the identifier during transmission from the smartphone to the reader also does not work, because It is transmitted in encrypted form.
Depending on the vendor, the issue is made in slightly different ways:
- Salto uses Over the Air (OTA) technology to transfer access to the smartphone, which allows you to safely transfer the virtual identifier to the user's smartphone in encrypted form.
- In other cases, the transfer of identifiers occurs directly to the user through the access control administrator. Thus, the ESMART brand is currently working.
- Nedap uses mobile verification and network transfer of identifiers to the smartphone, and also implements the issuance of a free Mace ID when registering a new user.
- HID Global has the admin software in its application arsenal. When the administrator receives virtual identifiers from the manufacturer, they are assigned to users and sent over the network via users' smartphones.
In this case, a ready-made identifier is issued to the user, which should only be activated using a unique activation code. The application contacts the server and, after comparison, confirms that the activation code is free, after which the identifier is transmitted to the application.
The cost of virtual identifiers
The database of virtual identifiers is maintained on the manufacturer’s servers — this is probably one of the reasons why manufacturers charge for issuing an identifier.
ESMART - Secure ESMART® Virtual ID Access:
- 100 rubles (Unlimited)
- 60 rubles (7 days)
- 40 rubles (1 Day)
Proxway
- 65 rubles (Unlimited)
Nedap
- Free Mace ID at registration
- 1.1 euro / year (you can issue an unlimited number of times if one person leaves, his identifier responds remotely and is given to another person. There is also an administrator portal system provided by the manufacturer for 399 euros per year. The identifier is issued on the principle of creating a user's personal account. This means that the user can see his ID from any device from which he logs into his personal account.
HID
Prices set before the end of January 2019.
- Unlimited 9 dollars per piece.
From February 2019:
- Approximately $ 5 per year - one identifier for 5 devices on the basis of a license (following the example of antivirus software).
- The cloud admin portal is free and, as with Nedap, provided by the manufacturer.
Suprema
Server issuing identifiers to users is created by the administrator on site and is contained by him. There are several types of packages:
- up to 250
- from 250 to 500
- from 500 to 1000
- from 1000 and more.
The average price specified by the manufacturer is $ 440 per 100 people indefinitely.
Suprema is in the making of its mobile solutions, so the price changes periodically.
Salto The
fee is charged for servicing the cloud at 2.1 Euro per year per user.
Sigur
Offers free, perpetual mobile ids, generated from smartphone data and Sigur software.
Generating an ID based on smartphone data
Parsec and RusGuard use the method of generating a virtual identifier based on the unique IMEI of the smartphone. This happens automatically when you install the corresponding mobile application. PERCo for these purposes uses IMSI , respectively, without a SIM card or with a non-working identification pass will not work.
Further, the identifier must be manually or with the help of a reader entered into the database of the access control software. Next, it enters the controller.
The disadvantages of generating an identifier based on phone data include the ease of identifier falsification. IMEI fake enough even for an inexperienced user.
IMSI is a little harder to fake, will require the so-called multisym card . Also in this case, the SIM card can simply be transferred, inserted into another phone and passed identification.
And of course, do not forget about the various technical devices , through which you can learn IMSI secretly from the user.
Well, and the saddest fact, your IMSI and IMEI, of course, are known to mobile operators, and therefore to all law enforcement agencies of all Russia. There are a lot of examples of sincere love between Russian companies and law enforcement agencies.
Do you want to give the key to all the doors in your company to our law enforcement officers? The question, which at least is worth considering, before making a choice.
Cost identifier generated based on phone data
So in this case, the manufacturer does not incur any costs for maintaining the database of identifiers, therefore obtaining identifiers for free.
But you need to realize that the access control system, with identifiers generated on the basis of phone data, is a security hole the size of a granary gate. The question of the correctness of the production of products with such holes is probably a topic for a separate article, because we do deal with security systems.
ID recall
There are two ways to revoke an identifier from a smartphone:
- The response is made in the controller's ACS software, after which the user is no longer able to go to the object
- Feedback online from the user's smartphone, through the access control software
ID recall from smartphone
If the identifiers are stored in the cloud access control interface, and the administrator has the appropriate software, then the identifier can be removed remotely. This technology is based on the HID Mobile Access application.
Similar technology is also used by the HID, Nedap and Suprema brands.
In other cases, deleting an identifier from a smartphone is done by deleting the identifier in the application or deleting the application itself from the smartphone.
Recalling identifiers from the access control controller
The identifier is withdrawn from the ACS controller manually using the “Dismiss the employee” function in the controller’s ACS software. Valid on all controllers.
Rusguard has in its arsenal the “Administrator” module in the mobile application, which allows it, among other things, to block and delete employees from the system remotely
Issuing Guest IDs
The advantages of mobile access for issuing guest passes are that for guests or employees working remotely, there is no need for a compulsory visit to the “pass office” to issue a guest pass. You can send it in advance, for example, by E-mail.
Guest IDs are issued in different ways depending on the vendor:
- Issuance of identifiers for a specific time (ESMART)
- Issuance of one-time identifiers (HID, Suprema)
- Issuing a QR code (Nedap), a QR code is sent to E-mail, read from the phone screen. This option seems to me especially convenient. does not require installation of the application on the smartphone for identification, but there is also a minus - a QR code can be easily transferred.
- Issuing a perpetual identifier and then manually deleting it from the access control system (all the others), in fact, is no different from guest contactless cards issued in classic access control systems
Transfer the identifier to the access control controller
The access control administrator can get activation codes from the manufacturer in different ways:
- By e-mail, in the form of a .xlsx file with a password. This is what happens with ESMART and ProxWay.
- There is an Administrator's personal account provided by the manufacturer for a fee, like Nedap and Salto, or a free personal administrator account like a HID.
Cloud monitoring is performed via a dedicated administrator’s personal account. It contains data on all issued identifiers with the possibility of their withdrawal and issue remotely. - In other cases, the server is created and monitored by the Access Control Administrator himself as in Suprema, Parsec, RusGuard and Sigur.
What will happen when you change your smartphone?
For any vendor, when changing or losing a smartphone, the identifier is lost, akin to losing or replacing the physical card, hence a new virtual identifier is needed for the new smartphone, and if generated, a new identifier will be generated based on the smartphone data.
Due to the fact that the application online checks all previously issued identifiers, the issuance of the same identifier again is not possible - the application will generate an authentication error.
An application of any reader vendor is subject to a unique identifier rule, as a result of which identifier repetition should not be possible from a system security point of view.
Data storage
The issue with personal data is a hot topic, so let’s dwell on what and where is stored.
Identifier Only: Stored in two places (in this case, the identifier is just a unique long number):
- In the reader’s manufacturer’s database, it can be browser-based for client access or programmatic, or it can be a local storage database that is not accessible from the outside. This item is for virtual identifiers only, identifiers generated on the basis of smartphone data are not stored in the general database of the manufacturer.
- In the application on the user's phone
- In the memory of the controller ACS
Identifier and name of the holder are stored:
- In the database of software that interacts with controllers ACS. The software is installed on a computer that is in the same network as the controller.
NFC or Bluetooth
To transfer the identifier from the smartphone to the reader, NFC or Bluetooth communication interfaces are used. Let us examine in more detail what is the difference, and what can be the pros and cons in the context of the ACS objectives.
NFC is a near identification technology. The advantage is less energy consumption compared to Bluetooth, but NFC loses Bluetooth technology in range, NFC - range up to 7 cm, Bluetooth - range up to 20 meters, unpretentiousness to weather conditions and data transfer speeds.
But long range is not always dignity. NFC, due to its short reading range, eliminates problems when transmitting an identifier, while Bluetooth transmissions may encounter interference and signals from third-party devices using this radio frequency.
An important feature of using NFC technology is that the NFC module is not available on iOS devices, in contrast to Bluetooth, which is available for almost all mobile devices and is more universal.
Do not forget that the specifics of using Bluetooth also lies in the fact that it must be permanently enabled on the smartphone. Often there is a fear that this will quickly discharge the phone. The use of fourth-generation Bluetooth technology, or BLE (Bluetooth Low Energy), makes it possible not to sacrifice the phone's charge for using mobile access systems, since the transmitter is turned on only for sending data.
In addition, the specifics of using Bluetooth will be that if there are several readers in the identification zone, they all consider the identifier and unlock the blocking devices, unless otherwise is programmed in the access control controller, but most likely it will not. Complex work scenarios are supported by far from all access control systems.
Well, imagine a situation: you walk along the corridor and all the doors on your way are torn off, except that it looks like a choir, this, of course, completely contradicts the goals of the ACS. Most manufacturers allow you to adjust the range for each particular reader, which will be a good solution, because for a door, it can be one, a small distance, and for a barrier, on the contrary, and a maximum of 20 meters is quite a working configuration.
findings
Access control systems that we know are already dead. But the industry seems to have not realized this yet. Mobile identifiers will become one of the key paradigm shift drivers for access control in the world, and in the world, in Russia.
Mobile devices have already replaced a lot of everyday objects in our lives. Moreover, the replacement occurs at a staggering rate. Six months ago, I did not use the phone for shopping, and today I try to avoid places where it is impossible to pay for the purchase with a smartphone, and I succeed. Today, I pay about 99.9% of my personal purchases from a smartphone. The progress from 0 to 99.9% in half a year impressed me even when I realized this.
The arrival of mobile technology in the security industry will produce a bombshell. And it seems that many will be thrown out of the market by this blast wave.
HID, Suprema, and Nedap - traditionally presented excellent, and unparalleled solutions, traditionally for a lot of money.
The strategy, which is chosen by Russian manufacturers of access control systems, is already visible. Of the Russian brands, only ESMART and ProxWay presented solutions comparable in technical implementation to foreign vendors. And there are ACS manufacturers, including those occupying a decent market share, who have not presented any mobile access solutions at all, and, accordingly, not mentioned in this article.
And what is most interesting, neither ESMART nor ProxWay are leaders in the ACS market. I would even say this newbies.
And mobile identifiers and biometrics are just the beginning. Another trend that may have a significant impact on the Russian market is the entry of the video surveillance manufacturers into the ACS market. HikVision presented a very broad and fairly high-quality line of access control systems .
And if you remember, and I remember about it every time someone pronounces the phrase "mysterious Russian soul", that one of the most disgusting controllers for access control, Bolid S-2000-2 , is also the most popular controller simply due to its popularity. fireide fire alarm systems. It turns out that video surveillance can become the same engine for the access control system from the manufacturers of video surveillance.
Another significant feature of contactless cards is that over its more than 30 year history, they have not gone beyond a local access control solution used mainly in companies. Individuals from the time of ancient Rome to the present use metal keys.
Using a smartphone may well be a solution for the retail market. Trite, but as a fan of Airbnb, I just got bogged down to agree on the time when the keys to the apartment I rented could be handed to me. How much easier would it be if I could put the app on my smartphone and quietly open the door during the entire rental period. In hotels, similar solutions may be more convenient than existing card solutions.
These are, in one way or another, other products, but the technologies are the same and, like in the video surveillance market, there are companies that offer solutions for different markets under different brands. So it can happen in access control.
It seems that many leaders of the Russian market of ACS instinctively seek salvation from the future in the past. They cling to the old experience, trying to extract from it what it has never been and could not be, since the Russian market for access control has never faced such changes. Probably, such a strategy will work for some time.
But many do not mean everything; a couple of Russian companies ESMART and ProxWay presented quality products on the same level as their foreign counterparts. Sigur stands out with an interesting approach and seamless integration with its access control system.
All this gives us a good hope that soon old-timers will be able to remember about EM-marine cards, along with perforated cards, bar-code cards and magnetic stripe cards.
Another point worth mentioning is: identification devices, which we reviewed in detail in this article, are just one of the components of the access control system, and for your system to work perfectly (and for less we disagree), not less attention should be paid to the choice of actuators , controllers and software. And of course, you should pay attention that the integration capabilities of modern access control systems are enormous - with security and fire systems, with video surveillance systems, with access to a computer, with elevator systems, and much more. So, do not forget to make a choice.read our next longrid for the choice of access control .

Only registered users can participate in the survey. Sign in , please.
