In the wake of cyber detective

Hello to all Khabrovites!
I happened to participate in a competition, quite rare of its kind, called Cyber Detective. The competition was held at the HackIT-2017 conference, in which he also took an active part. Tasks are based on finding open information on the network. I want to share my experience, writing and impressions.
I’m participating in a similar CTF for the first time. I usually participate in CTF in jeopardy format, in which there are several categories at once (Web, Reverse, Crypto, Stego, Pwn, etc.). In the same contest, the developers did almost all the tasks for the Recon category and one task for the Forensic. But more about that below. Initially, I did not plan to participate in the competition, but I was interested in the task of social engineering, which later gave uniqueness to this competition and made me play seriously.
Jobs in the direction of Recon, or as they are often called "jobs on OSINT", are solved by finding information from open sources. To solve such tasks, you need to be well able to use the features of search engines such as Google , Duckduckgo , Shodan , Censys , to know about various public databases, usually state ones, to be well versed in the features of social networks. Of course, nowhere without social engineering. And this is not all the skills that a qualified Internet intelligence officer should possess.
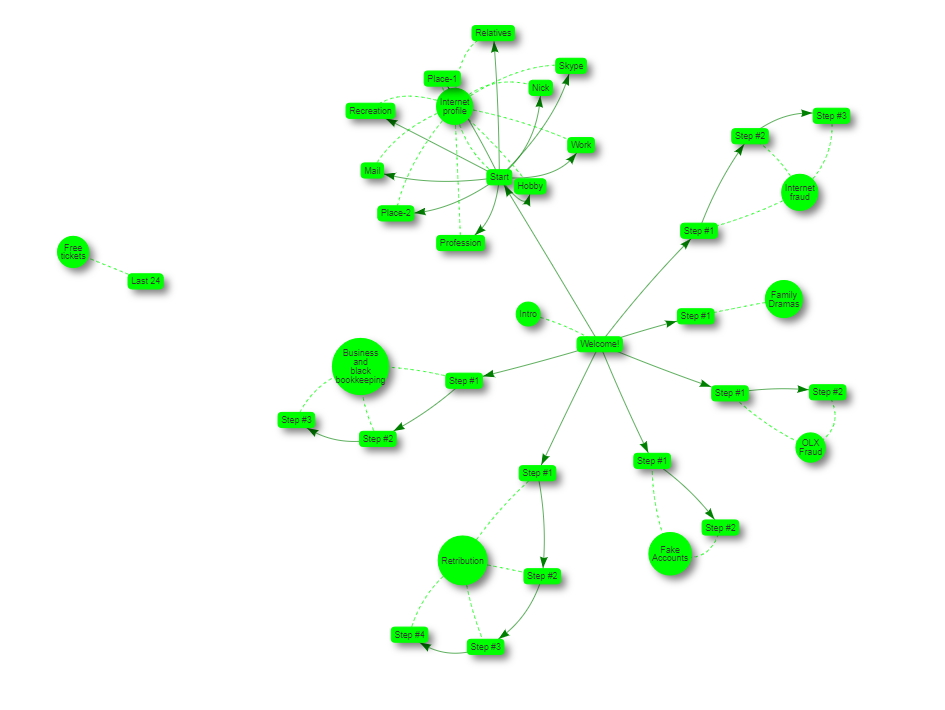
A total of 27 tasks were posted on Cyber Detective, which were divided into groups. These groups, “branches” had their own legend, a story around which tasks and decisions revolve. The visual graph of task dependencies taken from the platform is presented above. The story is revealed as the current branch is resolved, which is much more interesting than reading the meager job condition on a typical CTF. Each story had an average of 3-4 assignments.
I want to note the high level of preparation and reasonableness of the platform. On many CTFs, there is friction and controversy between some teams and organizers regarding the honesty of other teams regarding the rules of participation. Simply put - it is forbidden to exchange flags between teams / participants. And it happens that a team, not taking the coveted prize place, tries to get it by searching for the reasons and evidence of fraud of the winning teams. This is quite low and most often causes nothing but contempt and disrespect, as the organizers themselves try to catch and punish violators. However, in this platform, information on passing the flag is open to any participant, and allows anyone to analyze the history of passing decisions of another participant.
As the tasks are described, I will talk not only about the right decisions, but also the wrong ones, and how they led to the answer. Used many interesting services, utilities, approaches. So you need to stock up on tea / coffee and read on.
Intro
From this category, the solution to all other tasks begins. It is impossible to solve all the others without passing one of this task, but since it was solved quickly, no problems arose.

It was easy to find. Going into the telegram chat and opening the chat page, you could see the flag. I want to note that flags do not have a typical template, like flag {...}, or md5. This makes it difficult to find. On the other hand, this format can not be placed everywhere, so the developers decided to sacrifice my nerves in favor of a variety of tasks.
Flag: "Welcome on board!"
Internet profile
Next, it was worth starting to solve this category, each of the tasks was rated at 50 points. Here were simple tasks on which you can stretch yourself. The tasks were written in the order in which they were published on the site, but of course they were not solved in that order.
Start
In some social networks, it is possible to find out information about the page, in particular, it is vk.com , knowing the user's email / phone number, as well as his last name. This is a bug, or a feature - it's hard to say, but there is a flaw (it’s not worth running a report on hackerone :)).
It would be logical to think that Mark is a name, but no, this is a surname. This did not baffle me for long and did not immediately introduce a "last name". Then I went to the VK, clicking on the "Forgot Password", entered the number, last name, and got a page, which without problems can be found through the search. Here's the profile: Orest Mark

Flag: "Orest"
Nick

Everything is elementary here, his nickname is the address on the VK site.
Flag: "0n1zz"
Work

Having looked at many groups to which he is subscribed, and also glancing at the page on his github, the idea came up that it was Microsoft.
Flag: "Microsoft"
Profession

I did not solve this task immediately, continuing to browse the tasks below, and extracting as much information as possible from the page, I entered such values as Programmer, Developer, and so on. Then he went looking for a guy in other social networks. networks, found him an Orest Mark . When searching, in the list of profiles or in the page information, it is written that he is a Software Engineer at Microsoft.
Flag: "Software Engineer"

It was very simple, I remembered that on his github page I saw soap.
Flag: "oreest1987@gmail.com"
Skype

The very name of the task prompted what exactly to look for, the answer on the Orest Mark page.
Flag: "orest_mark_87"
Place-1

I had to tinker a bit with this and the following tasks, as several options formally suited. On the page, a geotag is attached to the post , which did not fit. Looking at friends, it’s immediately clear that Mark has a brother, Tenson Mark , who also has a geo-geek. Just looking at facebook, it became clear where he was from.
Flag: "Sinaia, Romania"
Place-2

The answer is on the facebook page, in the column "About me."
Flag: "Kiel, Germany"
Relatives

Taking into account that Mark has a brother, Mark Tenson , we hand over the next flag.
Flag: "Tenson Mark"
Hobby

Having already studied this man enough, it is clear that he is fond of racing. The correct flag name can be found in the list of groups on the VK page, or, if you look closely, you can see his T-shirt on the avatar, where this inscription was.
Flag: "Speed racing"
Recreation
Remembering that on the guy’s VK page , a geo-geek was attached to the post , google the place, we find a solution.
Flag: "Sesena, Spain"
The first branch is closed, the tasks are completed, +550 points in just 20 minutes. This gave a huge incentive to understand further, naively thinking that subsequent tasks would be just as easy. But let's see in the end what dossier I collected for the guy. His name is Orest Mark, I know his pages on VK , Facebook , Github. I know the mail, nickname, phone number. He also loves whom he works with, where he works, where he lives, where he was born, who his relatives and friends are, where they live. This quest thread is a great illustration of how you can find information about many people through social networks. The information collected is enough to attack his mailing address, try to access accounts on social networks, apply social engineering and find out any other data. However, there will be enough elementary things, I will move on to the most interesting task of this competition.
Family dramas
Immediately google the person by number, try to repeat the trick with restoring the page in vk. Google gave out something interesting, at first glance, at the request of "0671710968", especially the first page . I did not understand what this means. For lack of other options, I decided to dial the number. To my surprise, the girl answered, and immediately dumped. The task involved the application of social engineering skills, as I understood later, which would help to figure out the address. It was necessary to do this not intrusively, having interested a person. Somewhere I thought about the legend for about 20-30 minutes, and it took about 15 minutes to practice reading so that it wasn’t very noticeable that I was reading the text, speaking not intrusively and not monotonously. Many subtleties that I tried to take into account. Here is the text that compiled.
Good evening!We managed to find out the address. But then I had to call back, because I didn’t make out the address a little, and I’m supposedly now clarifying the address on the map for drawing up the route. Already in the process of the conversation I realized that I was submitting a bit of information, I needed more communication. However, as the developers later admitted, this was the best attempt of all who received and did not receive the address. Of course, I’m far from Kevin Mitnik, and I don’t do carding, but for the first time it will do. I want to note that it was from this task that CTF began to solve, attracted an unusual and very interesting format for receiving an answer. I think the admins did not sleep for days, since there are a lot of participants, and they decide 24 hours a day. As they later told me, it was possible to write this number in a telegram, and they would also have answered that it was done, I think, for foreigners. Although, of course, this is not the drive, risk, emotions. On the phone you need to answer quickly questions that you could not foresee, and the quality of answers depended on the literacy and thoughtfulness of the legend. Having a cool experience, I wanted to continue to solve new impressions. However, such an interesting task was estimated at 100 points, which did not please, unfairly allocated points for this task in my opinion. The players in the top of the scorboard were far away, but two sleepless nights fixed it.
My name is Andrey.
I represent a student movement called World Frendship. We are committed to bringing people together based on mutual assistance. Helping in various matters of life and everyday life, we make new friends and acquaintances, and also want to give people a little good mood. Would you like to participate?
- (answer)
Then I’ll talk a little bit about our movement and what we are actually doing.
Our movement organizes many projects. For example, not so long ago we launched one project, the essence of which is to help foreigners find housing for free. The idea is to make new acquaintances, foreign friends, also have the opportunity to learn a little about the culture of other people, practice a foreign language, and so on. You may have heard of such similar projects being carried out in England and the USA. Here.
I want to offer you to participate in another project called “Warm Dinner”.
The bottom line is that we cook with you and spend time in a fun environment. How do you like the offer?
- (answer)
Take a look. You cook foods, as well as recipes that you would like to try. Two of our students, usually a guy and a girl, come to you and cook. Then you can play some kind of board games, or go for a walk. Well, do you agree?
- (answer)
Then you need to clarify a couple more points. Tell me, what is your name?
- ...
And tell me your address
Flag: "Odessa, Palubnaya, 7"
Retribution
Then I took up this category, since judging by the number of solutions to tasks from it, it should not have been difficult.
Step # 1

At the time of this writing, Google was not giving out absolutely no information at this strange address. This is not base64, or any other kind of ciphertext, as it seemed to me at first. It was then logical to assume that this is an onion resource. After downloading the Tor browser, this site was seen in a few minutes. At the time of writing, the search engine has already cached something, and this greatly facilitated the process of solving this task.
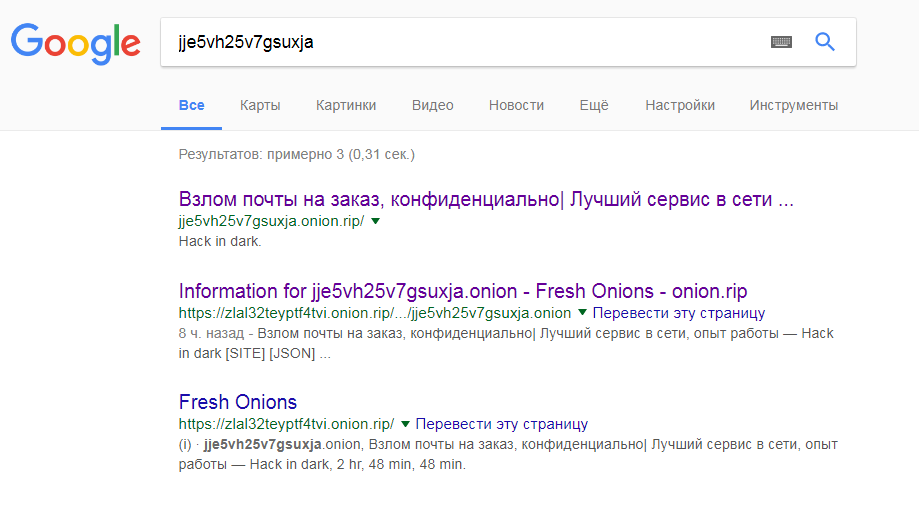
Here is a site opened, and received the first flag.
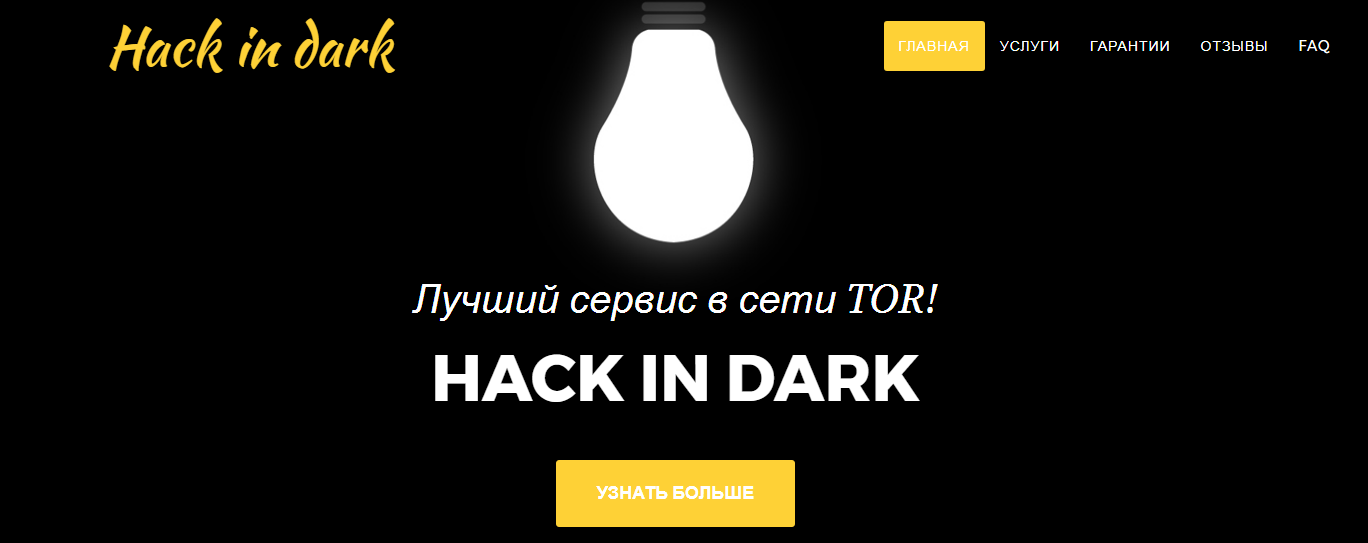
Flag: "HACK IN DARK"
Step # 2
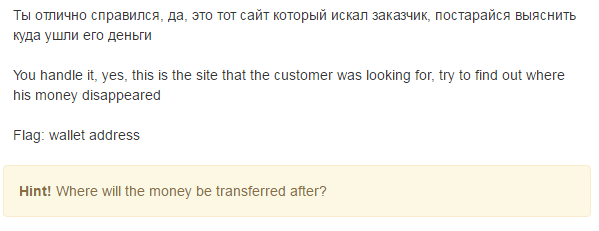
This task was not easy and hung on it for a long time. On the page below were offers to hack various mails, accounts on social networks, breaking through sim cards, and even learning how to hack. Here is a small part of the list of services.

By clicking on one of the services I get a QR code.
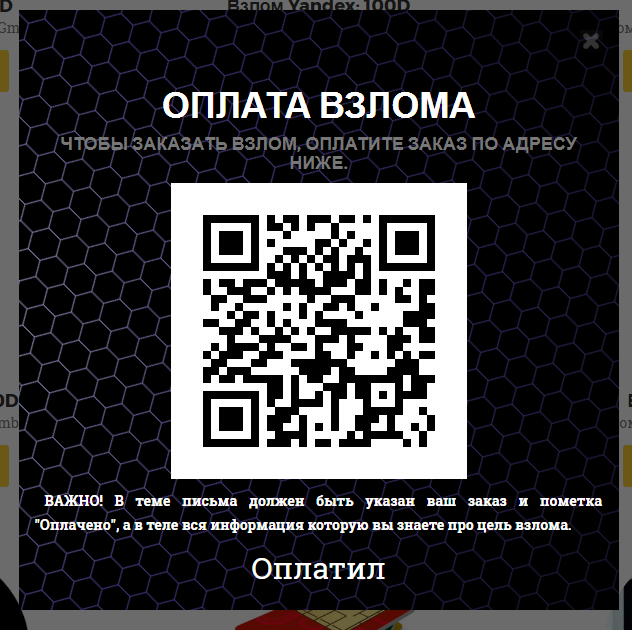
Decryption: DRYcucyK5Hfc3A4hit9KqsKm5FwxHJYSdk
During CTF, these QR codes changed, which complicated the decision, a little confusing. One of these codes was successfully decrypted through base64 decoder, and having received a rather incomprehensible text, he went the wrong way, analyzing what it was. Then he inspected that at the bottom of the page there is a mention of such a thing as dogecoin, and immediately it became clear that it was a cryptocurrency. Now, when I write this description, in principle, it seems obvious, but at that time it didn’t seem so. Googling, he learned that dogecoin is an altcoin based on the blockchain. Going to the Dogecoin website, I registered a wallet and tried to figure it out. But everything turned out to be simpler, it was necessary to view the transaction history for the current wallet . Here is a list of transfers for this wallet.
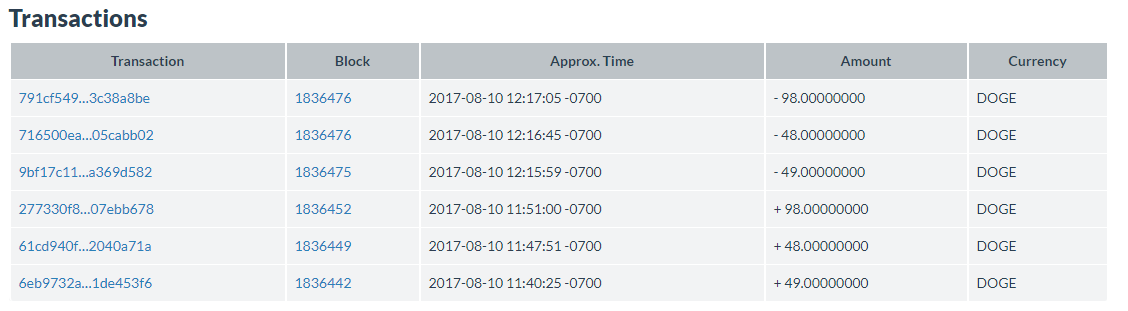
I came across cryptocurrencies, but I did not have to track operations, and this turned out to be a problem for me. Here, the transfer of coins is carried out through intermediate wallets, which forward these coins through other wallets and so on. This whole scheme can be tracked through the Maltego program, which is part of KaliLinux and Parrot OS, and you could also use online services that could do this automatically. In the process of solving it, he did it in a rather simple way - he clicked on transactions with outgoing coins from the wallet, choosing the largest amount. As a result of several transitions, I found a wallet where coins flocked. Of course, various mixers would greatly complicate the work, but the developers did not complicate the already difficult life of the participants.
Flag: "DMqh6vFJ5LpdEbJnW5NYhwRmW5tAC69UmG"
Step # 3

This task turned out to be very simple, done in a few minutes. It was necessary to google the wallet, it was mentioned on several forums, here is the forum that attracted my attention thanks to one positive review.
Flag: "w3bg00dua"
Step # 4

This is where the task developers recouped for the ease of the previous task. I had to google this nickname a lot, not finding anything. Small changes in the nickname also did not help. Facebook, VK also did not give results, as did telegrams. But in the process of searching, I found a wonderful service for probing unique names on many social networks. It works on the basis that many social networks allow you to assign an abbreviated url to your account, which is often a person’s nickname. That's what the service gave out.

I was interested in an account on Github , in which there was one repository, and at the bottom of the description there was an email for feedback or suggestions.
I also fooled with the email for a long time, it didn’t go anywhere. After a while, I guessed to enter google + in the search, where I got a link to my accountGlebReed .
Flag: "Gleb Reed"
What is the outcome of this thread? +1000 points, many hours spent working on erroneous solutions. What is the result of the analysis of this legend? Even if a person has a website in Tor and is not attentive enough to information about him on the network, he can be tracked. By wallet, nickname, email, some posts, and so on, and this is done exclusively through the search for information from open sources, not to mention the various closed databases or other features that the special services possess.
Internet fraud

Step # 1
Stuck on this task for a long time. But this is due to lack of experience. It is not difficult to solve, although the site itself caused a lot of questions, which could not be answered. Entering the site I see such a greeting.

It scanned the site in a subdirectory of the dirsearch utility, and it became clear that the site was running on Wordpress. Of course, out of habit, I started scanning with wpscan, and other utilities, looking for vulnerable plugins, but this was not worth doing.
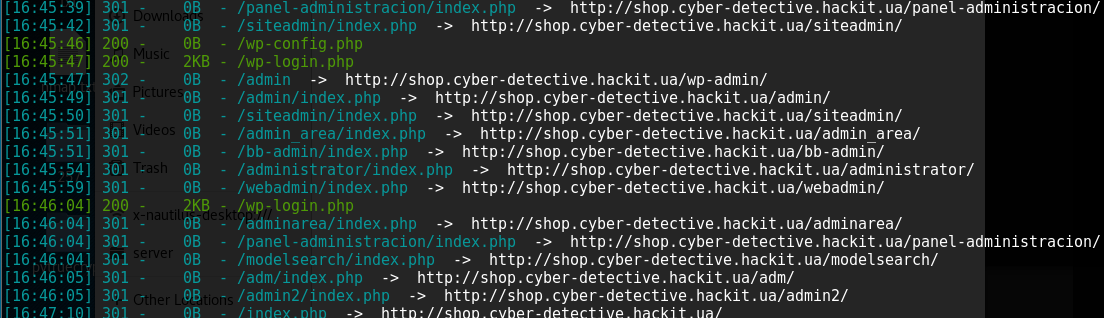
I go to the authorization page , click "Lost your password?" And get to the site page.
Going to some pages, I was redirected to the default page that I saw when I opened the site. However, I didn’t find anything on the site and started googling. The query "site: shop.cyber-detective.hackit.ua" did not return anything. But going to the resourceWeb Archive , found a lot of interesting things. This service allows you to store snapshots of sites. Even if the site is deleted, it is possible to view html pages and some pictures. It is also possible to take pictures of the site yourself. There are pictures in 2 days.
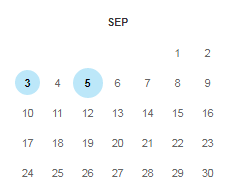
The pictures for the 3rd number are nothing interesting, but for the 5th on the Contacts page there is an email and skype.
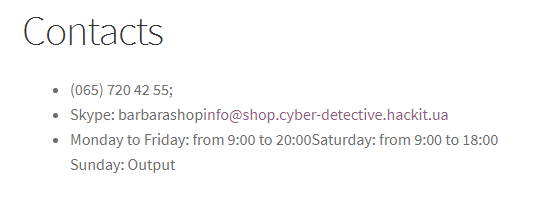
It is worth paying attention to the fact that there is a curve layout. It was done deliberately, or webarchive did it himself, it is not known, but by going to the element inspector, you can see that the email is separated by tags. However, this email is erroneous, you need to continue to search. Skype search didn’t give anything, nor did nickname search. The answer lies in The best clothes wholesale in Ukraine fileWomen's clothes Spring 2017 . Nothing is interesting inside the file, but there was an author in the properties, whose nickname was part of the necessary mail.
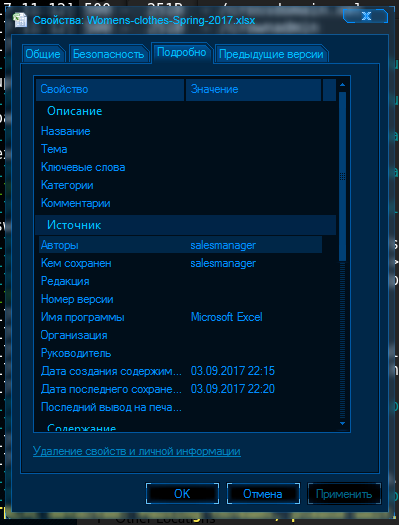
Flag: "salesmanager@shop.cyber-detective.hackit.ua"
Step # 2
It’s immediately clear that here the flag is the IP address. Most likely the recipient's IP address. Sent a letter to this email. There was no response. I must say that sending a letter to info@shop.cyber-detective.hackit.ua, a letter came with a message that it was not delivered. Since there was no answer to my last letter, I began to compose a sniffer to intercept the IP address of the one who opens it. Here's a sniffer for me.
Добрый вечер!
Почему не работает сайт shop.cyber-detective.hackit.ua?

When using, of course, it was not mydomain. There were two scripts on my server, one of which produced a pixel and both recorded IP, UserAgent and other information. Everyone can write such a script without difficulty. However, this did not work, I did not tap anything on the server. But after a couple of hours such a letter arrived in the mail (there was a bot on the server that answered all messages the same way).
We look at the detailed information about the letter.
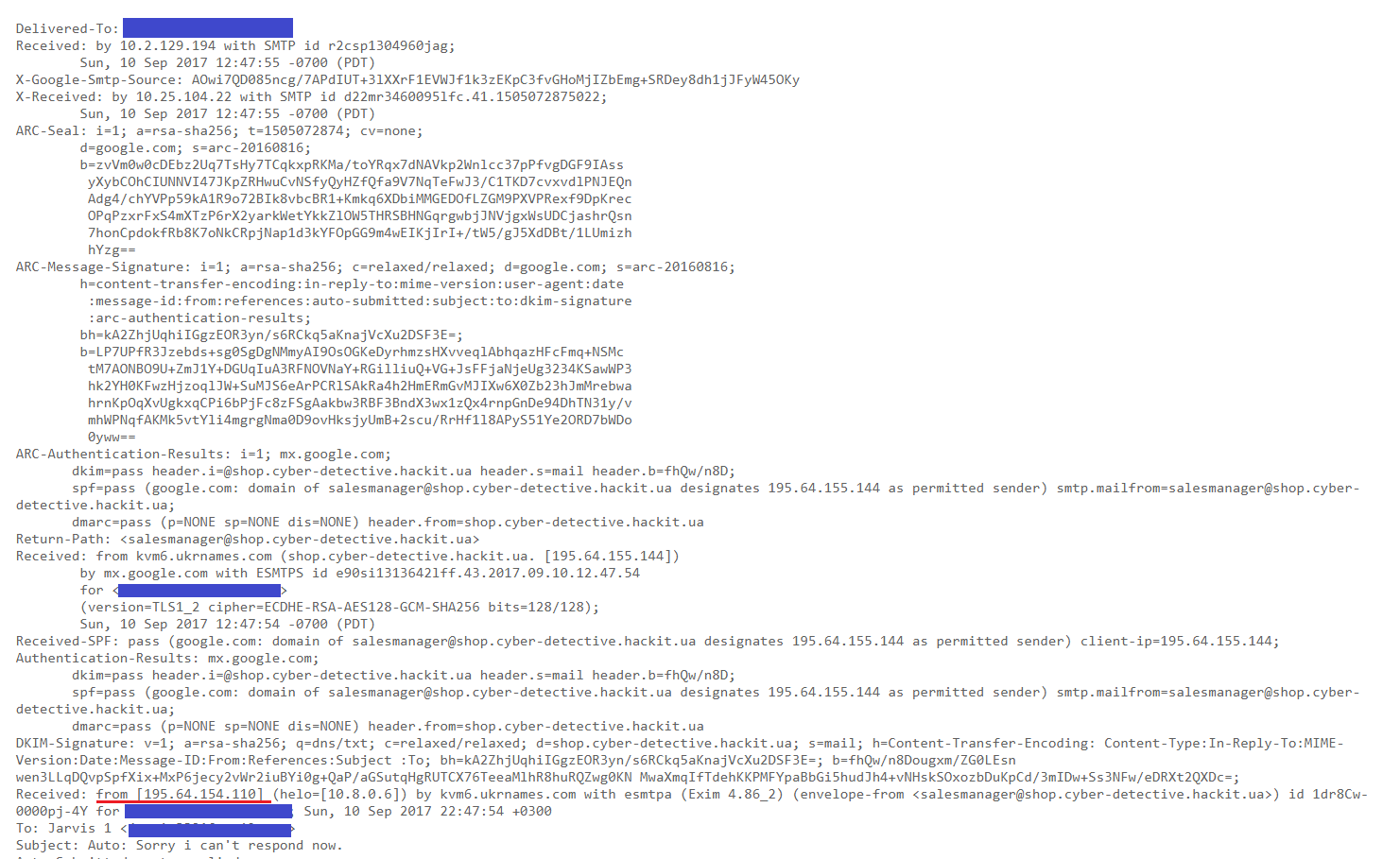
Flag: "195.64.154.110"
Step # 3
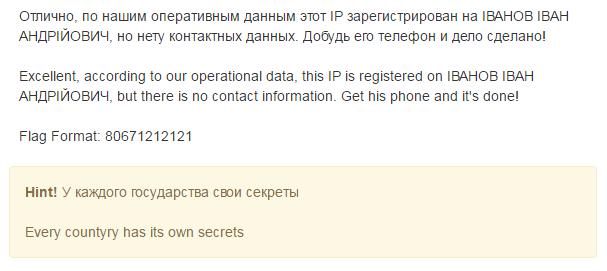
Having little experience in searching by last name, judging by the person’s full name, it is also written in a large register, he suggested that it can be found in some state registry.
The Ministry of Justice did an excellent job of this. I enter the name, I get three people. Empirically, I determine that the person with the registered office of the "Department of Registration of Kharkiv City sake" is suitable.
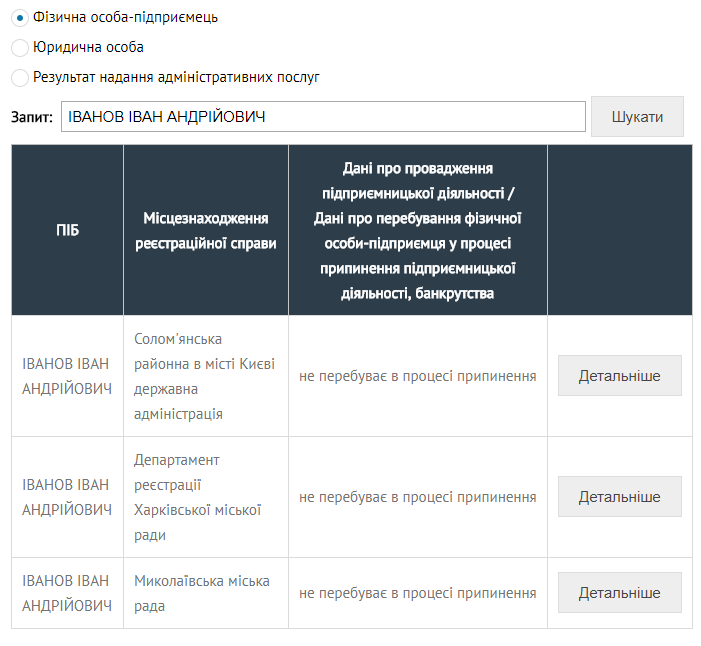
Flag: "80577109515" The
next branch is closed and received +700 points. It was difficult to give only the first task, but we can say that the branch is not complicated.
OLX Fraud

Next, I will describe branches that caused a lot of difficulties, had many false paths, and solving these tasks took a lot of time. I will describe as complexity increases. OLX branch is one of those not so simple.
Step # 1
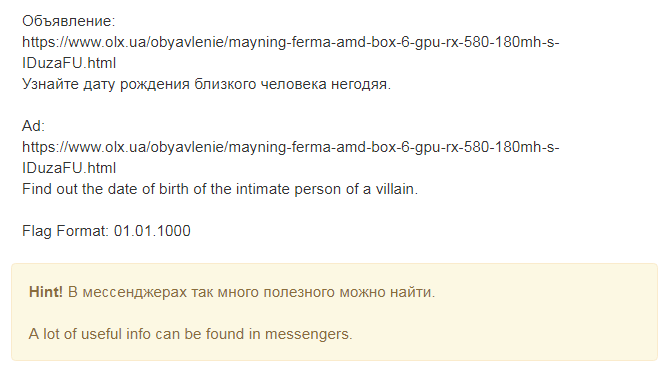
Then he began to compile a dossier with all the information that he found elsewhere. What do I know? The guy’s name is Igor, phone number 380983607320, lives in the Chervonozavodskaya region, in Kharkov, and his farm is like this: “AMD BOX 6 GPU RX 580 180mh / s mining farm”. I found the guy in a telegram, wrote to him, called, but no one answered, and then he went very far to the side, as I understood later. At first I tried to weed out those who are Igor in the VK, about 2 million of them. I chose the male sex, Ukraine, Kharkov, it turned out somewhere around 22 thousand. Perhaps it would be possible to find something if the surname were more exotic. Weed out of 22 thousand did not work. Googling the picture didn’t give anything, but googling the name of the farm gave something interesting. I came across ads on other sites, for example, this. I immediately thought that I was deciding correctly, since the photos are identical. Continued to search and stumbled upon an ad in VK , not so long ago it became possible to sell goods there. I found the guy ’s page and spent a huge amount of time trying to find out the loved ones of this person. It was a false trail. Returning to this task after passing some others, he continued to deal with the telegram account, wrote and called again, and as last time - no one answered. After a while, I was able to understand how to find out a nickname in a telegram, knowing the phone number. And that was the right direction. I added a contact in the telegram, the result is lower. You can try to write something, but they won’t answer.

Then you need to log in to your account, as in the first picture, and in the upper right menu click the “Delete” button. A couple of seconds will turn out like this.
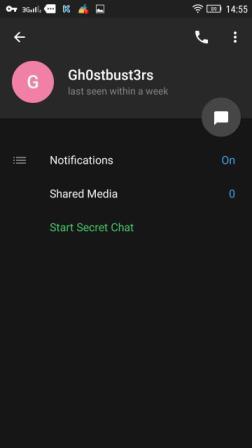
The point is that when we delete this contact, the application does not throw it into the list of dialogs, and the contact does not disappear (where, for example, then send correspondence), and the developers of the telegram decided to replace the number / name with a nickname (and again, do not run to hackerone scribble a report). Nickname - Gh0stbust3rs. I take the previously mentioned service . Here again there was a huge number of wrong moves, since there are a lot of accounts with such a nickname. The right decision was to choose the VK page of this person - Ed Vysotsky . Here you need to go into the groups that he signed and immediately rushed to the group with a small number of subscribers and a strange name.
The administrator of this public Anna Gosteva , who has a marital status with Ed Vysotsky, then this is our goal.
Flag: "04/04/1991"
Step # 2

I punch the girl, her nickname in VK a.gosteva91 and use the service , which has already become my faithful ally against the battle with the tricky tasks of this CTF. I find this account and open it through the mobile application. In the subscribers I find her boyfriend already on Instagram.
I find his photo with a geo-geek, a certain residential complex.

Flag: “LCD“ 5th Avenue “” (standard double quotation marks in the flag)
I would like to note that the complexity of the branch is mainly because the fraudster took photos / materials from the Internet and this greatly complicated the search. It was worth giving more than +300 points for this thread. But in any case, this is not the most difficult branch.
Facke accounts
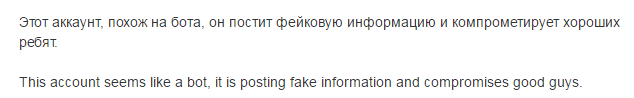
Step # 1
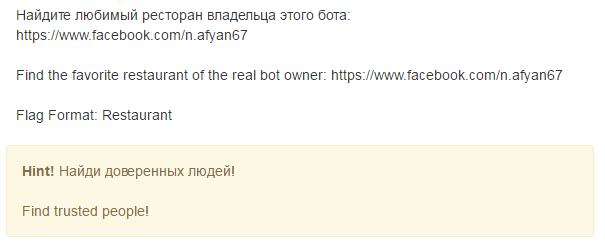
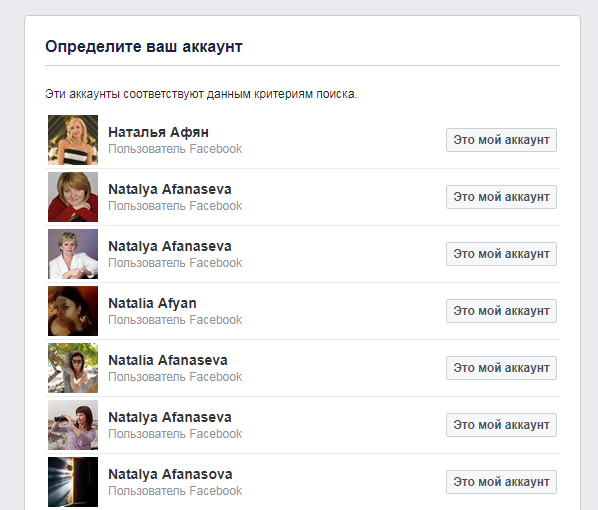
This branch seemed the most difficult. Inquiring about the right decision from the developers, I realized that everything is much simpler there, but it is done through a method known to very few. However, I will first analyze the false paths, then how I did it and how it was necessary. There is Natalya Afyan . Need to find a restaurant, remember. I’m studying the page of this fake in detail. Here is a photo that gives the owner of the original page. The real person is Olga Dyakova , who works at Slow Food Kiev. Feeling that this is not easy, I analyze her page in detail, this does not help. I find some articles about her, here is one of them, which, by the way, was taken almost all the photos for the fake account. Studying all this material yielded nothing. Then he began to analyze the likes that are under some posts on the wall. I didn’t notice anything special. Reposts were made on the wall from popular publics, also looking there is not an option. It remained to analyze the friends of the fake, whom she had 133. Under a fresh cup of coffee, he began to open each page. People whose page is not in Russian or in English skipped. As a result, I highlighted such a page - Mariya Odintsova . She studied at KNURE, from Kharkov, and attracted more posts on the wall, there are two similar to the posts of Natalia Afyan. Studying reposts of this and this posts, studying those who reposted, I see the following.
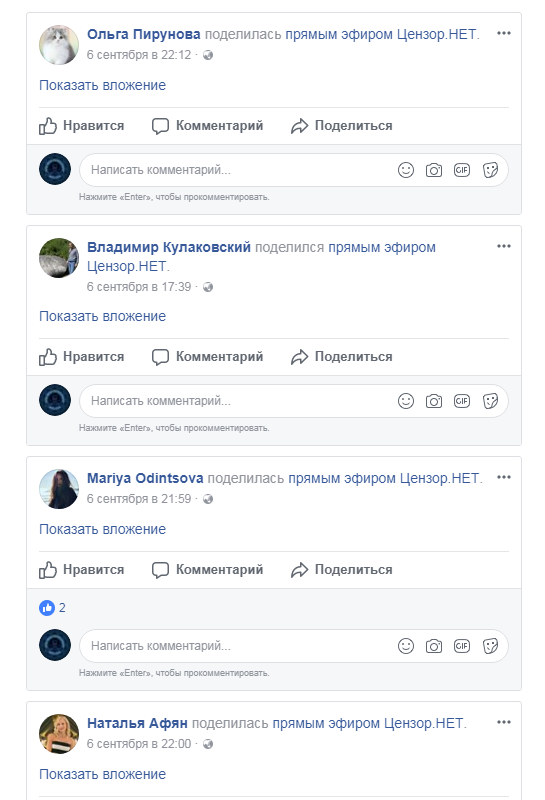
I already know Natalya Afyan and Mariya Odintsova, that's who the first two people are not clear. Vladimir Kulakovsky was a random user, but Olga Pirunova turned out to be very similar to a fake. Checked - in the friends of Natalia Afyan she is. What turns out? A person registered not one, but three fake accounts, added many friends and his other created fakes to each account. Moreover, he reposted 2 identical entries on all three pages. This is strange, but seeing that it was artificially created, I understand that I am moving forward. Here he was stuck again, since not a single page had any useful links to anyone else. After several hours of studying friends, I realized that at least one account is found in the friends of all three fakes - Oleg Stanov . On his page there ispost , on the photo of which you can see the restaurant's napkin holder.
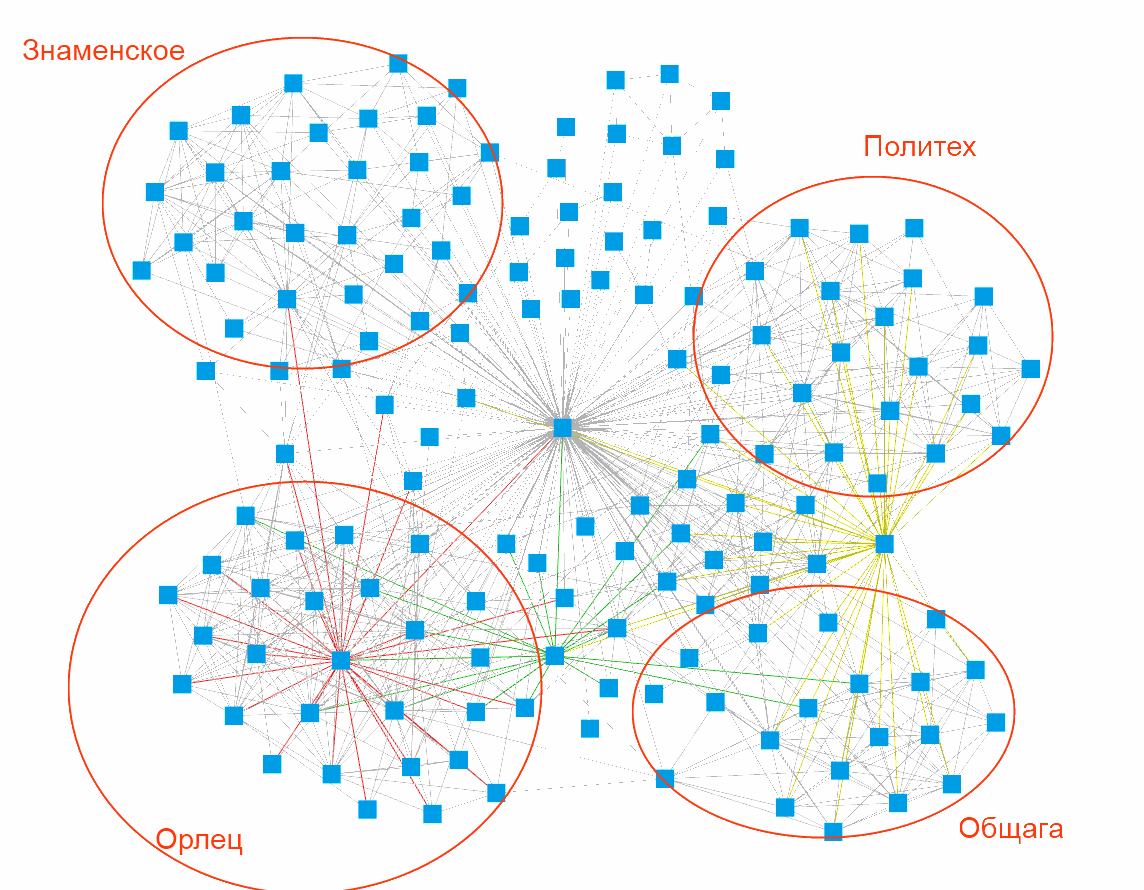
It turns out that not only were three accounts created that added each other as friends and made the same reposts, so the fraudster also added as friends to these accounts. Only after passing the flag it occurred to me that having recognized three fake accounts, it was possible to search for a service for building social graphs, met such ones for VK and based on three fake accounts to find out who united them. Must be for facebook. An example of such a social graph below, taken from the Internet and perfectly illustrates why such a construction.
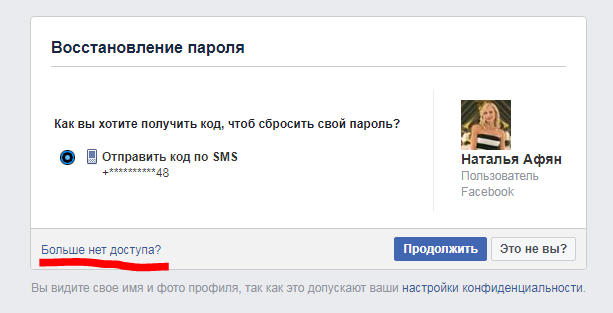
Now about how it was worth deciding. Some of the aforementioned fake likes like this one and this oneposts of Natalia Afyan. Among the likes met and Oleg Stanov. But it is not yet clear that it is he who is the center of the whole thing, it is necessary to continue collecting information. Having come to those who liked Natalya Afyan, one can single out Mariya Odintsova by the method described above. Now we’ll use the Facebook chip, which is not in VK. You need to go to the password recovery page , enter the first and last name.
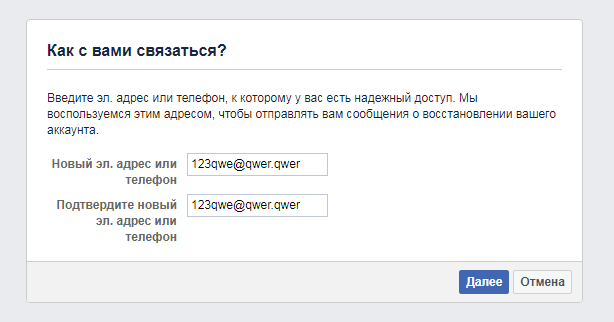
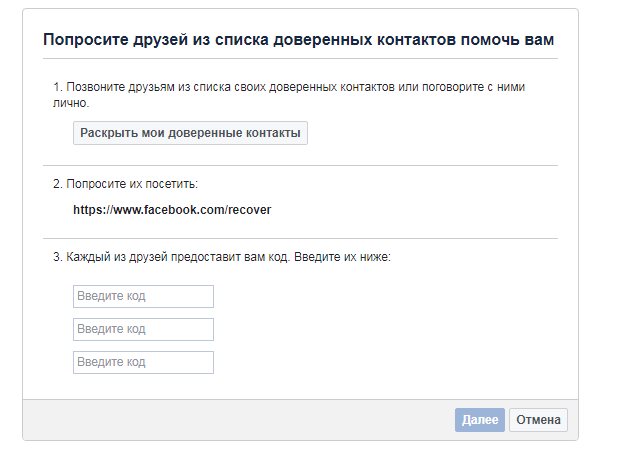
Clicking on “Open my trusted contacts”, you need to enter the distinguished name and surname “Mariya Odintsova”. The list of trusted friends contains two fakes that the creator’s page also found earlier. Next, follow the steps from the method above.

Flag: "Stargorod"
Step # 2
Studying the page, it turns out that a person likes tennis. In this public , to which the person is subscribed, there is a post in the comments to which the goal was unsubscribed.

Flag: “Oleg Sotnichuk”
As I was hinted in the process of writing the article, there are such cases in my life and there are real people who so stupidly connect fake accounts, at first I did not even believe it. For those who do this, read this article and don’t do stupid things, but rather get down to business.
Business and black bookkeeping

This branch is not the most difficult, or confused, but it turned out that he took it seriously at the very end, and other top players also passed the assignments from it last. It will be fair to talk about this thread at the end.
Step # 1
Here is a site opened.
Before getting on the right track, I came across a few false ones. For example, there were several sites that looked similar in appearance to the interface, for example this one . Google also issues cached pages, which at the time of passing CTF were gone. A Google request was site: company.cyber-detective.hackit.ua.

Remembering the web archive from the previous assignment, he also went on a false trail. In fact, it was worth finding a subdomain of the current site, which was not an easy task, this domain was not cached anywhere. The knockpy utility helped.

The resulting cloud.
Flag: "cloud.company.cyber-detective.hackit.ua"
Step # 2
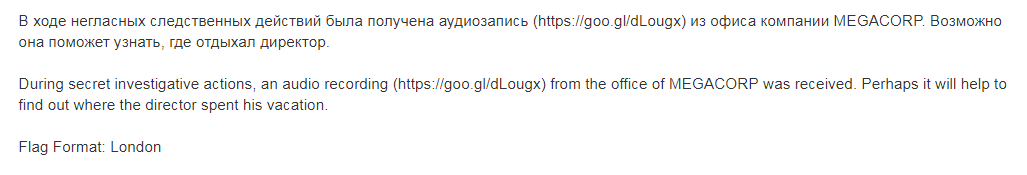
This task was the most fun of all, performed it in a cafe in the bite with pizza, and 2 hours of well-chosen songs were very welcome. The solution is obvious, since it is not standard CTF and there should not be any complex steganography here. Between the songs, a piece of the director’s conversation with the subordinate was inserted, during which the subordinate reported important information. To find a song, Windows Media Player is enough, slowly flipping a music track forward. For lovers of software screen below. The conversation lasted 15 seconds.
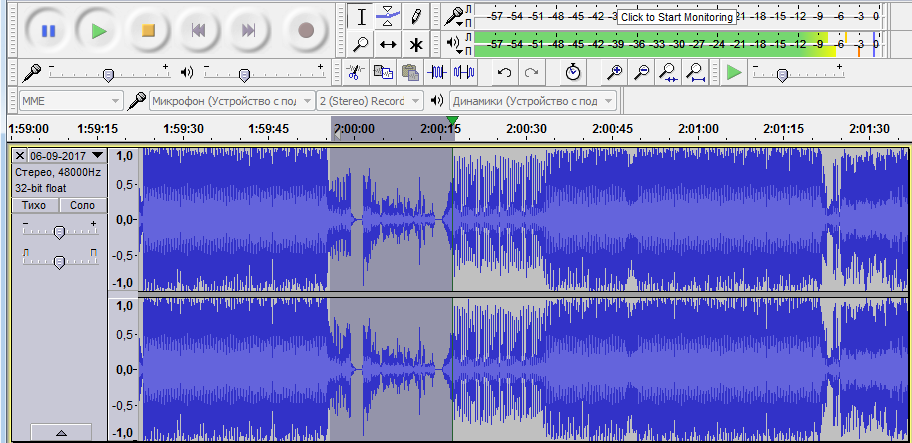
Login: director
Password: Vladimir-1985
Aduacity, a program often used in tasks with musical steganography, illustrates well the inserted conversation. Going back to the cloud . After extracting some files from the recycle bin, I have the following.
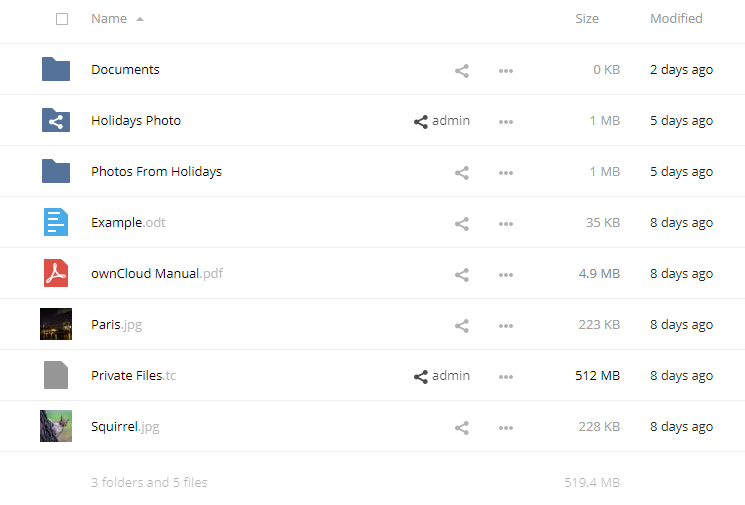
Immediately attracted to the picture with the name Paris.jpg, but the flag did not fit. In the Photos From Holidays folder there were such pictures that, in my opinion, are too cool for photos for an ordinary person. Perhaps this is like a picture-memory for the person who visited there.

Studying exif files using such a service yielded nothing. But the pictures were similar, perhaps from one area. Through a Google search, each picture yielded something like the following.
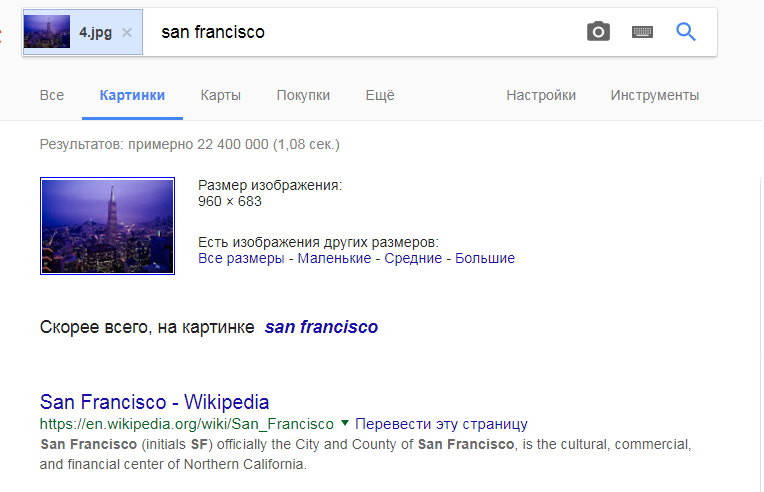
Flag: "San Francisco"
Step # 3
In sticky photographs there were file checksums calculated using the 7-Zip program.
This task was from the Forensic category. There was a file called “Private Files.tc” in the cloud, and the task suggested downloading “20170906.mem”. The first file was a TrueCrypt container, the second one was a memory dump, in which session keys from the container are hidden. For the solution I tried such utilities as pytruecrypt (for decryption using extracted keys), volatility, Elcomsoft Forensi Disk Decryptor. Passware Kit Forensic came up, but it was not possible to decrypt immediately. Only Passware Kit Forensic came up with this cryptocontainer.
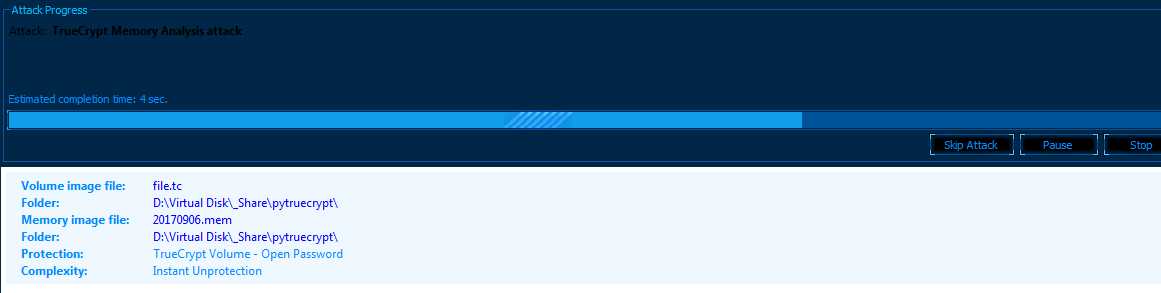
The decryption process is simple, the menu “Full Disk Encryption” -> “TrueCrypt”, then the paths to the container and the memory dump are indicated. Further, the decryption process.
The output is an image that can be mounted in any convenient way. Inside the decrypted container were folders in which there are still many folders, in which there are still many folders.
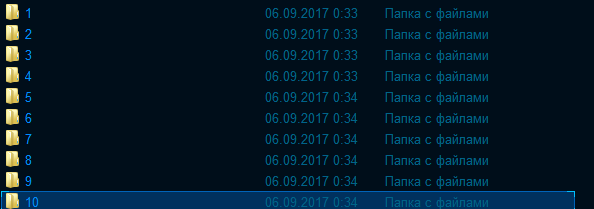
It’s easy to find the desired folder, just look at its size and the number of files included in it. As a result, I found the Exel document.
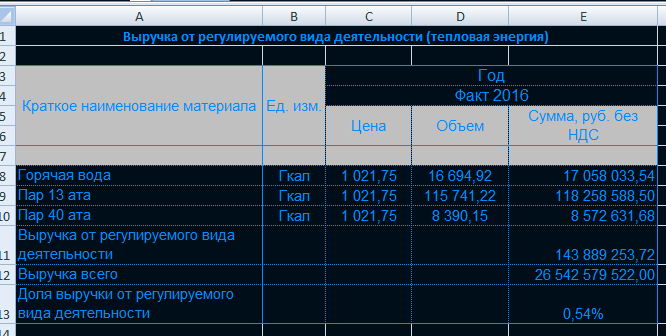
Flag: "26,542,579,522.00"
I happened to participate in a unique CTF, in which there were a huge number of non-standard tasks that I met for the first time. It turned out successfully to take third place, although with more preliminary experience, I could have achieved more. The great fellows were winners, together fighting for the victory for many hours to fly without sleep. I was very pleased with the task of social engineering. There were not very pleasant tasks, but this is as usual on any CTF. The experience was just colossal. I tried to write the article in as much detail as possible, so that anyone interested in the steps could repeat my actions, and moreover, understand the false paths and mistakes that happened to me. This will help to solve such tasks much faster in the future. Tasks are available on the site.another week, go for it! I advise everyone else to be vigilant, in the 21st century the digital footprint is an integral part of life, and you need to think about what to leave on the network.
Dear reader, if you have reached this place, congratulations! I hope you learned something useful from this article. If you have questions or suggestions - Wellcome in PM on VK , Telegram or comments.
