Research: hackers are increasingly leasing trojans
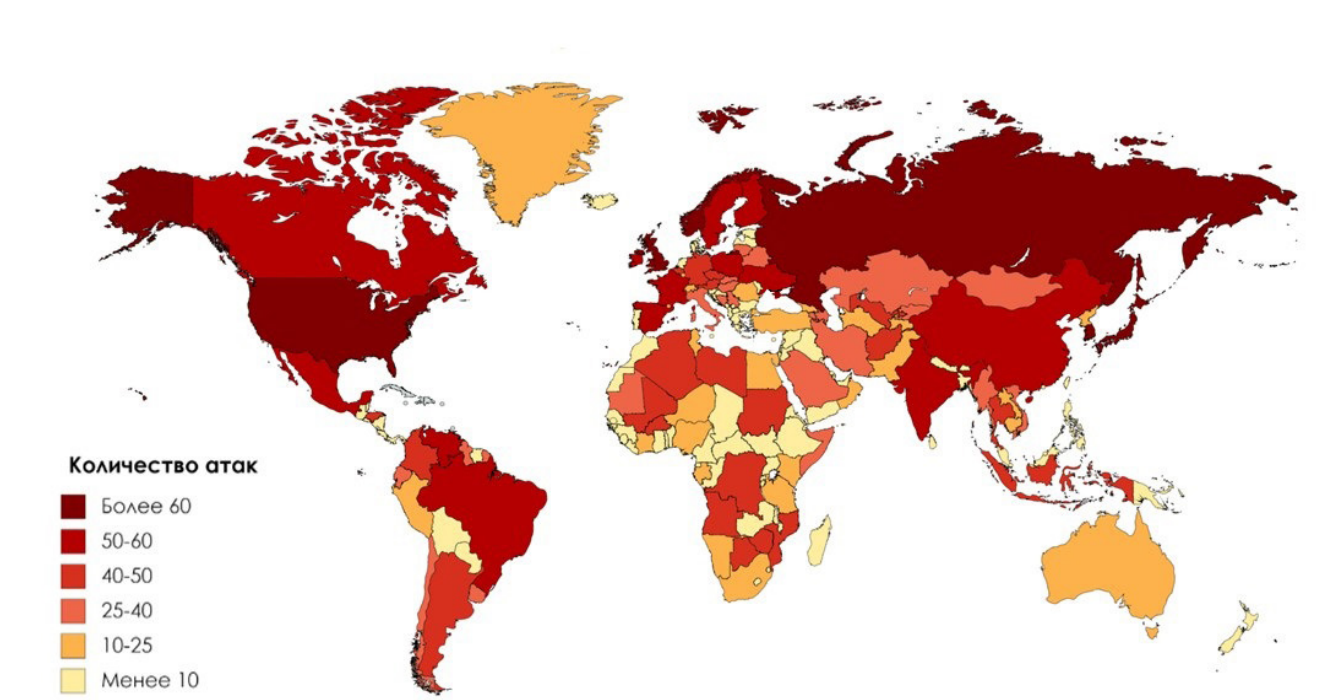
Geography of cyberattacks in the II quarter of 2017
Positive Technologies experts note that in the II quarter of 2017, ransomware as a service for renting Trojans continues to gain popularity. The United States and Russia are still the most frequent victims of cyberattacks, but in the second quarter of 2017, more than a quarter of attacks (28%) were large-scale and affected dozens of countries and hundreds (in some cases, thousands) of companies.
According to statistics from Positive Technologies, 67% of attacks were carried out in order to obtain direct financial benefits. At the same time, more than half of the attacks were massive and mainly used malicious software.
The epidemic of the WannaCry ransomware virus (WanaCypt0r, WCry) showed that you can become a victim of an attack even if you do not open suspicious letters and do not click on the links in them. According to Intel, the total number of infected computers exceeded 530 thousand. WannaCry developers' bitcoin wallets received more than 50 BTC ($ 128,000) from victims, with the total damage to companies exceeding a billion dollars.
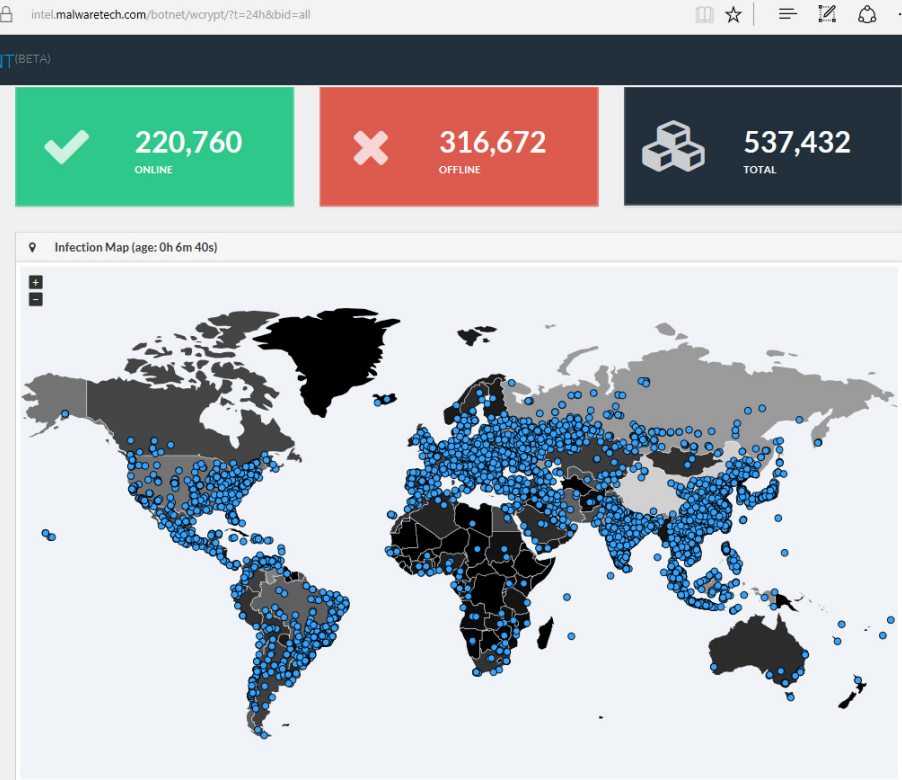
WannaCry Distribution Map
Another large-scale malicious campaign at the end of June was caused by the NotPetya ransomware (also known as ExPetr, PetrWrap, Petya, Petya.A and others). A distinctive feature of this epidemic was that the criminals did not aim at financial gain; they did not seek to send out a recovery key in exchange for payments. Malware was distributed to disable information systems, destroy files, and sabotage. More than 40 victims paid a ransom worth a total of $ 10,000.
The ransomware as a service trend, which Positive Technologies analysts described in a previous report, is gaining momentum. There are new services for renting trojans: for example, the distributor Petya or Mischa receives from 25% to 85% of the total payments made by victims, and another Karmen ransomware Trojan is sold on the black market for $ 175.
While some attackers prefer cryptocurrency to obtain illegal proceeds (victims of cryptographic trojans are invited to transfer money to Bitcoin wallets), others attack cryptocurrency exchanges and their customer accounts. For example, after gaining access to the personal data of 31,800 users of the South Korean exchange Bithumb, attackers were then able to gain access to their accounts. The losses from this attack were estimated at 1 billion won ($ 890,000). In another attack on Tapizon, attackers gained access to four wallets and in total stole about 3816 bitcoins ($ 5.3 million).
Analysts note the emergence of new non-standard chains of penetration into the target system. For example, the Cobalt group used arbitrary vulnerable sites as hosting for malware. During targeted attacks, APT10 members first gained access to the corporate networks of cloud service providers, and then through trusted channels penetrated the network of victim organizations.
While everyone is discussing large-scale attacks of ransomware viruses, attackers are not idle, working on new malware and planning future attacks. For example, researchers are discovering new botnets from IoT devices, but there is little news about new incidents related to highly loaded attacks. We cannot exclude the possibility that attackers are storing resources in order to realize large-scale attacks in the future.
Full study: www.ptsecurity.com/upload/corporate/ru-ru/analytics/Cybersecurity-2017-rus.pdf
On August 24, at 14:00 , Positive Technologies analyst Olga Zinenko will hold a free webinar on current cyber threats in the first half of 2017.
Students will get acquainted with the most popular techniques and mechanisms of cyberattacks, find out which objects are most often attacked by attackers and from which motives they come from. In addition, we will provide organizations and individuals with recommendations on how to protect against typical attacks.
Registration: www.ptsecurity.com/en-us/research/webinar/283988
