How not to break your brain about passwords like eLkdC, lk # jB

You remember the normal strong password figs. Almost an axiom. Security guards also joyfully toss firewood into this fire of horror, forcing them to learn monstrous mincemeat from a mishmash of symbols once a month. Paranoid security measures in the best traditions of “Hacker in the dining room” only lead to the fact that users carefully scratch passwords on the monitor or put under the keyboard. No, seriously, well, who of ordinary users in their right mind will comply with the password requirements in the spirit of:
- Longer than 8 characters
- Contains uppercase, lowercase letters, numbers and special characters,
- Does not repeat any of the previous ones
- Changes monthly.
Let's recall the classic story about paper clips, a battery, correct horses, and at the same time look at a couple of cool offline human-readable password generators. At one time, it greatly facilitated my life.
Entropy
Classic passwords are becoming more difficult for people to remember and easier to pick up for a car. This is unfortunate. On the next very important and secret website with recipes, do you need a ten-digit password in all registers and with numbers? There can be three reasons.
- The site admin is a crypto-paranoid who opens the door to the toilet with an implanted RFID tag.
- The administrator is a little worried about the fact that the current hardware grinds the leaked bases very quickly, and it would be nice to defend at least a bit. You can even salt hashes.
- The admin has completed a three-month course for advanced users, raised the default Wordpress and has no idea what his requirements are.
The two main areas of attack are dictionary search or brute force in the hope of low password length and entropy. Passwords like iloveyou and password are obviously flawed, passwords with low entropy are vulnerable to simple brute force.
Password complexity in the computer industry is usually evaluated in terms of information entropy (a concept from information theory), measured in bits. Instead of the number of attempts that must be made to guess the password, the base 2 logarithm of this number is calculated, and the resulting number is called the number of “entropy bits” in the password. A password with, say, 42-bit complexity calculated in this way will correspond to a randomly generated 42-bit password. In other words, in order to completely search for a password with 42-bit complexity, you need to create 2 42 passwords and try to use them; one of 2 42passwords will be correct. According to the formula, by increasing the password length by one bit, the number of possible passwords will double, which will make the attacker's task twice as difficult. On average, an attacker will need to verify half of all possible passwords before finding the correct one.
Wikipedia
You can estimate the amount of entropy per symbol in the table below.
| Character set | Number of characters, N | Entropy per character, H, bits |
|---|---|---|
| Arabic numerals (0-9) | 10 | 3,3219 |
| Hexadecimal digits (0-9, AF) | 16 | 4,0000 |
| Latin lowercase letters (az) | 26 | 4,7004 |
| Arabic numerals and lowercase Latin letters (az, 0-9) | 36 | 5.1699 |
| Uppercase and lowercase letters of the Latin alphabet (az, AZ) | 52 | 5,7004 |
| Arabic numerals, lowercase and capital letters of the Latin alphabet (az, AZ, 0-9) | 62 | 5.9542 |
| All printable ASCII characters | 95 | 6.5699 |
Paper clips in horses
There is a strong feeling that the ideal password should contain all possible characters, including Sanskrit and a smiling pile of poo. Six and a half bits per character after all! But here we are faced with the applicability problem. It’s very sad to try to reach your server if on the old phone somewhere on a business trip there is no way to enter Arabic characters or hieroglyphs. Ok, we think, and we are moving to a simpler line - az, AZ, 0-9. Almost 6 bits per character. But the trouble is - it is extremely difficult to remember the stuffing in the spirit of Vh8GkCnbqbQDRv. Especially when you consider the undesirability of using the same key in different places. Yes, for an account in Digital Ocean or with a domain registrar, you can and should use passwords of the form gZsa <(Dw} a + * 5p. But such keys require storage in a synchronized encrypted database like KeePassX, otherwise the brain may leak on such a twentieth key.
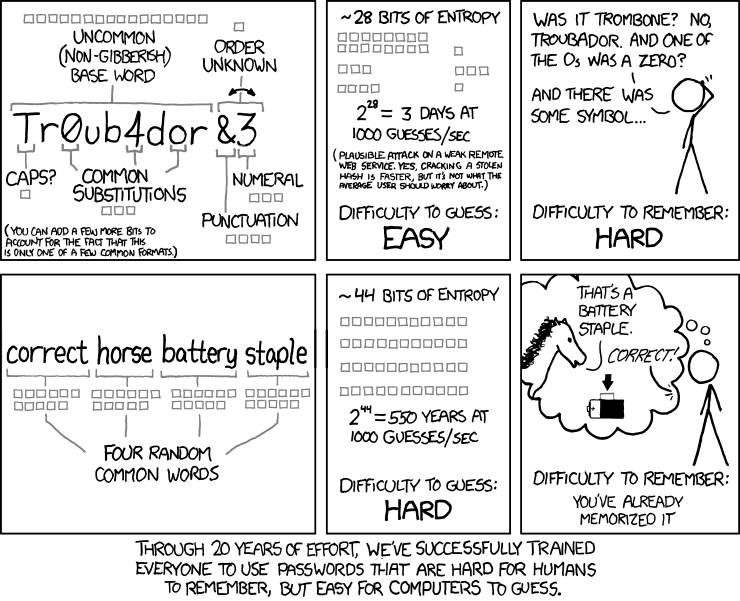
In such cases, a classic comic with a horse and paper clips comes to the rescue, which clearly demonstrates the advantage of long passwords with a relatively low entropy per character.
The password @Vy [o8! B can be quite easily forgotten, although it contains 8 * 6.5699 = 52 bits of entropy. A more compromise version of eastrightcloudexplore is much more cryptographic with ease of storage: 21 * 4.7004 = 99 bits of entropy.
There is even a resource for generating passwords using this algorithm with the talking name correcthorsebatterystaple.net . Although, of course, online password generators are an extremely bad idea. I immediately recall an old parable:
The system administrator wanted to pick up a strong password for centralized authorization through the radius server. He turned to Yin Fu Wo for advice.
- Do you think Master, password "пароль 戰役" is strong?
No, ”answered Yin Master,“ this is a dictionary password. ”
- But there is no such word in dictionaries ...
- "Vocabulary" means that this combination of characters is in wordlists, that is, "dictionaries" for enumeration, which are connected to cryptanalysis programs. These dictionaries are made up of all the combinations of characters that have ever been found on the Web.
- Will the password “Pft, bcm” work?
- Unlikely. It is also vocabulary.
“But what about?” The same ...
- Enter this combination in Google - and you will see.
The system administrator snapped keys.
- Oh yeah. You are right, Master.
After a while, the Sysadmin exclaimed:
- Teacher, I picked up a good password, which can not be in the dictionaries.
Yin Fu Wo nodded.
“I introduced it to Google,” the Sysadmin went on, “and made sure that there wasn’t such a combination on the Web.”
- Now it is.
Offline Password Generators
You can use some option like KeePass, but the result will be a terrible mess, which is difficult to remember. Therefore, programs that create pronounced keys that are easy to remember are a very attractive option. Yes, we sacrifice a bit of entropy, introducing restrictions on combinations of vowels and consonants, but we greatly gain in human readability.
xkcdpass
For starters, you can pay attention to xkcdpass, which works on the principle already voiced above. The installation for Debian-based distributions is quite familiar:
sudo apt-get install xkcdpassYou can also pull the python sources on Github: github.com/redacted/XKCD-password-generator . You can also use pip install. There are even ports on iOS:
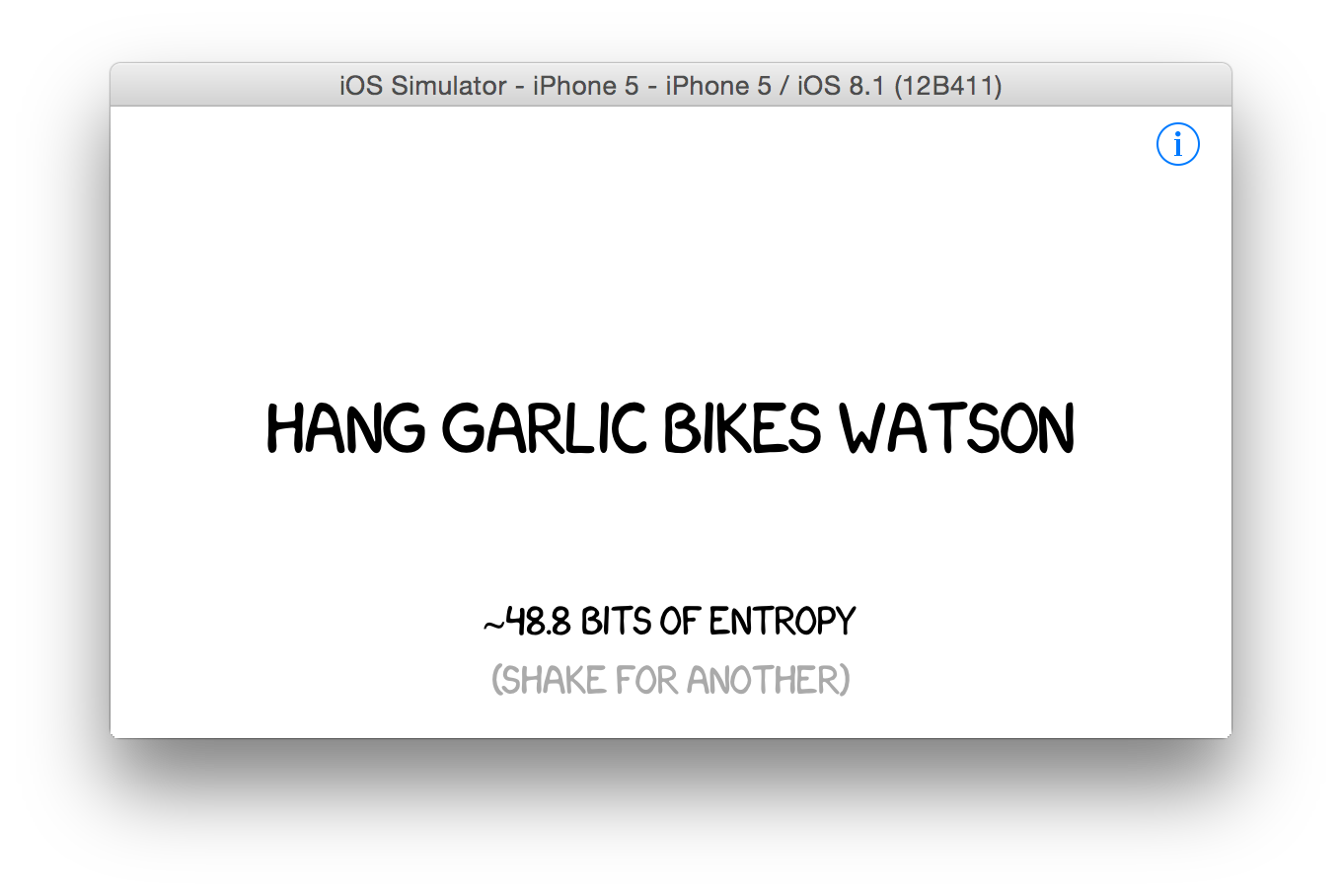
The main feature of this generator is the creation of mnemonic acronym sequences. To do this, use the --acrostic key.
meklon@meklon-desktop:~$ xkcdpass --count=5 --acrostic='habr' --delimiter='|' --min=9 --max=9 --valid_chars='[a-z]'
holograph|archetype|brutishly|refutable
hemstitch|allotropy|balalaika|revivable
hardboard|ampleness|boundless|refurnish
hypertext|adiabatic|backwards|replicate
halfpence|arrowhead|blackbird|recommend
The option with balalaika made me especially happy) The main drawback of this method is the ugly services with password length restrictions. I never understood what exactly they save. Moreover, storing them all the same only a salty hash from the user's key.
pwgen
The classic version. It can generate keys that are easy to remember, as well as truly random sequences. Installation:
sudo apt-get install pwgenThe syntax is simple - pwgen [keys] [password_length] [number of passwords]. The keys can both complicate and simplify the resulting passwords. By default, numbers and uppercase / lowercase letters are used.
meklon@RegenLab-LinuxDesktop-1:~$ pwgen 8 4
eesohy9E Ohqu3che Mo7aijeu ieb1Quie You can reduce entropy a bit and improve readability by throwing numbers away. At the same time, let's extend up to 12 characters to compensate for this (12 * 5.7004 = 68 bits of entropy).
meklon@meklon-desktop:~$ pwgen 12 4 --no-numerals
Eipohliemiwi WoLooJeemeir laishaisaTho oquaibahYoriAdding the --secure option makes passwords unreadable, but completely random:
meklon@meklon-desktop:~$ pwgen 12 4 --secure
YFSb5lqAfSLV nMa5GKJhMmw2 VczwRho2xuwG PPAc6SByedfh
gpw
Another great generator. When constructing passwords, he uses the principle of combining the most common trigrams. The result is extremely pleasant keys for pronunciation:
meklon@meklon-desktop:~$ gpw 4 12
oventryllyna
slytersiderm
raboalsollic
testrisheocu
APG
Advanced Password Generator. A bunch of options and features. In the default version, it is very convenient to split the password into fragments:
meklon@meklon-desktop:~$ apg
Please enter some random data (only first 16 are significant)
(eg. your old password):>
BidKasJuink6 (Bid-Kas-Ju-ink-SIX)
ontEjsed6 (ont-Ej-sed-SIX)
rordOWren4 (rord-O-Wren-FOUR)
yalIkatEac0 (yal-Ik-at-Eac-ZERO)
WruAdNevav1 (Wru-Ad-Nev-av-ONE)
tipBevJieb8 (tip-Bev-Jieb-EIGHT)
There should be a conclusion, but the author is tired
Successful generation)
UPD
I decided to add a utility to check the cryptographic strength of the password. Useless thing, picks a key in dictionaries and evaluates durability.
sudo apt install libcrack2
It is used quite simply. You can feed something sequentially with a script or just drop the password through echo on the input. Let's check the generators from the post:
meklon@RegenLab-LinuxDesktop-1:~$ echo "abc123456" | cracklib-check
abc123456: слишком простой
meklon@RegenLab-LinuxDesktop-1:~$ echo "WruAdNevav1" | cracklib-check
WruAdNevav1: OK
meklon@RegenLab-LinuxDesktop-1:~$ echo "testrisheocu" | cracklib-check
testrisheocu: OK
meklon@RegenLab-LinuxDesktop-1:~$ echo "WoLooJeemeir" | cracklib-check
WoLooJeemeir: OK
The utility looks suspiciously at xkcdpass, but recognizes long passwords from a mixture of dictionary words as valid:
meklon@RegenLab-LinuxDesktop-1:~$ echo "holograph|archetype|brutishly|refutable" | cracklib-check
holograph|archetype|brutishly|refutable: OK
meklon@RegenLab-LinuxDesktop-1:~$ echo "holograph" | cracklib-check
holograph: основан на слове из словаря
meklon@RegenLab-LinuxDesktop-1:~$ echo "archetype" | cracklib-check
archetype: основан на слове из словаря
meklon@RegenLab-LinuxDesktop-1:~$ echo "holograph|archetype" | cracklib-check
holograph|archetype: OK
Thanks for editing in_green_shoes
