PCI DSS Cloud Hosting: Service Details
Some companies whose activities are associated with the processing of customer payment card data use the PCI DSS hosting service. This is due to the fact that meeting the requirements of the standard for infrastructure is a laborious process. For example, the RFI Bank, a bank for Internet entrepreneurs, whose systems are managed by IT-GRAD, uses the services of PCI DSS hosting . The bank leases a secure virtual infrastructure in accordance with the requirements of the PCI DSS standard according to the IaaS model .
As more and more companies pay attention to PCI DSS Compliant Hosting, we want to talk about the details of providing this type of service. / photo kuhnmi CC

The PCI DSS standard was released in 2005 with the aim of bringing the requirements of international payment systems to a common denominator in matters of ensuring the security of cardholder data. Since mid-2012, all organizations (including Russian companies) involved in the storage, processing and transfer of WPC must comply with PCI DSS.
 Determining the need for PCI DSS compliance
Determining the need for PCI DSS compliance
To understand whether a company needs to be audited for PCI DSS compliance, two questions need to be answered:
If you gave a negative answer to both of these questions, then PCI DSS certification is not necessary, otherwise the requirements of the standard become mandatory for the organization. Note that the standard consists of twelve sections and contains about four hundred security requirements for data processing.
We at IT-GRAD conducted a market research and evaluated the options for providing PCI DSS service by various companies. As a result, it was found that the most popular subclasses of PCI DSS hosting were Colocation, IaaS Basic and IaaS Advanced.
It should be noted that when choosing a provider, it is worth paying attention to the prescribed boundaries for the provision of services, which Russian suppliers often boil down to placing equipment in the machine rooms of data centers. This means that the provider provides the Colocation service and fulfills the requirements for ensuring exclusively physical security according to PCI DSS.
If we talk about foreign hosting sites, then providers here most often offer the IaaS Basic service. In this case, the customer himself performs the procedures regulated by the standard, and the supplier configures the edge firewalls, routers, virtualization systems and other components.
The IaaS Advanced service is no less popular when the client receives the most secure cloud on an all-inclusive basis. The customer simply places business applications in the cloud, and most of the PCI DSS requirements are “closed” by the provider.
As for the IT-GRAD company, we provide the service of certified cloud PCI DSS hosting with physical equipment location (Colocation), as well as IaaS Basic and IaaS Advanced services. Next, we consider the features of each type of service.
The service of placing equipment in the data center requires compliance with established safety standards. In this case, means of control and management of access to the data center are used, where video surveillance systems and employee identification systems are mandatory. All equipment placed is located in lockable racks, access to which is regulated. At the same time, the supplier is responsible for regularly conducting an inventory and verifying the operability of devices used in the infrastructure. This is one of the mandatory requirements of the PCI DSS standard.
When providing the IaaS Basic service, the obligations of the supplier and the customer are divided according to the established liability matrix of the parties. The vendor is responsible for the individual components of the client’s infrastructure and makes adjustments in accordance with the developed standards for secure configuration and taking into account PCI DSS requirements.
The allocation of areas of responsibility can be done in different ways. As an example, consider how it works at IT-GRAD. Since our infrastructure uses Web Application Firewall, applications hosted by the client in the cloud can be passed through it, removing some of the requirements for protecting applications.
At the same time, IT-GRAD regularly monitors the emergence of new vulnerabilities, fulfilling the sixth requirement of the PCI DSS standard for updating systems and ranking risks. A change management process has also been introduced, when adjustments to the working system are made only after approval by a special committee. This approach avoids accidental errors.
In addition, the provider’s employees monitor access to network resources, as well as monitor IP events in 24/7/365 mode, so that in the event of an incident, respond quickly.
Infrastructure as a service in Advanced format is a turnkey solution, when the client only develops and supports secure applications, and all other tasks, be it configuring components, shielding, restricting access or encrypting channels and others are implemented by the cloud provider.
To provide the IaaS Advanced service, the provider must comply with certain requirements and apply appropriate technological solutions. Let's consider a few of them using the example of IT-GRAD.
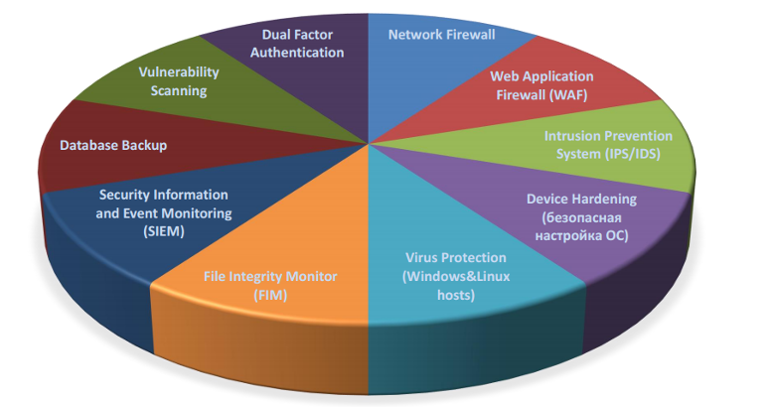 Technology Solutions for IaaS Advanced Service
Technology Solutions for IaaS Advanced Service
The first requirement is Dual Factor Authentication. For example, in the IT-GRAD infrastructure, an OTP server is used that generates one-time tokens, with which users perform a VPN connection with a forward to the DMZ zone, where the management and administration node is located. Connecting to this node allows you to perform administrative tasks and access individual components of the infrastructure.
The second requirement is a network firewall that delimits networks into zones. In this case, we follow the principle of "what is not allowed is forbidden." The provider’s infrastructure also uses the Palo Alto system, equipped with the IPS / IDS function, to identify unauthorized access situations and take measures to eliminate emerging threats. Also here, a centralized anti-virus protection server with installed agents on the customer’s hosts is often used. This allows for the detection of virus messages to quickly generate incidents and organize mailing with the subsequent response of the CM-system to a recorded event.
Another requirement is to ensure the integrity of application files (File Integrity Monitor). If changes are made, the checksum changes, which becomes the reason for the automatic creation of the incident. In addition, FIM monitors critical Windows and Linux files. As part of working with file integrity, we also take daily snapshots of virtual machines so that we can “roll back” to the original operating state in the event of an emergency.
Thus, using the PCI DSS hosting service , the client receives a number of advantages, including cost savings and a guarantee of a quick start of the project. This approach simplifies the implementation of the requirements of the standard and the passage of the audit and makes it possible to focus on the core business development.
In conclusion, I would like to note that a company offering a PCI DSS hosting service must have a valid certificate, and the boundaries of the service provided must correspond to the value of the managed service provider. This suggests that the provider has the right to provide PCI DSS hosting services, divided into classes Colocation, IaaS Basic and IaaS Advanced.
As more and more companies pay attention to PCI DSS Compliant Hosting, we want to talk about the details of providing this type of service. / photo kuhnmi CC

A few words about the standard
The PCI DSS standard was released in 2005 with the aim of bringing the requirements of international payment systems to a common denominator in matters of ensuring the security of cardholder data. Since mid-2012, all organizations (including Russian companies) involved in the storage, processing and transfer of WPC must comply with PCI DSS.

To understand whether a company needs to be audited for PCI DSS compliance, two questions need to be answered:
- Is payment card data stored, processed or transmitted in your organization?
- Can the business processes of your organization directly affect the security of payment card data?
If you gave a negative answer to both of these questions, then PCI DSS certification is not necessary, otherwise the requirements of the standard become mandatory for the organization. Note that the standard consists of twelve sections and contains about four hundred security requirements for data processing.
Details of PCI DSS Hosting Services
We at IT-GRAD conducted a market research and evaluated the options for providing PCI DSS service by various companies. As a result, it was found that the most popular subclasses of PCI DSS hosting were Colocation, IaaS Basic and IaaS Advanced.
It should be noted that when choosing a provider, it is worth paying attention to the prescribed boundaries for the provision of services, which Russian suppliers often boil down to placing equipment in the machine rooms of data centers. This means that the provider provides the Colocation service and fulfills the requirements for ensuring exclusively physical security according to PCI DSS.
If we talk about foreign hosting sites, then providers here most often offer the IaaS Basic service. In this case, the customer himself performs the procedures regulated by the standard, and the supplier configures the edge firewalls, routers, virtualization systems and other components.
The IaaS Advanced service is no less popular when the client receives the most secure cloud on an all-inclusive basis. The customer simply places business applications in the cloud, and most of the PCI DSS requirements are “closed” by the provider.
Related Sources: PCI DSS Certification
As for the IT-GRAD company, we provide the service of certified cloud PCI DSS hosting with physical equipment location (Colocation), as well as IaaS Basic and IaaS Advanced services. Next, we consider the features of each type of service.
Colocation
The service of placing equipment in the data center requires compliance with established safety standards. In this case, means of control and management of access to the data center are used, where video surveillance systems and employee identification systems are mandatory. All equipment placed is located in lockable racks, access to which is regulated. At the same time, the supplier is responsible for regularly conducting an inventory and verifying the operability of devices used in the infrastructure. This is one of the mandatory requirements of the PCI DSS standard.
IaaS Basic
When providing the IaaS Basic service, the obligations of the supplier and the customer are divided according to the established liability matrix of the parties. The vendor is responsible for the individual components of the client’s infrastructure and makes adjustments in accordance with the developed standards for secure configuration and taking into account PCI DSS requirements.
The allocation of areas of responsibility can be done in different ways. As an example, consider how it works at IT-GRAD. Since our infrastructure uses Web Application Firewall, applications hosted by the client in the cloud can be passed through it, removing some of the requirements for protecting applications.
At the same time, IT-GRAD regularly monitors the emergence of new vulnerabilities, fulfilling the sixth requirement of the PCI DSS standard for updating systems and ranking risks. A change management process has also been introduced, when adjustments to the working system are made only after approval by a special committee. This approach avoids accidental errors.
In addition, the provider’s employees monitor access to network resources, as well as monitor IP events in 24/7/365 mode, so that in the event of an incident, respond quickly.
IaaS Advanced
Infrastructure as a service in Advanced format is a turnkey solution, when the client only develops and supports secure applications, and all other tasks, be it configuring components, shielding, restricting access or encrypting channels and others are implemented by the cloud provider.
To provide the IaaS Advanced service, the provider must comply with certain requirements and apply appropriate technological solutions. Let's consider a few of them using the example of IT-GRAD.

The first requirement is Dual Factor Authentication. For example, in the IT-GRAD infrastructure, an OTP server is used that generates one-time tokens, with which users perform a VPN connection with a forward to the DMZ zone, where the management and administration node is located. Connecting to this node allows you to perform administrative tasks and access individual components of the infrastructure.
The second requirement is a network firewall that delimits networks into zones. In this case, we follow the principle of "what is not allowed is forbidden." The provider’s infrastructure also uses the Palo Alto system, equipped with the IPS / IDS function, to identify unauthorized access situations and take measures to eliminate emerging threats. Also here, a centralized anti-virus protection server with installed agents on the customer’s hosts is often used. This allows for the detection of virus messages to quickly generate incidents and organize mailing with the subsequent response of the CM-system to a recorded event.
Another requirement is to ensure the integrity of application files (File Integrity Monitor). If changes are made, the checksum changes, which becomes the reason for the automatic creation of the incident. In addition, FIM monitors critical Windows and Linux files. As part of working with file integrity, we also take daily snapshots of virtual machines so that we can “roll back” to the original operating state in the event of an emergency.
Thus, using the PCI DSS hosting service , the client receives a number of advantages, including cost savings and a guarantee of a quick start of the project. This approach simplifies the implementation of the requirements of the standard and the passage of the audit and makes it possible to focus on the core business development.
In conclusion, I would like to note that a company offering a PCI DSS hosting service must have a valid certificate, and the boundaries of the service provided must correspond to the value of the managed service provider. This suggests that the provider has the right to provide PCI DSS hosting services, divided into classes Colocation, IaaS Basic and IaaS Advanced.



