Check Point Security CheckUP - R80.10. Part 3
- Tutorial
The third and final part regarding the possibility of conducting a free network security audit using Check Point Security CheckUP . If you missed the past parts:
Having completed the installation and initialization, we can proceed with the configuration itself. A large number of pictures will follow. If you are too lazy to read, then you can subscribe to our YouTube channel , where soon there will be a video instruction on CheckUP.
The first step is to adjust the network topology, as shown in the figure below. We should have two interfaces.
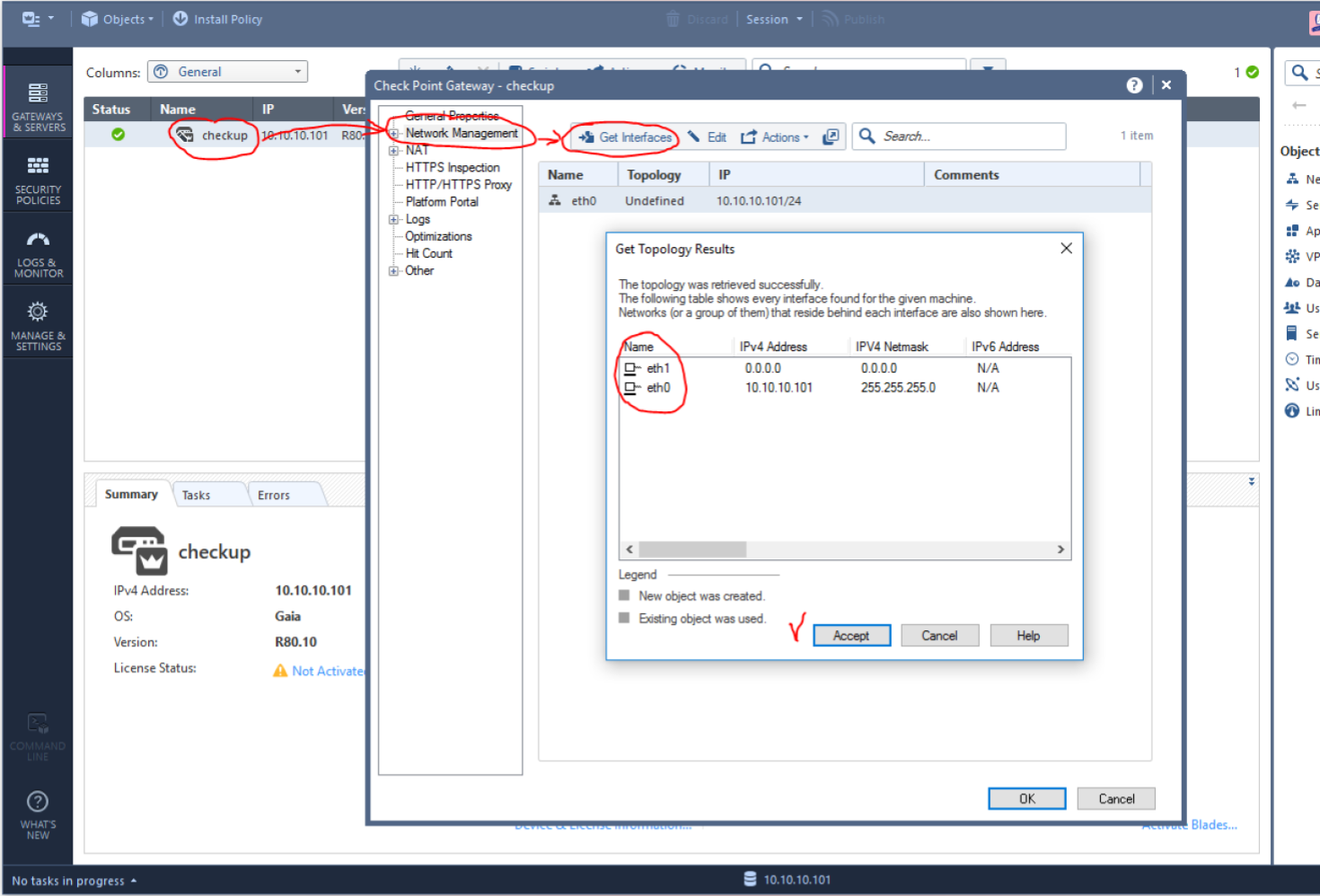
Next, we must define the first interface (which is used to control and access the Internet) as Internal, enable anti-spoofing in detect mode and disable logging (so as not to clutter up the report):

We will definitely define the second interface as External with the same anti-spoofing settings.
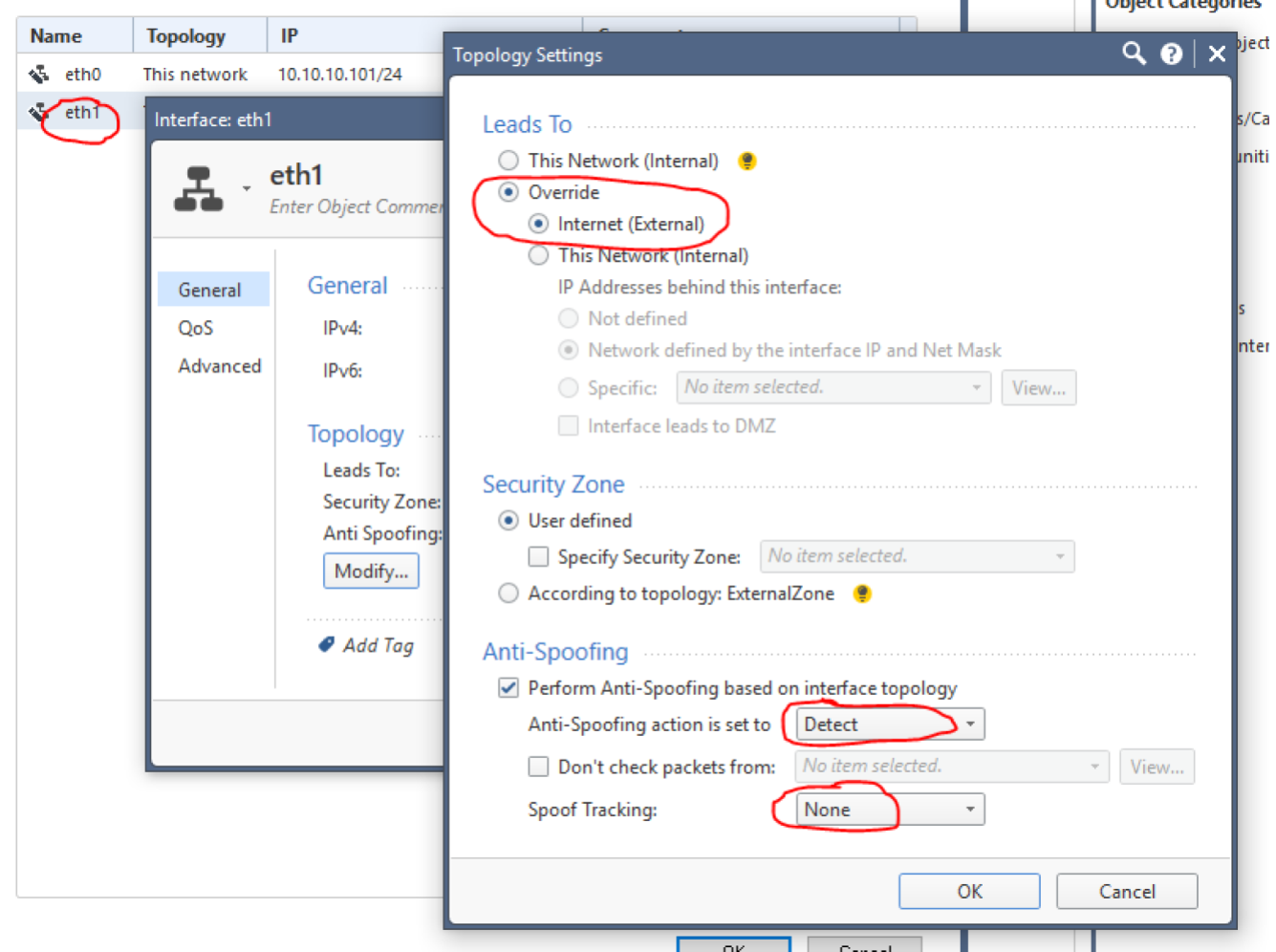
The result should be the following:

Now you can proceed to turn on the blades. To do this, double-click on the gateway properties and start ticking off the necessary blades (Application Control, URL Filtering, IPS ...):
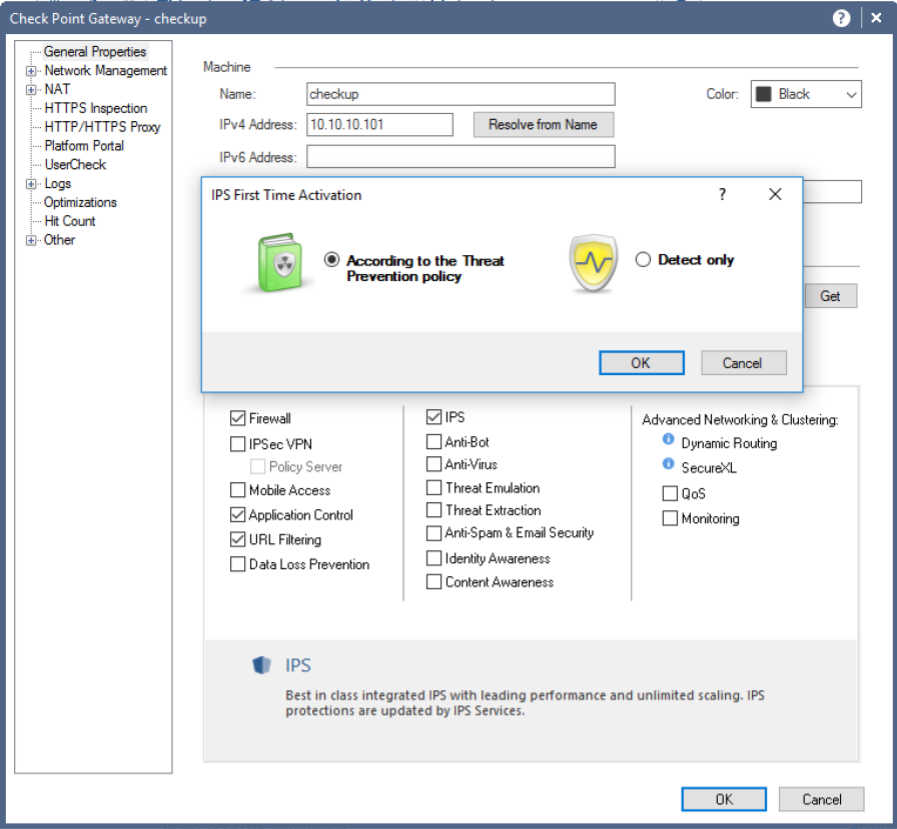
If you try to enable Threat Emulation, you will
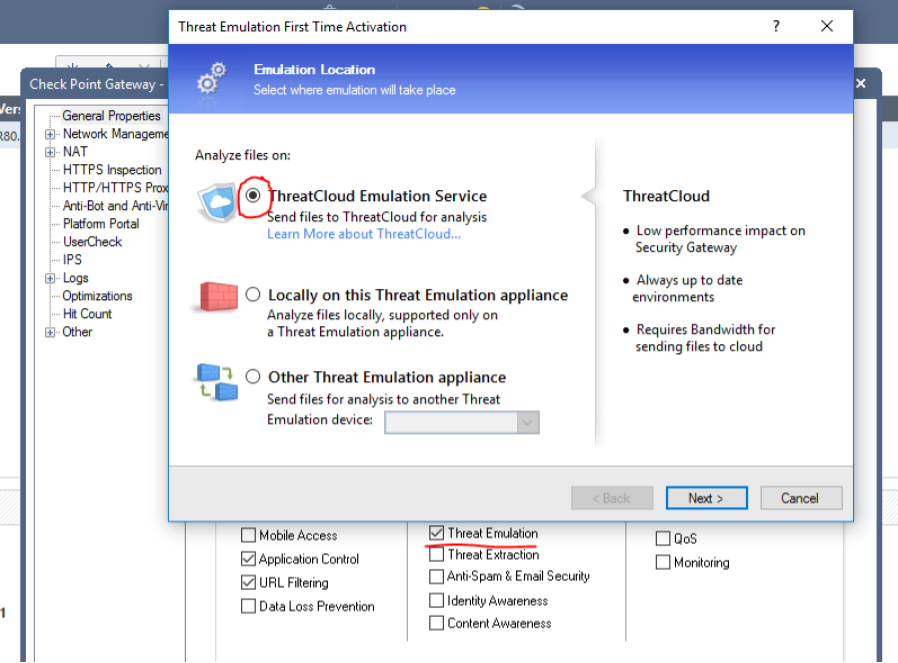
find an error:
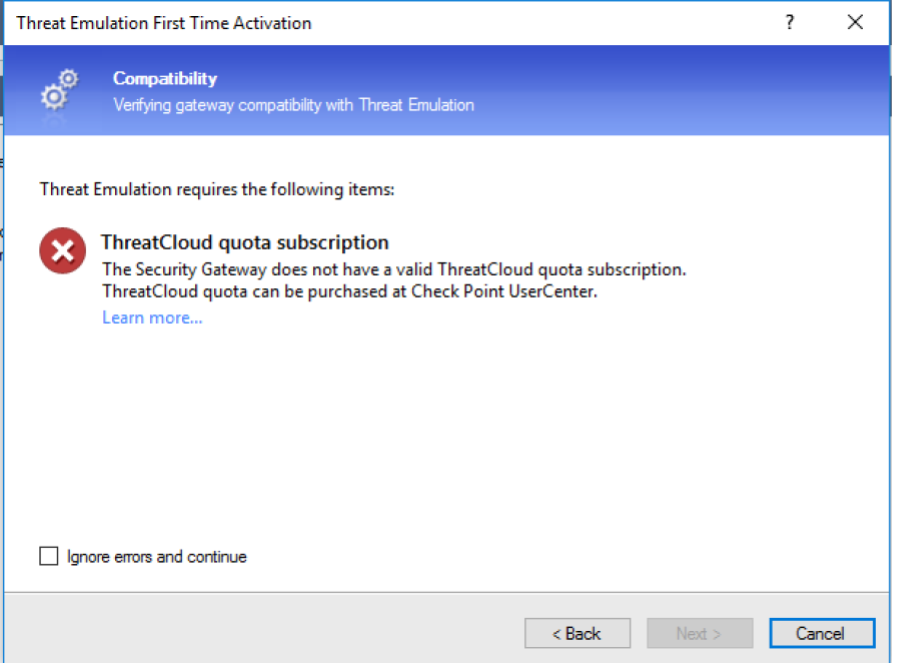
Unfortunately, Trial mode does not include the cloud sandbox function for 15 days ( Threat Emulation). If this feature is really needed, then you can request a demo license for a month.
To identify users (namely username, but to ip addresses), you need to configure integration with AD using the Identity Awareness blade
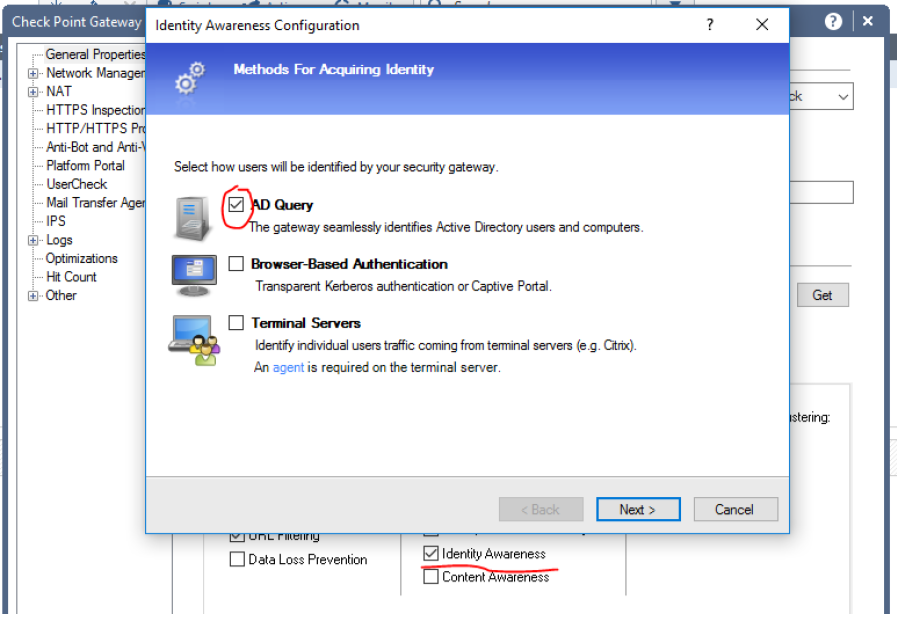
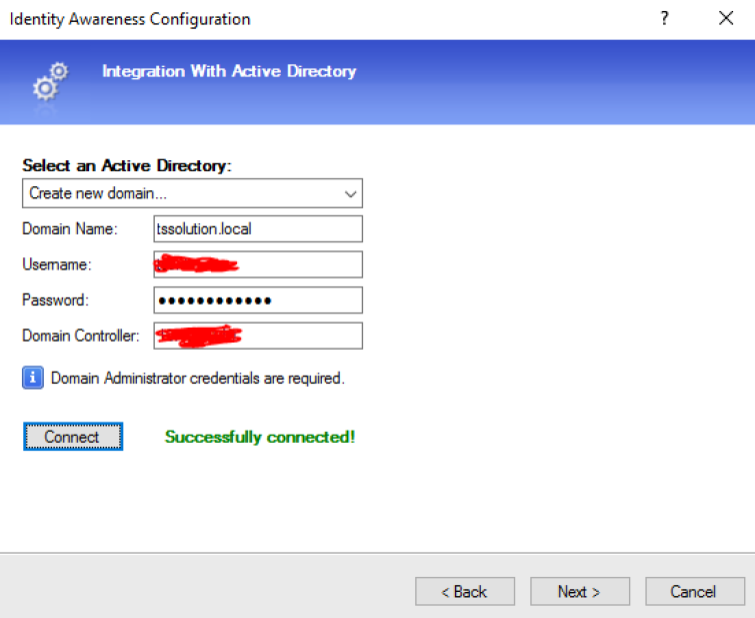
For this, an account with admin rights is used. In fact, Check Point connects to the AD server and grabs logs related to user authentication, after which it can map the user to his IP address. After specifying the domain, credentials and ip address of the AD server, we must successfully connect:
By enabling the necessary Network Security blades, we can go to the Management tab and enable the Smart Event blade:

This blade allows you to generate complex reports.
After that, do not forget to click Ok, and not just close the window. Now you can move on to customizing some of the blades. Let's start with Application Control. Specify the settings as shown below:
Do the same for the Threat Prevention blade:
Now you can go to the policy settings. Let's start with the usual firewall. Naturally allow all traffic and turn off logging. These logs are absolutely not interesting in the report and only increase the load on the device when they are processed:
Now Application Control and URL filtering. By default, this policy is absent (unlike R77.30) and in order to fix this, you must first enable them. This is done as follows:
Add a new Layer:
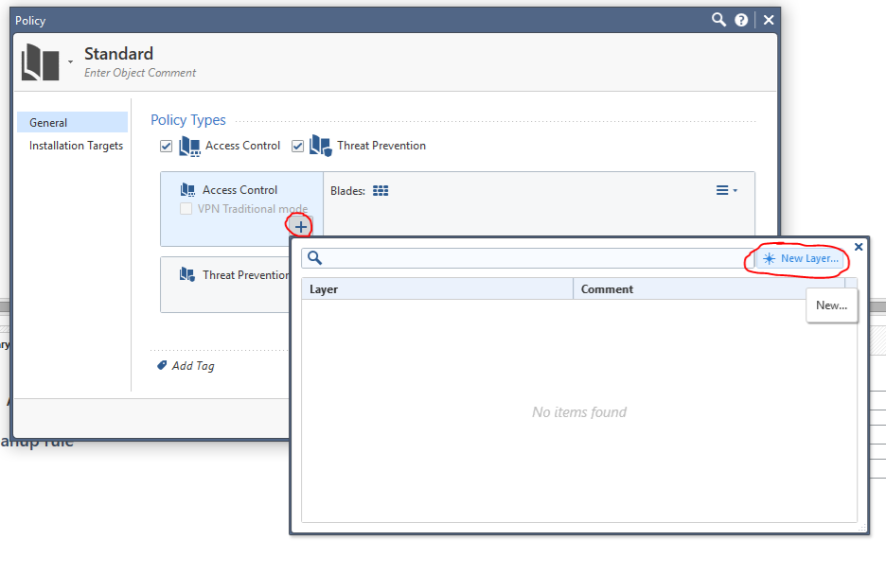
with the name Apllication and mark only one blade:

It should turn out the following:

Now Application has appeared in the policies. Allow all traffic:
And be sure to enable Detaild Log and Accounting:
Then we can try updating the databases:
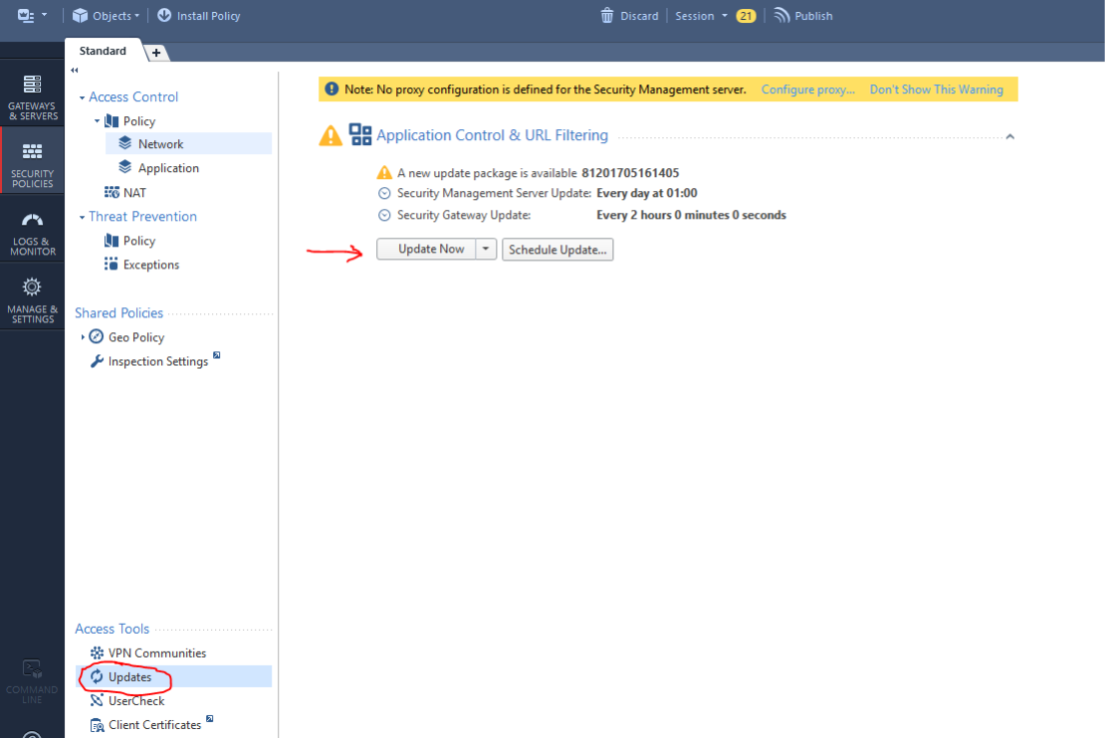
The update process will be displayed in the lower left corner. Wait for it to finish:

Now you can go to the Threat Prevention policy settings. The default policy with the Optimized profile is set: You

need to adjust the settings. Double-click on the profile properties and set everything to Detect mode (there is no point in Prevent on traffic copies):
In the Anti-Virus settings, turn on “deep” scanning and archive checking:
In Threat Emulation settings (if you got a license) we enable emulation for all supported files:
When you click Ok, we are prompted to save the profile under a new name: After
saving, set it in the Threat Prevention policies (right-click on the profile):
Now you can go to the Updates section and try to update IPS and other blades:
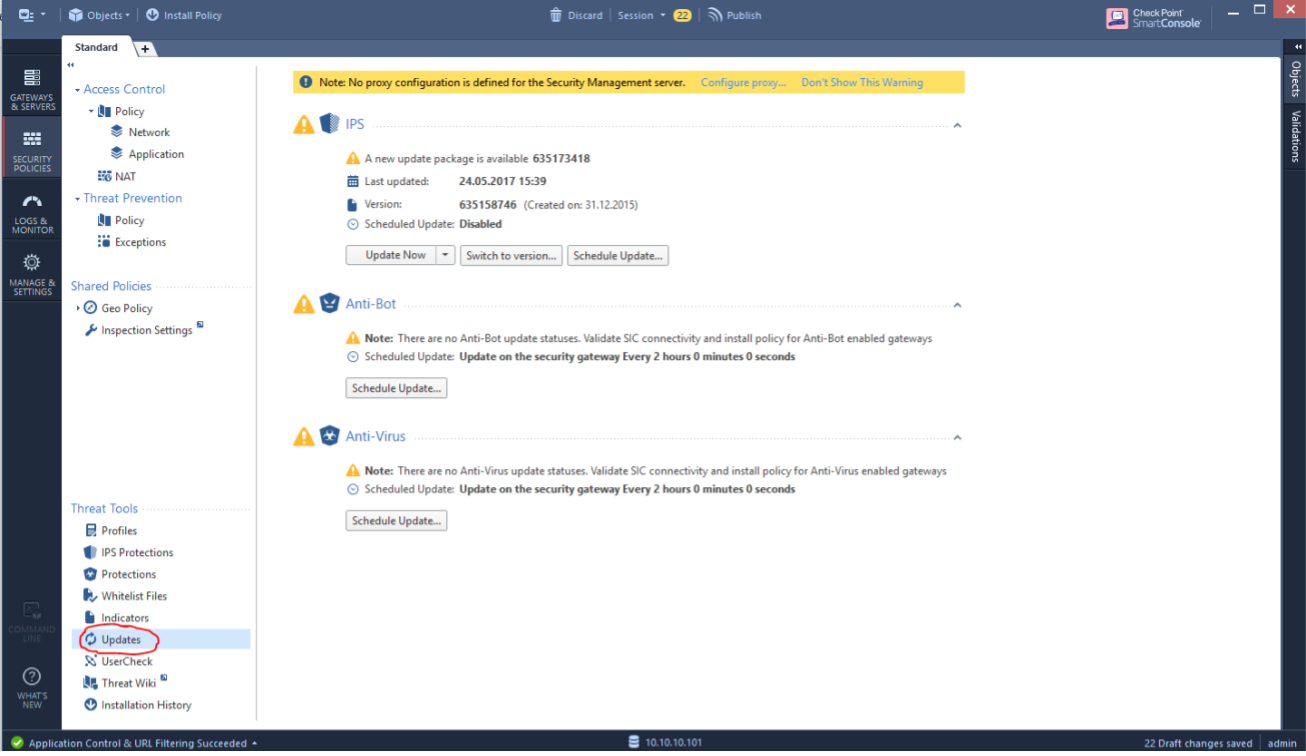
In addition, you need to go to the Check Point global properties:
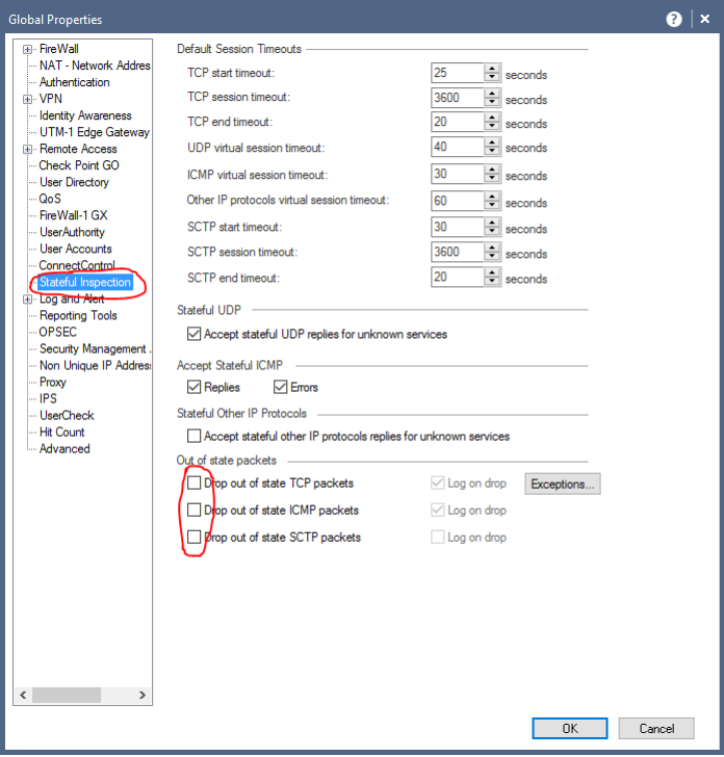
And disable Drops, as in the picture below:
Now you need to install the policies. Click Install Policy:

First, check only Access Control (Threat Prevention cannot be installed without this policy):

After successful installation, click Install Policy again and select only Threat Prevention:
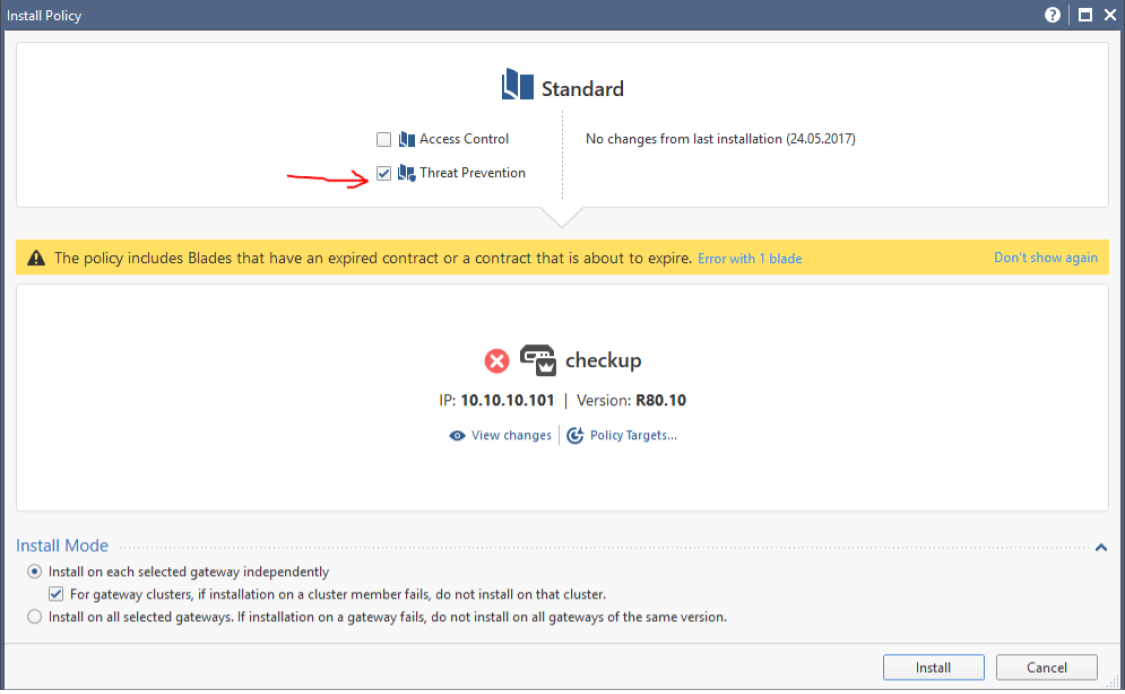
Done! If you configured the SPAN port correctly, then Check Point should already begin to process traffic. To verify this, you can go to the Logs & Monitor tab and filter logs for example by the Apllication Control blade:
If all is well, then leave logging for at least one day, after which you can see the statistics by clicking on New Tab - Reports - Security CheckUP Advanced. You
should have the following:
You can download this report in PDF format, while it is possible to make the report anonymous, those. Exclude parameters by which your organization can be identified.
The desired time to collect statistics is two weeks. An example report can be found here .
In this "simple" way, you can conduct an express analysis of the security of your network. We sincerely hope that this information is useful to someone. If you have any questions, you can feel free to contact . I repeat, soon on our channel video instruction will be posted.
