VMware NSX for the smallest. Part 1

If you look at the configuration of any firewall, then most likely we will see a sheet with a bunch of IP addresses, ports, protocols and subnets. This is how classically implemented network security policies for user access to resources. At first, they try to maintain order in the config, but then employees start to move from department to department, servers multiply and change their roles, access for different projects appears where they usually cannot be, and hundreds of unknown goat trails are obtained.
About any rules, if lucky, the comments are spelled out “I asked Vasya to do it” or “This is a passage in the DMZ”. The network administrator quits and everything becomes completely incomprehensible. Then someone decided to clean the config from Vasya, and SAP fell, because Vasya once asked for this access for the combat SAP operation.
Today I will talk about the solution of VMware NSX, which helps point-to-point apply the policy of network interaction and security without confusion in the firewall configs. I will show you what new features appeared compared to what VMware used to have in this part.
VMWare NSX is a platform for virtualizing and securing network services. NSX solves problems of routing, switching, load balancing, firewall and can do many other interesting things.
NSX is the successor to its own VMware vCloud Networking and Security (vCNS) product and Nicira NVP purchased.
From vCNS to NSX
Previously, a client in a cloud built on VMware vCloud had a separate vCNS vShield Edge virtual machine. It served as an edge gateway, where you could configure many network functions: NAT, DHCP, Firewall, VPN, load balancer, etc. vShield Edge limited the interaction of the virtual machine with the outside world according to the rules prescribed in Firewall and NAT. Inside the network, virtual machines communicated freely among themselves within subnets. If you really want to separate and conquer traffic, you can make a separate network for individual parts of applications (different virtual machines) and write the corresponding rules on the firewall according to their network interaction. But it is long, difficult and uninteresting, especially when you have several dozen virtual machines.
In NSX, VMware implemented the concept of microsegmentation using a distributed firewall (distributed firewall) embedded in the core of the hypervisor. It contains security and network policies not only for IP and MAC addresses, but also for other objects: virtual machines, applications. If NSX is deployed within an organization, then a user or group of users from Active Directory can become such objects. Each such object turns into a microsegment in its security loop, in the required subnet, with its cozy DMZ :).

Previously, the security perimeter was one for the entire pool of resources, protected by a border switch, and with the NSX you can protect a separate virtual machine from unnecessary interactions even within the same network.
Security policies and network interactions are adapted if the object moves to another network. For example, if we move a machine with a database to another network segment or even to another related virtual data center, the rules prescribed for this virtual machine will continue to operate regardless of its new position. The application server will still be able to interact with the database.
The vCNS vShield Edge border gateway itself has been replaced by the NSX Edge. He has the whole gentlemanly set of the old Edge plus some new useful features. About them, and will be discussed further.
What's new in NSX Edge?
The functionality of the NSX Edge depends on the edition of the NSX. There are five of them: Standard, Professional, Advanced, Enterprise, Plus Remote Branch Office. All new and interesting can be seen only since Advanced. Including the new interface, which until the full transition of vCloud to HTML5 (VMware promises the summer of 2019) opens in a new tab.
Firewall You can select IP addresses, networks, gateway interfaces, and virtual machines as objects to which the rules will be applied.
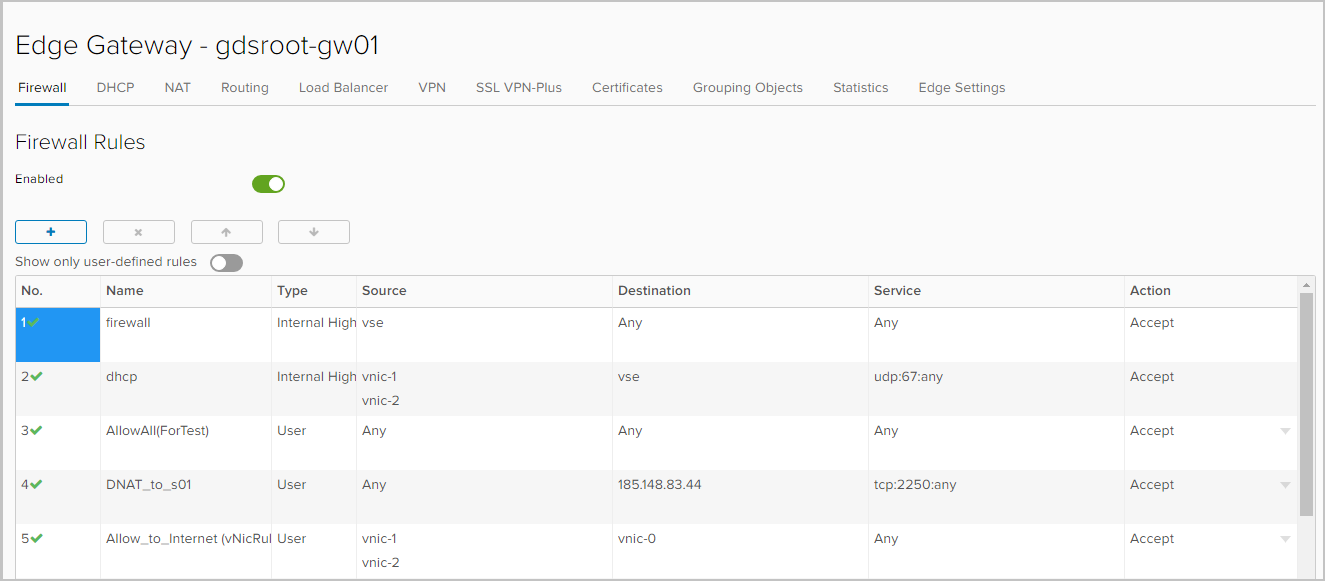

DHCP. In addition to setting the range of IP addresses that will automatically be issued to the virtual machines of this network, the Binding and Relay functions are now available in NSX Edge .
In the Bindings tabYou can bind the MAC address of the virtual machine to the IP address if you want the IP address to remain unchanged. The main thing is that this IP address is not included in the DHCP Pool.

In the Relay tab, you can configure the relay of DHCP messages to DHCP servers that are located outside your organization in vCloud Director, including the physical infrastructure DHCP servers.

Routing With vShield Edge, you could only configure static routing. This is where dynamic routing appeared, supporting OSPF and BGP protocols. ECMP (Active-active) settings have also become available, and therefore active-active failover to physical routers.

Configure OSPF

Configure BGP
Another of the new - setting up the transfer of routes between different protocols, the
redistribution of routes (route redistribution).

L4 / L7 Load Balancer. Appeared X-Forwarded-For for HTTPs header. Without him, everyone cried. For example, you have a website that you are balancing. Without forwarding this header, everything works, but in the web server statistics you did not see the visitors IP, but the balancer IP. Now everything was right.
Also in the Application Rules tab you can now add scripts that will directly control traffic balancing.

VPN. In addition to IPSec VPN, NSX Edge supports:
- L2 VPN, allowing you to stretch the network between geographically separated sites. Such a VPN is needed, for example, so that when moving to another site, the virtual machine remains on the same subnet and stores the IP address.

- SSL VPN Plus, which allows users to connect remotely to the corporate network. At the vSphere level, such a function was, but for vCloud Director this is an innovation.

SSL certificates. You can now put certificates on NSX Edge. This is again to the question of who needed a balancer without a certificate for https.

Grouping Objects. In this tab, groups of objects are defined for which certain network interaction rules will be applied, for example, firewall rules.
These objects can be IP and MAC addresses.


It also contains a list of services (protocol-port combination) and applications that can be used to compose firewall rules. New services and applications can be added only by the administrator of the vCD portal.


Statistics. Connection statistics: traffic that passes through the gateway, firewall and balancer.
Status and statistics for each IPSEC VPN and L2 VPN tunnel.

Logging In the Edge Settings tab, you can set the server for logging. Logging works for DNAT / SNAT, DHCP, Firewall, routing, balancer, IPsec VPN, SSL VPN Plus.
The following types of alerts are available for each object / service:
- Debug
- Alert
- Critical
- Error
- Warning
- Notice
- Info

NSX Edge Sizes
Depending on the tasks and volumes, VMware recommends creating an NSX Edge of the following sizes:
| NSX Edge (Compact) | NSX Edge (Large) | NSX Edge (Quad-Large) | NSX Edge (X-Large) | |
| vCPU | one | 2 | four | 6 |
| Memory | 512MB | 1GB | 1GB | 8GB |
| Disk | 512MB | 512MB | 512MB | 4.5GB + 4GB |
| Purpose | One application, test data center | Small or medium data center | Loaded firewall | Load balancing at L7 level |
The table below shows the working metrics for network services, depending on the size of the NSX Edge.
| NSX Edge (Compact) | NSX Edge (Large) | NSX Edge (Quad-Large) | NSX Edge (X-Large) | |
| Interfaces | ten | ten | ten | ten |
| Sub Interfaces (Trunk) | 200 | 200 | 200 | 200 |
| NAT Rules | 2,048 | 4,096 | 4,096 | 8,192 |
| ARP Entries Until Overwrite | 1,024 | 2,048 | 2,048 | 2,048 |
| FW Rules | 2000 | 2000 | 2000 | 2000 |
| FW Performance | 3Gbps | 9.7Gbps | 9.7Gbps | 9.7Gbps |
| DHCP Pools | 20,000 | 20,000 | 20,000 | 20,000 |
| ECMP Paths | eight | eight | eight | eight |
| Static routes | 2,048 | 2,048 | 2,048 | 2,048 |
| Lb pools | 64 | 64 | 64 | 1,024 |
| LB Virtual Servers | 64 | 64 | 64 | 1,024 |
| LB Server / Pool | 32 | 32 | 32 | 32 |
| Lb health checks | 320 | 320 | 320 | 3,072 |
| LB Application Rules | 4,096 | 4,096 | 4,096 | 4,096 |
| L2VPN Clients Hub to Spoke | five | five | five | five |
| L2VPN Networks per Client / Server | 200 | 200 | 200 | 200 |
| IPSec Tunnels | 512 | 1,600 | 4,096 | 6,000 |
| SSLVPN Tunnels | 50 | 100 | 100 | 1,000 |
| SSLVPN Private Networks | sixteen | sixteen | sixteen | sixteen |
| Concurrent session | 64,000 | 1,000,000 | 1,000,000 | 1,000,000 |
| Sessions / Second | 8,000 | 50,000 | 50,000 | 50,000 |
| LB Throughput L7 Proxy) | 2.2Gbps | 2.2Gbps | 3Gbps | |
| LB Throughput L4 Mode) | 6Gbps | 6Gbps | 6Gbps | |
| LB Connections / s (L7 Proxy) | 46,000 | 50,000 | 50,000 | |
| LB Concurrent Connections (L7 Proxy) | 8,000 | 60,000 | 60,000 | |
| LB Connections / s (L4 Mode) | 50,000 | 50,000 | 50,000 | |
| LB Concurrent Connections (L4 Mode) | 600,000 | 1,000,000 | 1,000,000 | |
| BGP Routes | 20,000 | 50,000 | 250,000 | 250,000 |
| BGP Neighbors | ten | 20 | 100 | 100 |
| BGP Routes Redistributed | No limit | No limit | No limit | No limit |
| OSPF Routes | 20,000 | 50,000 | 100,000 | 100,000 |
| OSPF LSA Entries Max 750 Type-1 | 20,000 | 50,000 | 100,000 | 100,000 |
| OSPF Adjacencies | ten | 20 | 40 | 40 |
| OSPF Routes Redistributed | 2000 | 5000 | 20,000 | 20,000 |
| Total routes | 20,000 | 50,000 | 250,000 | 250,000 |
From the table it can be seen that balancing on NSX Edge for productive scenarios is recommended to be organized only from the Large size.
Today I have everything. In the following sections, I’ll go through the details of configuring each NSX Edge network service.
