Integrated Automation with Ansible and OpenStack
- Transfer
- Tutorial
- Recovery mode
Ansible solutions guarantee maximum flexibility. This allows the community to find ever new ways to use Ansible modules to automate frequently performed operations at many levels, including in combination with OpenStack technologies.
In this blog, we will discuss numerous uses for Ansible, the most popular automation software (software), together with OpenStack, the most popular cloud infrastructure software. We will help you understand how and why you should use Ansible to make your life easier with Full-Stack Automation, as we like to call it.
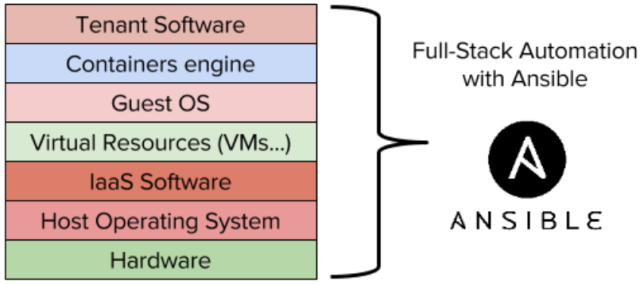
To begin with, we will discuss the levels of integrated automation shown in the diagram above. Below we have equipment (servers, storage systems and network equipment). Next is the operating system (Linux or Windows). On Linux, you can install OpenStack to abstract from the physical resources of the data center and deploy the software version of computing resources, networks, and storage. On top of OpenStack, tenant-specific services are deployed to create the virtual machines on which the applications will run. Finally, you must provide operating system management (Linux or Windows) to deploy the applications and workloads that you really need (databases, web servers, mobile application servers, etc.). If you use containers (e.g. Docker or Rkt), You will pack these applications into images that will then be deployed over the guest OS. In addition, the concept of application servers has appeared in some languages, which adds another layer (for example, J2EE).
Ansible provides modules for managing each layer. Even for network equipment, more precisely, if you approach this from a technical point of view, for a network operating system such as IOS or NXOS (see the full list of Ansible network modules ).
1. Standard interaction with the operating system: installing packages, changing or enforcing content or file permissions, managing services, creating and deleting users and user groups, etc.
2. Software for implementing the Infrastructure as a Service (IaaS) concept: Install IaaS software and related components (databases, load balancers, configuration files, services, and other supporting tools).
3. Virtual resources: configure resources, such as a virtual machine or instance, by determining the size, access rights, content, security profile, network connection settings, etc.
4. Guest OS: the components are similar to those of the host OS. But how do you know how many guest systems you have?
5. Container management module (optional).
6. Leased software: databases, web servers, load balancers, data processing modules, etc.
As you already understood, some functions are available only in the latest versions of Ansible, for example 2.2. However, your OS version may have an older version. For example, in RHEL 7 or CentOS 7 you will find only Ansible 1.9.
Given that Ansible is a command-line tool written in Python that does not prohibit multiple versions of the system, you may not need the security enhancement in Ansible that your assembly offers, and you might want to try out the latest version.
However, as with any other Python software, there are many dependencies, so it is not recommended to use unverified new libraries with the system ones. Libraries can be shared by other components of your system, and unverified newer versions can disrupt other applications. The easiest way is to install the latest version of Ansible with all the dependencies in an isolated folder under your unprivileged account. This will be the Python Virtual Environment (virtualenv), and if you do everything right, you can safely try out the latest Ansible modules for complex orchestration. Not recommended , of course.apply this practice in a production environment. This is nothing more than an exercise to help you improve your DevOps skills.
1. Install the required components (pip, virtualenv)
In this case, we need only one "system-wide" Python library - virtualenvwrapper. In addition, you should not run the sudo pip install command, as this will replace the Python system libraries with newer unverified versions. In this case, we can only trust the virtualenvwrapper library. A virtual environment is an efficient mechanism for installing and testing new Python modules in your unprivileged user account .
In addition, if your account is other than sudoer, you can use the following commands.
2. Install a new virtual environment where we will deploy the latest version of Ansible.
First, create a directory for storing virtual environments.
Then add the following lines to your .bashrc file:
export WORKON_HOME = $ HOME / .virtualenvs
source /usr/bin/virtualenvwrapper.sh
Now run the source command for this file.
At this point, shell links are created, but only at the first start. Run the workon command to view a list of environments; it should not be empty. Next, we will create a new virtualenv environment called ansible2 , it will be activated automatically and gain access to packages installed by default using RPM.
Type deactivate to exit virtualenv , and workon to re-enter.
3. Enter the new virtualenv environment and install Ansible2 via PIP (as a regular user, without root rights).
You will see that the request to enter a command in the shell has changed and the name virtualenv is indicated in brackets.
This command will only install dependencies for Ansible 2 using your system-wide Python packages available in RPM (thanks to the system-site-packages flag that we used earlier). An alternative if you want to try out the development branch.
If you need to remove the virtualenv environment and all its dependencies, simply enter the rmvirtualenv ansible2 command.
NOTE. If the above commands did not work, make sure that the GCC and OpenSSL libraries are installed on your systems, as some Python dependencies use the latest cryptographic modules.
4. Install OpenStack Client Dependencies
The first command in the code snippet below ensures that you have the latest stable version of the OpenStack API, however you can also use the pip install command to get the latest command-line tool (CLI). The second command provides the latest version of the Python Shade library for connecting to the latest versions of the OpenStack API using ansible, regardless of the specific CLI tool.
5. Test your deployment
NOTE. You cannot run this version of ansible outside the virtual environment of virtualenv, so always run the workon ansible2 command before usi.
Attentive readers will notice that using Ansible to orchestrate OpenStack, we seem to ignore the fact that Heat is the official orchestration module for this platform. In fact, Ansible Playbook provides almost the same features as the HOT template (HOT is YAML-based syntax for Heat, the reincarnation of AWS CloudFormation ). Nevertheless, many DevOps professionals prefer not to waste time learning the new syntax, and they are already consolidating the whole process for their hybrid infrastructure.
Ansible team understands this, therefore uses Shade, the official library from the OpenStack project, for creating interfaces for calling the OpenStack API. At the time of this writing, Ansible 2.2 included modules for calling the following APIs.
From Ansible's point of view, it is necessary to organize interaction with the server, where the system will be able to download OpenStack credentials and create HTTP connections with various OpenStack APIs. If this server is your machine (localhost), then Ansible will work locally, load the Keystone credentials and initiate interaction with OpenStack.
Let's look at an example. We will use Ansible OpenStack modules to connect to Nova and launch a small instance with a Cirros image. To get started, we will download the latest Cirros image if you haven’t done this before. We will use the existing SSH key of the current user. You can download this playbook from this link on Github.
After starting, we see the IP address of the instance. We write it down. Now you can use Ansible to connect to this instance via SSH. It is assumed that the default Nova network supports connections from our workstation (in our case, through the network of the service provider).
Using Ansible instead of Heat has its advantages and disadvantages. For example, when working with Ansible, you must track the resources you create and manually delete them (in reverse order) when they are no longer needed. Particularly difficult you will have with Neutron ports, floating IPs and routers. But if it is Heat, then you simply delete the stack, and all created resources will be deleted automatically.
Compare the above example with a similar (but not similar) Heat Template, which can be downloaded from the following Github gist repository.
Now let's see what happens if we create many instances but forget to write down their IP addresses. A great example of using the Dynamic Inventory tool for OpenStack is to analyze the current state of our rented virtualized resources and get all the IP addresses of the servers so that we can, for example, check the version of their kernel. For example, this is transparently done using the Ansible Tower solution, which will periodically conduct an inventory and generate an updated list of OpenStack servers to be managed.
Before performing these operations, make sure that you do not have obsolete cloud.yaml files in the ~ / .config / openstack, / etc / openstack or / etc / ansible directory. The Dynamic Inventory script will first search for environment variables (OS_ *), and then the listed files.
For interest, you can view all the information that the above inventory script returns, for this, do the following.
$ ./openstack.py –list
Despite the fact that Heat is very useful, some may prefer to study Ansible to use this solution for orchestration, since it offers the use of a single language to define and automate the entire set of IT resources. I hope this article was useful from a practical point of view. We covered the basic uses of Ansible to run OpenStack resources. If you are interested and want to evaluate the capabilities of Ansible and Ansible Tower, visit the resource . A good starting point would be to implement Heat interacting with Ansible Tower through callbacks, as described in another blog post.
In addition, if you want to learn more about the Red Hat OpenStack platform, then on our site you will find many valuable resources (including videos andofficial documents ).
In this blog, we will discuss numerous uses for Ansible, the most popular automation software (software), together with OpenStack, the most popular cloud infrastructure software. We will help you understand how and why you should use Ansible to make your life easier with Full-Stack Automation, as we like to call it.

To begin with, we will discuss the levels of integrated automation shown in the diagram above. Below we have equipment (servers, storage systems and network equipment). Next is the operating system (Linux or Windows). On Linux, you can install OpenStack to abstract from the physical resources of the data center and deploy the software version of computing resources, networks, and storage. On top of OpenStack, tenant-specific services are deployed to create the virtual machines on which the applications will run. Finally, you must provide operating system management (Linux or Windows) to deploy the applications and workloads that you really need (databases, web servers, mobile application servers, etc.). If you use containers (e.g. Docker or Rkt), You will pack these applications into images that will then be deployed over the guest OS. In addition, the concept of application servers has appeared in some languages, which adds another layer (for example, J2EE).
Management capabilities provided by Ansible solutions
Ansible provides modules for managing each layer. Even for network equipment, more precisely, if you approach this from a technical point of view, for a network operating system such as IOS or NXOS (see the full list of Ansible network modules ).
1. Standard interaction with the operating system: installing packages, changing or enforcing content or file permissions, managing services, creating and deleting users and user groups, etc.
- Linux and BSD via SSH (the first and most popular use case).
- Windows through PowerShell (since version 1.7).
2. Software for implementing the Infrastructure as a Service (IaaS) concept: Install IaaS software and related components (databases, load balancers, configuration files, services, and other supporting tools).
- OpenStack-ansible installer used in some OpenStack builds from other vendors. Remember that the Red Hat OpenStack platform does not use Ansible, but Heat and Puppet. In future releases, Ansible will be used to perform certain checks and assist operators in the process of installing updates and new versions.
- CloudStack Installer is also an Ansible based project.
3. Virtual resources: configure resources, such as a virtual machine or instance, by determining the size, access rights, content, security profile, network connection settings, etc.
- OpenStack Ansible modules (starting with Ansible 2.0), such as Nova or Neutron . They are based on the OpenStack Shade library, which is used by all CLI tools in OpenStack.
- These modules can also manage not so virtual network resources via netconf (since version 2.2).
- Modules Ansible the vSphere the VMware .
- RHV, or oVirt, or Libvirt for KVM only.
- There are also modules for cloud service providers such as Amazon , Google Cloud , Azure, and Digital Ocean .
4. Guest OS: the components are similar to those of the host OS. But how do you know how many guest systems you have?
- The Ansible Dynamic Inventory tool will dynamically query the IaaS and VM level to detect currently available instances. At the same time, the host name, IP addresses and security settings are determined, that is, asset management becomes dynamic. This feature will be especially useful for those who use Auto Scaling Groups in their cloud infrastructure, as the list of instances changes dramatically over time.
5. Container management module (optional).
- Docker : note that the old Docker module in Ansible 2.1 will be replaced with a new native component.
- Kubernetes.
- Atomic Host.
6. Leased software: databases, web servers, load balancers, data processing modules, etc.
- Ansible Galaxy is a recipe repository (playbook) for deploying the most popular software, and this is the result of the collaboration of thousands of community members.
- You can also manage your web infrastructure like JBoss , allowing Ansible to determine how the application will be deployed to the application server.
Best practices for installing the latest version of Ansible in a Python virtual environment
As you already understood, some functions are available only in the latest versions of Ansible, for example 2.2. However, your OS version may have an older version. For example, in RHEL 7 or CentOS 7 you will find only Ansible 1.9.
Given that Ansible is a command-line tool written in Python that does not prohibit multiple versions of the system, you may not need the security enhancement in Ansible that your assembly offers, and you might want to try out the latest version.
However, as with any other Python software, there are many dependencies, so it is not recommended to use unverified new libraries with the system ones. Libraries can be shared by other components of your system, and unverified newer versions can disrupt other applications. The easiest way is to install the latest version of Ansible with all the dependencies in an isolated folder under your unprivileged account. This will be the Python Virtual Environment (virtualenv), and if you do everything right, you can safely try out the latest Ansible modules for complex orchestration. Not recommended , of course.apply this practice in a production environment. This is nothing more than an exercise to help you improve your DevOps skills.
1. Install the required components (pip, virtualenv)
In this case, we need only one "system-wide" Python library - virtualenvwrapper. In addition, you should not run the sudo pip install command, as this will replace the Python system libraries with newer unverified versions. In this case, we can only trust the virtualenvwrapper library. A virtual environment is an efficient mechanism for installing and testing new Python modules in your unprivileged user account .
$ sudo yum install python-pip
$ sudo pip install virtualenvwrapper
$ sudo yum install python-heatclient python-openstackclient python2-shade
In addition, if your account is other than sudoer, you can use the following commands.
wget https://bootstrap.pypa.io/get-pip.py
python get-pip.py --user
.local/bin/pip install virtualenvwrapper --user
export PATH=$PATH:~/.local/bin #Remember to include this in your .bashrc2. Install a new virtual environment where we will deploy the latest version of Ansible.
First, create a directory for storing virtual environments.
$ mkdir $HOME/.virtualenvsThen add the following lines to your .bashrc file:
export WORKON_HOME = $ HOME / .virtualenvs
source /usr/bin/virtualenvwrapper.sh
Now run the source command for this file.
$ source ~/.bashrcAt this point, shell links are created, but only at the first start. Run the workon command to view a list of environments; it should not be empty. Next, we will create a new virtualenv environment called ansible2 , it will be activated automatically and gain access to packages installed by default using RPM.
$ mkvirtualenv ansible2 --system-site-packagesType deactivate to exit virtualenv , and workon to re-enter.
$ deactivate
$ workon ansible23. Enter the new virtualenv environment and install Ansible2 via PIP (as a regular user, without root rights).
You will see that the request to enter a command in the shell has changed and the name virtualenv is indicated in brackets.
(ansible2) $ pip install ansible This command will only install dependencies for Ansible 2 using your system-wide Python packages available in RPM (thanks to the system-site-packages flag that we used earlier). An alternative if you want to try out the development branch.
(ansible2) $ pip install git+git://github.com/ansible/ansible.git@devel(ansible2) $ ansible --versionIf you need to remove the virtualenv environment and all its dependencies, simply enter the rmvirtualenv ansible2 command.
NOTE. If the above commands did not work, make sure that the GCC and OpenSSL libraries are installed on your systems, as some Python dependencies use the latest cryptographic modules.
4. Install OpenStack Client Dependencies
The first command in the code snippet below ensures that you have the latest stable version of the OpenStack API, however you can also use the pip install command to get the latest command-line tool (CLI). The second command provides the latest version of the Python Shade library for connecting to the latest versions of the OpenStack API using ansible, regardless of the specific CLI tool.
(ansible2) $ yum install python-openstackclient python-heatclient(ansible2) $ pip install shade --upgrade5. Test your deployment
(ansible2) $ ansible -m ping localhost
localhost | SUCCESS => {
"changed": false,
"ping": "pong"
}NOTE. You cannot run this version of ansible outside the virtual environment of virtualenv, so always run the workon ansible2 command before usi.
OpenStack Orchestration Using Ansible
Attentive readers will notice that using Ansible to orchestrate OpenStack, we seem to ignore the fact that Heat is the official orchestration module for this platform. In fact, Ansible Playbook provides almost the same features as the HOT template (HOT is YAML-based syntax for Heat, the reincarnation of AWS CloudFormation ). Nevertheless, many DevOps professionals prefer not to waste time learning the new syntax, and they are already consolidating the whole process for their hybrid infrastructure.
Ansible team understands this, therefore uses Shade, the official library from the OpenStack project, for creating interfaces for calling the OpenStack API. At the time of this writing, Ansible 2.2 included modules for calling the following APIs.
- Keystone: users, groups, roles, projects.
- Nova: servers, key pairs, groups, and security flags.
- Neutron: ports, network, subnets, routers, floating IP addresses.
- Ironic: nodes, introspective.
- Swift objects.
- Tom Cinder.
- Images of Glance.
From Ansible's point of view, it is necessary to organize interaction with the server, where the system will be able to download OpenStack credentials and create HTTP connections with various OpenStack APIs. If this server is your machine (localhost), then Ansible will work locally, load the Keystone credentials and initiate interaction with OpenStack.
Let's look at an example. We will use Ansible OpenStack modules to connect to Nova and launch a small instance with a Cirros image. To get started, we will download the latest Cirros image if you haven’t done this before. We will use the existing SSH key of the current user. You can download this playbook from this link on Github.
---
# Setup according to Blogpost "Full Stack automation with Ansible and OpenStack". Execute with "ansible-playbook ansible-openstack-blogpost.yml -c local -vv"
# #
# #
# #
- name: Execute the Blogpost demo tasks
hosts: localhost
tasks:
- name: Download cirros image
get_url:
url: http://download.cirros-cloud.net/0.3.4/cirros-0.3.4-x86_64-disk.img
dest: /tmp/cirros-0.3.4-x86_64-disk.img
- name: Upload cirros image to openstack
os_image:
name: cirros
container_format: bare
disk_format: qcow2
state: present
filename: /tmp/cirros-0.3.4-x86_64-disk.img
- name: Create new keypair from current user's default SSH key
os_keypair:
state: present
name: ansible_key
public_key_file: "{{ '~' | expanduser }}/.ssh/id_rsa.pub"
- name: Create the test network
os_network:
state: present
name: testnet
external: False
shared: False
#provider_network_type: vlan
#provider_physical_network: datacentre
register: testnet_network
- name: Create the test subnet
os_subnet:
state: present
network_name: "{{ testnet_network.id }}"
name: testnet_sub
ip_version: 4
cidr: 192.168.0.0/24
gateway_ip: 192.168.0.1
enable_dhcp: yes
dns_nameservers:
- 8.8.8.8
register: testnet_sub
- name: Create the test router
ignore_errors: yes #for some reasons, re-running this task gives errors
os_router:
state: present
name: testnet_router
network: nova
external_fixed_ips:
- subnet: nova
interfaces:
- testnet_sub
- name: Create a new security group
os_security_group:
state: present
name: secgr
- name: Create a new security group allowing any ICMP
os_security_group_rule:
security_group: secgr
protocol: icmp
remote_ip_prefix: 0.0.0.0/0
- name: Create a new security group allowing any SSH connection
os_security_group_rule:
security_group: secgr
protocol: tcp
port_range_min: 22
port_range_max: 22
remote_ip_prefix: 0.0.0.0/0
- name: Create server instance
os_server:
state: present
name: testServer
image: cirros
flavor: m1.small
security_groups: secgr
key_name: ansible_key
nics:
- net-id: "{{ testnet_network.id }}"
register: testServer
- name: Show Server's IP
debug: var=testServer.openstack.public_v4
After starting, we see the IP address of the instance. We write it down. Now you can use Ansible to connect to this instance via SSH. It is assumed that the default Nova network supports connections from our workstation (in our case, through the network of the service provider).
Comparison with OpenStack Heat
Using Ansible instead of Heat has its advantages and disadvantages. For example, when working with Ansible, you must track the resources you create and manually delete them (in reverse order) when they are no longer needed. Particularly difficult you will have with Neutron ports, floating IPs and routers. But if it is Heat, then you simply delete the stack, and all created resources will be deleted automatically.
Compare the above example with a similar (but not similar) Heat Template, which can be downloaded from the following Github gist repository.
heat_template_version: 2015-04-30
description: >
Node template. Launch with "openstack stack create --parameter public_network=nova --parameter ctrl_network=default --parameter secgroups=default --parameter image=cirros --parameter key=ansible_key --parameter flavor=m1.small --parameter name=myserver -t openstack-blogpost-heat.yaml testStack"
parameters:
name:
type: string
description: Name of node
key:
type: string
description: Name of keypair to assign to server
secgroups:
type: comma_delimited_list
description: List of security group to assign to server
image:
type: string
description: Name of image to use for servers
flavor:
type: string
description: Flavor to use for server
availability_zone:
type: string
description: Availability zone for server
default: nova
ctrl_network:
type: string
label: Private network name or ID
description: Network to attach instance to.
public_network:
type: string
label: Public network name or ID
description: Network to attach instance to.
resources:
ctrl_port:
type: OS::Neutron::Port
properties:
network: { get_param: ctrl_network }
security_groups: { get_param: secgroups }
floating_ip:
type: OS::Neutron::FloatingIP
properties:
floating_network: { get_param: public_network }
port_id: { get_resource: ctrl_port }
instance:
type: OS::Nova::Server
properties:
name: { get_param: name }
image: { get_param: image }
flavor: { get_param: flavor }
availability_zone: { get_param: availability_zone }
key_name: { get_param: key }
networks:
- port: { get_resource: ctrl_port }Using Dynamic Inventory in Combination with OpenStack Modules
Now let's see what happens if we create many instances but forget to write down their IP addresses. A great example of using the Dynamic Inventory tool for OpenStack is to analyze the current state of our rented virtualized resources and get all the IP addresses of the servers so that we can, for example, check the version of their kernel. For example, this is transparently done using the Ansible Tower solution, which will periodically conduct an inventory and generate an updated list of OpenStack servers to be managed.
Before performing these operations, make sure that you do not have obsolete cloud.yaml files in the ~ / .config / openstack, / etc / openstack or / etc / ansible directory. The Dynamic Inventory script will first search for environment variables (OS_ *), and then the listed files.
#ensure you are using latest ansible version
$ workon ansible2
$ wget https://raw.githubusercontent.com/ansible/ansible/devel/contrib/inventory/openstack.py$ chmod +x openstack.py$ ansible -i openstack.py all -m pingbdef428a-10fe-4af7-ae70-c78a0aba7a42 | SUCCESS => {
"changed": false,
"ping": "pong"
}
343c6e76-b3f6-4e78-ae59-a7cf31f8cc44 | SUCCESS => {
"changed": false,
"ping": "pong"
}For interest, you can view all the information that the above inventory script returns, for this, do the following.
$ ./openstack.py –list
{
"": [
"777a3e02-a7e1-4bec-86b7-47ae7679d214",
"bdef428a-10fe-4af7-ae70-c78a0aba7a42",
"0a0c2f0e-4ac6-422d-8d9b-12b7a87daa72",
"9d4ee5c0-b53d-4cdb-be0f-c77fece0a8b9",
"343c6e76-b3f6-4e78-ae59-a7cf31f8cc44"
],
"_meta": {
"hostvars": {
"0a0c2f0e-4ac6-422d-8d9b-12b7a87daa72": {
"ansible_ssh_host": "172.31.1.42",
"openstack": {
"HUMAN_ID": true,
"NAME_ATTR": "name",
"OS-DCF:diskConfig": "MANUAL",
"OS-EXT-AZ:availability_zone": "nova",
"OS-EXT-SRV-ATTR:host": "compute-0.localdomain",
"OS-EXT-SRV-ATTR:hypervisor_hostname": "compute-0.localdomain",
"OS-EXT-SRV-ATTR:instance_name": "instance-000003e7",
"OS-EXT-STS:power_state": 1,
"OS-EXT-STS:task_state": null,
"OS-EXT-STS:vm_state": "active",
"OS-SRV-USG:launched_at": "2016-10-10T21:13:24.000000",
"OS-SRV-USG:terminated_at": null,
"accessIPv4": "172.31.1.42",
"accessIPv6": "",
(....)Conclusion
Despite the fact that Heat is very useful, some may prefer to study Ansible to use this solution for orchestration, since it offers the use of a single language to define and automate the entire set of IT resources. I hope this article was useful from a practical point of view. We covered the basic uses of Ansible to run OpenStack resources. If you are interested and want to evaluate the capabilities of Ansible and Ansible Tower, visit the resource . A good starting point would be to implement Heat interacting with Ansible Tower through callbacks, as described in another blog post.
In addition, if you want to learn more about the Red Hat OpenStack platform, then on our site you will find many valuable resources (including videos andofficial documents ).
