Dynamic testing of Android applications
Dynamic testing is conducted to identify vulnerabilities during the operation of the application. In this article I want to share several ways to test the application for Android. Also show how to configure and configure hardware. Who cares, welcome under cat.
Dynamic testing implies analysis of application logs, analysis of application traffic, search for bugs during operation, etc. To test, you need to set up a virtual machine for Genimotion, as it is described here .
What tools are used for dynamic analysis:
- BurpSuite;
- Inspakage;
- Pidcat or another application with permissions to read logs.
How to test using BurpSuite
First you need to configure the proxy and import the certificate. BurpSuite shows application vulnerabilities to SSL pinning and can find vulnerabilities that exist on the server with which the application contacts.
1. Installing a proxy
First you need to see the interface information for correct proxy settings.

Fig. 1. Information about the interfaces.
Configure proxy on BurpSuite.
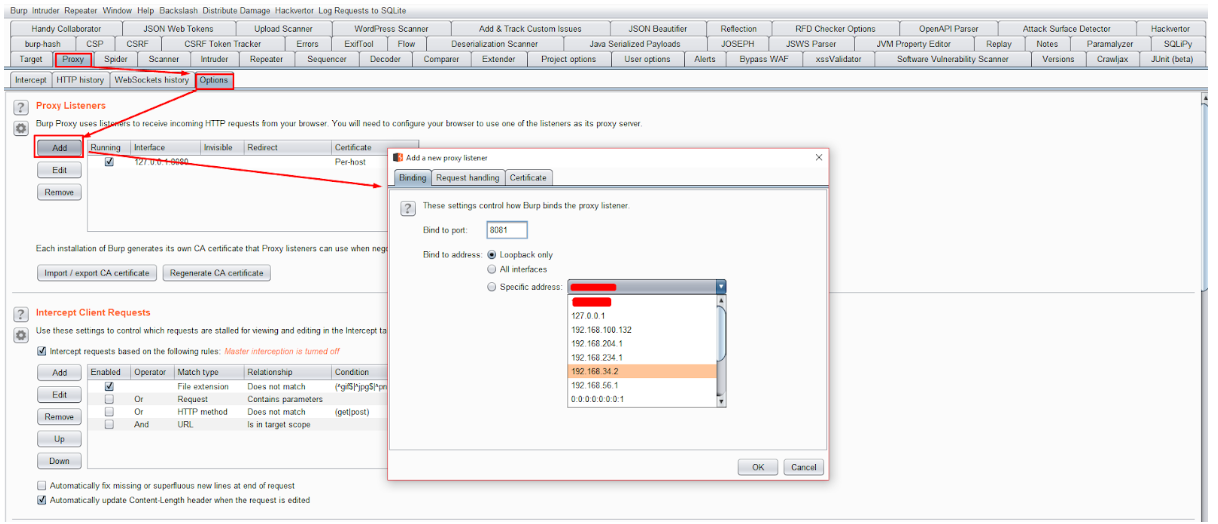
Fig. 2. Set up a proxy on BurpSuite.
We install the proxy on the device on which we will conduct testing.
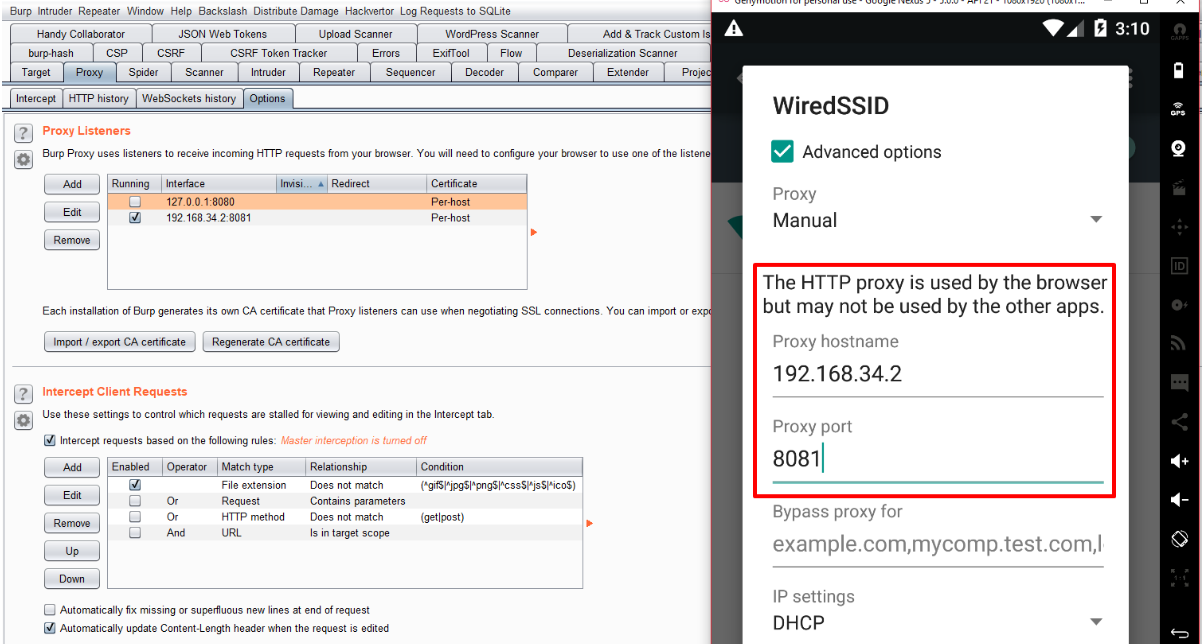
Fig. 3. Setting up a proxy on the device.
Enter in the browser http [:] // burp / - this is needed to download the certificate. And download the certificate for work. Next, you need to open the “Downloads” folder, there is a downloaded certificate. With a long click on the certificate, a menu appears in which we select “Rename” and change the extension to .cer and import the certificate.

Fig. 4. Download certificate /
2. Import certificate
Go to the device settings, find the item “Security”, then select “Install from SD”. From the “Downloads” folder, select the certificate that was downloaded and renamed. After you need to give the certificate a name.
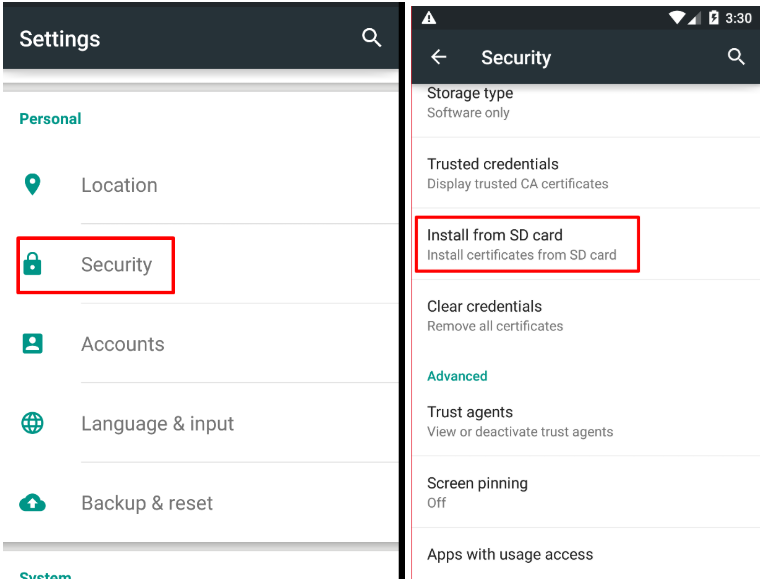
Fig. 5. Import certificate.
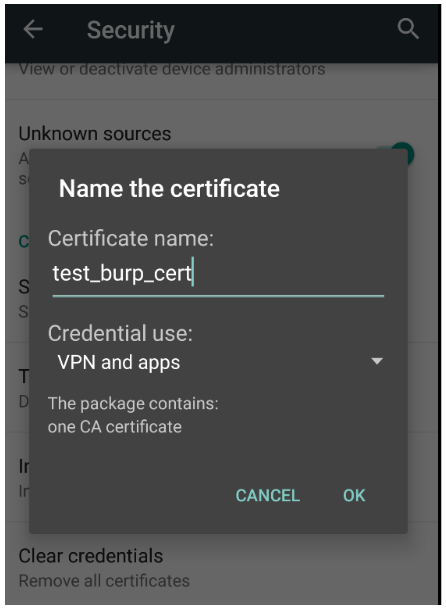
Fig. 6. Import certificate.
3. Verifying the certificate installation and viewing traffic through BurpSuite.
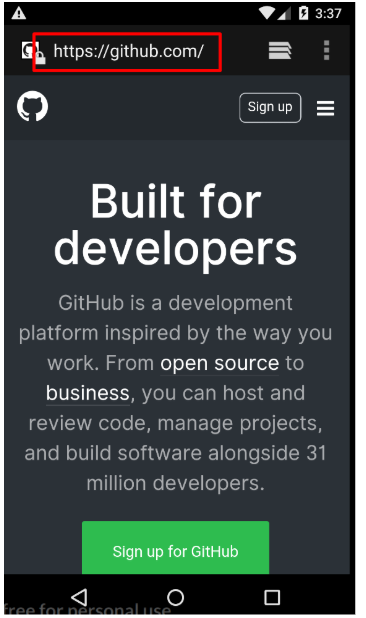
Fig. 7. Testing the correctness of import certificate.
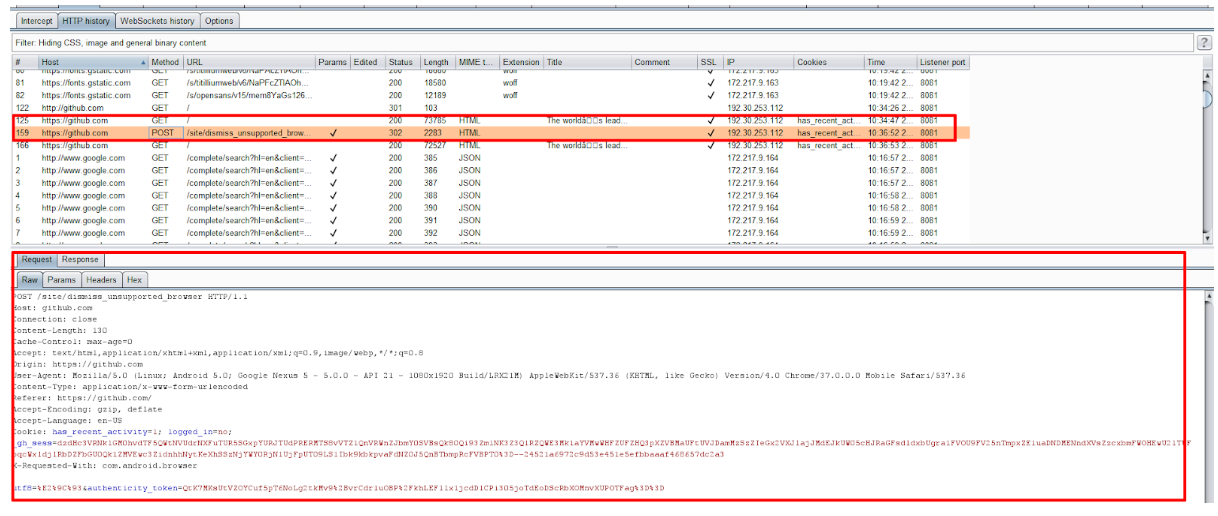
Fig. 8. We look at the requests that go with the device.
Now you can test interaction with the API.
Starting with Android 7, this way of adding a Burp certificate to trusted ones will not work for most applications - by default, user certificates are no longer trusted. So you have to root, give the certificate the correct name and put it in the system directory. (Comment y4ppieflu)
How to test for Inspakage
Inspekage is a tool that allows you to perform dynamic testing of Android applications and helps you understand what the application performs at runtime. Inspekage shows the application running with:
- files
- databases
- cryptography
- http requests
- lines
- logs, etc.
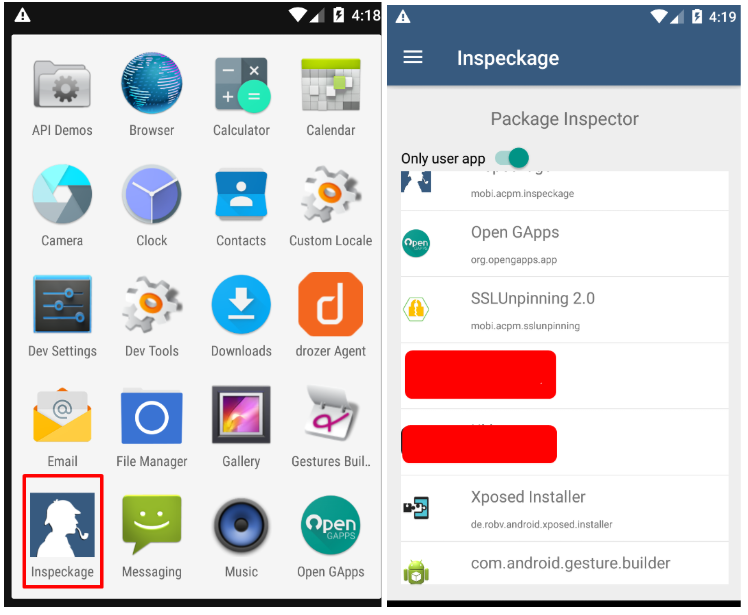
Fig. 9. Run the application for testing.
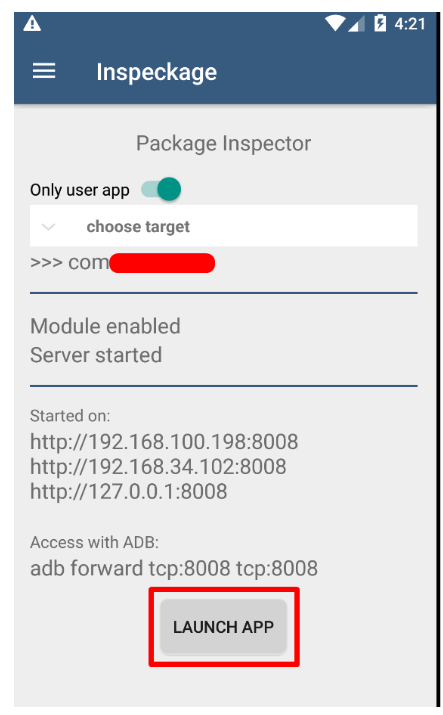
Fig. 10. Run the application for testing.
After launching the application, enter https [:] // 192 [.] 168 [.] 100 [.] 198 [:] 8008 to the application console in the browser (Fig. 11).
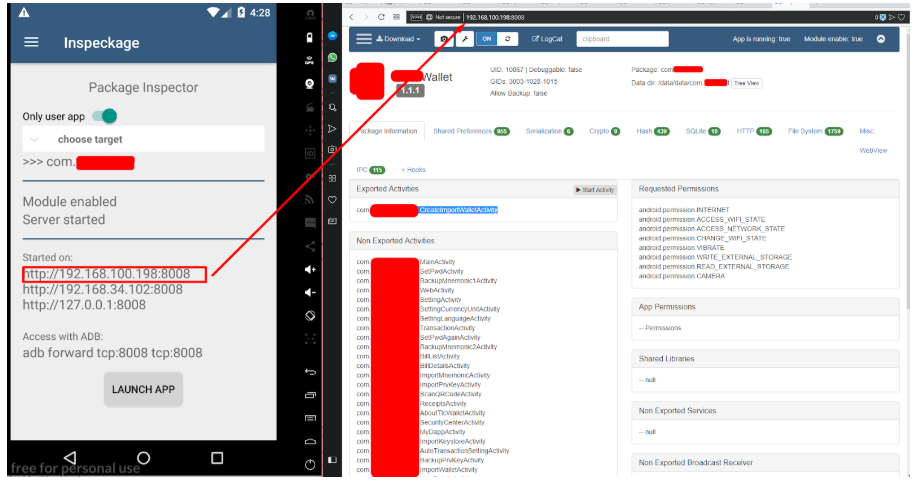
Fig. 11. Launch console in browser.
Next we go through the tabs in the console:
- Shared Preferences - pic. 12 - demonstrates the interaction of the application with local resources.
- Serialization - rice. 13
- Crypto - rice. 14 - demonstrates work with cryptography (SSL / TLS is not included here)
- Hash - rice 14
- SQLite - fig. 15
- HTTP - fig. 16 - in BurpSuite this tab is better disclosed
- FileSystems - Fig. 17 - application work with files
- IPC - fig. 18, etc.
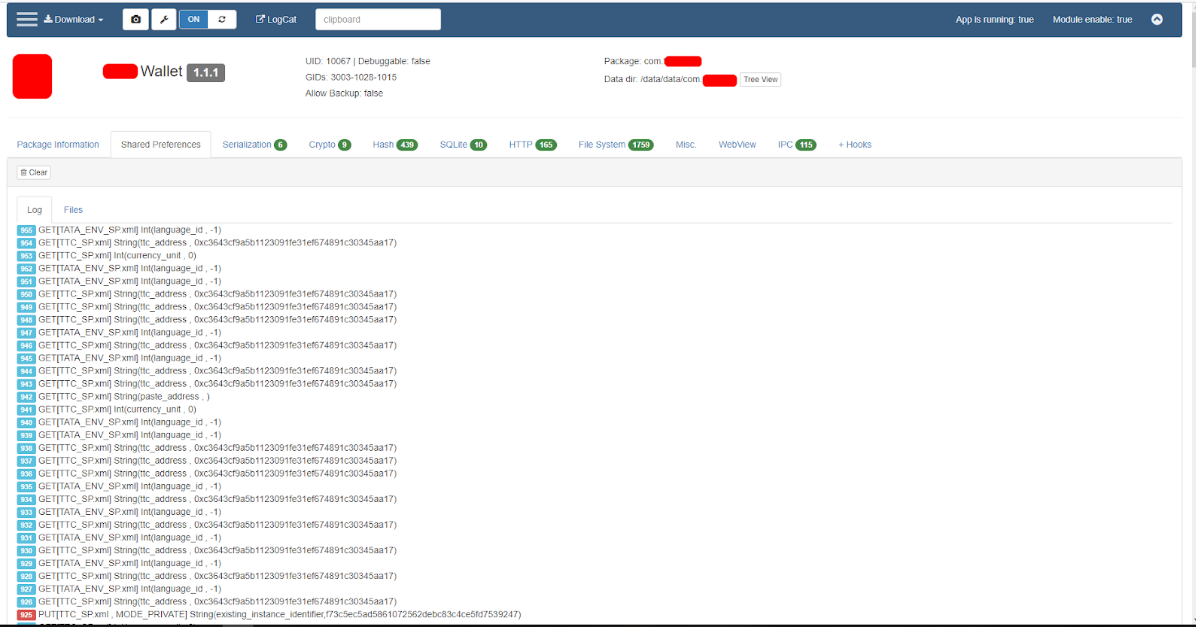
Fig. 12. Shared Preferences.
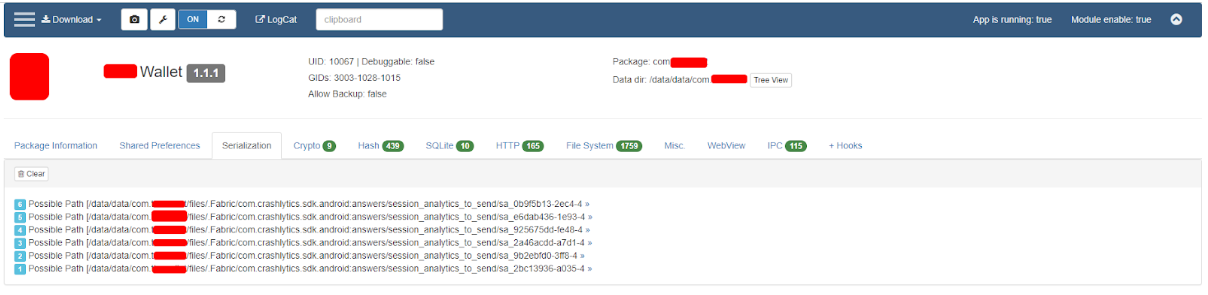
Fig. 13. Serialization.
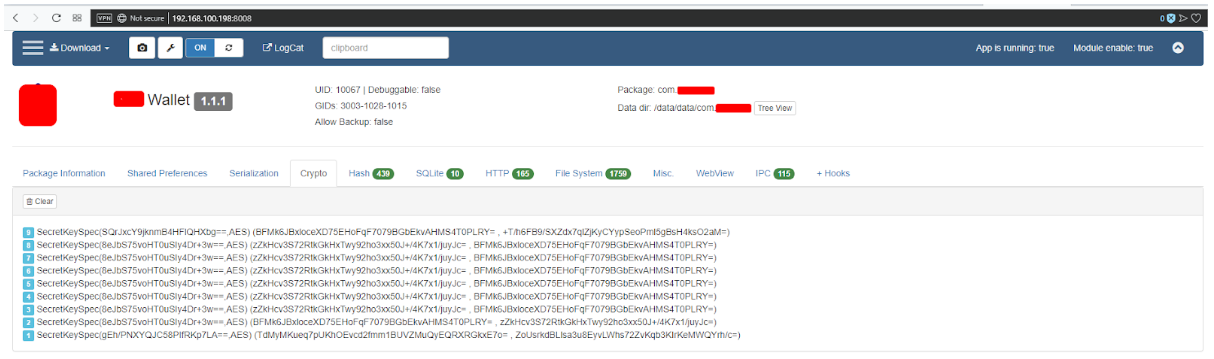
Fig. 14. Crypto.
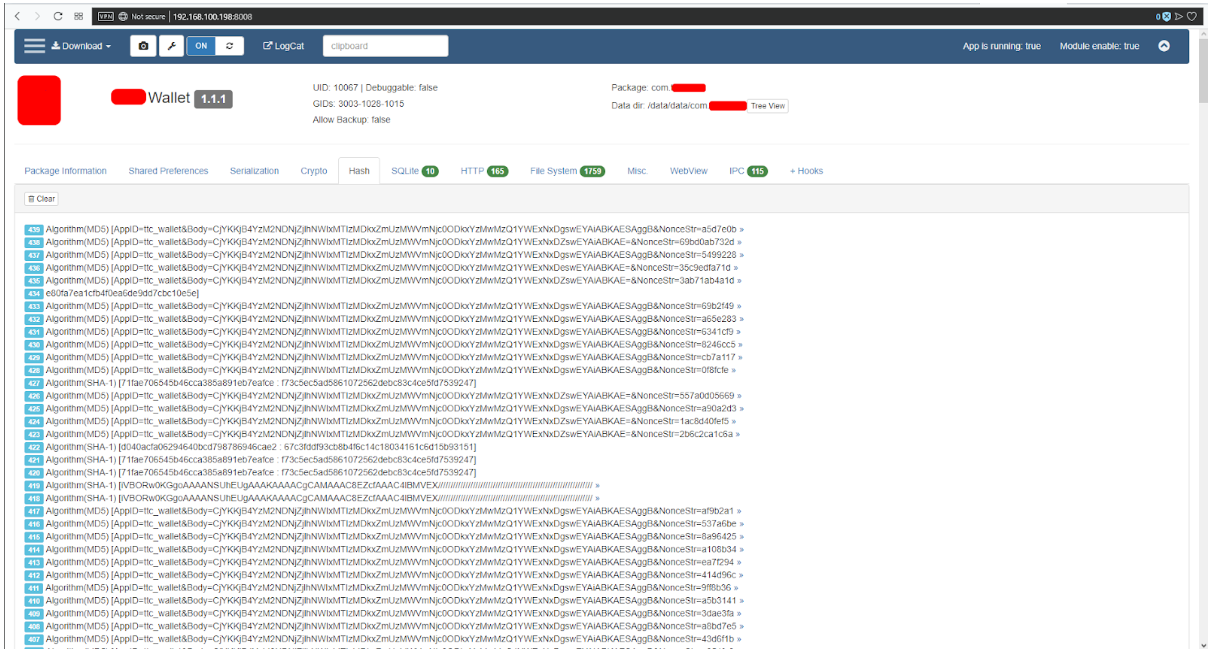
Fig. 15. Hash.
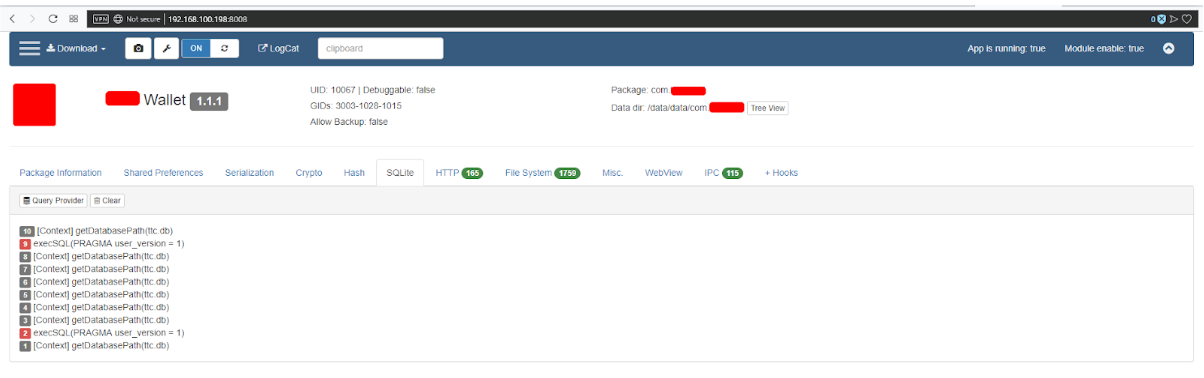
Fig. 16. SQLite.
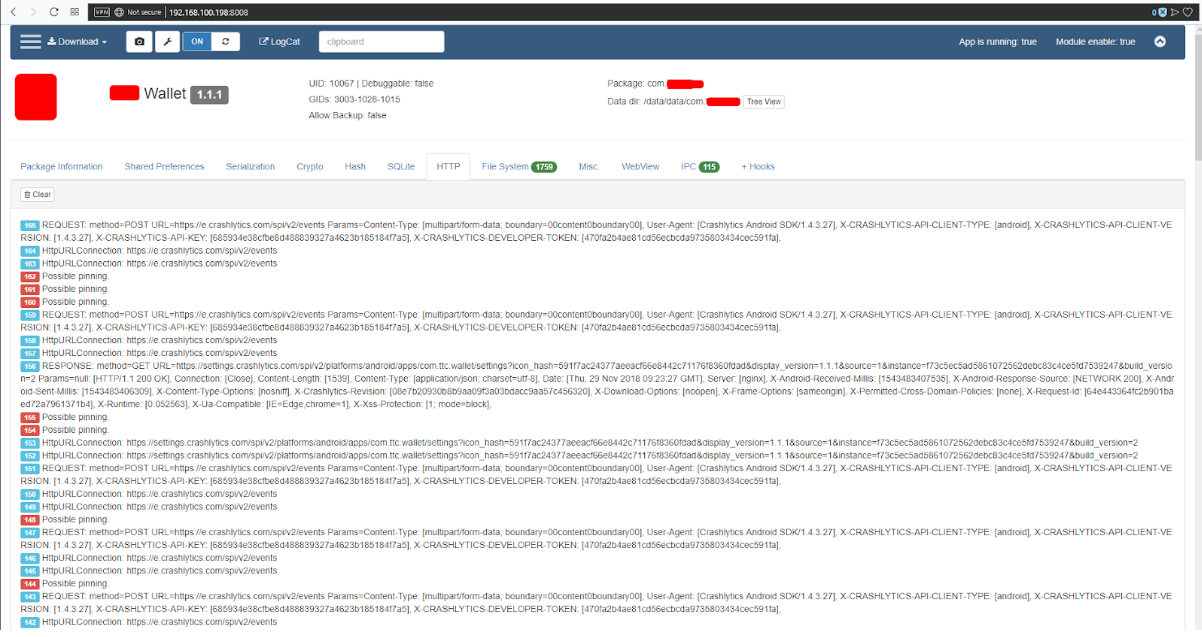
Fig. 17. HTTP.
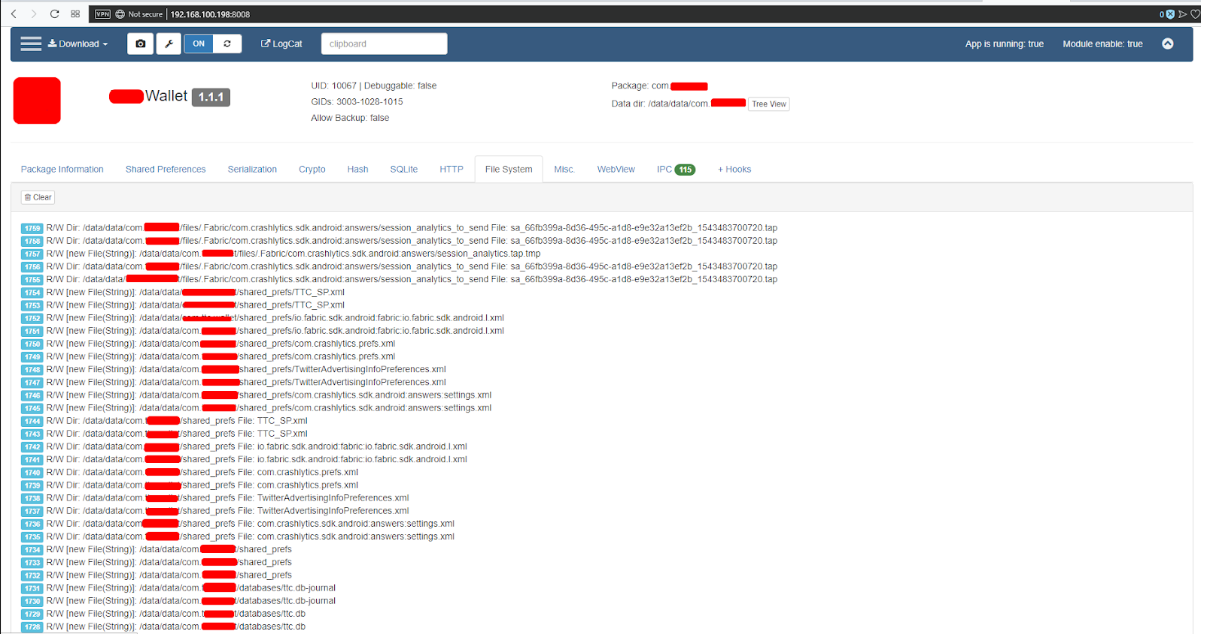
Fig. 18. File system.
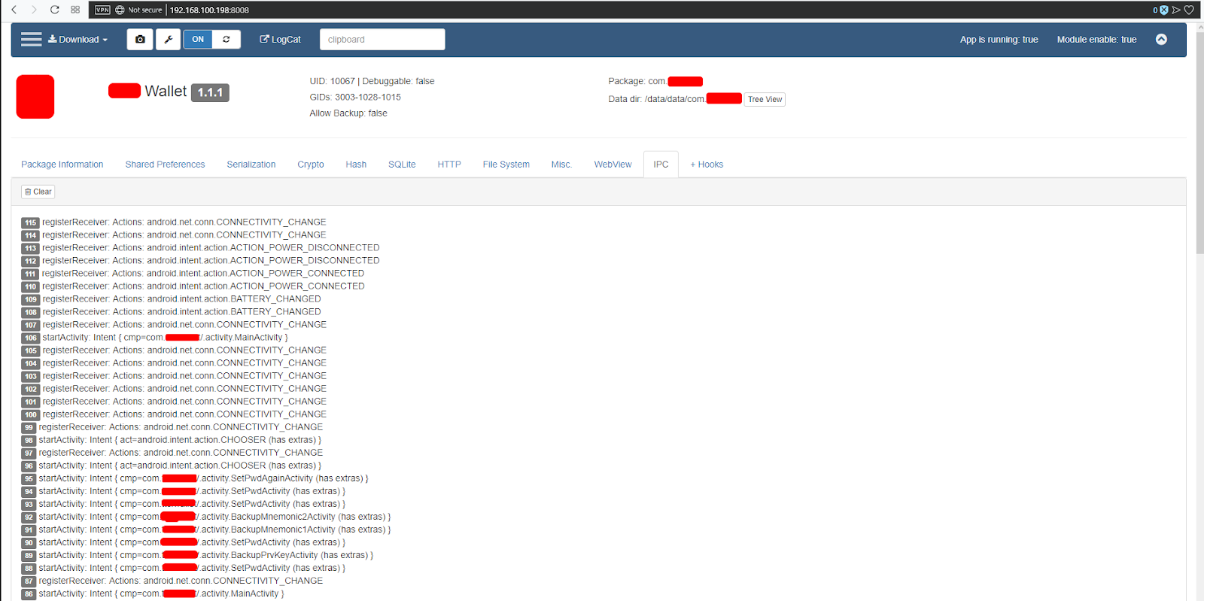
Fig. 19. IPC.
Testing with Pidcat
Pidcat is an application that reads the logs of the application. When testing, you need to perform the functions of the application and watch what data fall into the logs of work. Basically, service information is displayed there, it happens that you can get some critical information, such as a backup copy of the private key. If the device is malvar, then this information may fall into the hands of an attacker.
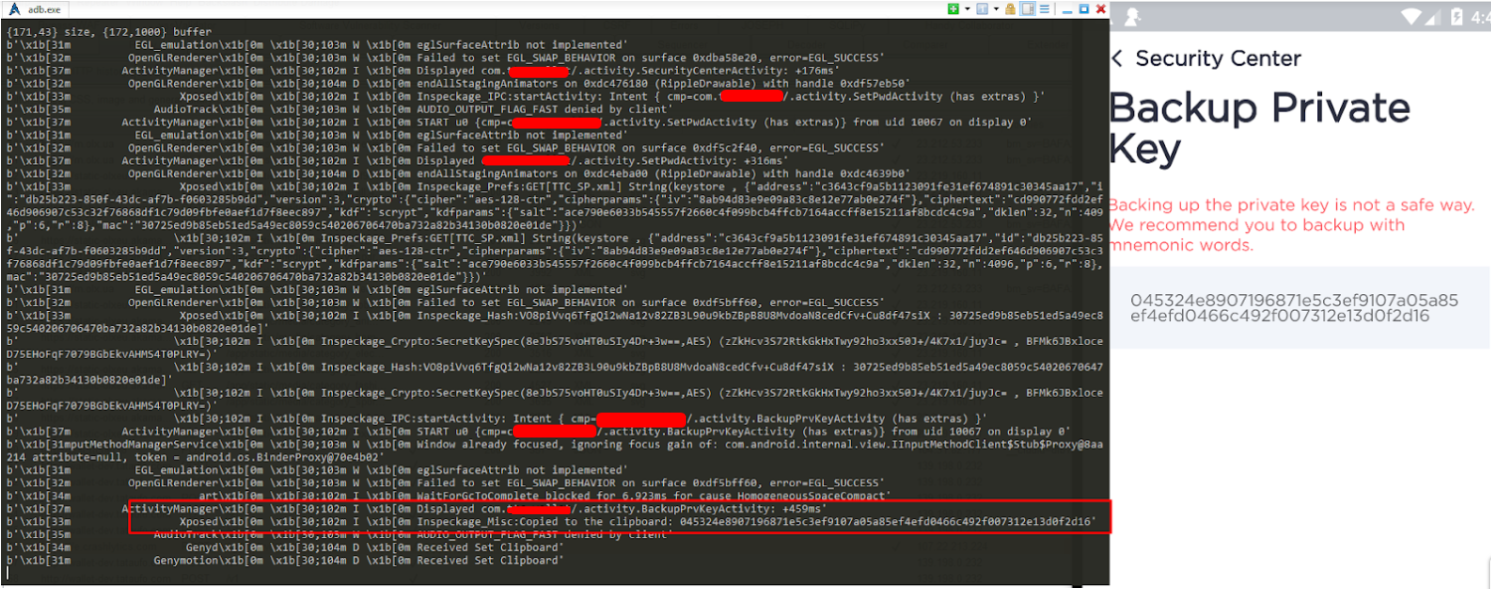
Fig. 20. Backup private key.

Fig. 21. Confidential information.
Conclusion
In practice, the methods of basic dynamic testing of applications for Android, which we use in Hacken , are shown . There is also a module for automated testing in the MobSF framework, but this requires a separate article.
