Security Watch: IBM QRadar SIEM
Modern cybercriminals use increasingly sophisticated methods to attack company defense systems. To counteract them, information security departments are forced to analyze and interpret a huge number of events per day. IBM offers network security threats from IBM QRadar Security Intelligence Platform, which provides a unified architecture for integrating security information and event management (SIEM) and logs, detecting abnormal situations, analyzing incidents, responding to them, managing settings and fixing vulnerabilities .
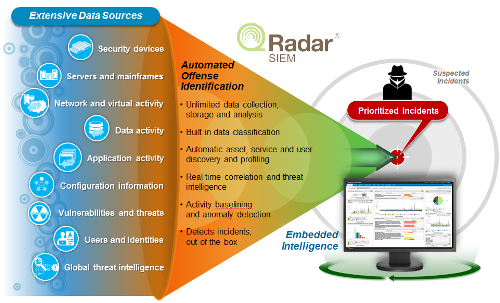
The unified architecture of the QRadar Security Intelligence Platform allows you to analyze logs, network flows, packets, vulnerabilities, as well as data about users and resources. Using Sense Analytics allows you to conduct correlation analysis to identify the most serious threats, attacks and vulnerabilities in real time. This enables IT departments to prioritize and highlight the most important incidents from the huge data stream. The solution automatically responds to incidents and fulfills regulatory requirements due to the ability to collect data, determine their correlation and reporting. It also provides predictive analysis of existing risks caused by improper device settings and known vulnerabilities.
The IBM QRadar Security Intelligence Platform includes a number of different modules. One of the key components of the solution is the IBM QRadar SIEM tool - a system for collecting and analyzing events. It consolidates information from event logs coming from devices, endpoints, and applications on the network. QRadar SIEM normalizes and analyzes correlation to identify security risks, and also uses the advanced Sense Analytics engine to detect normal behavior, detect anomalies, reveal advanced threats and remove false positives. This software module makes it possible to collect all related events in one incident. QRadar SIEM may include IBM X-Force Threat Intelligence threat analysis tools with a list of potentially malicious IP addresses, addresses of computers with malware, sources of spam and other threats, allowing you to implement a proactive approach to security. In addition, to prioritize the product, it can map threats to systems with events and data from the network.
The ability to create detailed reports on access to data and user actions provides more effective threat management and compliance with standards. It is also worth mentioning that QRadar SIEM can be used in on-premises and cloud environments.
In addition, it is worth noting that in the near future, IBM plans to use the Watson artificial intelligence platform in the field of security, integrating it with QRadar software and the X-Force database. This will increase the level of analytics to determine the nature of threats, as well as compensate for the lack of IT personnel in the field of information security.
Consider the above features of the IBM QRadar SIEM in more detail. Providing real-time transparency allows you to detect misuse of applications, internal fraud, and small threats that could be overlooked among millions of daily events. The solution allows collecting logs and events from various sources, including security devices, operating systems, applications, databases, and access and identification management systems. Network flow data comes from switches and routers, including layer 7 data (application layer). Information is provided from access control and identification systems and infrastructure services such as Dynamic Host Configuration Protocol (DHCP), as well as from vulnerability scanners in the network and applications.
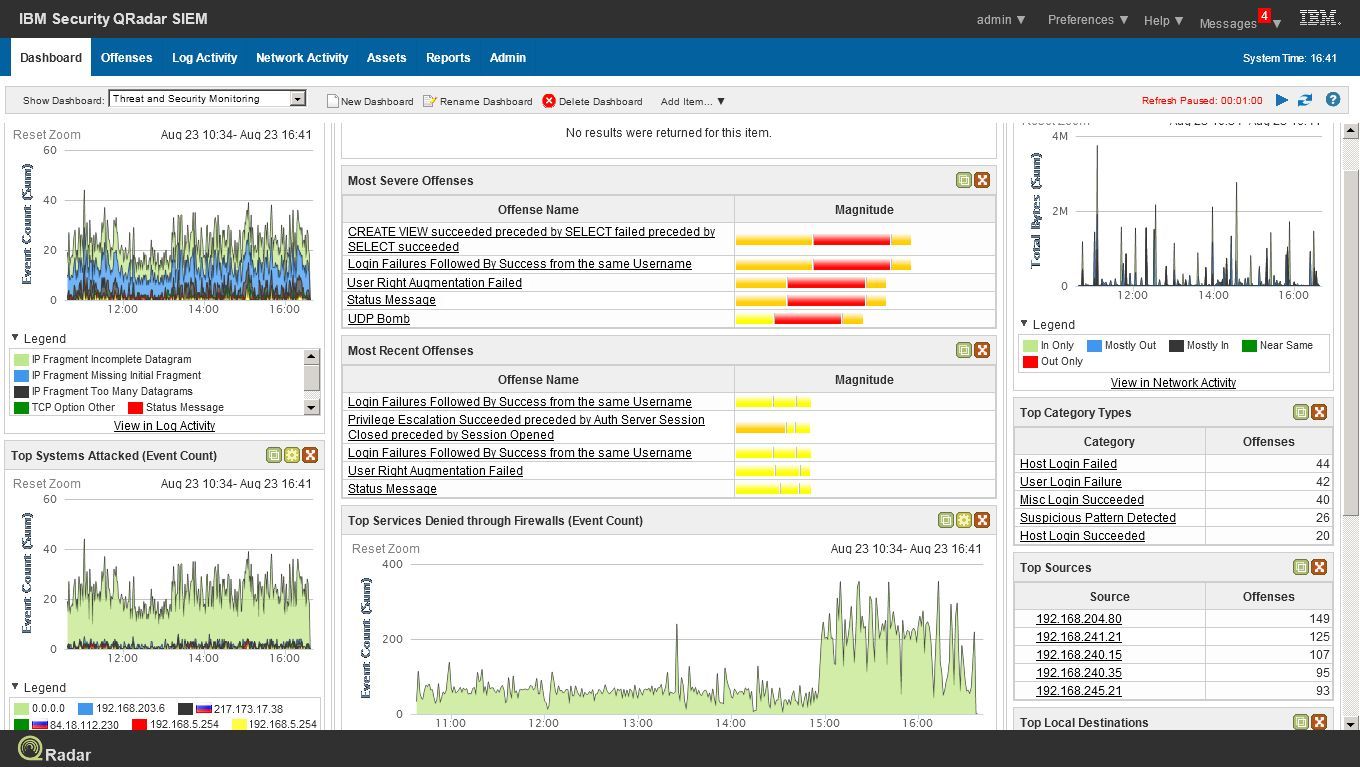
On the IBM QRadar SIEM Dashboard, you can display all the necessary reports and graphs.
QRadar SIEM performs instant event normalization and comparison with other data to detect threats and create regulatory reports. The decision prioritizes events, highlighting a small number of real violations that pose the most serious threat to business. The detected anomalies make it possible to detect changes in behavior associated with applications, computers, users, and network segments. When using the IBM X-Force Threat Intelligence software, actions associated with suspicious IP addresses are also determined.
The solution provides an opportunity to more effectively manage threats by tracking serious incidents and providing links to all the required data for analysis. This allows you to detect actions after hours or unusual use of applications and cloud services, as well as network activity that does not match stored usage patterns. To improve analytics, QRadar SIEM supports the ability to search events and data streams in near real-time mode, as well as stored data. It is possible to perform a combined search in large distributed environments. For a deeper understanding and better display of applications, databases, collaboration products and social networks, you can use the IBM QRadar QFlow and IBM QRadar VFlow Collector devices,
The ability to install in the cloud SoftLayer allows QRadar SIEM to receive real-time security information in the cloud. Moreover, the collection of events and data streams from applications is performed both in the cloud and on local resources.
The solution has an intuitive reporting module that does not require special databases or special skills from IT administrators. Generating reports on data access and user activity with the ability to track information by name and IP address ensures compliance with security policies, as well as compliance with regulatory requirements.
A number of modules are integrated with the QRadar SIEM tool to increase its efficiency. One of the most important is QRadar Risk Manager, which compares vulnerability information with data on network topology and connections. The solution identifies vulnerabilities in the company’s network and the applications running in it, assessing risks and minimizing them. Risk Manager monitors the configuration of switches, routers, firewalls and intrusion prevention systems (IPS), recognizing conditions that pose a security risk. In addition, it allows you to simulate network attacks and other intrusion scenarios, making changes to the network configuration that make it possible to assess the magnitude of the threat.
Another interesting tool is the QRadar Log Manager module. It collects and processes real-time event data from routers, switches, firewalls, VPNs, intrusion detection and prevention systems (IDS / IPS), antivirus programs, and other sources. Log Manager provides an opportunity to simplify the maintenance of necessary reporting and monitoring compliance with regulatory requirements.
IBM QRadar SIEM is one of the most effective analytic security systems. It is also important that the solution supports working with more than 200 products from leading manufacturers and collects, analyzes and correlates data through a wide range of systems, including network solutions, security tools, servers, hosts, operating systems and applications. In addition, an additional advantage of the solution is the low cost of the entry-level system.

The unified architecture of the QRadar Security Intelligence Platform allows you to analyze logs, network flows, packets, vulnerabilities, as well as data about users and resources. Using Sense Analytics allows you to conduct correlation analysis to identify the most serious threats, attacks and vulnerabilities in real time. This enables IT departments to prioritize and highlight the most important incidents from the huge data stream. The solution automatically responds to incidents and fulfills regulatory requirements due to the ability to collect data, determine their correlation and reporting. It also provides predictive analysis of existing risks caused by improper device settings and known vulnerabilities.
Threat analyzer
The IBM QRadar Security Intelligence Platform includes a number of different modules. One of the key components of the solution is the IBM QRadar SIEM tool - a system for collecting and analyzing events. It consolidates information from event logs coming from devices, endpoints, and applications on the network. QRadar SIEM normalizes and analyzes correlation to identify security risks, and also uses the advanced Sense Analytics engine to detect normal behavior, detect anomalies, reveal advanced threats and remove false positives. This software module makes it possible to collect all related events in one incident. QRadar SIEM may include IBM X-Force Threat Intelligence threat analysis tools with a list of potentially malicious IP addresses, addresses of computers with malware, sources of spam and other threats, allowing you to implement a proactive approach to security. In addition, to prioritize the product, it can map threats to systems with events and data from the network.
The ability to create detailed reports on access to data and user actions provides more effective threat management and compliance with standards. It is also worth mentioning that QRadar SIEM can be used in on-premises and cloud environments.
In addition, it is worth noting that in the near future, IBM plans to use the Watson artificial intelligence platform in the field of security, integrating it with QRadar software and the X-Force database. This will increase the level of analytics to determine the nature of threats, as well as compensate for the lack of IT personnel in the field of information security.
Functionality Issues
Consider the above features of the IBM QRadar SIEM in more detail. Providing real-time transparency allows you to detect misuse of applications, internal fraud, and small threats that could be overlooked among millions of daily events. The solution allows collecting logs and events from various sources, including security devices, operating systems, applications, databases, and access and identification management systems. Network flow data comes from switches and routers, including layer 7 data (application layer). Information is provided from access control and identification systems and infrastructure services such as Dynamic Host Configuration Protocol (DHCP), as well as from vulnerability scanners in the network and applications.

On the IBM QRadar SIEM Dashboard, you can display all the necessary reports and graphs.
QRadar SIEM performs instant event normalization and comparison with other data to detect threats and create regulatory reports. The decision prioritizes events, highlighting a small number of real violations that pose the most serious threat to business. The detected anomalies make it possible to detect changes in behavior associated with applications, computers, users, and network segments. When using the IBM X-Force Threat Intelligence software, actions associated with suspicious IP addresses are also determined.
The solution provides an opportunity to more effectively manage threats by tracking serious incidents and providing links to all the required data for analysis. This allows you to detect actions after hours or unusual use of applications and cloud services, as well as network activity that does not match stored usage patterns. To improve analytics, QRadar SIEM supports the ability to search events and data streams in near real-time mode, as well as stored data. It is possible to perform a combined search in large distributed environments. For a deeper understanding and better display of applications, databases, collaboration products and social networks, you can use the IBM QRadar QFlow and IBM QRadar VFlow Collector devices,
The ability to install in the cloud SoftLayer allows QRadar SIEM to receive real-time security information in the cloud. Moreover, the collection of events and data streams from applications is performed both in the cloud and on local resources.
The solution has an intuitive reporting module that does not require special databases or special skills from IT administrators. Generating reports on data access and user activity with the ability to track information by name and IP address ensures compliance with security policies, as well as compliance with regulatory requirements.
Associated components
A number of modules are integrated with the QRadar SIEM tool to increase its efficiency. One of the most important is QRadar Risk Manager, which compares vulnerability information with data on network topology and connections. The solution identifies vulnerabilities in the company’s network and the applications running in it, assessing risks and minimizing them. Risk Manager monitors the configuration of switches, routers, firewalls and intrusion prevention systems (IPS), recognizing conditions that pose a security risk. In addition, it allows you to simulate network attacks and other intrusion scenarios, making changes to the network configuration that make it possible to assess the magnitude of the threat.
Another interesting tool is the QRadar Log Manager module. It collects and processes real-time event data from routers, switches, firewalls, VPNs, intrusion detection and prevention systems (IDS / IPS), antivirus programs, and other sources. Log Manager provides an opportunity to simplify the maintenance of necessary reporting and monitoring compliance with regulatory requirements.
As an afterword
IBM QRadar SIEM is one of the most effective analytic security systems. It is also important that the solution supports working with more than 200 products from leading manufacturers and collects, analyzes and correlates data through a wide range of systems, including network solutions, security tools, servers, hosts, operating systems and applications. In addition, an additional advantage of the solution is the low cost of the entry-level system.
