Automating the search for clones of sites and one-day sites
Attackers, in order to infect users' computers, very often use methods aimed at deceiving users who type the address of the site they are interested in in the browser line. For example, typosquatting (aka hijacking URL), that is, the use of user errors, which may be mistaken in writing the domain on the keyboard. For example, if you make a mistake in spelling the cisco.ru domain and instead of the first letter “c” type the letter “v” next to the keyboard, then we will not get to the Cisco website, but to the domain that is currently on sale.
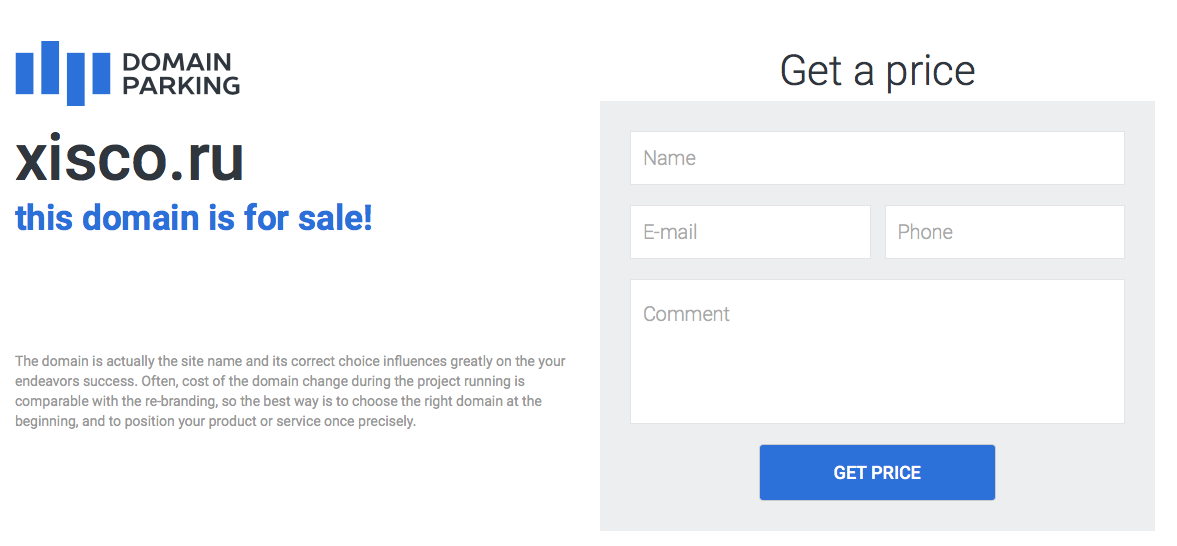
And if, for example, instead of “sberbank.ru”, you enter the domain “sbrrbank.ru” (confusing the “e” and “r” standing next to each other), then we will get to such a resource.

Finally, lack of knowledge of the Russian language and the use of Sberbank instead of Sberbank leads us to an online casino:

All this is quite harmless, but still unpleasant cases that can end with nothing more than user dissatisfaction or a blow to the reputation of the organization whose brand is used to enrich other, less well-known companies (for example, by displaying ads). But what if the attacker uses user errors to explicitly harm them by infecting their computers with malicious code located on a site with a similar name? For example, there is a well-known example of the long existence of the site goggle.com, which distributes malicious code and fake SpySheriff antivirus, or the yuube.com domain, which redirects users to a malicious site. In addition to the mistakes of users themselves when typing with the keyboard, attackers can also count on the carelessness of users who do not immediately see the difference between vkontakte. ru and vkolakte.ru (a real example) in mailing lists or links on various Internet resources. But how to deal with them?
The fight against such domains is simple on the one hand. It is enough just to track through the domain registrars or whois service the emergence of new domains on the Internet. But this is also the difficulty - the number of such new domains can be huge and they can appear daily (in fact, every minute). In manual mode, tracking such changes is difficult. For example, here's what a simple search for domains that contain a link to the popular and yet not banned in Russia social network Facebook looks like:

Several hundred such domains. And look, for example, at domains that use "microsoft" in their name. There are not only a lot of them, but they are constantly being created (the screenshot was taken just on March 10).

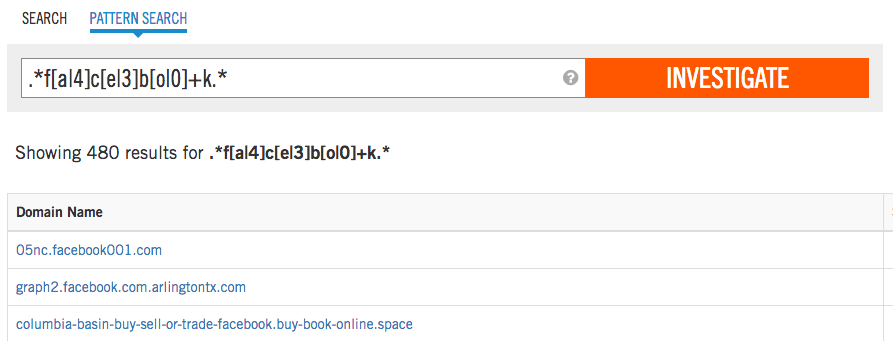
It is worth noting that the search is complicated by the fact that attackers can create domains using various combinations of characters that are not usually used by companies whose domains are selected as victims. For example, attackers can replace the letter “o” with the number “0”, the letter “A” with the number “4”, the capital “i” with the lowercase “L”, “s” with “5”, “z”, “es” or "2", etc. For Facebook, it looks like this:

Finally, an attacker can use character repetition. The same “facebook” can be replaced with a “faceboook” and this may go unnoticed:
If we ignore the bourgeois examples and look at the Runet, then taking the most popular bank in Russia as an example, we get the following picture:

A large number of domains (sometimes clearly causing questions) use the word "sberbank" as their basis. Interestingly, multiple studies show that for some reason users tend to trust such domains, believing that the domain in which the name of the company (or a popular product / service) is mentioned belongs to this company, and not to someone else. And therefore, the likelihood of clicking on such links is much higher than on links that do not use the names of the victim companies.
It is clear that Sberbank is not the only company that suffers from the described attacks. For example, in RuNet you can find domains related to Cisco:

or the website of the President of the Russian Federation:

At the same time, I consciously in this article chose clearly malicious domains that are detected using the Cisco OpenDNS Investigate service, which is designed specifically for investigating such attacks. Passing through itself 80 billion DNS queries daily, Cisco OpenDNS services (Investigate for investigation and Umbrella for blocking) analyze a huge number of domains and their activity, classifying and placing them in our databases, which can then be accessed using various tools. For example, the above screenshots were taken using Cisco OpenDNS Investigate, in the interface of which through a normal browser you can conduct investigations on the domain of interest (as well as the IP address, autonomous system or e-mail of the domain owner).
To automate this task and the ability to check domains of interest on the fly (for example, through firewalls, Internet access control systems, SIEMs, SOCs, etc.), you can use the Investigate API developed by us. For example, the code below allows you to find the desired string in the domains created in the last day:
The search string can be created in advance and include all possible combinations of characters that may occur in the domains of interest to us. In the event that there are several brands that we want to monitor, then it is better to use a separate script, which at the output produces a set of possible replacements for a particular character:
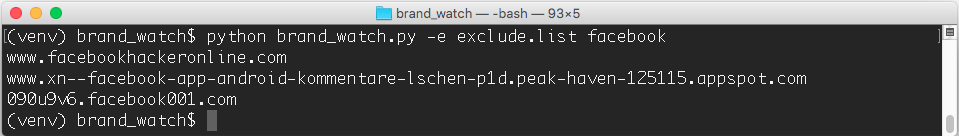
Next, we can only on a regular basis (for example, once a day) monitor the Internet in search of new domains that appear using us interesting brand names (companies, products, services, etc.). We automated this task as a barnd_watch script in Python, which can be found on GitHub . It’s easy to work with it - just specify the search string of interest to us:

If we want to exclude some domains from the search (if it is assumed that there will be many of them in the search results), then for this it is enough to give a script file with a prepared domain exceptions:
In such a simple way, Cisco OpenDNS helps automate the process of searching for clone sites and other domains used by attackers to attack companies and their users. The advantage of the services of Cisco OpenDNS Investigate or Cisco OpenDNS Umbrella is that they not only automate the search, but also using classification algorithms, allows you to immediately make a conclusion about the harmfulness of a particular domain. Here's how, for example, it looks for a domain that uses the Gazprombank brand:

Further, it is already possible to carry out relevant investigations using the same Cisco OpenDNS Investigate service, which will tell us who and when created this domain, where it is located, which other domains are located on the same IP address or in an autonomous system, as well as other related information ( distributed malicious code, other domains belonging to this owner, etc.). But about these features of Cisco OpenDNS Investigate another time.
In conclusion, I would like to note that such attacks are used not only to direct users to fake sites. By creating fake domains similar to the site of the victim company, you can send phishing emails on their behalf that increase the likelihood of user infection. We even made a special video clip (actually several), which demonstrates an attack based on this particular attack method, against which Cisco OpenDNS solutions work.
Threat. It will be possible to see and "feel" this solution on Cisco Connect, which will be held in Moscow on April 4-5, where we have planned a rich program on cybersecurity.

And if, for example, instead of “sberbank.ru”, you enter the domain “sbrrbank.ru” (confusing the “e” and “r” standing next to each other), then we will get to such a resource.

Finally, lack of knowledge of the Russian language and the use of Sberbank instead of Sberbank leads us to an online casino:

All this is quite harmless, but still unpleasant cases that can end with nothing more than user dissatisfaction or a blow to the reputation of the organization whose brand is used to enrich other, less well-known companies (for example, by displaying ads). But what if the attacker uses user errors to explicitly harm them by infecting their computers with malicious code located on a site with a similar name? For example, there is a well-known example of the long existence of the site goggle.com, which distributes malicious code and fake SpySheriff antivirus, or the yuube.com domain, which redirects users to a malicious site. In addition to the mistakes of users themselves when typing with the keyboard, attackers can also count on the carelessness of users who do not immediately see the difference between vkontakte. ru and vkolakte.ru (a real example) in mailing lists or links on various Internet resources. But how to deal with them?
The fight against such domains is simple on the one hand. It is enough just to track through the domain registrars or whois service the emergence of new domains on the Internet. But this is also the difficulty - the number of such new domains can be huge and they can appear daily (in fact, every minute). In manual mode, tracking such changes is difficult. For example, here's what a simple search for domains that contain a link to the popular and yet not banned in Russia social network Facebook looks like:

Several hundred such domains. And look, for example, at domains that use "microsoft" in their name. There are not only a lot of them, but they are constantly being created (the screenshot was taken just on March 10).

It is worth noting that the search is complicated by the fact that attackers can create domains using various combinations of characters that are not usually used by companies whose domains are selected as victims. For example, attackers can replace the letter “o” with the number “0”, the letter “A” with the number “4”, the capital “i” with the lowercase “L”, “s” with “5”, “z”, “es” or "2", etc. For Facebook, it looks like this:

Finally, an attacker can use character repetition. The same “facebook” can be replaced with a “faceboook” and this may go unnoticed:

If we ignore the bourgeois examples and look at the Runet, then taking the most popular bank in Russia as an example, we get the following picture:

A large number of domains (sometimes clearly causing questions) use the word "sberbank" as their basis. Interestingly, multiple studies show that for some reason users tend to trust such domains, believing that the domain in which the name of the company (or a popular product / service) is mentioned belongs to this company, and not to someone else. And therefore, the likelihood of clicking on such links is much higher than on links that do not use the names of the victim companies.
It is clear that Sberbank is not the only company that suffers from the described attacks. For example, in RuNet you can find domains related to Cisco:

or the website of the President of the Russian Federation:

At the same time, I consciously in this article chose clearly malicious domains that are detected using the Cisco OpenDNS Investigate service, which is designed specifically for investigating such attacks. Passing through itself 80 billion DNS queries daily, Cisco OpenDNS services (Investigate for investigation and Umbrella for blocking) analyze a huge number of domains and their activity, classifying and placing them in our databases, which can then be accessed using various tools. For example, the above screenshots were taken using Cisco OpenDNS Investigate, in the interface of which through a normal browser you can conduct investigations on the domain of interest (as well as the IP address, autonomous system or e-mail of the domain owner).
To automate this task and the ability to check domains of interest on the fly (for example, through firewalls, Internet access control systems, SIEMs, SOCs, etc.), you can use the Investigate API developed by us. For example, the code below allows you to find the desired string in the domains created in the last day:
inv = investigate.Investigate('12345678-1234-1234-1234-1234567890ab')
inv.search('searchregex', start=datetime.timedelta(days=1), limit=100, include_category=False)The search string can be created in advance and include all possible combinations of characters that may occur in the domains of interest to us. In the event that there are several brands that we want to monitor, then it is better to use a separate script, which at the output produces a set of possible replacements for a particular character:
self.word = word
self.a=['a','4']
self.b=['b','8','6']
self.c=['c','k']
self.d=['d','0']
self.e=['e','3']
self.f=['f']
self.g=['g','6','9']
self.h=['h']
self.i=['i','!','1','|','l']
self.j=['j']
self.k=['k','x']
self.l=['l','1','7']
self.m=['m','nn']
self.n=['n']
self.o=['o','0']
self.p=['p','9','q']
self.q=['q','9']
self.r=['r']
self.s=['s','5','z','es','2']
self.t=['t','7','1']
self.u=['u','m']
self.v=['v']
self.w=['w','vv']
self.x=['x','ex']
self.y=['y','j']
self.z=['z','2']
self.zero=['0','o']
self.one=['1','l']
self.two=['two','2','z']
self.three=['e','3','three']
self.four=['4','four','for','fore','a']
self.five=['5','five','s']
self.six=['6','six','g']
self.seven=['7','seven','t','l']
self.eight=['8','eight','b']
self.nine=['9','nine','g']
self.alphabet={ 'a':self.a, 'b':self.b, 'c':self.c,
'd':self.d, 'e':self.e, 'f':self.f, 'g':self.g,
'h':self.h, 'i':self.i, 'j':self.j, 'k':self.k,
'l':self.l, 'm':self.m, 'n':self.n, 'o':self.o,
'p':self.p, 'q':self.q, 'r':self.r, 's':self.s,
't':self.t, 'u':self.u, 'v':self.v, 'w':self.w,
'x':self.x, 'y':self.y, 'z':self.z, '0':self.zero,
'1':self.one,'2':self.two,'3':self.three,'4':self.four,
'5':self.five,'6':self.six,'7':self.seven,'8':self.eight,
'9':self.nine }
def get_permutations(self, letter):
try:
permutations = self.alphabet[letter]
except KeyError:
permutations = letter
regex = '['
for p in permutations[:-1]:
regex += '{0}|'.format(p)
regex += '{0}]'.format(permutations[-1])
return regexNext, we can only on a regular basis (for example, once a day) monitor the Internet in search of new domains that appear using us interesting brand names (companies, products, services, etc.). We automated this task as a barnd_watch script in Python, which can be found on GitHub . It’s easy to work with it - just specify the search string of interest to us:

If we want to exclude some domains from the search (if it is assumed that there will be many of them in the search results), then for this it is enough to give a script file with a prepared domain exceptions:

In such a simple way, Cisco OpenDNS helps automate the process of searching for clone sites and other domains used by attackers to attack companies and their users. The advantage of the services of Cisco OpenDNS Investigate or Cisco OpenDNS Umbrella is that they not only automate the search, but also using classification algorithms, allows you to immediately make a conclusion about the harmfulness of a particular domain. Here's how, for example, it looks for a domain that uses the Gazprombank brand:

Further, it is already possible to carry out relevant investigations using the same Cisco OpenDNS Investigate service, which will tell us who and when created this domain, where it is located, which other domains are located on the same IP address or in an autonomous system, as well as other related information ( distributed malicious code, other domains belonging to this owner, etc.). But about these features of Cisco OpenDNS Investigate another time.
In conclusion, I would like to note that such attacks are used not only to direct users to fake sites. By creating fake domains similar to the site of the victim company, you can send phishing emails on their behalf that increase the likelihood of user infection. We even made a special video clip (actually several), which demonstrates an attack based on this particular attack method, against which Cisco OpenDNS solutions work.
Threat. It will be possible to see and "feel" this solution on Cisco Connect, which will be held in Moscow on April 4-5, where we have planned a rich program on cybersecurity.
