Cryptography and secure communications: the history of the first ciphers
- Transfer
Cryptography and encryption has been used by people for thousands of years to protect their secrets. With some degree of conventionality, this story can begin with Ancient Egypt.
The oldest text with elements of cryptography was found in the tomb of the ancient Egyptian nobleman Khnumhotep II, the crown prince and nomarch of the city of Menat Khufu, who lived almost 4000 years ago. Somewhere around 1900 BC the clerk of Khnumhotep described the life of his master in his tomb. Among the hieroglyphs, he used several unusual characters that hide the direct meaning of the text. This encryption method is actually a substitution cipher, when the elements of the source text are replaced by other elements according to certain rules.

Symbols from the tomb of Khnumhotep II and their decoding
As the Egyptian culture developed, the replacement of hieroglyphs met more and more often. There are different versions of why the Egyptians used such an encryption system. According to one version, they wanted to protect their religious rituals from ordinary people. According to another version, in this way the scribes gave the text a certain formal appearance, as in our time lawyers use specific expressions to replace ordinary words. As now, Egyptian cryptography could also be a way for a scribe to impress other people - to show that he can speak at a higher level than they do.
Around 500 g BC the Spartans developed a device called a wanderer, designed to send and receive secret messages. It was a cylinder wrapped in a spiral with a narrow strip of parchment. The message was written along the wanderer, but if you expand the strip, it becomes unreadable. To read the text required a wanderer of the same diameter. Only in this case, the letters became in a row to restore the original message.

An example of a wanderer A wanderer
is an example of a permutation cipher in which the elements of the source text are interchanged rather than replaced by other characters. By modern standards, it would be very easy to hack into a wanderer, but 2500 years ago very few people could read and write. The wanderer provided the Spartans with a secure connection.
The earliest known method of military use of cryptography belongs to Julius Caesar. About 2000 years ago, Caesar, as a commander of the Roman army, solved the problem of secure communications with his regiments. The problem was that messengers with secret military communications were often intercepted by the enemy. Caesar developed a substitution cipher in which he replaced one letter with another. Only someone who knew the lookup table could decrypt the secret message. Now, even if the messenger falls into the hands of the enemy, the encryption will not be declassified. This gave the Romans a huge advantage in the war.
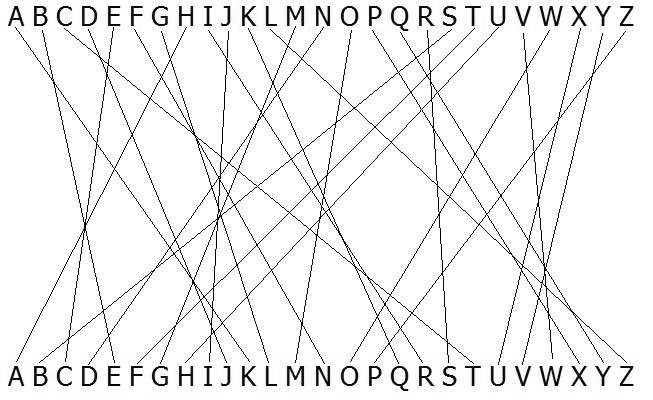
Example of a substitution cipher
In contrast to the example in this illustration, Caesar usually simply shifted the letters by a certain number. This number was the encryption key for its algorithm. Random character replacement provides much better security with more possible replacement tables.
In the mid-15th century, Italian scientist, architect, sculptor, artist and mathematician Leon Batista Alberti invented an encryption system based on an encryption disk. It was a mechanical device with sliding disks that allowed for many different character substitution methods. This is the basic concept of a multi-alphabet cipher, in which the encryption method changes directly during the encryption process. In his book, Code Crackers, David Kahn calls Alberti "the father of Western cryptography." Alberti never realized his concept of an encryption disk, it remained only on paper.
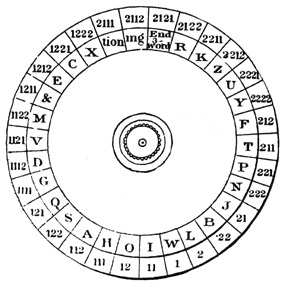
Cipher disk
In the 16th century, French diplomat Blaise Vizhener, based on the concept of a multi-alphabetic cipher, Alberti created a cipher, which was called the Vigenere cipher. It works exactly like Caesar’s system except that the key changes during the encryption process. The Vizhener cipher uses a lattice of letters, which sets the substitution method. It is called the Vigenère Square or the Vigenère Table. The lattice consists of 26 lines of the alphabet with an offset of one character relative to each other.

The method of changing one key to another follows a simple pattern. A special secret word is selected as the encryption key. Each character in the source text is replaced using a table. To determine which letter the first character needs to be replaced, we combine the first character of the source text (on one axis) with the first character of the secret word (on the other axis). The method is repeated for the second and each subsequent letter, the secret word is used repeatedly until the characters in the source text end.
Suppose you want to encrypt a phrase like this:
The sender of the message selects the secret word and repeats it until the end of the source text. For example, LEMON.
To encrypt the first character, you need to combine row A with column L (the result is L), to encrypt the second character - row T with column E (the result is X) and so on. Here is the result:
Decryption is performed in the same way: the letter in the text of the message (diagonal rows of the table) is combined with the letter of the secret word in the columns or rows of the table.
At the end of the 18th century, Thomas Jefferson came up with an encryption system, very similar to the Vigenere cipher, but with better protection. Its encoder consisted of 26 disks with letters of the alphabet randomly placed on each. The disks were numbered and mounted on the cylinder in a specific order. The key is the order of the disks on the axis.

Jefferson Disk Cipher
To encrypt a message, you need to compose the source text in one of the lines of the cylinder. The encrypted text will be any other line. The message recipient must arrange the disks in the correct order, and then compose a line of ciphertext on the cylinder. Then a quick visual inspection of the cylinder immediately reveals the text of the original message. Almost zero probability that two messages without meaning will appear in the lines of the cylinder.
Like Alberti, Jefferson never used his encryption system. At the beginning of the 20th century, cryptographers of the American army invented anew the Jefferson cylinder, knowing nothing about this invention. Jefferson is ahead of his time by more than a hundred years. The U.S. Army used such an encryption system from 1923 to 1942.
Ancient Egypt
The oldest text with elements of cryptography was found in the tomb of the ancient Egyptian nobleman Khnumhotep II, the crown prince and nomarch of the city of Menat Khufu, who lived almost 4000 years ago. Somewhere around 1900 BC the clerk of Khnumhotep described the life of his master in his tomb. Among the hieroglyphs, he used several unusual characters that hide the direct meaning of the text. This encryption method is actually a substitution cipher, when the elements of the source text are replaced by other elements according to certain rules.

Symbols from the tomb of Khnumhotep II and their decoding
As the Egyptian culture developed, the replacement of hieroglyphs met more and more often. There are different versions of why the Egyptians used such an encryption system. According to one version, they wanted to protect their religious rituals from ordinary people. According to another version, in this way the scribes gave the text a certain formal appearance, as in our time lawyers use specific expressions to replace ordinary words. As now, Egyptian cryptography could also be a way for a scribe to impress other people - to show that he can speak at a higher level than they do.
Ancient Greece
Around 500 g BC the Spartans developed a device called a wanderer, designed to send and receive secret messages. It was a cylinder wrapped in a spiral with a narrow strip of parchment. The message was written along the wanderer, but if you expand the strip, it becomes unreadable. To read the text required a wanderer of the same diameter. Only in this case, the letters became in a row to restore the original message.

An example of a wanderer A wanderer
is an example of a permutation cipher in which the elements of the source text are interchanged rather than replaced by other characters. By modern standards, it would be very easy to hack into a wanderer, but 2500 years ago very few people could read and write. The wanderer provided the Spartans with a secure connection.
Ancient Rome
The earliest known method of military use of cryptography belongs to Julius Caesar. About 2000 years ago, Caesar, as a commander of the Roman army, solved the problem of secure communications with his regiments. The problem was that messengers with secret military communications were often intercepted by the enemy. Caesar developed a substitution cipher in which he replaced one letter with another. Only someone who knew the lookup table could decrypt the secret message. Now, even if the messenger falls into the hands of the enemy, the encryption will not be declassified. This gave the Romans a huge advantage in the war.

Example of a substitution cipher
In contrast to the example in this illustration, Caesar usually simply shifted the letters by a certain number. This number was the encryption key for its algorithm. Random character replacement provides much better security with more possible replacement tables.
Alberti-Vigenenera code
In the mid-15th century, Italian scientist, architect, sculptor, artist and mathematician Leon Batista Alberti invented an encryption system based on an encryption disk. It was a mechanical device with sliding disks that allowed for many different character substitution methods. This is the basic concept of a multi-alphabet cipher, in which the encryption method changes directly during the encryption process. In his book, Code Crackers, David Kahn calls Alberti "the father of Western cryptography." Alberti never realized his concept of an encryption disk, it remained only on paper.

Cipher disk
In the 16th century, French diplomat Blaise Vizhener, based on the concept of a multi-alphabetic cipher, Alberti created a cipher, which was called the Vigenere cipher. It works exactly like Caesar’s system except that the key changes during the encryption process. The Vizhener cipher uses a lattice of letters, which sets the substitution method. It is called the Vigenère Square or the Vigenère Table. The lattice consists of 26 lines of the alphabet with an offset of one character relative to each other.

The method of changing one key to another follows a simple pattern. A special secret word is selected as the encryption key. Each character in the source text is replaced using a table. To determine which letter the first character needs to be replaced, we combine the first character of the source text (on one axis) with the first character of the secret word (on the other axis). The method is repeated for the second and each subsequent letter, the secret word is used repeatedly until the characters in the source text end.
Suppose you want to encrypt a phrase like this:
ATTACKATDAWN («Нападение на рассвете»)The sender of the message selects the secret word and repeats it until the end of the source text. For example, LEMON.
LEMONLEMONLETo encrypt the first character, you need to combine row A with column L (the result is L), to encrypt the second character - row T with column E (the result is X) and so on. Here is the result:
Исходный текст: ATTACKATDAWN
Ключевое слово: LEMONLEMONLE
Шифротекст: LXFOPVEFRNHRDecryption is performed in the same way: the letter in the text of the message (diagonal rows of the table) is combined with the letter of the secret word in the columns or rows of the table.
Jefferson Disk Cipher
At the end of the 18th century, Thomas Jefferson came up with an encryption system, very similar to the Vigenere cipher, but with better protection. Its encoder consisted of 26 disks with letters of the alphabet randomly placed on each. The disks were numbered and mounted on the cylinder in a specific order. The key is the order of the disks on the axis.

Jefferson Disk Cipher
To encrypt a message, you need to compose the source text in one of the lines of the cylinder. The encrypted text will be any other line. The message recipient must arrange the disks in the correct order, and then compose a line of ciphertext on the cylinder. Then a quick visual inspection of the cylinder immediately reveals the text of the original message. Almost zero probability that two messages without meaning will appear in the lines of the cylinder.
Like Alberti, Jefferson never used his encryption system. At the beginning of the 20th century, cryptographers of the American army invented anew the Jefferson cylinder, knowing nothing about this invention. Jefferson is ahead of his time by more than a hundred years. The U.S. Army used such an encryption system from 1923 to 1942.
