Citrix NetScaler and One-Time Passwords
 Friends, good afternoon! I thought about the topic of the next article for a long time, I wanted to cover the vast and not seem biased. I thought about analytics, administration, and just about how to. As a result, the decisive factor was the next contact of a friend “on the shop floor” with the question of organizing 2-factor authentication for Citrix solutions. At one time, I wrote about a solution based on x509 certificates, and offered them to a colleague. But most of his remote clients were based on apple solutions, and in this case the access device and certificate were either in the old Head & Shoulders 2-in-1 ad, or as a bunch of keys to all the locks on one bunch. In the end, I want this article to cover a bit of administration, analysis and analytics.
Friends, good afternoon! I thought about the topic of the next article for a long time, I wanted to cover the vast and not seem biased. I thought about analytics, administration, and just about how to. As a result, the decisive factor was the next contact of a friend “on the shop floor” with the question of organizing 2-factor authentication for Citrix solutions. At one time, I wrote about a solution based on x509 certificates, and offered them to a colleague. But most of his remote clients were based on apple solutions, and in this case the access device and certificate were either in the old Head & Shoulders 2-in-1 ad, or as a bunch of keys to all the locks on one bunch. In the end, I want this article to cover a bit of administration, analysis and analytics.The architectural solution was based on OTP, or simply - the second “factor" - a one-time password. I believe you should not dwell on the advantages of using OTP, understanding their effectiveness, similarly to the need to use 2-factor authorization of resources and services that are accessible on the Internet (or on the Internet). Here I will run a little ahead: in my work, after introducing 2-factor authorization to access corporate information systems using one-time passwords, users with remote access (mainly middle-level managers) began to ask questions about “what became so difficult and uncomfortable ??? ”, they say no one uses it anywhere, so why run ahead of the rest? I ask, and the client bank sends a new password every time - this is normal. Usually after this, the issue of safety and convenience is removed. So, here the lyrics and analytics have passed, we will continue further.
I’ll dwell on the components of the solution used to implement this solution, and in the description I’ll focus only on the cornerstones of the settings, namely NetScaler profiles, StoreFront settings and iPad client devices. So, in stock: Deployed infrastructure XenDesktop / App, StoreFront, Citrix NetScalaler, RADIUS server, OTP server. As clients, I suggest using Google Authenticator (although the choice of free OTP clients is quite large). Regarding the implementation of OTP solutions, I also believe that this remains on the “conscience” of a particular project. This can be a one-time password on a mobile phone or via SMS or other options. Configuring the RADIUS server itself with the functionality of one-time passwords is a topic for a separate conversation, we outline its contours in passing.
Having determined the need to use 2-factor authorization, let's look at the NetScaler settings that ensure the use of the selected method and the correct operation from all types of devices:
First, create rules for a RADIUS connection and a RADIUS server:
add authentication radiusPolicy RSA-SelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" RSA
add authentication radiusPolicy RSA-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" RSA
add authentication radiusAction RSA -serverIP 192.168.60.43 -serverPort 1812 -radKey ……
add authentication ldapPolicy LDAP-Corp-SelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" AD
add authentication ldapPolicy LDAP-Corp-Web "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" AD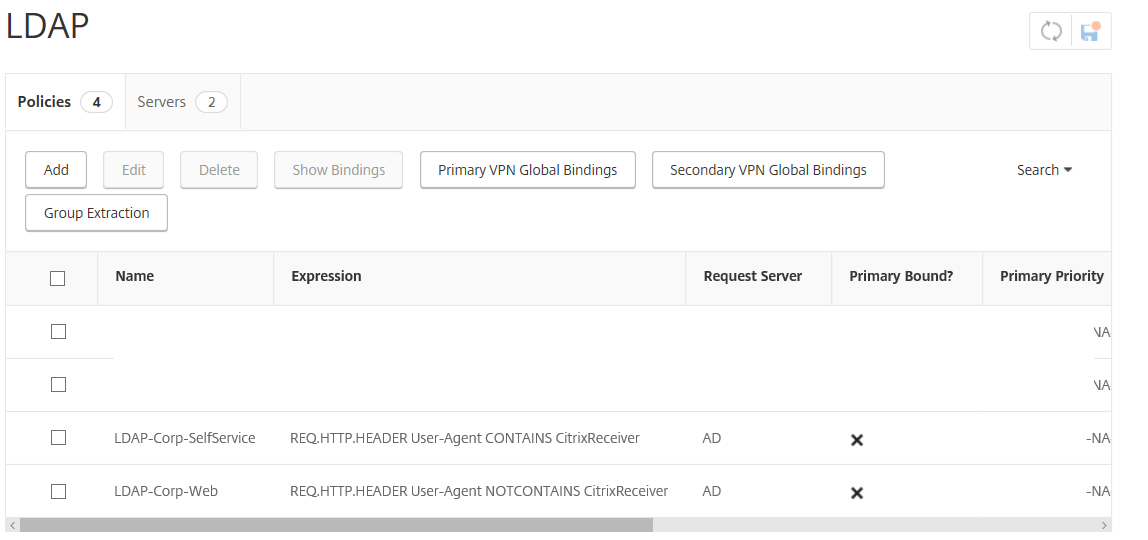
The final chord will be the connection of the created policies to the prepared SSL VPNc server:
bind vpn vserver ssl_ag_xd_wa2.*******.ru -policy LDAP-Corp-Web -priority 100
bind vpn vserver ssl_ag_xd_wa2.*******.ru -policy RSA-SelfService -priority 110
bind vpn vserver ssl_ag_xd_wa2.*******.ru -policy RSA-ReceiverForWeb -priority 100 -secondary
bind vpn vserver ssl_ag_xd_wa2.*******.ru -policy LDAP-Corp-SelfService -priority 110 -secondary
It remains to register the connection point on StoreFront (in the video below it will be clear):

In the Logon type field, select “Domain and security token”.

Administration is simple, let's move on. It remains to see this solution live:
1. Access via a WEB browser
2. Access from iOS (iPad)
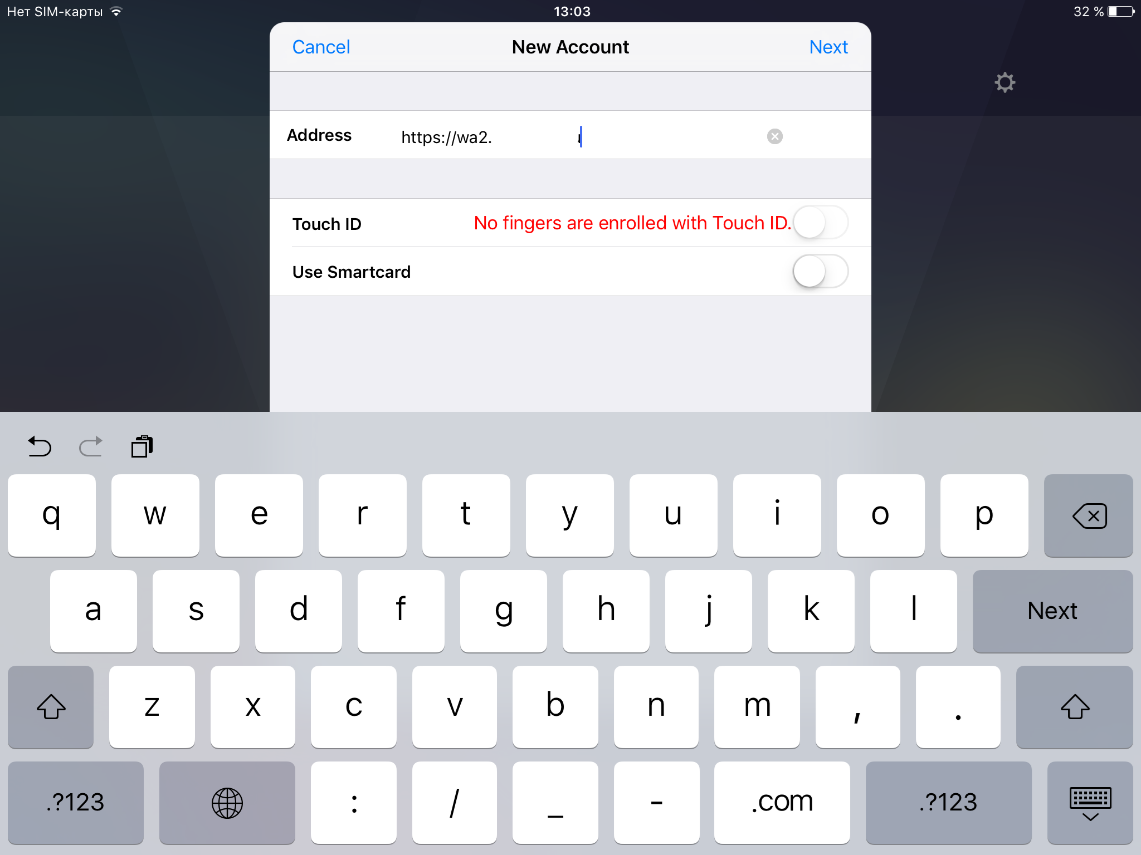
Add a new account:
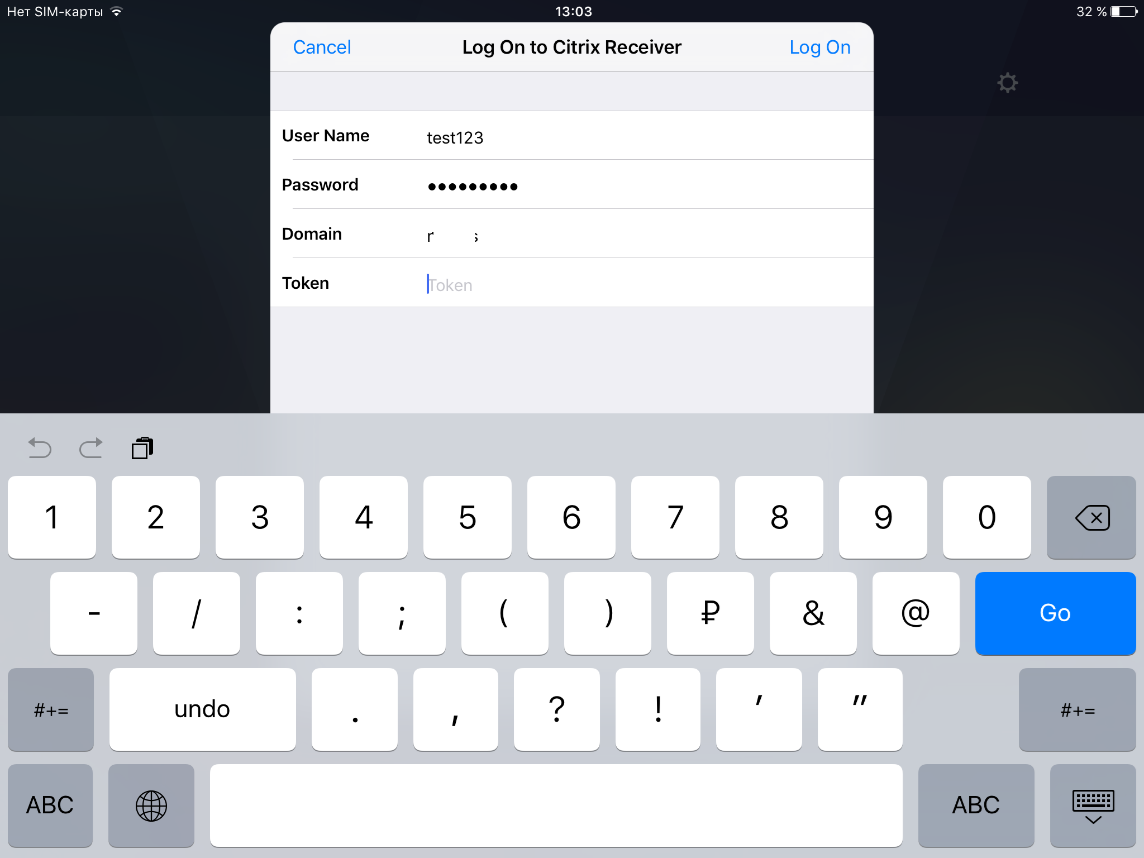
Enter username, password, domain, one-time code:
In the connection properties we see the type of location selected (This is on StoreFront)):

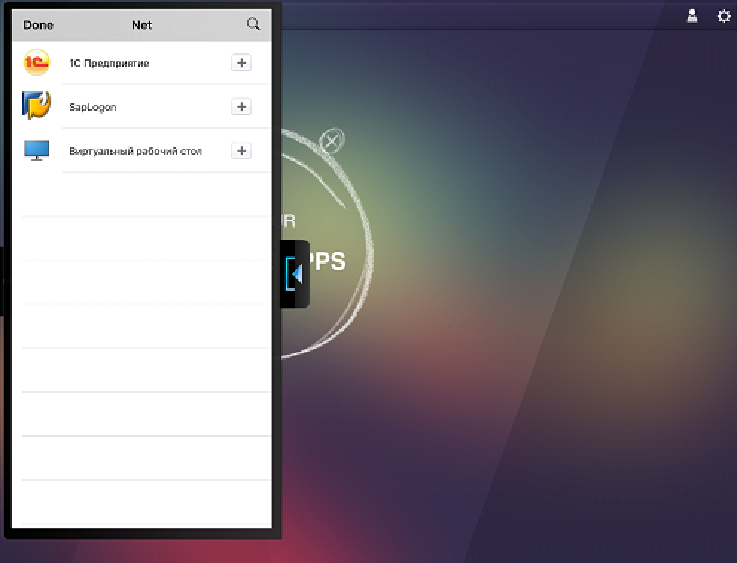
We see a list of published applications:
When the application starts, a password and PIN are requested Code:
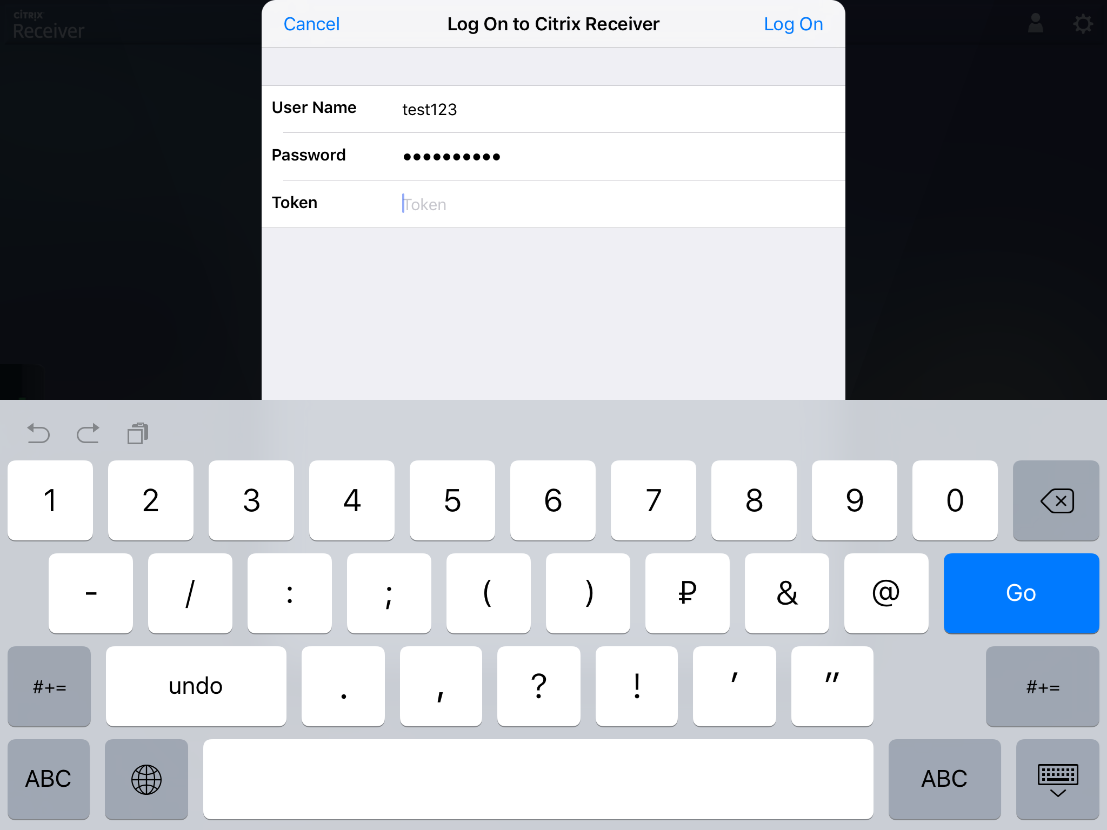
3. Classic Citrix Receiver
So, 2-factor authorization is not only an effective and reliable method of publishing corporate information systems on the Internet, but also convenient, and most importantly, it is a modern solution, so to speak, “keeping up to date”.
It is up to you to stay on x509 or OTP, but the fact that this mechanism should be implemented is unambiguous.
PS. In my daily work, I “mandatory” use 2-factor authentication, based on all of the above, a question arose for readers formulated in the survey. Please vote:
Only registered users can participate in the survey. Please come in.
Do you use 2 factor authorization when publishing corporate services on the Internet?
- 56.2% Yes 9
- 37.5% No 6
- 6.2% I have nothing to protect ... 1
