How to protect a smart home: A solution from the ITMO University team
The market for smart home systems is not developing as fast as it seemed a few years ago - in Russia it is quite rare to find fully automated homes. In addition to the complexity of implementation and high cost, such systems have one more drawback - a smart home can be hacked quite easily.
Today we will talk about the degree of security of such systems and how to make them safer with the help of developments created at ITMO University. Amir Zmora / Flickr / CC

Often, developers do not pay enough attention to the safety of created products. For example, there is a case where an information security researcher was able to find a link to the smart home system management interface directly on Google. The page was not password protected, so he got the ability to manage all smart systems, and also learned the address of the house and the phone number of its owner.
Without problems, you can hack a smart home while on the spot. As a rule, when creating such systems - especially for residential premises - an additional level of new devices is simply “attached” to the existing infrastructure. New gadgets communicate with each other using protocols for wireless communication. And often, system developers choose protocols that do not require encryption, so that anyone who is connected to the room network can intercept data.
In general, a smart home system diagram represents two main data streams in which control signals are transmitted:

/ Formal model of the Smart Home system. Illustration from the article "Authentication of Automation Devices in the Smart Home System" by the authors of the Safe Smart Home project.
The first stream is between the user and the control system - commands from the person to the computer are transmitted there. To do this, use the interface: terminal, mobile device, web application, etc. The main data stream is the second, between the control system and the automation end devices.
Automation devices, a control system, and the information flow between them are some of the most vulnerable elements in a smart home. Most often in modern systems, communication between their elements goes through open channels without ensuring confidentiality and data integrity. As a result, attackers can easily listen to the information flows of the system, gain access to its specific elements and, in some cases, take complete control of the rooms.
The participants of the Safe Smart Home project are trying to answer this question - it is being developed by the team of the Department of Safe Information Technologies of ITMO University. Specialists are developing a software and hardware complex for a smart home that will be devoid of the main disadvantages of current systems.
In order to secure the system, it is necessary first of all to increase the security of all the weak links described above. For example, choose a secure way to transfer data. The project team conducted an analysisthe communication protocols used in such systems - according to the results of this work, it was found that from the point of view of the main characteristics, the best choice for such systems is Zig-Bee technology. This protocol maximizes data privacy, integrity and availability.
In addition, the system must correctly respond to possible attacks. An attacker can not only intercept data, but also try to physically interfere with the operation of system devices, for example, disable them. In this case, other devices should notice an anomaly in the form of an inaccessible first gadget.
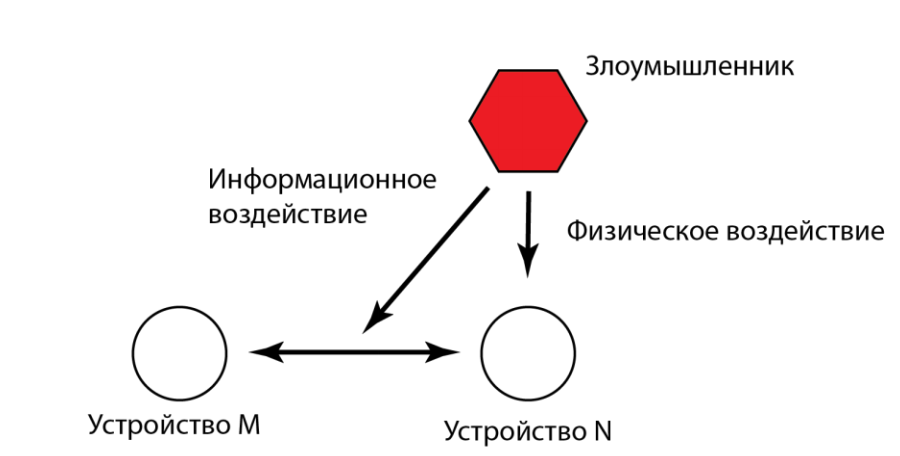
/ Scheme of the impact on the devices of the Smart Home system. Illustration from the article “Identifying anomalies in the automation systems of security objects” by the authors of the “Safe Smart Home” project
Any attempt to attack affects the characteristics of the smart home system - it means they need to be analyzed. If two devices monitor network activity and perform interaction analysis, then an attacker will not be able to hide an attack like MITM or replay.
To solve this problem, the participants of the Safe Smart Home project developed a hybrid neural network that combines two models of artificial neural networks: a self-organizing network with competition (Kohonen layer) and a multilayer perceptron.
After training, an artificial neural network is able, on the basis of incoming data, to make decisions on whether the current state of the network node is abnormal or normal with an accuracy of 91.47%. You can read more about working on the neural network used in the project here .
To implement authentication on the side of the final gadget, an Arduino Uno-based solution with an enc28j60 Ethernet controller is used. This microcontroller supports a large number of external devices, so it can be a universal link for organizing interaction with various automation elements. The system architecture is described in more detail in this article .
The team of the Department of Safe Information Technologies at ITMO University has been developing the Safe Smart Home project since 2015. During this time, the architecture of the firmware module was developed, the necessary software was written, and secure data transfer protocols were selected. The final result can seriously reduce the applicability of the main attacks on smart home systems:
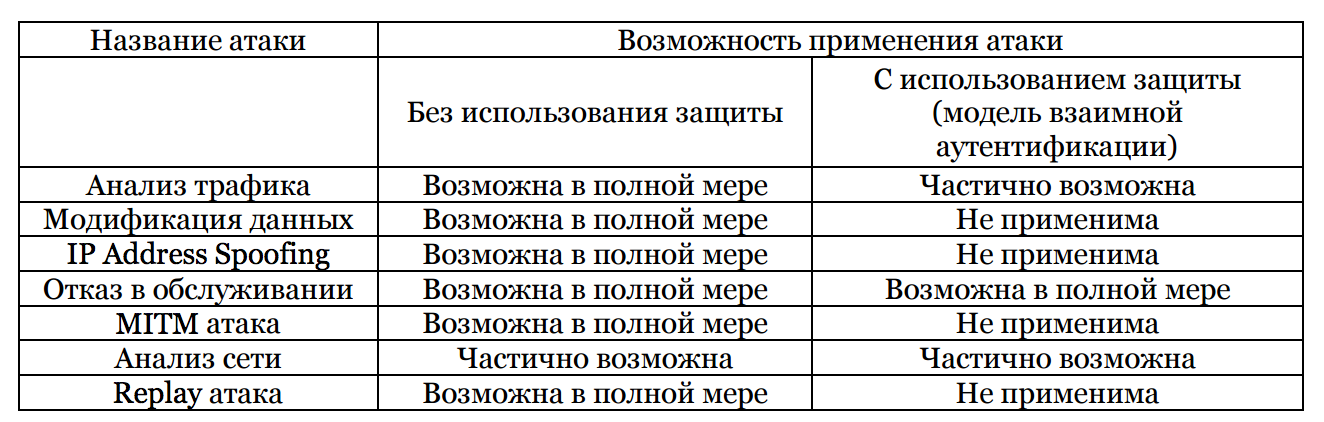
/ Results of checking the main types of network attacks before and after embedding the security device. Illustration from the article "Authentication of Automation Devices in the Smart Home System" by the authors of the Safe Smart Home project The
flexibility of the created secure smart network allows you to combine virtually any device in it and transfer data safely. Therefore, in the future its use is possible not only in residential buildings, but also in industrial ones.
Additional materials on the topic:
Today we will talk about the degree of security of such systems and how to make them safer with the help of developments created at ITMO University. Amir Zmora / Flickr / CC

What's wrong with smart home
Often, developers do not pay enough attention to the safety of created products. For example, there is a case where an information security researcher was able to find a link to the smart home system management interface directly on Google. The page was not password protected, so he got the ability to manage all smart systems, and also learned the address of the house and the phone number of its owner.
Without problems, you can hack a smart home while on the spot. As a rule, when creating such systems - especially for residential premises - an additional level of new devices is simply “attached” to the existing infrastructure. New gadgets communicate with each other using protocols for wireless communication. And often, system developers choose protocols that do not require encryption, so that anyone who is connected to the room network can intercept data.
Where is the weak link in the system
In general, a smart home system diagram represents two main data streams in which control signals are transmitted:

/ Formal model of the Smart Home system. Illustration from the article "Authentication of Automation Devices in the Smart Home System" by the authors of the Safe Smart Home project.
The first stream is between the user and the control system - commands from the person to the computer are transmitted there. To do this, use the interface: terminal, mobile device, web application, etc. The main data stream is the second, between the control system and the automation end devices.
Automation devices, a control system, and the information flow between them are some of the most vulnerable elements in a smart home. Most often in modern systems, communication between their elements goes through open channels without ensuring confidentiality and data integrity. As a result, attackers can easily listen to the information flows of the system, gain access to its specific elements and, in some cases, take complete control of the rooms.
How to make a smart home safer: ITMO University project
The participants of the Safe Smart Home project are trying to answer this question - it is being developed by the team of the Department of Safe Information Technologies of ITMO University. Specialists are developing a software and hardware complex for a smart home that will be devoid of the main disadvantages of current systems.
In order to secure the system, it is necessary first of all to increase the security of all the weak links described above. For example, choose a secure way to transfer data. The project team conducted an analysisthe communication protocols used in such systems - according to the results of this work, it was found that from the point of view of the main characteristics, the best choice for such systems is Zig-Bee technology. This protocol maximizes data privacy, integrity and availability.
In addition, the system must correctly respond to possible attacks. An attacker can not only intercept data, but also try to physically interfere with the operation of system devices, for example, disable them. In this case, other devices should notice an anomaly in the form of an inaccessible first gadget.

/ Scheme of the impact on the devices of the Smart Home system. Illustration from the article “Identifying anomalies in the automation systems of security objects” by the authors of the “Safe Smart Home” project
Any attempt to attack affects the characteristics of the smart home system - it means they need to be analyzed. If two devices monitor network activity and perform interaction analysis, then an attacker will not be able to hide an attack like MITM or replay.
To solve this problem, the participants of the Safe Smart Home project developed a hybrid neural network that combines two models of artificial neural networks: a self-organizing network with competition (Kohonen layer) and a multilayer perceptron.
After training, an artificial neural network is able, on the basis of incoming data, to make decisions on whether the current state of the network node is abnormal or normal with an accuracy of 91.47%. You can read more about working on the neural network used in the project here .
To implement authentication on the side of the final gadget, an Arduino Uno-based solution with an enc28j60 Ethernet controller is used. This microcontroller supports a large number of external devices, so it can be a universal link for organizing interaction with various automation elements. The system architecture is described in more detail in this article .
Conclusion
The team of the Department of Safe Information Technologies at ITMO University has been developing the Safe Smart Home project since 2015. During this time, the architecture of the firmware module was developed, the necessary software was written, and secure data transfer protocols were selected. The final result can seriously reduce the applicability of the main attacks on smart home systems:

/ Results of checking the main types of network attacks before and after embedding the security device. Illustration from the article "Authentication of Automation Devices in the Smart Home System" by the authors of the Safe Smart Home project The
flexibility of the created secure smart network allows you to combine virtually any device in it and transfer data safely. Therefore, in the future its use is possible not only in residential buildings, but also in industrial ones.
Additional materials on the topic:
