Where does the botnet begin: a dangerous backdoor found in Sony IP cameras

Botnets built from hundreds of thousands of infected Internet of Things devices have become one of the main trends in the cyber threats of the past year - and, apparently, will be just as popular next year. However, it is possible to predict such threats (and fight against them) several years earlier. Recently, talking about botnets based on DVR systems and webcams , we recalled that our researchers had warned of the vulnerabilities of such devices back in 2013 .
Recently, researchers from SEC Consult discovered a vulnerability, which allows you to attack 80 models of Sony IPELA Engine IP cameras, turning them into botnets or using for espionage. An interesting feature is that remote access, which is used for attack (Telnet), is disabled in these cameras. However, the backdoor left by the developers allows you to enable it with a secret team.
According to the researchers, at first they found files in the camera firmware that contained password hashes for the admin and root users:
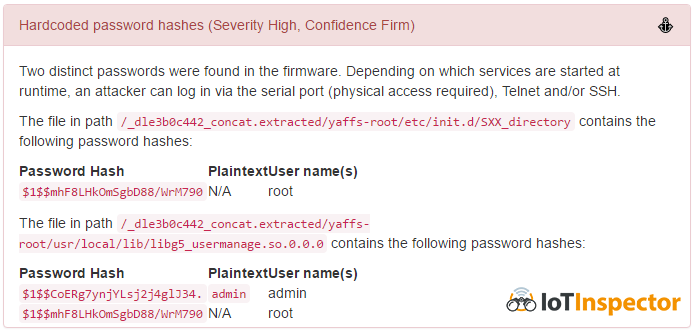
The first of the passwords turned out to be quite classic - it matches the username (admin: admin). The password for the root user can also be obtained from the hash. Such data can be used to access the device through a physical port, or remotely, via Telnet or SSH - this is exactly the opportunity the authors usedbotnet Mirai , looking for routers with default passwords like admin: admin.
However, in this case, the situation was trickier. Formally, Sony cameras do not allow Telnet access. Nevertheless, it turned out that the developers of the camera firmware left such an opportunity for themselves - apparently for testing. To do this, they wrote separate code that launches Telnet in response to a special HTTP request. The user name and username used for HTTP authentication (primana: primana) are also protected in the code:
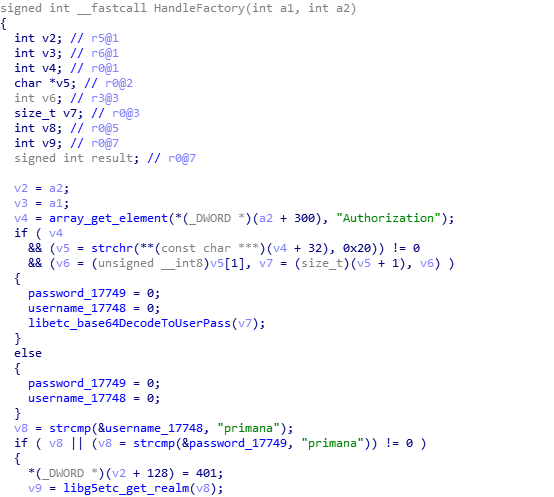
Thus, an attacker, having received all the authorization codes he needs directly from the firmware files, can remotely download any malicious code to the IP camera, which gives him many different options - from trivial spying and creating botnets to editing camera entries (we recall that, ironically, , millions of these vulnerable devices around the world are called “security cameras”).
Researchers report that Sony has already released firmware updates for vulnerable cameras. However, you need to understand that these updates will reach the goal soon - after all, webcams, like many other gadgets of the “Internet of Things”, are not equipped with user-friendly interfaces, and the culture of online updating of such devices has not yet developed.
According to Gartner, by 2020 the number of IoT devices will reach 20 billion, which means that there will be even more objects for massive attacks.
You can learn more about how the security of the Internet of Things should be organized at all stages of its creation and use at the free webinar of Anton Tyurin, head of the Positive Technologies attack detection methods development team. A webinar titled “ How to Leave an IoT Hacker Without Work ” will be held on December 15 at 2 pm on the company's website. You need to register in advance .
PS We remind you that very soon, with the support of Positive Technologies, a course on asyncio + aiohttp from Python core developer Andrei Svetlov will be held in Moscow .
We want to offer one free ticket to the seminar to the author of the best question for Andrey - he will choose the question and answer it during the lesson. Send your questions to asyncio2016@ptsecurity.com .
