About quantum cryptography. Protocols E91 & Lo05
Good time of day As promised in the first article , I’ll talk about the E91 and Lo05 protocols.
This protocol was developed by Arthur Eckert in 1991. It also has the name EPR (Einstein-Podolsky-Rosen) since it is based on the Einstein-Podolsky-Rosen paradox .
The protocol proposes to use, for example, pairs of photons generated in antisymmetric polarization states. Interception of one of the pair’s photons does not bring Eve any information, but for Alice and Bob it is a signal that their conversation is being tapped.
The EPR effect occurs when a spherically symmetric atom emits two photons in opposite directions towards two observers. Photons are emitted with an indefinite polarization, but due to the symmetry of their polarization, they are always opposite. An important feature of this effect is that the polarization of photons becomes known only after measurement. Based on EPR, Eckert also proposed a protocol that guarantees the security of the transmission and storage of the key. The sender generates a number of EPR photon pairs. He leaves one photon from each pair for himself, the second sends to his partner. Moreover, if the registration efficiency is close to unity, when the sender receives a polarization value of 1, his partner will register a value of 0 and vice versa. It’s clear that in this way partners, whenever required,
First, let N create the most confusing EPR-pairs of photons, then one photon from each pair is sent to Alice, and the other to Bob. Three possible quantum states for these EPR pairs are

It can be written in general form as
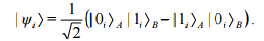
The last formula clearly shows that each of these three states encodes bits "0" and "1" in a unique basis. Then Alice and Bob take measurements on their parts of the separated EPR pairs using appropriate projectors.
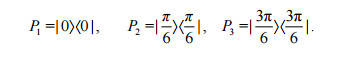
For each bit, Alice and Bob randomly choose a basis for measuring a particle, as in the case of BB84 they discuss what methods they used to measure particles in an open channel:
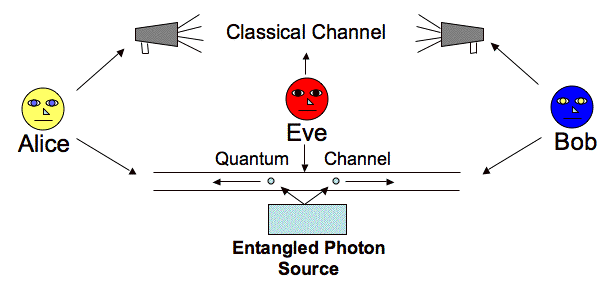
Thanks to the principles of quantum entanglement, using the same basis, Alice and Bob opposite results should be expected, if roughly, this means that in order to get the key one of them must invert its result. For other results, Alice and Bob test Bell's inequality as a test for Eve's presence.
Lo05 is a quantum cryptographic key distribution protocol created by scientists H. H.-K. Ma K. and Chen K.
Quantum Key Distribution (QKD) allows two users, Alice and Bob, to communicate in absolute security in the presence of an interceptor, Eve.
Unfortunately, all these exciting recent experiments are, in principle, unsafe due to the imperfection of real life. More specifically, highly attenuated lasers are often used as sources. But sources sometimes produce signals that contain more than one photon. These multi-photon signals open the door to a world of powerful new attacks, including attacks aimed at splitting multi-photons. For example, Eve can, in principle, measure the number of photons of each signal emitted by Alice and selectively suppress single-photon signals. She breaks down multiphoton signals, keeping one copy for herself and sending one copy to Bob. Now, since Eve has an identical copy of what Bob has. And as a result, the unconditional security of QKD (in, for example, the BB84 protocol) is completely violated.
Therefore, in 2005, a group of Laws proposed a protocol that circumvents such shortcomings of existing protocols. The idea behind this protocol is based on “trap states”. That is, quantum states that are used only to determine the presence of an eavesdropper in a communication channel.
As stated by the creators themselves, the method has an advantage over the others as it can be safely implemented on the basis of current hardware. The basic idea is that Alice is preparing a set of additional “states - baits”, in addition to the standard states used in BB84. Baits are used only for the purpose of detecting eavesdropping, while standard BB84 states are used to generate keys. The main difference between them is the intensity.
Let's imagine that, with a bait, the state and state of the signal have the same characteristics (wavelength, synchronization information, etc.). Thus, Eve cannot distinguish between the state of the bait and the signal state, and only part of the information available to Eva is the number of photons in the signal.
Assuming that the two detectors have equal chances, the error rate is 50%. If the signal has N ≥ 1 photons, it also has a certain frequency of velocity errors. That is, if we speak correctly, the error consists of two parts:
1. Detection error
2. Background contribution
But for the Lo05 protocol, this is not so. Alice and Bob have the ability to isolate single-photon signals, plus using bait signals, you can transfer data over a distance of more than 140 km. The protocol is also resistant to small velocity perturbations, which ideally eliminates background errors. Among other things, the speed of key generation has been increased several times, to be more precise, the creators are talking about an increase of 5 times. Thus, as they say, "using the best of both worlds," the authors were able to achieve not only an increase in distance, but also an increase in safety not only at small, but also at relatively large distances.
PSAnd by the way about “BUT”, which I promised to say in spite of my seemingly ideal, the algorithm is very difficult to implement and a lot of cost due to the fact that the basic principles of its operation are connected with direct current.
PSS When describing the Lo05 algorithm, I intentionally did not load the description with equations, otherwise I would just have to rewrite the whole article. Which by the way, if you wish, you can take a link here .
E91
A bit of territory ...
This protocol was developed by Arthur Eckert in 1991. It also has the name EPR (Einstein-Podolsky-Rosen) since it is based on the Einstein-Podolsky-Rosen paradox .
The protocol proposes to use, for example, pairs of photons generated in antisymmetric polarization states. Interception of one of the pair’s photons does not bring Eve any information, but for Alice and Bob it is a signal that their conversation is being tapped.
The EPR effect occurs when a spherically symmetric atom emits two photons in opposite directions towards two observers. Photons are emitted with an indefinite polarization, but due to the symmetry of their polarization, they are always opposite. An important feature of this effect is that the polarization of photons becomes known only after measurement. Based on EPR, Eckert also proposed a protocol that guarantees the security of the transmission and storage of the key. The sender generates a number of EPR photon pairs. He leaves one photon from each pair for himself, the second sends to his partner. Moreover, if the registration efficiency is close to unity, when the sender receives a polarization value of 1, his partner will register a value of 0 and vice versa. It’s clear that in this way partners, whenever required,
First, let N create the most confusing EPR-pairs of photons, then one photon from each pair is sent to Alice, and the other to Bob. Three possible quantum states for these EPR pairs are

It can be written in general form as
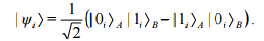
The last formula clearly shows that each of these three states encodes bits "0" and "1" in a unique basis. Then Alice and Bob take measurements on their parts of the separated EPR pairs using appropriate projectors.
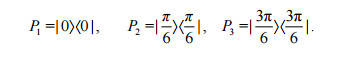
And now, in a simple way ...
For each bit, Alice and Bob randomly choose a basis for measuring a particle, as in the case of BB84 they discuss what methods they used to measure particles in an open channel:

Thanks to the principles of quantum entanglement, using the same basis, Alice and Bob opposite results should be expected, if roughly, this means that in order to get the key one of them must invert its result. For other results, Alice and Bob test Bell's inequality as a test for Eve's presence.
Lo05
Lo05 is a quantum cryptographic key distribution protocol created by scientists H. H.-K. Ma K. and Chen K.
Quantum Key Distribution (QKD) allows two users, Alice and Bob, to communicate in absolute security in the presence of an interceptor, Eve.
Unfortunately, all these exciting recent experiments are, in principle, unsafe due to the imperfection of real life. More specifically, highly attenuated lasers are often used as sources. But sources sometimes produce signals that contain more than one photon. These multi-photon signals open the door to a world of powerful new attacks, including attacks aimed at splitting multi-photons. For example, Eve can, in principle, measure the number of photons of each signal emitted by Alice and selectively suppress single-photon signals. She breaks down multiphoton signals, keeping one copy for herself and sending one copy to Bob. Now, since Eve has an identical copy of what Bob has. And as a result, the unconditional security of QKD (in, for example, the BB84 protocol) is completely violated.
Therefore, in 2005, a group of Laws proposed a protocol that circumvents such shortcomings of existing protocols. The idea behind this protocol is based on “trap states”. That is, quantum states that are used only to determine the presence of an eavesdropper in a communication channel.
As stated by the creators themselves, the method has an advantage over the others as it can be safely implemented on the basis of current hardware. The basic idea is that Alice is preparing a set of additional “states - baits”, in addition to the standard states used in BB84. Baits are used only for the purpose of detecting eavesdropping, while standard BB84 states are used to generate keys. The main difference between them is the intensity.
Let's imagine that, with a bait, the state and state of the signal have the same characteristics (wavelength, synchronization information, etc.). Thus, Eve cannot distinguish between the state of the bait and the signal state, and only part of the information available to Eva is the number of photons in the signal.
Assuming that the two detectors have equal chances, the error rate is 50%. If the signal has N ≥ 1 photons, it also has a certain frequency of velocity errors. That is, if we speak correctly, the error consists of two parts:
1. Detection error
2. Background contribution
But for the Lo05 protocol, this is not so. Alice and Bob have the ability to isolate single-photon signals, plus using bait signals, you can transfer data over a distance of more than 140 km. The protocol is also resistant to small velocity perturbations, which ideally eliminates background errors. Among other things, the speed of key generation has been increased several times, to be more precise, the creators are talking about an increase of 5 times. Thus, as they say, "using the best of both worlds," the authors were able to achieve not only an increase in distance, but also an increase in safety not only at small, but also at relatively large distances.
PSAnd by the way about “BUT”, which I promised to say in spite of my seemingly ideal, the algorithm is very difficult to implement and a lot of cost due to the fact that the basic principles of its operation are connected with direct current.
PSS When describing the Lo05 algorithm, I intentionally did not load the description with equations, otherwise I would just have to rewrite the whole article. Which by the way, if you wish, you can take a link here .
