Security Study of Parking Payment Systems
In this article I want to talk about the security of automated parking payment systems. Approximately such as in this picture.

At the entrance is issued a parking ticket, when leaving, he sticks back to the terminal. Basically, coupons are of two types: paper with a bar code / QR code and plastic contactless cards, the latter will be discussed.
As usual, I immediately want to make a reservation that all information is presented solely for informational purposes and does not carry the purpose of sponsoring terrorism and establishing world domination.
Once, using the parking of one metropolitan shopping center, I, inspired by articles about Troika and Plantain , as well as out of pure curiosity, launched the MifareClassicTool application on my NFC-enabled phoneand tried to read the contents of the card. It would be logical to assume that the verification of the fact of payment is carried out online, and the card is used only as a user ID. In this case, there would be nothing to do without access to the internal network, and this article simply would not exist, but the reality turned out to be more interesting. Something like this appeared to my eyes:
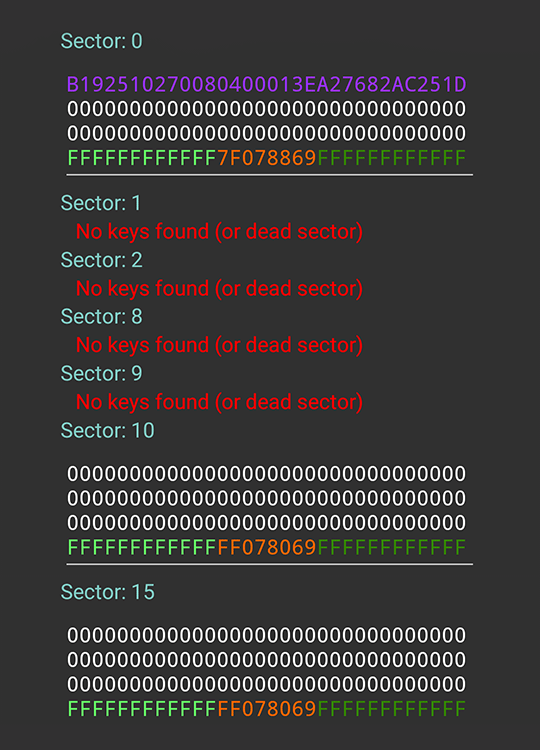
Screenshot slightly shortened for the convenience of readers. The map is a Mifare Classic 1K, divided into 16 sectors. In sectors 1-9 recorded some information and the keys to them are unknown. The rest are empty and use the default keys. Really curious. Fortunately for us, the crypto1 proprietary encryption protocol used in these cards is well understood and has vulnerabilities.
We need a laptop, contactless card reader type ACR122U and the application mfocwhich allows having only one key from any sector in a reasonable time to restore all the others. We will skip the assembly step and adjust this good, let's get straight to the point. Put the card on the reader, run the program, leave the laptop in the car and go shopping, because for this we came here. An hour passed, all the keys were restored, try to read the card again.

It became even more curious, but so far it is not very clear what is written here. We leave the parking lot and immediately check in again. We already have the keys and you can immediately go over the comparison of dumps.
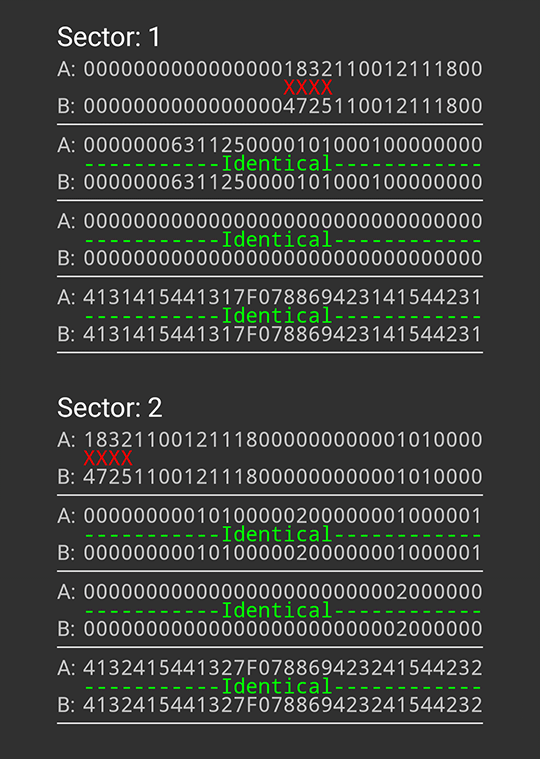
There are not many differences, but what do they look like? Yes, this is the time of entry into the BCD format, 11:25:47. Next to it is the date 12/12/2018. We change the date for a few days ago, go to the payment terminal and he happily reports that we owe him a lot of money. We change the date back, set the current time and leave the parking for free.
In principle, this could be stopped, but the love of research overpowers laziness, we go to another shopping center and repeat the operation there. The keys are different, but the data format is similar. Having visited several shopping centers and one station and having made several experiments it becomes clear what's what. In the first sector, the validity period of the card is stored, in our example this is until 12/31/2050. In the second - the time of entry, the time and amount of payment, the time until which exit is allowed. The blocks of the third and subsequent sectors should be read as 4 numbers in little-endian. Let's try to decrypt the data in our example.
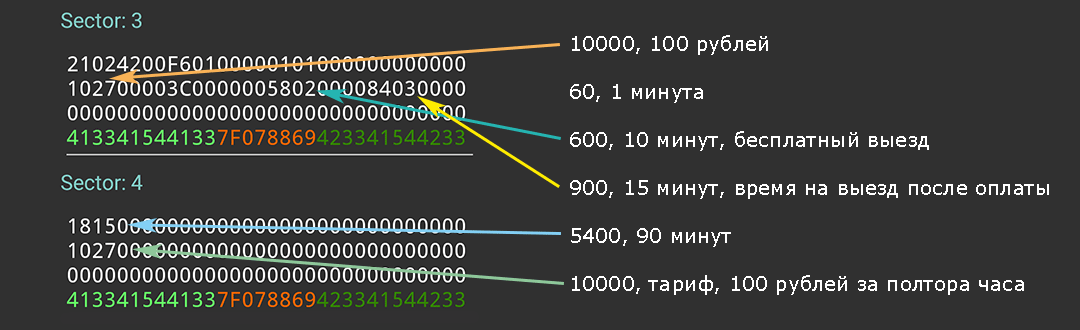
The blocks with the description of tariffs differ between parking lots, the first block of sector 3 is used as a heading, but its format remained unknown, it was not possible to find documentation in open access, and this is not so important anymore.
Probably, it is necessary to draw some conclusions. System developers could use online verification, could use Desfire / Ultralight C card types that do not have known vulnerabilities, but relied on the security of outdated technology. On the other hand, this is not a bank card and the loss here is not significant, although the taxi drivers at the station will be happy.

At the entrance is issued a parking ticket, when leaving, he sticks back to the terminal. Basically, coupons are of two types: paper with a bar code / QR code and plastic contactless cards, the latter will be discussed.
As usual, I immediately want to make a reservation that all information is presented solely for informational purposes and does not carry the purpose of sponsoring terrorism and establishing world domination.
Once, using the parking of one metropolitan shopping center, I, inspired by articles about Troika and Plantain , as well as out of pure curiosity, launched the MifareClassicTool application on my NFC-enabled phoneand tried to read the contents of the card. It would be logical to assume that the verification of the fact of payment is carried out online, and the card is used only as a user ID. In this case, there would be nothing to do without access to the internal network, and this article simply would not exist, but the reality turned out to be more interesting. Something like this appeared to my eyes:

Screenshot slightly shortened for the convenience of readers. The map is a Mifare Classic 1K, divided into 16 sectors. In sectors 1-9 recorded some information and the keys to them are unknown. The rest are empty and use the default keys. Really curious. Fortunately for us, the crypto1 proprietary encryption protocol used in these cards is well understood and has vulnerabilities.
We need a laptop, contactless card reader type ACR122U and the application mfocwhich allows having only one key from any sector in a reasonable time to restore all the others. We will skip the assembly step and adjust this good, let's get straight to the point. Put the card on the reader, run the program, leave the laptop in the car and go shopping, because for this we came here. An hour passed, all the keys were restored, try to read the card again.

It became even more curious, but so far it is not very clear what is written here. We leave the parking lot and immediately check in again. We already have the keys and you can immediately go over the comparison of dumps.

There are not many differences, but what do they look like? Yes, this is the time of entry into the BCD format, 11:25:47. Next to it is the date 12/12/2018. We change the date for a few days ago, go to the payment terminal and he happily reports that we owe him a lot of money. We change the date back, set the current time and leave the parking for free.
In principle, this could be stopped, but the love of research overpowers laziness, we go to another shopping center and repeat the operation there. The keys are different, but the data format is similar. Having visited several shopping centers and one station and having made several experiments it becomes clear what's what. In the first sector, the validity period of the card is stored, in our example this is until 12/31/2050. In the second - the time of entry, the time and amount of payment, the time until which exit is allowed. The blocks of the third and subsequent sectors should be read as 4 numbers in little-endian. Let's try to decrypt the data in our example.

The blocks with the description of tariffs differ between parking lots, the first block of sector 3 is used as a heading, but its format remained unknown, it was not possible to find documentation in open access, and this is not so important anymore.
Probably, it is necessary to draw some conclusions. System developers could use online verification, could use Desfire / Ultralight C card types that do not have known vulnerabilities, but relied on the security of outdated technology. On the other hand, this is not a bank card and the loss here is not significant, although the taxi drivers at the station will be happy.
