The network published a database of 98 million Rambler accounts
The leakedsource.com resource, which specializes in information security, got an account database from the Rambler.ru service, which was stolen by cybercriminals back in 2012. It was provided by user daykalif@xmpp.jp, who is also responsible for publishing the last.fm account database.
Each of the 98 167 935 accounts contains the user's login, his password and some more information. Separately, it is worth noting that passwords are not encrypted and are stored in plain text. The most popular passwords for the database were asdasd, asdasd123, and, of course, 123456.
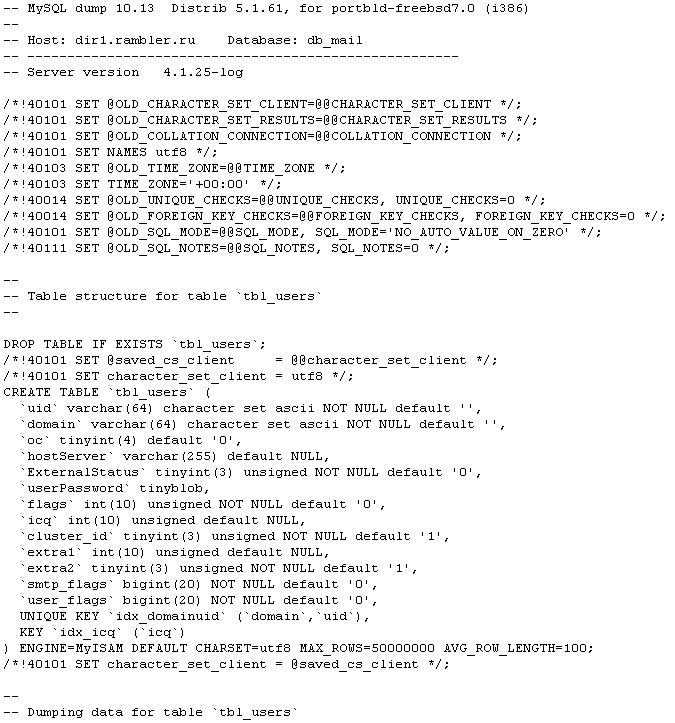
As one of the proofs, leakedsource gives a screenshot of the beginning of the base dump:
To one of the most well-known habrausers - Trin mobilz Zotoff, we asked the following questions about this hack:
- Why are such situations constantly repeated?
- Why were passwords stored in clear text?
- How relevant is the base?
- What do users do?
- For those with a password in the database, "Rambler" will offer to change the password?
I did not see the database itself, but I fully admit that the passwords were in the clear. This is a relic of the past, from which many services cannot get rid of until now. In particular, I admit that it was not the main base of rambler users that was obtained, but some kind of conditionally “neighboring”, which was used for some old projects. It may contain both irrelevant and incomplete user base.
Why is it repeated over and over again? It doesn’t matter whether the text or password hash is stored in the database, simple passwords like “123456” can be quickly recovered from hashes. As we can see from the article, out of 100 million users, at least 6 million have very simple passwords. And this is only the top50. I have a dictionary for cracking passwords into 2 gigs, a text file, I think that with it you can recover up to 90% of passwords, because people are not always serious about security. Even if the service hashes passwords, they can still be recovered a lot if they are relatively simple.
2-factor authorization from global hacks will definitely save. Even knowing the victim’s password, if authorization is also tied to the phone, then alas.
For rambler, as already mentioned, this is probably a relic of the past. Old services that do not want to be rewritten compared passwords with plain text. However, I have seen modern services who still manage to store passwords in clear text. Moreover, I came across projects, large projects, modern ones that stored hashes, but next to the table were passwords in clear text.
Why is this necessary? To know user passwords). Earlier, a very very long time, even knowing about the hashes for some of my projects, I allowed storing passwords in the clear. This was done for the UserFriendly interface. Type you ask to restore the password for mail and your current password immediately comes to your mail. Sometimes it’s more convenient, you don’t have to come up with a new one, restore, etc. But I was stupid, of course). Now only hashes, only with salt, etc.
It says February 2012. If you recall the history of yahoo with the restoration of mail for hijacking asek - this database can be relevant for a very long time. Let's say you used a box on rambler for a long time, but scored on it. The news about hacking didn’t bother you at all, you don’t use rambler. But rambler remembers all your correspondence, all your contacts, including business contacts, and this information can be used.
Who does not need boxes on rambler - delete everything to hell. Who needs to - change passwords and enable 2-factor authentication.
Typically, such services independently change passwords to users and inform them about it.
According to leakedsource.com, at least part of the database may be relevant, which was revealed during the audit with the participation of one of the journalists of the Hacker magazine.
