Linux Vulnerability Audit with Vulners.com
Vulners was conceived as a search engine for Security Content: vulnerabilities, security bulletins, exploits, plug-ins, detectors and other useful information. But we thought: if we already have parsed security bulletins for the main Linux distributions, why don’t we make a service that will take data about the system and give a list of vulnerabilities at the output. Also, as the usual vulnerability scanners do, only faster and free.
Where do we get information about Linux vulnerabilities? For this, we parse vendor bulletins. We show the parsing process using the Debian DSA-3638 security bulletin as an example.
Initial information on the vendor page:
https://security-tracker.debian.org/tracker/DSA-3638-1

We see that the source package curl is vulnerable on the operating system version jessie and the vulnerability is fixed in the package version 7.38.0-4 + deb8u4. But this information is not enough to correctly determine the vulnerability. curl in this case is a source package, that is, binary packages are collected on its basis. Therefore, you need to find all binary packages compiled from curl package:
packages.debian.org/source/jessie/curl

As a result, we believe that there is a vulnerability for all of the packages listed below version 7.38.0-4 + deb8u4
https://vulners.com/api/v3/search/id?id=DSA-3638
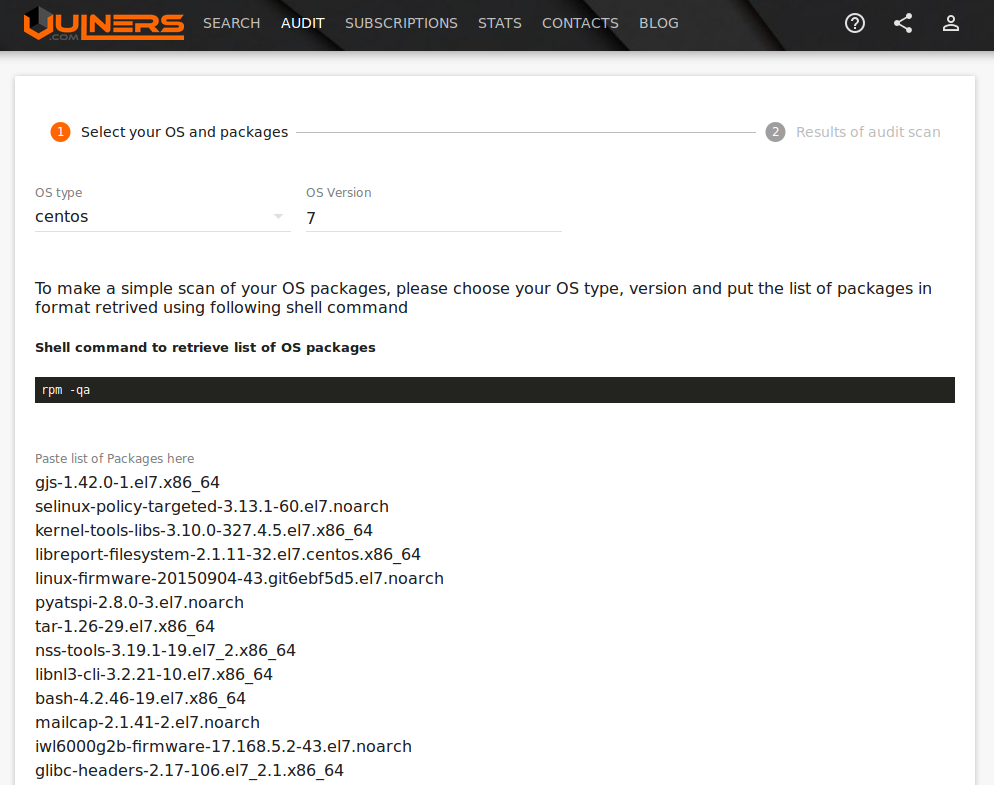
How does Audit work? First, we need to collect and send information about packages and OS to the server. The OS version is contained in the files / etc / os-release, / etc / centos-release and other files specific to particular operating systems. As a source of information about installed packages for rpm-based systems, the standard rpm -qa command is sufficient. In the case of a deb-based system, the output of the command is more complicated - dpkg-query -W -f = '$ {Package} $ {Version} $ {Architecture} \ n'
In response, the server will return us information about the vulnerabilities found. The calculation is very fast. We process 750 packages in 160ms! You might think that some kind of magic is happening on the server. But this is not so, everything is actually very simple, and so practically all vulnerability scanners work.
Consider the package - curl 7.38.0-4 + deb8u3 amd64 for Debian Linux. The package name is curl. We look in the system for all newsletters that contain this package among the list of vulnerable packages. After all such ballots have been found, you need to go through each of them and check whether at least one of the conditions listed in the affectedPackage field is met. Take the DSA-3638 package as an example:
It indicates that the vulnerability exists if:
- The operating system is Debian GNU / Linux (“OS”: “Debian GNU / Linux”)
- The version of this operating system is 8 (“OSVersion”: “8”)
- Installed a package named libcurl3-nss ("packageName": "libcurl3-nss")
- Architecture of the vulnerable package - any
- And the version of this package is less than 7.38.0-4 + deb8u4 ("operator": "lt" and "packageVersion ":" 7.38.0-4 + deb8u4 ")
If all the conditions are met, the package is subject to this vulnerability DSA-3638. For each package in the system, we check all conditions from the newsletters and get a list of vulnerabilities for the system. As you see, there is no difficulty or magic in this.
It is important to note that in no case can you compare versions as numbers or strings. For each of the systems (debian, redhat, solaris), the version structure is different. And accordingly, the mechanics of their comparison are different. In order to ensure the reliability of the scan, it is necessary to implement version comparison exactly according to the same algorithm as it is done in the operating system itself. Fortunately, there is no secret in this, there are ready-made examples of comparison functions for the same debian .
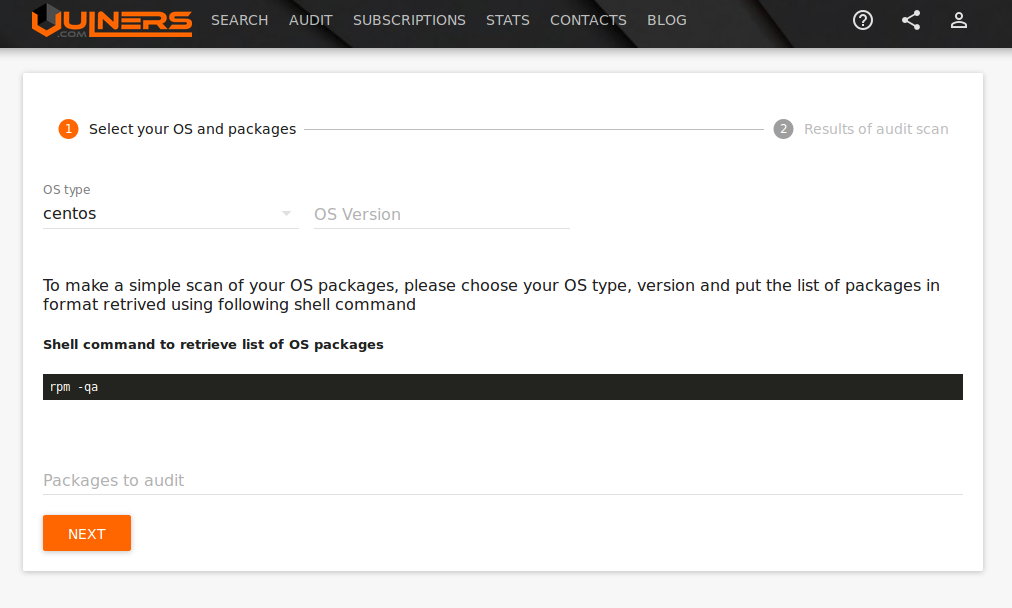
Today we are ready to offer you a web interface with which you can check your server for vulnerabilities, a full API for automation and PoC agentfor our future cloud vulnerability management solution. The following Linux distributions are supported: RedHat, CentOS, Fedora, Oracle Linux, Ubuntu, Debian.
The graphical interface is available on the Audit tab .
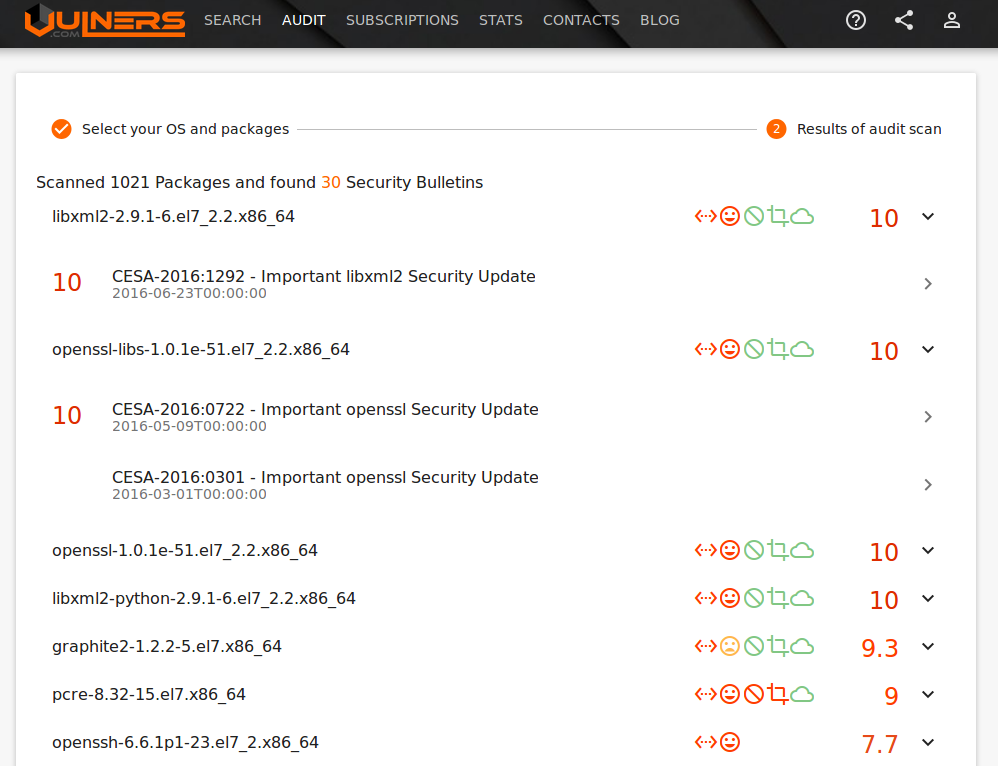
Vulnerabilities Found:
Similarly, it is possible to work through the Audit API. Specify the list of installed packages and the OS version, and in response you will receive a list of vulnerabilities and a description of why we believe that the vulnerability really exists. You can compare the results with the results of your scanner and ask your vendor to explain the discrepancies. Well, or kick us, that we messed up somewhere ;-)
And finally, the agent for the future cloud-based vulnerability management solution. We stand for the transparency of the work of all components; therefore, we have made the agent fully functional. It not only collects data from the system and sends it to the Vulners server for analysis and display, but also receives calculated lists of vulnerabilities from the server and displays them in the console. The agent solution was not chosen by chance. It gives the fastest and most reliable result if you solve the problems with automatic casting of agents once. No need to create any accounts, open network access for scanners and understand, calculate the parameters, and the time when the scan will not clog the channel, etc. At the moment, this is just a python script, but in the future there will be a full package for the system.
As you can see, Linux security analysis can be done more efficiently and faster and without expensive vulnerability scanners. We certainly recommend Vulners. But if you do not want to send anything to our server, for example, you are worried about privacy, you can implement this functionality yourself. This is not difficult to do. You will have to implement the comparison function, download the full set of data on the operating system, for example, the set for CentOS , and process your data as we showed above. You can see how to collect data in the source code of our agent. We have an open agent and we would be happy to develop it with you! Pull requests welcome! We are waiting for suggestions and wishes!

Where do we get information about Linux vulnerabilities? For this, we parse vendor bulletins. We show the parsing process using the Debian DSA-3638 security bulletin as an example.
Initial information on the vendor page:
https://security-tracker.debian.org/tracker/DSA-3638-1

We see that the source package curl is vulnerable on the operating system version jessie and the vulnerability is fixed in the package version 7.38.0-4 + deb8u4. But this information is not enough to correctly determine the vulnerability. curl in this case is a source package, that is, binary packages are collected on its basis. Therefore, you need to find all binary packages compiled from curl package:
packages.debian.org/source/jessie/curl

As a result, we believe that there is a vulnerability for all of the packages listed below version 7.38.0-4 + deb8u4
https://vulners.com/api/v3/search/id?id=DSA-3638
{
"result": "OK",
"data": {
"documents": {
"DSA-3638": {
"objectVersion": "1.0",
"modified": "2016-08-03T00:00:00",
"affectedPackage": [
{
"packageName": "libcurl3-nss",
"packageVersion": "7.38.0-4+deb8u4",
"packageFilename": "libcurl3-nss_7.38.0-4+deb8u4_all.deb",
"arch": "all",
"operator": "lt",
"OSVersion": "8",
"OS": "Debian GNU/Linux"
},
{
"packageName": "curl",
"packageVersion": "7.38.0-4+deb8u4",
"packageFilename": "curl_7.38.0-4+deb8u4_all.deb",
"arch": "all",
"operator": "lt",
"OSVersion": "8",
"OS": "Debian GNU/Linux"
...How does Audit work? First, we need to collect and send information about packages and OS to the server. The OS version is contained in the files / etc / os-release, / etc / centos-release and other files specific to particular operating systems. As a source of information about installed packages for rpm-based systems, the standard rpm -qa command is sufficient. In the case of a deb-based system, the output of the command is more complicated - dpkg-query -W -f = '$ {Package} $ {Version} $ {Architecture} \ n'
In response, the server will return us information about the vulnerabilities found. The calculation is very fast. We process 750 packages in 160ms! You might think that some kind of magic is happening on the server. But this is not so, everything is actually very simple, and so practically all vulnerability scanners work.
Consider the package - curl 7.38.0-4 + deb8u3 amd64 for Debian Linux. The package name is curl. We look in the system for all newsletters that contain this package among the list of vulnerable packages. After all such ballots have been found, you need to go through each of them and check whether at least one of the conditions listed in the affectedPackage field is met. Take the DSA-3638 package as an example:
{
"OS": "Debian GNU/Linux",
"operator": "lt",
"packageFilename": "libcurl3-nss_7.38.0-4+deb8u4_all.deb",
"OSVersion": "8",
"packageVersion": "7.38.0-4+deb8u4",
"packageName": "libcurl3-nss",
"arch": "all"
}It indicates that the vulnerability exists if:
- The operating system is Debian GNU / Linux (“OS”: “Debian GNU / Linux”)
- The version of this operating system is 8 (“OSVersion”: “8”)
- Installed a package named libcurl3-nss ("packageName": "libcurl3-nss")
- Architecture of the vulnerable package - any
- And the version of this package is less than 7.38.0-4 + deb8u4 ("operator": "lt" and "packageVersion ":" 7.38.0-4 + deb8u4 ")
If all the conditions are met, the package is subject to this vulnerability DSA-3638. For each package in the system, we check all conditions from the newsletters and get a list of vulnerabilities for the system. As you see, there is no difficulty or magic in this.
It is important to note that in no case can you compare versions as numbers or strings. For each of the systems (debian, redhat, solaris), the version structure is different. And accordingly, the mechanics of their comparison are different. In order to ensure the reliability of the scan, it is necessary to implement version comparison exactly according to the same algorithm as it is done in the operating system itself. Fortunately, there is no secret in this, there are ready-made examples of comparison functions for the same debian .
Today we are ready to offer you a web interface with which you can check your server for vulnerabilities, a full API for automation and PoC agentfor our future cloud vulnerability management solution. The following Linux distributions are supported: RedHat, CentOS, Fedora, Oracle Linux, Ubuntu, Debian.
The graphical interface is available on the Audit tab .

Vulnerabilities Found:

Similarly, it is possible to work through the Audit API. Specify the list of installed packages and the OS version, and in response you will receive a list of vulnerabilities and a description of why we believe that the vulnerability really exists. You can compare the results with the results of your scanner and ask your vendor to explain the discrepancies. Well, or kick us, that we messed up somewhere ;-)
curl -H"Accept: application/json" -H"Content-Type: application/json" -XPOST -d '{"os":"centos","package":["pcre-8.32-15.el7.x86_64", "samba-common-4.2.3-11.el7_2.noarch", "gnu-free-fonts-common-20120503-8.el7.noarch", "libreport-centos-2.1.11-32.el7.centos.x86_64", "libacl-2.2.51-12.el7.x86_64", "sos-3.2-35.el7.centos.noarch" ],"version":"7"}' https://vulners.com/api/v3/audit/audit/
{
"result": "OK",
"data": {
"reasons": [
{
"providedPackage": "sos-3.2-35.el7.centos.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0188",
"providedVersion": "0:3.2-35.el7.centos",
"bulletinPackage": "sos-3.2-35.el7.centos.3.noarch.rpm",
"bulletinVersion": "3.2-35.el7.centos.3",
"package": "sos-3.2-35.el7.centos.noarch"
},
{
"providedPackage": "pcre-8.32-15.el7.x86_64",
"operator": "lt",
"bulletinID": "CESA-2016:1025",
"providedVersion": "0:8.32-15.el7",
"bulletinPackage": "pcre-8.32-15.el7_2.1.x86_64.rpm",
"bulletinVersion": "8.32-15.el7_2.1",
"package": "pcre-8.32-15.el7.x86_64"
},
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:1486",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-7.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-7.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
},
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0612",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-6.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-6.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
},
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0448",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.3-12.el7_2.noarch.rpm",
"bulletinVersion": "4.2.3-12.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
],
"vulnerabilities": [
"CESA-2016:1486",
"CESA-2016:1025",
"CESA-2016:0448",
"CESA-2016:0612",
"CESA-2016:0188"
],
"cvelist": [
"CVE-2015-5370",
"CVE-2015-7560",
"CVE-2016-2119",
"CVE-2016-2118",
"CVE-2015-7529",
"CVE-2016-2112",
"CVE-2016-2113",
"CVE-2016-3191",
"CVE-2015-8386",
"CVE-2015-8388",
"CVE-2015-8385",
"CVE-2016-2110",
"CVE-2015-5073",
"CVE-2015-8391",
"CVE-2015-2328",
"CVE-2016-2115",
"CVE-2015-3217",
"CVE-2016-2114",
"CVE-2016-2111"
],
"cvss": {
"vector": "AV:NETWORK/AC:LOW/Au:NONE/C:PARTIAL/I:PARTIAL/A:COMPLETE/",
"score": 9.0
},
"packages": {
"pcre-8.32-15.el7.x86_64": {
"CESA-2016:1025": [
{
"providedPackage": "pcre-8.32-15.el7.x86_64",
"operator": "lt",
"bulletinID": "CESA-2016:1025",
"providedVersion": "0:8.32-15.el7",
"bulletinPackage": "pcre-8.32-15.el7_2.1.x86_64.rpm",
"bulletinVersion": "8.32-15.el7_2.1",
"package": "pcre-8.32-15.el7.x86_64"
}
]
},
"sos-3.2-35.el7.centos.noarch": {
"CESA-2016:0188": [
{
"providedPackage": "sos-3.2-35.el7.centos.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0188",
"providedVersion": "0:3.2-35.el7.centos",
"bulletinPackage": "sos-3.2-35.el7.centos.3.noarch.rpm",
"bulletinVersion": "3.2-35.el7.centos.3",
"package": "sos-3.2-35.el7.centos.noarch"
}
]
},
"samba-common-4.2.3-11.el7_2.noarch": {
"CESA-2016:1486": [
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:1486",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-7.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-7.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
],
"CESA-2016:0448": [
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0448",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.3-12.el7_2.noarch.rpm",
"bulletinVersion": "4.2.3-12.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
],
"CESA-2016:0612": [
{
"providedPackage": "samba-common-4.2.3-11.el7_2.noarch",
"operator": "lt",
"bulletinID": "CESA-2016:0612",
"providedVersion": "0:4.2.3-11.el7_2",
"bulletinPackage": "samba-common-4.2.10-6.el7_2.noarch.rpm",
"bulletinVersion": "4.2.10-6.el7_2",
"package": "samba-common-4.2.3-11.el7_2.noarch"
}
]
}
}
}
And finally, the agent for the future cloud-based vulnerability management solution. We stand for the transparency of the work of all components; therefore, we have made the agent fully functional. It not only collects data from the system and sends it to the Vulners server for analysis and display, but also receives calculated lists of vulnerabilities from the server and displays them in the console. The agent solution was not chosen by chance. It gives the fastest and most reliable result if you solve the problems with automatic casting of agents once. No need to create any accounts, open network access for scanners and understand, calculate the parameters, and the time when the scan will not clog the channel, etc. At the moment, this is just a python script, but in the future there will be a full package for the system.
$ git clone https://github.com/videns/vulners-scanner
$ cd vulners-scanner
$ ./linuxScanner.py
_
__ ___ _| |_ __ ___ _ __ ___
\ \ / / | | | | '_ \ / _ \ '__/ __|
\ V /| |_| | | | | | __/ | \__ \
\_/ \__,_|_|_| |_|\___|_| |___/
==========================================
Host info - Host machine
OS Name - centos, OS Version - 7
Total found packages: 1026
Vulnerable packages:
krb5-libs-1.13.2-10.el7.x86_64
CESA-2016:0532 - 'Moderate krb5 Security Update', cvss.score - 6.8
openssh-server-6.6.1p1-23.el7_2.x86_64
CESA-2016:0465 - 'Moderate openssh SecurityUpdate', cvss.score - 7.7
libtdb-1.3.6-2.el7.x86_64
CESA-2016:0612 - 'Critical ipa SecurityUpdate', cvss.score - 0.0
kernel-tools-3.10.0-327.4.5.el7.x86_64
CESA-2016:1033 - 'Important kernel SecurityUpdate', cvss.score - 0.0
CESA-2016:1633 - 'Important kernel SecurityUpdate', cvss.score - 4.3
CESA-2016:0185 - 'Important kernel SecurityUpdate', cvss.score - 7.2
CESA-2016:1539 - 'Important kernel SecurityUpdate', cvss.score - 7.2
CESA-2016:1277 - 'Important kernel SecurityUpdate', cvss.score - 7.2
openssl-libs-1.0.1e-51.el7_2.2.x86_64
CESA-2016:0301 - 'Important openssl SecurityUpdate', cvss.score - 0.0
CESA-2016:0722 - 'Important openssl SecurityUpdate', cvss.score - 10.0
nss-softokn-3.16.2.3-13.el7_1.x86_64
CESA-2016:0685 - 'Moderate nss-softokn SecurityUpdate', cvss.score - 6.8
...
As you can see, Linux security analysis can be done more efficiently and faster and without expensive vulnerability scanners. We certainly recommend Vulners. But if you do not want to send anything to our server, for example, you are worried about privacy, you can implement this functionality yourself. This is not difficult to do. You will have to implement the comparison function, download the full set of data on the operating system, for example, the set for CentOS , and process your data as we showed above. You can see how to collect data in the source code of our agent. We have an open agent and we would be happy to develop it with you! Pull requests welcome! We are waiting for suggestions and wishes!
