Malicious software used for cyber spying on users in Central and Eastern Europe
Last year, ESET specialists were able to detect and analyze several instances of the malware that were used in cyber espionage operations for users. This malware is called SBDH and uses powerful data filters, various methods of interaction with its operators, as well as an interesting technique to ensure its survival in the system. The malware was aimed at gaining government and government agencies computers that are interesting for attacking computers, which are mainly focused on economic growth and cooperation in Central and Eastern Europe. SBDH information will also be presented by ESET researchers Tomáš Gardoň and Robert Lipovský at the conferenceCopenhagen Cybercrime Conference 2016 in Copenhagen.

SBDH consists of a loader and other modules that are used by operators. A compact downloader was distributed by cybercriminals using phishing emails. Such messages contained an attachment, which contained a file with a double extension in the title. Since Windows hides the extension of known files, a false extension was displayed to the user, which was what the attackers expected. In order to further convince the potential victim of their legitimacy, the icons for standard Microsoft applications or Word documents were selected for executable files.
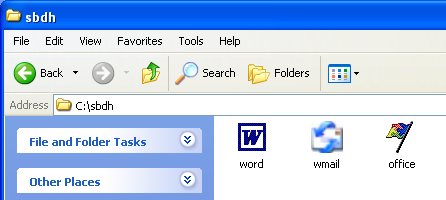
Fig. Attackers disguise the bootloader executable file as legitimate Microsoft applications.
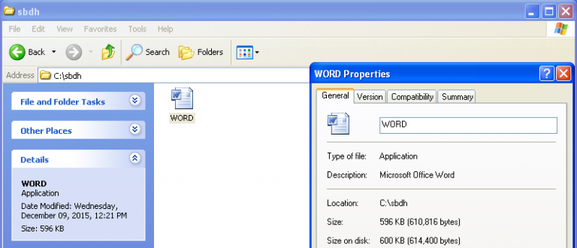
Fig. Attackers disguise the bootloader executable as a Word document.
After successful execution in the system, the malicious program contacts the remote server to load two of its main components into the system: a backdoor and a data thief. The combination of these modules allows the attacker not only to gain full control over the compromised computer, but also provides him with advanced methods of stealing data from him. Thanks to the powerful filter system, the operator can specify in great detail which particular data should be stolen. The filter includes information about the file extension, its creation date, its size and other characteristics. The filter service data can be modified using malware configuration files.
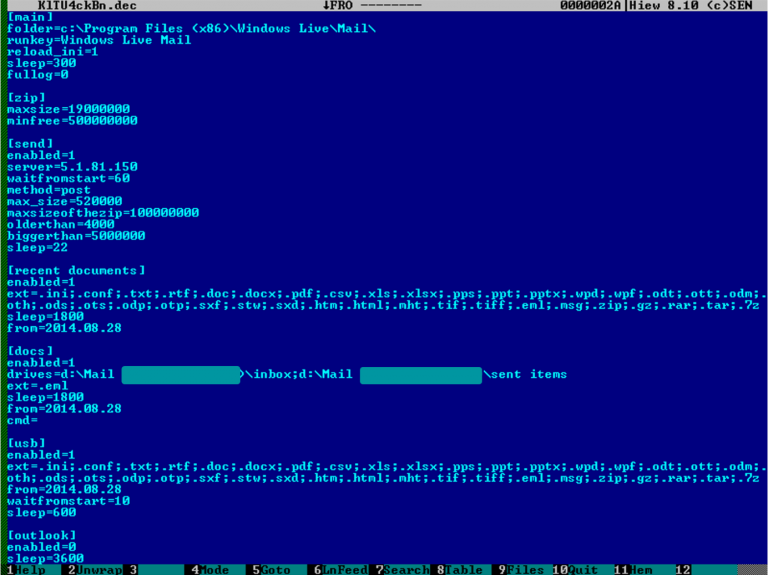
Fig. Malware configuration file.
Since all the components of this cybercriminal tool require connection to a controlling C&C server, the operation of SBDH largely depends on the ability to work with a network connection. To do this, the authors implemented several methods of interaction in the C & C server in SBDH. The first is to use a simple HTTP protocol. If it is unavailable, the malicious program tries to use the SMTP protocol and a free external gateway to send letters. The latter method consists in the possibility of using the Microsoft Outlook Express application and sending through it specially formed electronic messages. Such emails are sent under the current user account, allowing the malware to bypass security restrictions (it’s assumed that the current user has the right to send and receive emails). Messages sent by the malware are then placed in the outgoing mail directory in order to prevent them from showing increased attention.
To detect incoming connections, i.e., attempts by operators to contact the bot, the malicious program searches for emails in the user's mailbox. Such malicious emails have a specific subject name. If SBDH detects such letters, they are parsed in order to extract sent operator commands from there. After this operation, the bot modifies the subject field in the electronic message so that it does not attract his attention in the future. However, this last feature was used by SBDH authors until 2006, when Outlook Express was replaced by another new application called Windows Mail. After that, the authors focused more on improving the method of interacting with C &
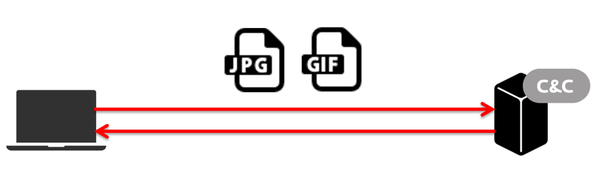
Fig. Disguise the process of interaction with the management server.
If the managing C&C server is unavailable, the backdoor component will resort to using a hard-wired URL that contains a fake image file (located on a free resource), which, in turn, contains the address of an alternative C&C server.
Fig. A picture with the URL of an alternate C&C server.
Some of the SBDH samples we analyzed contained an interesting implementation of the method for ensuring their survival in the system. The malicious program modified the Word document processor used by the system in such a way that when trying to open or edit the Word file in Windows Explorer, the malicious program code was executed.
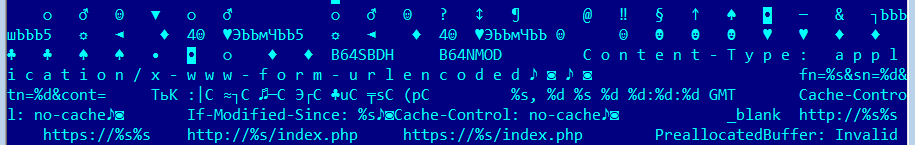
Fig. The identifier of B64SBDH in the body of the malware.
It should be noted that the name SBDH itself is a sequence of characters that was part of the compilation path in the bootloader file. Another interesting feature is the fact that the “B64SBDH” line, which works as a trigger, is used to download the other two components of the malicious program from the C&C server.
Conclusion
Cybercriminals behind SBDH use the same methods as those behind Buhtrap operations. This spy tool proves the fact that even modern threats are spread using simple methods such as email attachments. Nevertheless, the risks of compromising such malware in organizations can be significantly reduced by instructing employees and using a reliable solution of a multi-level security system.
IDs of malware samples SBDH (hashes):
1345b6189441cd1ed9036ef098adf12746ecf7cb
15b956feee0fa42f89c67ca568a182c348e20ead
f2a1e4b58c9449776bd69f62a8f2ba7a72580da2
7f32cae8d6821fd50de571c40a8342acaf858541
5DDBDD3CF632F7325D6C261BCC516627D772381A
4B94E8A10C5BCA43797283ECD24DF24421E411D2
D2E9EB26F3212D96E341E4CBA7483EF46DF8A1BE
09C56B14DB3785033C8FDEC41F7EA9497350EDAE

SBDH consists of a loader and other modules that are used by operators. A compact downloader was distributed by cybercriminals using phishing emails. Such messages contained an attachment, which contained a file with a double extension in the title. Since Windows hides the extension of known files, a false extension was displayed to the user, which was what the attackers expected. In order to further convince the potential victim of their legitimacy, the icons for standard Microsoft applications or Word documents were selected for executable files.

Fig. Attackers disguise the bootloader executable file as legitimate Microsoft applications.

Fig. Attackers disguise the bootloader executable as a Word document.
After successful execution in the system, the malicious program contacts the remote server to load two of its main components into the system: a backdoor and a data thief. The combination of these modules allows the attacker not only to gain full control over the compromised computer, but also provides him with advanced methods of stealing data from him. Thanks to the powerful filter system, the operator can specify in great detail which particular data should be stolen. The filter includes information about the file extension, its creation date, its size and other characteristics. The filter service data can be modified using malware configuration files.

Fig. Malware configuration file.
Since all the components of this cybercriminal tool require connection to a controlling C&C server, the operation of SBDH largely depends on the ability to work with a network connection. To do this, the authors implemented several methods of interaction in the C & C server in SBDH. The first is to use a simple HTTP protocol. If it is unavailable, the malicious program tries to use the SMTP protocol and a free external gateway to send letters. The latter method consists in the possibility of using the Microsoft Outlook Express application and sending through it specially formed electronic messages. Such emails are sent under the current user account, allowing the malware to bypass security restrictions (it’s assumed that the current user has the right to send and receive emails). Messages sent by the malware are then placed in the outgoing mail directory in order to prevent them from showing increased attention.
To detect incoming connections, i.e., attempts by operators to contact the bot, the malicious program searches for emails in the user's mailbox. Such malicious emails have a specific subject name. If SBDH detects such letters, they are parsed in order to extract sent operator commands from there. After this operation, the bot modifies the subject field in the electronic message so that it does not attract his attention in the future. However, this last feature was used by SBDH authors until 2006, when Outlook Express was replaced by another new application called Windows Mail. After that, the authors focused more on improving the method of interacting with C &

Fig. Disguise the process of interaction with the management server.
If the managing C&C server is unavailable, the backdoor component will resort to using a hard-wired URL that contains a fake image file (located on a free resource), which, in turn, contains the address of an alternative C&C server.

Fig. A picture with the URL of an alternate C&C server.
Some of the SBDH samples we analyzed contained an interesting implementation of the method for ensuring their survival in the system. The malicious program modified the Word document processor used by the system in such a way that when trying to open or edit the Word file in Windows Explorer, the malicious program code was executed.

Fig. The identifier of B64SBDH in the body of the malware.
It should be noted that the name SBDH itself is a sequence of characters that was part of the compilation path in the bootloader file. Another interesting feature is the fact that the “B64SBDH” line, which works as a trigger, is used to download the other two components of the malicious program from the C&C server.
Conclusion
Cybercriminals behind SBDH use the same methods as those behind Buhtrap operations. This spy tool proves the fact that even modern threats are spread using simple methods such as email attachments. Nevertheless, the risks of compromising such malware in organizations can be significantly reduced by instructing employees and using a reliable solution of a multi-level security system.
IDs of malware samples SBDH (hashes):
1345b6189441cd1ed9036ef098adf12746ecf7cb
15b956feee0fa42f89c67ca568a182c348e20ead
f2a1e4b58c9449776bd69f62a8f2ba7a72580da2
7f32cae8d6821fd50de571c40a8342acaf858541
5DDBDD3CF632F7325D6C261BCC516627D772381A
4B94E8A10C5BCA43797283ECD24DF24421E411D2
D2E9EB26F3212D96E341E4CBA7483EF46DF8A1BE
09C56B14DB3785033C8FDEC41F7EA9497350EDAE
