The battle for the client or how to find a spammer
Three and a half weeks ago (September 24), one of our clients called our office and asked in an excited voice: “Is it true that you are closing? And only yesterday I replenished the balance in the system. What will happen to my money? ”
A slight tremor ran through the manager, because he also did not plan to remain without work, but after a short pause he managed to pull himself together and find out what happened. About how to find a distributor of false information (hereinafter referred to as “spammer”, because in our case there was a spam mailing of phishing emails) about your company on the Internet and how to respond if someone starts to threaten you and your customers, read on.

On September 24, the customers of LLC Call will receive a letter stating that the company will Call is closed, we suggest you become a client of the LPTracker service. It was understood that the client who read this letter would take it as a notification from the company itself, therefore a mailbox similar in sound to pozvonim@inbox.ru was created for mail.ru
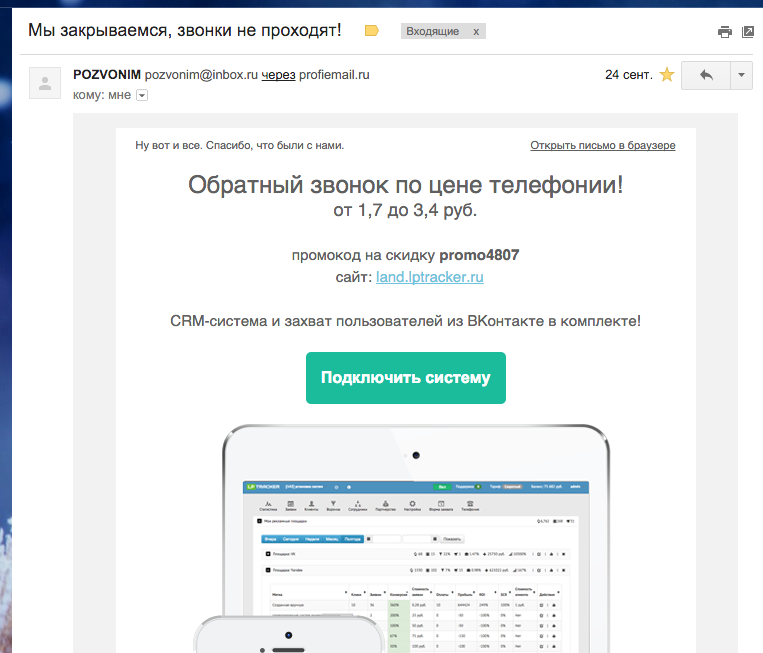
Fig. 1 Screenshot of a spam email sent to pozvonim.com customers
Expectations senders were justified, indeed, many received this letter, calls from customers rained down into the office.
Our representative contacted the company indicated in the mailing list, spoke about the distribution of false information by their partner, about spamming and asked to block the link. Soon, the link was blocked, but after 5 minutes it was made active again. Our phone numbers were blacklisted, letters and calls via other communication channels were no longer answered.
Time passed, the company completely abstracted from us while continuing to collect transitions.
Realizing that the competing company does not plan to engage in a constructive dialogue and block spammers, we wrote an article about this incident and posted it on thematic resources, primarily on the megamind. The main goal was to block the link, but it continued to be active. And with it appeared activity and our spammer.
On one of the resources where the article was also posted, he starts an account and begins to threaten us with new spam mailings if we do not delete the article, which in his opinion damages the reputation of LPTracker (hereinafter LP). In the same place, in the comments, he admits that it was the distribution, and not the sending of several letters, that was committed.

Fig. 2. A deleted comment in which a spammer tries to prove that the company tracker is not connected with him, and if we do not believe this, he will bring down new mailings on us.
For unknown reasons, the news resource deleted these comments, but we still have screenshots.
Lesson 1: Save all evidence at once, and not after a while. After a while, they may no longer be there, and only you alone will know the truth.
In parallel, threats went through the e-mail, so we set ourselves the task of exploring every pixel in a provocative letter, but to find the one who sent it and continues the threat.
Fortunately, this was not required.
Read carefully the letter that started it all.
It was:

Fig. 3. Excerpt from the letter with the identifier of the partner spammer
This promo4807 promo code is used to identify by the LP company where the client came from and from which partner (if the partner recommended them). Let’s verify that google knows about this affiliate ID.
Promo 4807 turned out to be very popular, it was posted on the official pages of LPtracker on behalf of. Representatives used in social. Networks, as a link to register for videos that the company regularly records and uploads to YouTube, etc. Below are a few screenshots where this is demonstrated:

fig. 4. Ivan Bochenkov, advertises the LP service under the partner identifier 4807. By the way, again, due to the name of the competing company,

fig. 5. The official representative of the lptracker company on the spark, when you click in detail you can see the same screenshot as in the mailing list and the same promo code 4807. And this is again Ivan

pic. 6 Detail, by clicking on the comment.
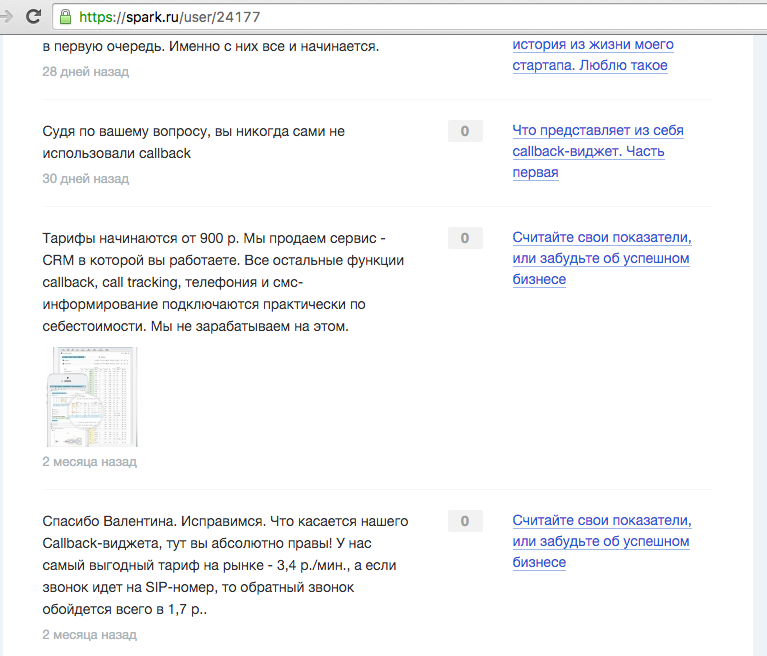
Fig. 7 Comments of Ivan on the sparks, as of. Representative of the company on the Internet. As you can see, it accepts user requests and writes on behalf of "We" - that is, the company.
In addition, in a phishing letter, Ivan also indicated: “Gookit.com - a service for publishing and sending commercial offers, announcements and articles” - this site is registered on Ivan Bochenkov.
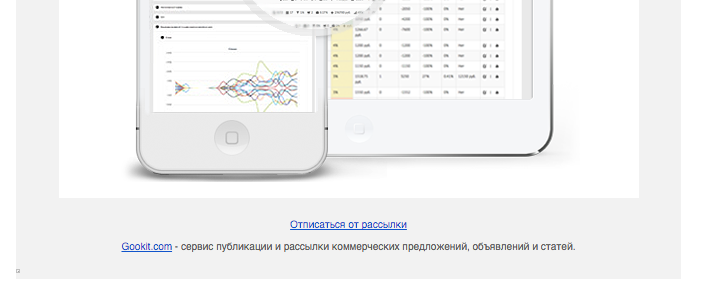
Fig. 8 excerpt from the letter

fig. 9. Issue in google when entering affiliate link 4807.
As we see, the same projects drop out of the same person.
Of course, the Internet allows you to maintain some anonymity, but when you already know the participants in the conspiracy, you can identify certain patterns.
The figure below shows two accounts on the information resource on which the spammer contacted us. The Alexandrovich account - the spammer account, which he himself admitted in the comments, and the Nicolas account ... - Ivan's account, were on the site at the same time. More precisely, the spammer first came in, corresponded with us, and a little later Ivan came in.

Fig. 10 Two accounts of Ivan
Continuation of the story:
Affiliate link 4807, through which spam clicks go active for the 3rd day, the LP company does not get in touch, has blocked all our contacts. We posted an article about this, which became very worrying for the “spammer” and he began to demand its removal, threatening with new mailings.
The question immediately arose: why should a spammer be so worried about the service and ask to delete those articles, in every possible way denying his involvement in the drug.
By the middle of the 3rd day the "spammer" began to sweep tracks. Promo code 4807 posted on the official pages of the company LP, in social. Networks, forums, YouTube, in the news and other sources changed to another.
This explained why the spam link was unlocked after 5 minutes. As soon as they blocked it, the LP company had to change the promo code in all official mentions of them on the Internet, because the old one stopped working. That is, having blocked the partner 4807, they blocked themselves.
As soon as the promo code was changed, the malicious link 4807 was blocked.
Lesson 2: Do not forget about lesson 1. Save all the evidence at once, take screenshots, videos.

Fig. 11 The LP company blocked the link, confirming the fact that they understood all this time about the violation of the rights of third parties.
But the article about the incident continued to bother the spammer and the PL.
The spammer even called us on a personal cell phone, the same number from which we tried to contact the PL when we saw the newsletter. Where did he get this number from? It is not used anywhere in open sources. Other PL employees began calling us on the same number with a demand to remove the article, then they made threatening calls ...
After some time, Ivan’s friend, Sergei Arsenichev, also decides to send letters to Ivan’s base, but about his LeadBack service.

Fig. 12 Chronology of events restored using information from open sources.
Lesson 3. If you have not responded and have forgiven an infringement of your rights, they will be infringed constantly. Do not hope that the situation does not happen again.
In the course of our mini investigation, we managed to find a lot of evidence of the involvement of the above-listed persons in the defamatory newsletter. There is no purpose to bring them all in this article, therefore we will not do this.
The certification of documents cost us about 60 thousand rubles. However, now we have not just screenshots, the authenticity of which can be questioned, but certified documents with which you can protect your rights.
The newsletter discredited us in the face of our customers, we received a lot of negativity and consequences, but it is difficult to calculate the material damage from this. In addition, by the time the company blocked the link, we had already paid for notary services and legal advice.
Litigation requires additional financial costs and lasts a long time, so always try to agree on compensation for your damage peacefully, you may be able to compensate for some of your losses. We also tried to do this and wrote a letter in LP. In our cases, a constructive dialogue did not work: the company wrote that they did not intend to protect the spammer (i.e., their official representative Ivan Bochenkov), it was his full responsibility and we should make all claims personally to him, while they would not specify who this was spammer.
And at this time, the spammer continues to defend the honor of the company, threatens us in correspondence by email, writes letters on our behalf to clients using profanity.
Most likely, your case with the newsletter is not the only one and the person who deals with such has already offended someone before you. Gather this information, people often write in open sources about such incidents. They will be able not only to characterize you as a person, in our case a “spammer”, but they also probably know his contact and other data.
Ivan Bochenkov was no exception, on the network we found freelancers whom he did not pay for work, threatened spam mailings on their contacts about what they were “losers”, insulted with obscene expressions, etc. In general, he did everything the same as our spammer did and does.
One of the freelancers lost his official job, as he decided to demand payment from Ivan for the work done. According to him, Ivan talked with his leader, and the next day the freelancer was fired without explanation.
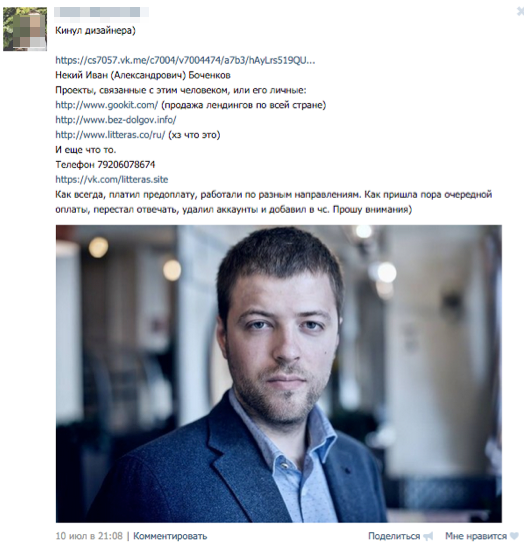
Fig. 13 Post in the social. Networks about deceiving a designer

Fig. 14. Review of Ivan in the list of customers who do not pay for orders
vk.com/photo-51016572_370984336
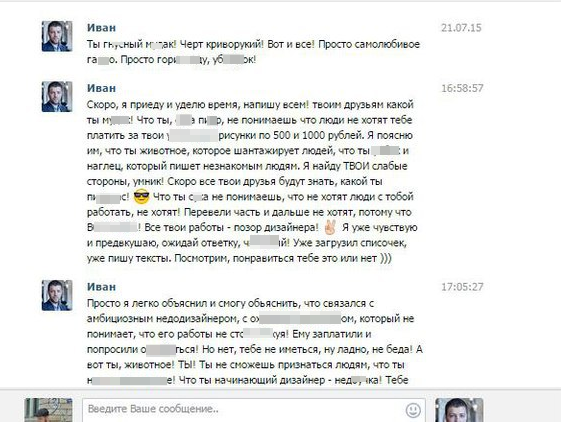
Fig. 15. The manner of communication of Ivan. An excerpt from correspondence with one of the freelancers whom Ivan did not pay, however, according to the freelancer himself, he used his work.
Each story of interactions with freelancers is a separate story that requires a separate investigation, but we can conclude for ourselves that if such stories happen, it’s not just that they give a person a certain characteristic by the very fact of their existence.
Step 6. Transfer the information you have to the competent authorities and write a statement
Now that you have collected all the information and facts about the incident, when you have feedback characterizing the participants, send all the data you have to the competent authorities. They will establish the possibility of fraudulent activity against you.
If this article was useful to you, then how to file an application, to which authorities and what happens next, we will write in the next part.
Lesson 4. As Warren Buffett said: “It takes 20 years to build a reputation and 5 minutes to destroy it” and do not trust the development of your project to dubious individuals.
Ps: While we were writing this news, Ivan became active again and now sends spam in the interests of Sipuni.com - but this is another story.
A slight tremor ran through the manager, because he also did not plan to remain without work, but after a short pause he managed to pull himself together and find out what happened. About how to find a distributor of false information (hereinafter referred to as “spammer”, because in our case there was a spam mailing of phishing emails) about your company on the Internet and how to respond if someone starts to threaten you and your customers, read on.

Beginning of the story:
On September 24, the customers of LLC Call will receive a letter stating that the company will Call is closed, we suggest you become a client of the LPTracker service. It was understood that the client who read this letter would take it as a notification from the company itself, therefore a mailbox similar in sound to pozvonim@inbox.ru was created for mail.ru

Fig. 1 Screenshot of a spam email sent to pozvonim.com customers
Expectations senders were justified, indeed, many received this letter, calls from customers rained down into the office.
Our representative contacted the company indicated in the mailing list, spoke about the distribution of false information by their partner, about spamming and asked to block the link. Soon, the link was blocked, but after 5 minutes it was made active again. Our phone numbers were blacklisted, letters and calls via other communication channels were no longer answered.
Time passed, the company completely abstracted from us while continuing to collect transitions.
Step 1. Write about the incident in the media
Realizing that the competing company does not plan to engage in a constructive dialogue and block spammers, we wrote an article about this incident and posted it on thematic resources, primarily on the megamind. The main goal was to block the link, but it continued to be active. And with it appeared activity and our spammer.
On one of the resources where the article was also posted, he starts an account and begins to threaten us with new spam mailings if we do not delete the article, which in his opinion damages the reputation of LPTracker (hereinafter LP). In the same place, in the comments, he admits that it was the distribution, and not the sending of several letters, that was committed.

Fig. 2. A deleted comment in which a spammer tries to prove that the company tracker is not connected with him, and if we do not believe this, he will bring down new mailings on us.
For unknown reasons, the news resource deleted these comments, but we still have screenshots.
Lesson 1: Save all evidence at once, and not after a while. After a while, they may no longer be there, and only you alone will know the truth.
In parallel, threats went through the e-mail, so we set ourselves the task of exploring every pixel in a provocative letter, but to find the one who sent it and continues the threat.
Fortunately, this was not required.
Step 2. Return to the beginning
Read carefully the letter that started it all.
It was:

Fig. 3. Excerpt from the letter with the identifier of the partner spammer
This promo4807 promo code is used to identify by the LP company where the client came from and from which partner (if the partner recommended them). Let’s verify that google knows about this affiliate ID.
Promo 4807 turned out to be very popular, it was posted on the official pages of LPtracker on behalf of. Representatives used in social. Networks, as a link to register for videos that the company regularly records and uploads to YouTube, etc. Below are a few screenshots where this is demonstrated:

fig. 4. Ivan Bochenkov, advertises the LP service under the partner identifier 4807. By the way, again, due to the name of the competing company,

fig. 5. The official representative of the lptracker company on the spark, when you click in detail you can see the same screenshot as in the mailing list and the same promo code 4807. And this is again Ivan

pic. 6 Detail, by clicking on the comment.

Fig. 7 Comments of Ivan on the sparks, as of. Representative of the company on the Internet. As you can see, it accepts user requests and writes on behalf of "We" - that is, the company.
In addition, in a phishing letter, Ivan also indicated: “Gookit.com - a service for publishing and sending commercial offers, announcements and articles” - this site is registered on Ivan Bochenkov.

Fig. 8 excerpt from the letter

fig. 9. Issue in google when entering affiliate link 4807.
As we see, the same projects drop out of the same person.
Of course, the Internet allows you to maintain some anonymity, but when you already know the participants in the conspiracy, you can identify certain patterns.
The figure below shows two accounts on the information resource on which the spammer contacted us. The Alexandrovich account - the spammer account, which he himself admitted in the comments, and the Nicolas account ... - Ivan's account, were on the site at the same time. More precisely, the spammer first came in, corresponded with us, and a little later Ivan came in.

Fig. 10 Two accounts of Ivan
Continuation of the story:
Affiliate link 4807, through which spam clicks go active for the 3rd day, the LP company does not get in touch, has blocked all our contacts. We posted an article about this, which became very worrying for the “spammer” and he began to demand its removal, threatening with new mailings.
The question immediately arose: why should a spammer be so worried about the service and ask to delete those articles, in every possible way denying his involvement in the drug.
By the middle of the 3rd day the "spammer" began to sweep tracks. Promo code 4807 posted on the official pages of the company LP, in social. Networks, forums, YouTube, in the news and other sources changed to another.
This explained why the spam link was unlocked after 5 minutes. As soon as they blocked it, the LP company had to change the promo code in all official mentions of them on the Internet, because the old one stopped working. That is, having blocked the partner 4807, they blocked themselves.
As soon as the promo code was changed, the malicious link 4807 was blocked.
Lesson 2: Do not forget about lesson 1. Save all the evidence at once, take screenshots, videos.

Fig. 11 The LP company blocked the link, confirming the fact that they understood all this time about the violation of the rights of third parties.
But the article about the incident continued to bother the spammer and the PL.
The spammer even called us on a personal cell phone, the same number from which we tried to contact the PL when we saw the newsletter. Where did he get this number from? It is not used anywhere in open sources. Other PL employees began calling us on the same number with a demand to remove the article, then they made threatening calls ...
After some time, Ivan’s friend, Sergei Arsenichev, also decides to send letters to Ivan’s base, but about his LeadBack service.

Fig. 12 Chronology of events restored using information from open sources.
Lesson 3. If you have not responded and have forgiven an infringement of your rights, they will be infringed constantly. Do not hope that the situation does not happen again.
Step 3. Verify the evidence with a notary
In the course of our mini investigation, we managed to find a lot of evidence of the involvement of the above-listed persons in the defamatory newsletter. There is no purpose to bring them all in this article, therefore we will not do this.
The certification of documents cost us about 60 thousand rubles. However, now we have not just screenshots, the authenticity of which can be questioned, but certified documents with which you can protect your rights.
Step 4. Try to negotiate
The newsletter discredited us in the face of our customers, we received a lot of negativity and consequences, but it is difficult to calculate the material damage from this. In addition, by the time the company blocked the link, we had already paid for notary services and legal advice.
Litigation requires additional financial costs and lasts a long time, so always try to agree on compensation for your damage peacefully, you may be able to compensate for some of your losses. We also tried to do this and wrote a letter in LP. In our cases, a constructive dialogue did not work: the company wrote that they did not intend to protect the spammer (i.e., their official representative Ivan Bochenkov), it was his full responsibility and we should make all claims personally to him, while they would not specify who this was spammer.
And at this time, the spammer continues to defend the honor of the company, threatens us in correspondence by email, writes letters on our behalf to clients using profanity.
Step 5. Gather More Information
Most likely, your case with the newsletter is not the only one and the person who deals with such has already offended someone before you. Gather this information, people often write in open sources about such incidents. They will be able not only to characterize you as a person, in our case a “spammer”, but they also probably know his contact and other data.
Ivan Bochenkov was no exception, on the network we found freelancers whom he did not pay for work, threatened spam mailings on their contacts about what they were “losers”, insulted with obscene expressions, etc. In general, he did everything the same as our spammer did and does.
One of the freelancers lost his official job, as he decided to demand payment from Ivan for the work done. According to him, Ivan talked with his leader, and the next day the freelancer was fired without explanation.

Fig. 13 Post in the social. Networks about deceiving a designer

Fig. 14. Review of Ivan in the list of customers who do not pay for orders
vk.com/photo-51016572_370984336

Fig. 15. The manner of communication of Ivan. An excerpt from correspondence with one of the freelancers whom Ivan did not pay, however, according to the freelancer himself, he used his work.
Each story of interactions with freelancers is a separate story that requires a separate investigation, but we can conclude for ourselves that if such stories happen, it’s not just that they give a person a certain characteristic by the very fact of their existence.
Step 6. Transfer the information you have to the competent authorities and write a statement
Now that you have collected all the information and facts about the incident, when you have feedback characterizing the participants, send all the data you have to the competent authorities. They will establish the possibility of fraudulent activity against you.
If this article was useful to you, then how to file an application, to which authorities and what happens next, we will write in the next part.
Lesson 4. As Warren Buffett said: “It takes 20 years to build a reputation and 5 minutes to destroy it” and do not trust the development of your project to dubious individuals.
Ps: While we were writing this news, Ivan became active again and now sends spam in the interests of Sipuni.com - but this is another story.
