New authentication methods - a threat to privacy?

Experts know that single-factor password authentication is outdated. Yes, it is suitable for insignificant systems like Habr, but really valuable assets are unacceptable to protect in this way. There are no “reliable” and “strong” passwords; even a crypto-resistant passphrase with 44 bits of entropy is of little use if it is not supported by other authentication factors.
Authentication factors:
- “What you know” (Something You Know) - for example, a password
- “Something You Have” - for example, a mobile phone or a PKI-token
- “Something you are” (for example, Something You Are) - for example, keyboard writing or other biometric features
Numerous database leaks with personal information of users and employees of large organizations are further proof of this. According to a Verizon Data Breach Investigations Report study , 81% of all information system hacks and data leaks in 2017 were caused by compromised accounts. That is, "stolen" or "lost" passwords.
But for the sake of security and more advanced authentication, you have to sacrifice something. Unfortunately, the privacy of users can suffer. Some modern technologies provide for either monitoring human behavior or collecting biometric data.
If implemented incorrectly, such security systems can turn into a kind of Big Brother, where it will be practicallyIt is impossible to ensure security while maintaining anonymity .
New Authentication Methods
Even the latest version of reCAPTCHA v3 , which Google recently officially unveiled , is using behavioral analysis methods, that is, it secretly tracks user actions .
From the point of view of the webmaster, the system works like this: along with the page, the user is given the reCAPTCHA library and the function is executed
grecaptcha.execute. The user does not notice anything - but from this point on, his actions are monitored by Google servers, and the site owner is given a specific user rating on a scale from 0.0 (bot) to 1.0 (people). 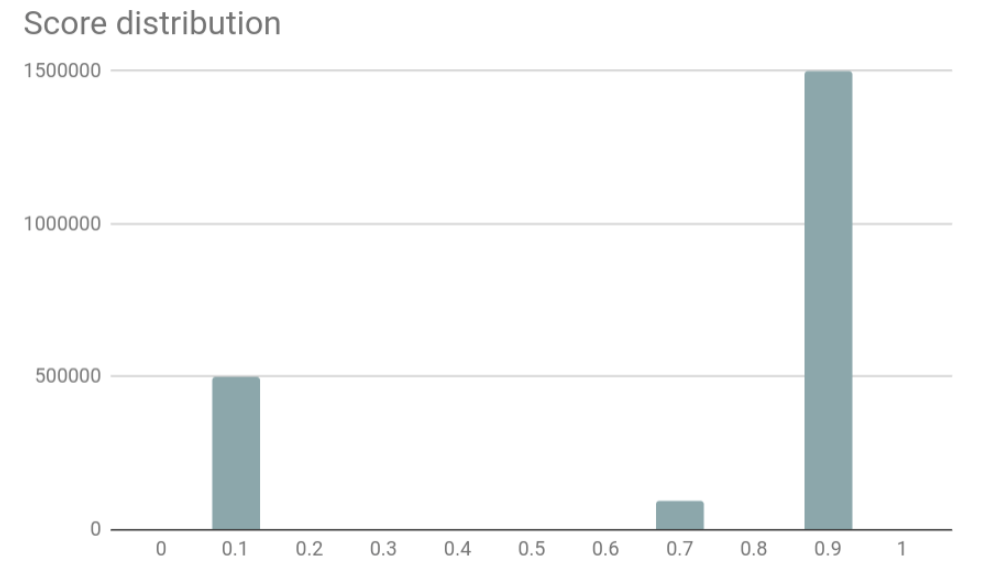
Based on this assessment, you can automatically disable authentication or other actions on the site. For example, only users with a rating higher than 0.5 are allowed to access the password entry page.
Although reCAPTCHA is not specifically an authentication system, it is a good demonstration of behavioral analysis, advanced risk risk analysis or risk-based authentication . This is a popular approach to new authentication systems that are now on the market . Here's how suppliers describe a risk-based approach:
“The need for authentication, the set and type of factors required to authenticate a given client are determined based on the risk assessment of the event and client“ here and now ”. Thus, the authentication process is adapted to the client, its environment and device. With a high level of confidence in these factors, the authentication procedure is generally invisible (in fact, it is just an identification) or minimal for the client. If the risk is identified, the client must authenticate using one or several factors, and if fraud is highly likely, access to services will be completely blocked. ”
The principle of background behavioral analysis is a bit like the algorithm for reCAPTCHA v3.
In fact, the idea is to implement multi-factor authentication, retaining or even increasing user convenience. For example, if the entrance to the Internet bank system is from a known device, from a typical place, and the system recognizes the keyboard style of a person, then they can enter it into the system without a password at all.
Another example: when paying from a personal account, the system does not request additional confirmation for standard operations that the client has already performed before. The second and / or third authentication factor is requested when a new payment is made to a new counterparty. Obviously, a non-standard payment increases the likelihood that someone has received unauthorized access to the account.
Biometrics in Russia
Yes, behavioral analysis with hidden surveillance of the user's actions seems to be a dubious technology, but with proper implementation, it still allows the person to remain anonymous and at the same time provide authentication in the system. Another thing - the collection of biometric data, which inherently implies the rejection of anonymity.

Masks printed on a 3D printer can deceive biometric verification in iPhone X phones. Of
particular concern is the initiative to deploy biometric identification in Russia, where leaks of databases with personal data of citizens have become commonplace .
At a recent forum on innovative financial technologies, Finopolis 2018 was told that in Russia "the stage of strategic discussion of the biometric identification system was completed," and now the practical implementation of this technology has begun, which will take "at least three years."
We are talking about a unified biometric systemto which large banks and other organizations of the Russian Federation are connected. At the first stage, there is a massive collection of biometric data from the public, the work is coordinated by Rostelecom.
From the official site of the project:
The Unified Biometric System is a digital platform for remote biometric identification, which allows you to provide new digital commercial and public services to citizens anytime and anywhere. The system was created at the initiative of the Central Bank of the Russian Federation and the Ministry of Digital Development, Communications and Mass Communications of the Russian Federation, Rostelecom - the developer and operator of the Unified Biometric System.
The unified biometric system together with the login and password from the state services allows banks to open an account, deposit or provide a loan to them without the personal presence of a citizen. Thus, banks can complete the digitization of the client's path, and citizens have the opportunity to digitize the will and remotely sign documents.
A single biometric system handles two types of biometrics: voice and face, and not separately, but together . Two modalities allow us to define a “living person”, rather than an imitation of his biometrics in a digital channel.
Face and voice - the most affordable and common technologies at the moment. Identification by vein pattern, retina or fingerprint requires special reading equipment that is not available in the mass segment. But the availability of technology today is not a limiting factor for their use in the future. The system architecture allows you to add other modalities.
...
Rostelecom is one of the leaders in the cyber security market, so the system is provided with a high level of protection.
The key application for Android has already been released for remote identification of clients of Russian banks. The application works in conjunction with an account on the portal of public services, while it scans the voice and face of the user. Judging by the reviews on Google Play, the application is extremely unstable, including using an invalid certificate.

In general, the collection of biometric information about citizens is gradually becoming the norm throughout the world. After the terrorist attack of 11/09, representatives of 188 countries of the world signed an agreement recognizing biometrics of a person as the main identification technology for passports and next-generation entry visas. A chip is sewn into the biometric passports, where it is supposed to record fingerprints, a photograph of the retina of the eye, the distance between the pupils and other biometric information of the holder.
The trends are such that biometric verification is gradually becoming a standard procedure, and the state assumes the function of collecting and storing citizens' biometric data. Perhaps the biometric verification will be applied to various Internet services.
When improving security and authentication systems, including those with biometric verification, it is important to keep the main points in mind:
Anonymity is a basic human right
In May 2015, the UN Human Rights Council adopted a document that explicitly calls the possibility of anonymous use of the Internet and encryption of personal data as part of basic human rights:
Encryption and anonymity allow individuals to exercise their right to freedom of thought and expression in the digital age and must be carefully protected.
The widespread adoption of biometric passports began after the September 11 attacks. Since then, the privacy situation has noticeably deteriorated under the pretext of fighting terrorism. The UN noted that anonymity on the Internet can be used by hackers, including for organizing terrorist acts, but with the same success, crimes can be committed using other communication channels. Due to the limited number of criminals, it is impossible to deny the basic right to all other people , they believe in the organization.
In other words, when introducing advanced authentication systems and biometric checks, it is important not to splash out the baby as well, that is, to ensure the proper protection of users' personal data, especially their biometric information.

